Power Saving MAC Protocols in Wireless Sensor Networks: A Performance Assessment Analysis
Volume 6, Issue 4, Page No 341-347, 2021
Author’s Name: Rafael Souza Cotrim1, João Manuel Leitão Pires Caldeira1,2,3,a), Vasco Nuno da Gama de Jesus Soares1,2,3, Pedro Miguel de Figueiredo Dinis Oliveira Gaspar4,5
View Affiliations
1Polytechnic Institute of Castelo Branco, Castelo Branco, 6000-084, Portugal
2Instituto de Telecomunicações, Covilhã, 6201-001, Portugal
3InspiringSci, Castelo Branco, 6000-767, Portugal
4Deparment of Electromechanical Engineering, University of Beira Interior, Rua Marquês d’Ávila e Bolama, Covilhã, 6201-001 Portugal
5Centre for Mechanical and Aerospace Science and Technologies (C-MAST), Rua Marquês d’Ávila e Bolama, Covilhã, 6201-001, Portugal
a)Author to whom correspondence should be addressed. E-mail: jcaldeira@ipcb.pt
Adv. Sci. Technol. Eng. Syst. J. 6(4), 341-347 (2021); ![]() DOI: 10.25046/aj060438
DOI: 10.25046/aj060438
Keywords: Wireless Sensor Networks, WSN, MAC protocols, Energy Efficiency, Performance Assessment, Simulation
Export Citations
Wireless sensor networks are an emerging technology that is used to monitor points or objects of interest in an area. Despite its many applications, this kind of network is often limited by the fact that it is difficult to provide energy to the nodes continuously, forcing the use of batteries, which restricts its operations. Network density may also lead to other problems. Sparse networks require stronger transmissions and have little redundancy while dense networks increase the chances of overhearing and interference. To address these problems, many novel medium access control (MAC) protocols have been developed through the years. The objective of this study is to assess the effectiveness of the T-MAC, B-MAC, and RI-MAC protocols in a variable density network used to collect data inside freight trucks carrying fruits that perish quickly. This article is part of the PrunusPós project, which aims to increase the efficiency of peach and cherry farming in Portugal. The comparison was done using the OMNET++ simulation framework. Our analysis covers the behavior and energetic properties of these protocols as the density of the network increases and shows that RI-MAC is more adaptable and consumes less energy than the alternatives.
Received: 13 June 2021, Accepted: 08 August 2021, Published Online: 26 August 2021
1. Introduction
The world’s growing reliance on technology has increased the necessity for data collection. Wireless sensor networks (WSNs) are one of the many technologies that have appeared to fulfill such a niche, allowing greater versatility on what data is collected and how. WSN’s applications include improving emergency response [1], control urban lighting [2], control precision irrigation systems [3], monitor patients in healthcare facilities [4], and many others.
A WSN is a network comprised of nodes that collect data about the environment and send it to a data collection system. Although flexible, WSNs have several limitations. Usually, nodes do not have long-range communication capabilities and rely on a gateway, also called a base station, to send the data to its destination. They are also made to be cheap and compact, limiting the hardware that may be used. Finally, nodes do not have a reliable power source, forcing them to use batteries. These factors combined limit a node’s battery life, so care must be taken to reduce consumption to a minimum.
The power used in performing the necessary measurements is hard to modify, being mostly dependent on the physical mechanism used to acquire the data. On the other hand, idle listening and transmitting data are some of the most power-intensive tasks on a WSN [5], therefore most optimization efforts have tried to tackle these factors. These attempts have achieved variable success through techniques such as duty cycling [6], the use of separate communication channels to wake up nodes [7], reworking the medium access control (MAC) protocol [8], and many others [9].
Attempts to implement novel MAC protocols have been particularly prevalent [10] because the MAC sublayer controls when transmissions are sent and is responsible for avoiding collisions, which force data to be retransmitted. A protocol’s behavior can be more adaptable than then a mechanism implemented on the radio level, allowing for the specialization of protocols into certain specific domains such as mobility [11] and others. Finally, data reduction, adaptive sampling, and data prediction techniques required additional coordination between nodes and may depend on the physical nature of the variable. These facts coupled with the availability of tools for simulations are the reason why this paper will focus on novel MAC protocols and their impact on energy consumption.
The environment and node density may also exacerbate the detriments of idle listening and retransmission [12]. Sparse networks have a much greater average distance between nodes, reducing interference between transmission and overhearing, but increasing the minimum power of the radios. On the other side of the scale, dense networks contain large quantities of nodes confined in a relatively small area. At its limit, a dense WSN may behave like a fully connected network. This increases the probability of collisions and means that many nodes around a transmitter will over-hear the radio signals. Because of these differences, sparse and dense networks have different requirements for optimal operations.
The purpose of this paper is to compare MAC protocol for use in variable density wireless sensor networks. More specifically, their use on freight trucks to gather data about cargo temperature and other properties during transport. The scenario was developed following a survey of MAC protocols [13] and as part of the PrunusPós project [14], which aims to extend the shelf life of peaches and cherries in the Beira Interior region in Portugal. These fruits are highly seasonal and deteriorate rapidly after harvest. Storage under controlled temperature and humidity can slow down their decay, but even slight variations may compromise this process. In the proposed scenario, the sensors have been integrated into the crates or other containers used to store and transport the product, which allows for them to provide continuous feedback on the ambient conditions. Such a system facilitates individualized data collection from the moment the fruits are packaged to their delivery.
This granularity is desirable because it allows historic data to be tracked even though products in the same store shelf can come from many different producers and take many different paths while flowing through national and local distribution networks. For example, if a problem happens to a specific batch of products, the companies involved could look through the data to determine exactly where the lapse in their process has happened. This individualized approach also means that other sensors could be added to track variables and phenomena which are more localized than temperature, meaning that such a system could be adapted for a variety of products.
One of the problems of the proposed setup is that the number of nodes in the space can vary according to the size of the container and how full the truck is. The main objective of this work is to analyze the behavior of several MAC protocols under a variety of node densities that could be expected in this application. For our comparison, we have simulated the Timeout MAC (T-MAC) [15], Berkley MAC (B-MAC) [16], and Receiver Initiated MAC (RI-MAC) [17] protocols. Together, these protocols cover the main types of MAC protocols available today and allow us to identify the weaknesses of each approach when compared to the others. The simulations have been done using the OMNeT++ discrete simulation framework [18], which is a robust simulation tool that has been used in previous research [19,20], is updated frequently, and has extensive documentation.
The rest of this paper is organized as follows: Section 2 overviews the related work and explains the basic operations of the protocols compared. Section 3 explains how the simulation environment was set up goes over the results of the simulations, detailing the behavior of each protocol. Finally, section 4 concludes the paper and provides directions for future work.
2. Related Work
There have been many MAC protocols developed over the years for specific applications. Some of the first ones that were tailor-made for WSNs focused on making defining schedules with active and inactive parts for each node, creating a period where whole sections of the network could sleep. Sensor MAC (S-MAC) [21] and T-MAC [15] are the most notable in this category. Both work by giving nodes wake-up/sleep schedules and synchronizing them as they enter the network. T-MAC, however, attempts to reduce the time a node remains awake by utilizing a timeout period. If a node does not receive any transmissions during a timeout window, it will assume all data has been sent and will go back to sleep. Otherwise, it restarts the timer and continues listening to the medium. S-MAC’s and T-MAC’s procedures are visualized in Figure 1.
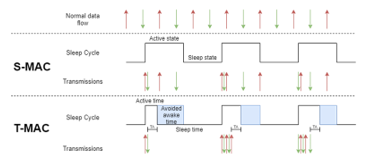 Figure 1: S-MAC and T-MAC comparison, adapted from [15]
Figure 1: S-MAC and T-MAC comparison, adapted from [15]
The Demand Wakeup MAC protocol (DW-MAC) [22] is an alternative synchronous protocol, however, it does not utilize the active part of the schedule to send and receive messages. It replaces CTS/RTS messages with scheduling messages (SCH), which the nodes use to choose a moment during the sleeping section of the frame where they can communicate without the risk of interferences. This scheduling is done based on the time the SCH frame was received, meaning that no two messages can be scheduled for reception by the same node at the same time.
Although effective, these approaches require a synchronization mechanism to prevent schedule drift, which adds complexity and extends the time the radio module is active. They are also less effective when multiple schedules are being used in the network, especially in very dense ones [15], a phenomenon called virtual clustering. Finally, one of the main flaws of synchronous protocols is that all the nodes wake up and contend for the medium at the same time. DW-MAC shifts when the data is sent, but the nodes still need to contend for the medium when the active part of the schedule begins. This means that there is a burst of activity in the beginning and, in networks restricted to small areas, that leads to only a few nodes being able to communicate at a time, with the rest of the network waiting for the medium to become free once more.
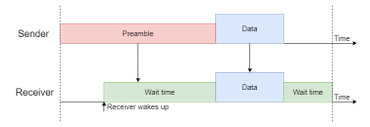 Figure 2: LPL communication example, adapted from [23].
Figure 2: LPL communication example, adapted from [23].
The B-MAC protocol [16] improves on some of these concerns. It is a specialized MAC protocol that reduces energy consumption by allowing nodes to have independent activity schedules. Nodes that have data to transmit send preambles slightly longer than the sleeping period of the receiver. When the destination node wakes up, it samples the medium and, if it detects a preamble, it remains awake. Once the preamble has ended, the sender transmits the data with the destination identifier. This process is known as Low Power Listening (LPL) and it allows nodes to have completely independent schedules. The procedure is illustrated in Figure 2. LPL has been shown to considerably reduce energy consumption when compared to other mechanisms. B-MAC addresses many of the problems synchronous protocols have by not requiring a schedule, which eliminates the necessity for synchronization mechanisms and means that it is not affected by the formation of virtual clusters. However, B-MAC’s long preamble leads to the same problem the other cited protocols have where a few nodes monopolize the medium, preventing nearby nodes from transmitting data in the meantime.
More recent protocols have explored other paradigms. As shown in Figure 3, in the RI-MAC protocol [17], the receiver initiates the data transfer by sending a beacon message to indicate to the sender nodes that it is available to receive data. This reduces the time a node occupies the medium and increases the maximum throughput. It also avoids sending the long preamble messages associated with LPL and other asynchronous strategies. However, this change in procedure can lead to problems when the communications channel is asymmetric, meaning that messages being sent in one of the communication directions has a lower chance of being received because of interference or other factors.
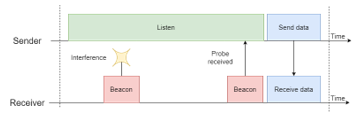 Figure 3: RI-MAC communication example, adapted from [8].
Figure 3: RI-MAC communication example, adapted from [8].
In cases where communication channels are very asymmetric, the Asymmetric MAC protocol (Asym-MAC) can reduce their impact [8]. Asym-MAC is very similar to RI-MAC, but it has two modes. Each communication attempt is started in R-mode, which operates like RI-MAC. However, if the sender does not receive a probe message within a certain period, indicating that it is being lost frequently, the communication will change to T-mode, where the sender initiates the communication. This prevents repeated loss of the beacon and restores communications in asymmetric channels, but Asym-MAC is slightly worse than RI-MAC in terms of energy consumption when the level of asymmetry is very low.
Much like Asym-MAC, the A-MAC protocol attempts to improve on RI-MAC [24]. It utilizes a different link-layer primitive, the backcast, to allow multiple nodes to be probed at the same time and reliably detect when it receives more than one reply at the same time, allowing it to better decide when to go back to sleep. A-MAC also allows nodes to utilize multiple frequencies to communicate, which increases the total throughput of the network and means that beacon messages may be segregated to a different frequency band to prevent interferences. While A-MAC is more effective than RI-MAC, it requires radios with memory-mapping and other features to work properly. A-MAC can still be used with other radios; however, it is less efficient and requires workarounds depending on the architecture of the hardware.
To test the effectiveness of various strategies in the proposed context, one protocol of each type was chosen. T-MAC was selected over the other alternatives because it makes various improvements without leading to additional drawbacks. B-MAC was chosen because it is one of the most robust asynchronous protocols. It has been used in multiple real-world applications and there are reliable implementations for TinyOS, an operational system for embedded systems. Despite its effectiveness, A-MAC’s hardware requirements often conflict with available equipment, which is made to be cheap and easily replaceable. On the other hand, Asym-MAC’s gains in asymmetric communication channels are not applicable in the proposed scenario. Outside interferences are dampened because the truck acts as a Faraday cage and there are no identifiable internal factors that could cause a high level of asymmetry. Considering these factors, RI-MAC was selected to be added to the simulations.
3. Performance Assessment
3.1. Network Settings
Figure 4 illustrates the proposed scenario. Nodes were integrated into the containers used to carry cargo inside a truck. These sensors measure the temperature regularly and transmit the data to a gateway that uses the truck’s radio to send the data to its destination. In real-world applications, the nodes could also measure other parameters to guarantee the safety and quality of the products. The density of the network in this scenario can vary according to the size of the container, how full the truck is, and how the boxes were arranged. To reduce complexity, the parameters of the protocols are not adjusted depending on how the truck is loaded, meaning that protocols must be flexible to accommodate a wide range of densities.
To measure the effectiveness of each protocol, the scenario was built on the OMNET++ [18] simulator and the INET framework [25] was used to handle wireless communications. The default B-MAC implementation from INET was used in these simulations. RI-MAC was implemented following the structure outlined in [17]. The original paper describing T-MAC leaves many questions unsolved about how the protocol should work [26], so our implementation was based on the one present in the Castalia Simulator [27], which is built on top of OMNET++.
As shown in Table 1, a variable number of nodes was scattered in a 2.2m by 15.75 m area to simulate the restricted environment where they would be deployed. Table 2 contains the power consumption of the various radio states used in the simulations, which were chosen to model the ESP8266EX Wi-Fi microchip [28]. For the purpose of this article, the energy consumed performing the measurements was ignored so that only the power spent by the normal function of each protocol is measured.
Table 1: Simulation parameters.
| Simulation Parameter | Value | Unit |
| Area height | 2.2 | m |
| Area width | 15.75 | m |
| Sapling interval | 100 | s |
| Data length | 32 | B |
Table 2: Radio power consumption based on a 3.3V power supply.
| State | Power Consumption | Unit |
| Idle | 15 | mA |
| Receiving | 50 | mA |
| Transmitting | 120 | mA |
| Sleep | 10 | uA |
Table 3 contains the main variables relating to the operations of the protocols studied. These values were previously acquired through other simulations designed to discover the optimal parameters for a network with 5 nodes. A small network was used so that the effects of increasing the number of nodes in the network without adjusting the parameters would be more noticeable.
Table 3: MAC variables
| MAC Variable | Value | Unit |
| T-MAC frame duration | 0.7 | s |
| T-MAC timeout interval | 0.03 | s |
| B-MAC slot duration | 0.17 | s |
| RI-MAC sleep interval | 0.85 | s |
The protocols were evaluated according to the number of delivered packages, their success rate, total energy consumption, energy spent per packet, number of over-heard packets, and their overall adaptability to the increasing network density. Other factors such as the latency of transmissions inside the network were not considered because external variables such as the delay of the communications between the truck’s radio and the system that stores the acquired results would overshadow these small aspects in real-world applications.
In order to get representative and meaningful results, each simulation scenario was executed 20 times. The results presented for each performance metric represent the average values calculated from the obtained results. Only the average values are represented in the graphs, as the standard deviations were negligible.
3.2. Results Analysis
Firstly, T-MAC, B-MAC, and RI-MAC were compared in terms of delivery success rate. Figure 5 shows the number of delivered packages for each density. In the base case with only 5 nodes, all protocols have a high success rate, however, their behavior starts to diverge as the number of nodes increases. T-MAC maintains a very high delivery ratio until the number of messages saturates its initial capacity, after which it becomes erratic. Success rates pick up again after 40 nodes because nodes are spending more time awake due to timeout extensions, which increases the network capacity. At the 50 to 55 range the number of delivered packets peaks because the repeated timeout extensions make nodes remain awake all the time, which maximizes the time they have to transmit. However, the protocol has reached its limit after this point and any additional messages only cause degradation of the service due to interference, leading to a drastic decline in capacity.
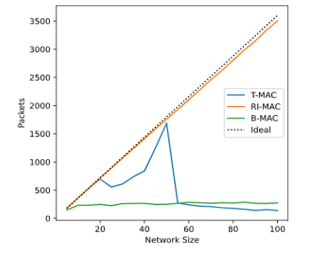 Figure 5: Total packets delivered according to network density.
Figure 5: Total packets delivered according to network density.
B-MAC also does not work effectively outside its ideal conditions, the absolute number of delivered packages remained stable throughout the experiment. This is likely because of how the protocol saturates the medium while transmitting a preamble. A centralized node can easily interferer with the communications anywhere else in such a limited space, reducing total throughput. Finally, RI-MAC had the best overall results. Figure 6 shows that it consistently delivered almost all the packets and showed minimal service degradation as the density of the network increased. This is because nodes block the medium for shorter durations and less frequently than the other protocols, leaving room for a greater load in the network.
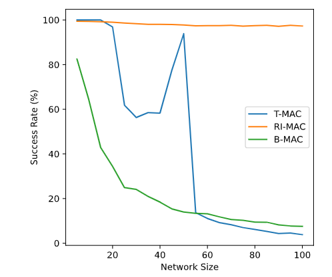 Figure 6: Delivery success rate according to network density.
Figure 6: Delivery success rate according to network density.
In terms of power consumption, the most visible difference between the protocols occurs after the network reached 50 nodes. Figure 7 shows that, because of the increasing amount of network events (transmissions), nodes running T-MAC spend an increasing amount of time awake, which leads to more energy consumption. At a certain point, nodes are not able to sleep between wake-up signals. Figure 8 illustrates how this happens. This extra awake time increases the number of transmissions the protocol is capable of handling but also causes a substantial increase in energy consumption.
After 55 nodes the extensions become so frequent that the nodes remain permanently awake, maximizing energy consumption. Because of that, the energy consumed by the network increases linearly with each added node after this point as shown by Figure 9. However, the added consumption does not translate into extra capacity. At 55 nodes, the protocol starts to become overloaded, and each additional node increases the chances of interference, which forces nodes to retransmit data, increasing the chances of interference further. This leads to a feedback loop that severely hinders the protocol’s operations.
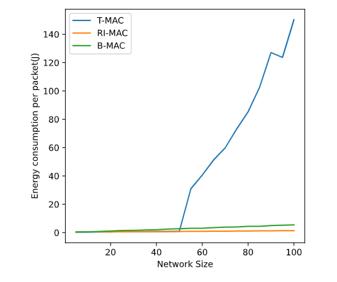 Figure 7: Energy consumption per packet according to network density.
Figure 7: Energy consumption per packet according to network density.
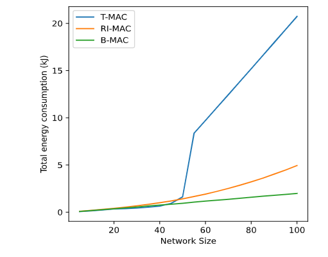 Figure 8: Continuous extension of the T-MAC timeout period leads to increased energy consumption and no sleep between wakeup signals.
Figure 8: Continuous extension of the T-MAC timeout period leads to increased energy consumption and no sleep between wakeup signals.
 Figure 9: Total network consumption according to network size.
Figure 9: Total network consumption according to network size.
B-MAC and RI-MAC do not suffer from the same problem, their power consumption grows smoothly with the number of nodes in the network. RI-MAC spends more power in absolute terms, but its performance compared to the number of delivered packages is much better. In contrast, B-MAC’s added expenditure does not translate into usable network capacity.
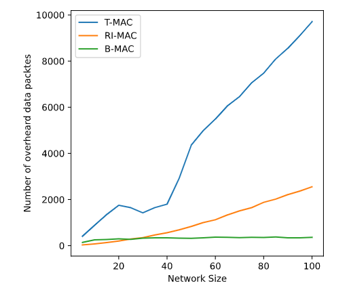 Figure 10: Average number of data packets overheard by nodes depending on network size.
Figure 10: Average number of data packets overheard by nodes depending on network size.
Figure 10 puts the previous results into perspective. The average number of over-heard messages, data packets a node received that were not addressed to it, can also be used to characterize the behavior of a protocol. Ideally, a node would never receive a message addressed to another node to conserve energy. As this statistic did not consider beacon messages, B-MAC comes close to the optimal case. However, this only occurs because the absolute number of packets B-MAC sent was constant. If the protocol was more flexible, a similar phenomenon to what happened with RI-MAC would have been seen. As the number of nodes in the network increase, not only does the same happens to the number of messages, but also to the chances of a node waking up and accidentally receiving a packet sent to another one. This is one of the causes of the increasing power consumption per packet sent seen in Figure 7.
Finally, T-MAC’s results are consistent with the increase in total energy consumption. Unlike RI-MAC, it displays a mostly linear increase in overhearing rate because nodes wake up at the same time, meaning that all nodes within the range of a transmission always receive the packet being sent. The gap in the graph is caused by the same issues explored in the analysis of the previous graphs.
4. Conclusion and Future Work
This paper presents the results from a series of simulations designed to study the performance of various MAC protocols in networks with variable node density, especially denser ones. In this instance, the proximity between nodes makes the network behave similarly to a fully connected one. The scenario was set up to model their use inside delivery trucks with the intent of monitoring perishable goods in transit as part of the PrunusPós project. This initiative aims to reduce the losses farmers and distributors of peaches and cherries incur every year due to the fragility of these fruits.
The protocols were evaluated in terms of delivery success rate, energy consumption, overhearing, and flexibility as node densities increase. The results show that RI-MAC, a protocol based on receiver-initiated communications, had the best reliability and lowest consumption per package in a wide range of network densities. Its flexibility is ideal for networks with highly variable density and where continuous adjustment of protocol parameters may be challenging. The growth of power expenditure is also minimal with every node, indicating the networks with more nodes are possible with a limited energy budget.
Furthermore, it is possible to see the various shortcoming of LPL based protocols such as B-MAC and synchronous protocols such as T-MAC. Their behavior is good under the conditions they were optimized for; however, they can quickly lose effectiveness when outside the initial bound. The length of beacon messages and the synchronized wakeup time make them unsuited for extremely dense networks. Future studies should focus on confirming the presented findings in a real testbed to uncover the finer details of RI-MAC’s behavior in a network with variable density. Protocols that take into account the number of neighbors a node has may also offer an avenue for research.
Conflict of Interest
The authors declare no conflict of interest.
Acknowledgment
This study is within the activities of project “PrunusPós – Optimization of processes for the storage, cold conservation, active and/or intelligent packaging and food quality traceability in post-harvested fruit products”, project n. º PDR2020-101-031695, Partnership n.º 87, initiative n.º 175, promoted by PDR 2020 and co-funded by FEADER within Portugal 2020. P.D.G. thanks the support of Fundação para a Ciência e Tecnologia (FCT) and C-MAST – Centre for Mechanical and Aerospace Science and Technologies, under project UIDB/00151/2020. V. N. G. J. S. and J. M. L. P. C. acknowledge that this work is funded by FCT/MCTES through national funds and when applicable co-funded EU funds under the project UIDB/50008/2020. The authors would also like to acknowledge the company InspiringSci, Lda for its interest and valuable contribution to the successful development of this work.
- K. Lorincz, D.J. Malan, T.R.F. Fulford-Jones, A. Nawoj, A. Clavel, V. Shnayder, G. Mainland, M. Welsh, S. Moulton, “Sensor Networks for Emergency Response: Challenges and Opportunities,” IEEE Pervasive Computing, 3(4), 16–23, 2004, doi:10.1109/MPRV.2004.18.
- X. Liu, P. Hu, F. Li, “A street lamp clustered-control system based on wireless sensor and actuator networks,” in Proceedings of the 10th World Congress on Intelligent Control and Automation, IEEE: 4484–4489, 2012, doi:10.1109/WCICA.2012.6359237.
- R.G. Vieira, A.M. Da Cunha, L.B. Ruiz, A.P. De Camargo, “On the design of a long range WSN for precision irrigation,” IEEE Sensors Journal, 18(2), 773–780, 2018, doi:10.1109/JSEN.2017.2776859.
- J.M.L.P. Caldeira, J.J.P.C. Rodrigues, P. Lorenz, “Intra-Mobility Support Solutions for Healthcare Wireless Sensor Networks–Handover Issues,” IEEE Sensors Journal, 13(11), 4339–4348, 2013, doi:10.1109/JSEN.2013.2267729.
- G.J. Pottie, W.J. Kaiser, “Wireless integrated network sensors,” Communications of the ACM, 43(5), 51–58, 2000, doi:10.1145/332833.332838.
- J. Ma, W. Lou, Y. Wu, X.-Y. Li, G. Chen, “Energy Efficient TDMA Sleep Scheduling in Wireless Sensor Networks,” in IEEE INFOCOM 2009 – The 28th Conference on Computer Communications, IEEE: 630–638, 2009, doi:10.1109/INFCOM.2009.5061970.
- S. Singh, C.S. Raghavendra, “PAMAS – Power aware multi-access protocol with signalling for Ad Hoc networks,” Computer Communication Review, 28(3), 5–25, 1998, doi:10.1145/293927.293928.
- M. Won, T. Park, S.H. Son, “Asym-MAC: A MAC protocol for low-power duty-cycled wireless sensor networks with asymmetric links,” IEEE Communications Letters, 18(5), 809–812, 2014, doi:10.1109/LCOMM.2014.032014.132679.
- G. Anastasi, M. Conti, M. Di Francesco, A. Passarella, “Energy conservation in wireless sensor networks: A survey,” Ad Hoc Networks, 7(3), 537–568, 2009, doi:10.1016/j.adhoc.2008.06.003.
- S. Hayat, N. Javaid, Z.A. Khan, A. Shareef, A. Mahmood, S.H. Bouk, “Energy efficient MAC protocols,” Proceedings of the 14th IEEE International Conference on High Performance Computing and Communications, HPCC-2012 – 9th IEEE International Conference on Embedded Software and Systems, ICESS-2012, 1185–1192, 2012, doi:10.1109/HPCC.2012.174.
- Q. Dong, W. Dargie, “A Survey on Mobility and Mobility-Aware MAC Protocols in Wireless Sensor Networks,” IEEE Communications Surveys & Tutorials, 15(1), 88–100, 2013, doi:10.1109/SURV.2012.013012.00051.
- F. Jia, Q. Shi, G.M. Zhou, L.F. Mo, “Packet delivery performance in dense wireless sensor networks,” 2010 International Conference on Multimedia Technology, ICMT 2010, 12–15, 2010, doi:10.1109/ICMULT.2010.5629537.
- R. Cotrim, J.M.L.P. Caldeira, V.N.G.J. Soares, Y. Azzoug, “Power Saving MAC Protocols in Wireless Sensor Networks: A Survey,” TELKOMNIKA, 2021.
- R.R. Nacional, PrunusPós, 2021.
- T. Van Dam, K. Langendoen, “An adaptive energy-efficient MAC protocol for wireless sensor networks,” SenSys’03: Proceedings of the First International Conference on Embedded Networked Sensor Systems, 171–180, 2003, doi:10.1145/958491.958512.
- J. Polastre, J. Hill, D. Culler, “Versatile low power media access for wireless sensor networks,” in Proceedings of the 2nd international conference on Embedded networked sensor systems – SenSys ’04, ACM Press, New York, New York, USA: 95, 2004, doi:10.1145/1031495.1031508.
- Y. Sun, O. Gurewitz, D.B. Johnson, “RI-MAC: A Receiver-Initiated Asynchronous Duty Cycle MAC Protocol for Dynamic Traffic Loads in Wireless Sensor Networks,” in Proceedings of the 6th ACM conference on Embedded network sensor systems – SenSys ’08, ACM Press, New York, New York, USA: 1, 2008, doi:10.1145/1460412.1460414.
- OpenSim Ltd, OMNeT++ Discrete Event Simulator, 2021.
- A.A. Ibrahim, O. Bayat, “Medium Access Control Protocol-based Energy and Quality of Service routing scheme for WBAN,” HORA 2020 – 2nd International Congress on Human-Computer Interaction, Optimization and Robotic Applications, Proceedings, 9–14, 2020, doi:10.1109/HORA49412.2020.9152849.
- M. Nabi, M. Blagojevic, M. Geilen, T. Basten, T. Hendriks, “MCMAC: An optimized medium access control protocol for mobile clusters in wireless sensor networks,” SECON 2010 – 2010 7th Annual IEEE Communications Society Conference on Sensor, Mesh and Ad Hoc Communications and Networks, 2010, doi:10.1109/SECON.2010.5508200.
- W. Ye, J. Heidemann, D. Estrin, “An energy-efficient MAC protocol for wireless sensor networks,” in Proceedings.Twenty-First Annual Joint Conference of the IEEE Computer and Communications Societies, IEEE: 1567–1576, 2005, doi:10.1109/INFCOM.2002.1019408.
- Y. Sun, S. Du, O. Gurewitz, D.B. Johnson, “DW-MAC: A low latency, energy efficient demand-wakeup MAC protocol for wireless sensor networks,” in Proceedings of the 9th ACM international symposium on Mobile ad hoc networking and computing – MobiHoc ’08, ACM Press, New York, New York, USA: 53, 2008, doi:10.1145/1374618.1374627.
- M. Buettner, G. V Yee, E. Anderson, R. Han, “X-MAC: A Short Preamble MAC Protocol for Duty-Cycled Wireless Sensor Networks,” in Proceedings of the 4th international conference on Embedded networked sensor systems – SenSys ’06, ACM Press, New York, New York, USA: 307, 2006, doi:10.1145/1182807.1182838.
- P. Dutta, S. Dawson-Haggerty, Y. Chen, C.J.M. Liang, A. Terzis, “A-MAC: A versatile and efficient receiver-initiated link layer for low-power wireless,” ACM Transactions on Sensor Networks, 8(4), 1–14, 2012, doi:10.1145/2240116.2240119.
- INET Framework.
- Y. Tselishchev, A. Boulis, L. Libman, “Experiences and lessons from implementing a wireless sensor network MAC protocol in the Castalia simulator,” IEEE Wireless Communications and Networking Conference, WCNC, 2010, doi:10.1109/WCNC.2010.5506096.
- T. Boulis, D. Pediaditakis, Castalia.
- T. Boulis, D. Pediaditakis, ESP8266EX Datasheet, 31, 2020.
Citations by Dimensions
Citations by PlumX
Google Scholar
Crossref Citations
- Rafael Souza Cotrim, João Manuel Leitão Pires Caldeira, Vasco Nuno da Gama de Jesus Soares, Pedro Miguel de Figueiredo Dinis Oliveira Gaspar, "Power Saving MAC Protocols in Wireless Sensor Networks: A Performance Assessment Analysis." Advances in Science, Technology and Engineering Systems Journal, vol. 6, no. 4, pp. 341, 2021.
No. of Downloads Per Month
No. of Downloads Per Country