The Role of RFID in Green IoT: A Survey on Technologies, Challenges and a Way Forward
Volume 6, Issue 1, Page No 17-35, 2021
Author’s Name: Zainatul Yushaniza Mohamed Yusoff1,2, Mohamad Khairi Ishak1,a), Kamal Ali Alezabi3
View Affiliations
1School of Electrical and Electronic Engineering, Universiti Sains Malaysia, Nibong Tebal, Pulau Pinang, 14300, Malaysia
2Majlis Amanah Rakyat, Kuala Lumpur, 56000, Malaysia
3Institute of Computer Science and Digital Innovation (ICSDI), UCSI University, Cheras, Kuala Lumpur, 56000, Malaysia
a)Author to whom correspondence should be addressed. E-mail: khairiishak@usm.my
Adv. Sci. Technol. Eng. Syst. J. 6(1), 17-35 (2021); ![]() DOI: 10.25046/aj060103
DOI: 10.25046/aj060103
Keywords: Green Power, Green IoT, RFID, Application, Challenges, Impacts
Export Citations
The Internet of Things (IoT) is a technology that enables communication between everyday life using different sensor actuators that work together to identify, capture, and distribute critical data from the planet. Massive machines and devices are therefore linked and communicate with them. The use of resources in this area presents new challenges for this technology. The goal was to find a green IoT that focuses on energy efficiency and IoT efficiency. Green IoT is an energy-efficient way to reduce or eliminate the greenhouse effect of current applications. Radio Frequency Identification (RFID) is one of the Green IoT and Master IoT components that identifies a person or entity in a high-frequency electromagnetic spectrum when combining electromagnetic or electrostatic couplings. If the predictions are also correct, energy use issues arise as active battery-powered RFID detection needs to be addressed by incorporating new solutions for Green IoT technology. Past studies and assessments have attempted to evaluate RFID technology and its functions. Unfortunately, however, they concentrated on a single RFID view of technique and technology. This paper examines holistically and systematically the impact of RFID applications on green IoT, focusing on three categories: the challenges, environmental consequences, and the benefits of green IoT RFID applications. The impacts, performance and safety of RFID IoT applications have been carefully described. The benefits and examples of RFID applications, including their key advantages and disadvantages, are also discussed. Overall, this paper highlights the potential efforts of RFID to address existing Green IoT issues.
Received: 11 October 2020, Accepted: 28 November 2020, Published Online: 10 January 2021
1. Introduction
Green power comes from natural sources such as sunlight, wind, rain, tides, plants, heat and algae as shown in Figure 1. These energy resources are renewable and naturally refilled to offer the most significant environmental benefit [1]. Conventional energy can be a valuable source of air pollution and emissions of greenhouse gases. The use of renewable energy helps to perform the following [2]:
- Reduce the carbon footprint with purchased electricity.
- Future price increases and volatility of electricity (individual products).
The purpose of green power is to find energy conservation measure in order to reduce energy consumption and increase the energy efficiency. Energy conservation means making use of less energy to accomplish work, namely reducing waste energy. Energy efficiency Although the use of renewable energy technologies also improves this, increased energy usage is the simplest and often most efficient way to reduce fossil fuel use. There are enormous opportunities to enhance productivity in every sector of the economy, whether it be infrastructure, transportation, manufacturing or energy generation [3]. In reality, without Internet of Things (IoT), it isn’t easy to imagine the future of renewable energies. Today sensor-based technology and data science enable wind farms and solar fields to be productive and automated. Green IoT technology programs should be taken into account because of the growing perception of environmental issues worldwide. The Greening IoT definition refers to innovations that make the IoT ecosystem healthier and environmentally pleasant through the use of facilities and storage that enables subscribers to capture, store, access, and handle different information.
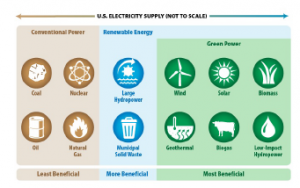
Figure 1: Green Power Generation [1]
The technology that enables green IoTs is called information and communication technologies (ICTs) [4]. ICTs will cause climate change in the world because the rising application of ICT has used much more energy [5, 6]. The emphasis on sustainability for ICTs has been on data center optimization through infrastructure sharing techniques that improve energy efficiency, minimize CO2 emissions and e-waste disposal [7]. Greening ICT enables green IoT technology which includes green wireless sensor networks (GWSNs), green machine-to-machine communication (GM2M), green RFID (GRFID), green data center (GDC), green cloud computing (GCC), green Internet (G-Internet), and green communication network (GCN) as shown in Figure 2. Greening ICT offers green IoT technologies. Green ICT innovations play a crucial role in green IoT and offer many benefits for society, including the reduction in energy used to develop, produce, and distribute ICT devices and equipment [8].

Figure 2: Green ICT technologies [8]
Green IoT consists of aspects of nature and exploitation. Green IoT focuses on reducing the use of IoT resources and CO2 emissions, which are essential for creating an innovative and prosperous world of intelligent everything. As Figure 3 shows, the green IoT design elements apply to computer creation, energy conservation, communication protocols, and architectures for networking [9]. It is possible to use the IoT portion to remove CO2 emissions, minimize pollution, and increase energy efficiency [10]. In networking, Green IoT aims to decide where the relay is located and how many nodes meet budget constraints and energy saving [11]–[12]. For achieving green IoT, there are three principles, namely, design technologies, leverage technologies, and enabling technologies. Build technologies that apply to computers, communication protocols, network interfaces, and interconnections for energy efficiency. Leverage technology relates to reducing emissions of carbon and rising energy efficiency [13]. By reducing electricity, toxic emissions, use of resources, and pollution, green IoT has become more effective due to green ICT technologies. As a result, green IoT ensures the protection of natural resources, minimizes the effect of technology on the environment and human health, and dramatically reduces costs. In reality, therefore, green IoT focuses on green development, green usage, green design, and green disposal [14].
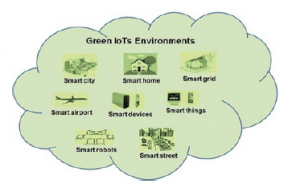
Figure 3: Green IoTs Environments [9]
RFID is a complementary solution to green IoT technology to save energy. RFID uses radio frequency to transmit, identify, classify and track data between readers and moving objects. It is fast and does not require a physical view or connection between the reader/scanner and the object to be inspected. The operating cost factor is deficient low and can use in many applications such as healthcare, manufacturing, inventory management, shipping, retail sales and home use [15]. RFID technology internal divided into two parts, namely RF communication; reader/tag protocols and middleware architecture, where RFID tag can be attached to almost anything such as items, cases or product palettes, high-value goods, vehicles, assets, livestock or personnel. RFID tags divided into two sits; which is a passive tag and an active tag. RFID middleware is RFID’s software that exists between readers and enterprise/business applications. Middleware has several functions and plays an essential role in the operation and management of RFID systems. Middleware handles RFID readers and printers and communicates between these devices and business applications, as well as manage, filter, aggregate, and understand data derived from RFID tags [15]. RFID application used in manufacturing and processing for supervision, production of warehouse processing and fulfillment orders. In supply chain management, it should face in Inventory Tracking and Logistics management system. It also used in local controls for customer inventory and views; and automated checks with reverse logistics which benefit the environment. Whereas securities applied on access control, counterfeiting and theft control/prevention [16]. However, there is little discussion in the existing literature on RFID management in the environment. Is seen that ICT harms the environment [17], and RFID, as part of ICT, has gained a reputation [18] as one of the leading computing technologies, using sufficient energy to impact the environment negatively [19].
The contributions of this paper are summarized as follows:
- A detailed review of current and recent RFID literature on IoT, notably the Green IoT, in order to show that RFID can be part of the green IoT, not only for the benefit of the economy but also for the benefit of the organization, but also to improve responsible IT practice.
- As this paper reviews the application of the Green IoT study proposed by RFID in recent years, it also outlines some of the early research related to this field.
Section 2 provides a summary of some IoT device RFID technologies. Section 3 Discussion about the security of RFID and addresses RFID implementation issues and environmental consequences in Section 4. In section 5, the benefit of greening IT. The future work of RFID in Green IoT is discussed in Section 6, and Section 7 outlines the study’s findings.
2. Studying RFID Technology in IoT Application
The Internet of Things (IoT) intended to describe a range of technologies and research disciplines that enable global connectivity through the world’s physical objects [20]. Activation technologies such as RFID, sensor networks, biometrics, and nanotechnologies are now widely used [21]. The IoT implemented in real implementations for different applications such as smart grid, e-health, and intelligent transport. RFID is a stand-alone technology used to enable various systems to perform functions based on object recognition, data recording, and different control objects [22]. The iconic RFID system consists of two parts: a tag (transmitter/receiver) and a reader (transmitter/receiver). The tag contains a chip attached to an object for detection and serves as an object identifier. Instead, RFID readers regularly exchange information with RFID tags using radio waves [23]. The main advantages of RFID technology are automatic object recognition, data acquisition and cost reduction in various activities [24]. The distributed RFID readers around the world are connecting to the Internet according to an appropriate routing protocol. Readers can then exchange information to identify, track, and monitor objects based on the tags they carry. Instead, IoT refers to virtual presentations in the IoT architecture, where identifiable objects are called ”things”. RFID is a prerequisite for the proper operation of an IoT system [25]. IoT is a global infrastructure that connects and ignores the distance between virtual and physical objects based on data usage and routing capabilities. The IoT architecture consists of three layers, namely the service or application layer, the network layer, and the perceptual layer, where the level of perception includes real-time information and the Internet of Things [26]. This layer uses sensors, wireless sensor networks, tags, RFID systems, cameras, GPS, smart terminals, EDIs, and creators to collect and display information about objects in the physical world. RFID tags, readers and application systems are composed of RFID systems. RFID systems are fast and effective for the electronic identification, control, and identification of different artifacts.
RFID uses wireless transmission to send a signal for an RFID tag that responded to a data collection reader linked to the host computer’s data for analysis by a single ID code [27] RFID application functionality divided into three categories: control, tracking, and supervision. Monitoring concerns the current device status. For medical circumstances to be detected, irregular behavior and alarm must be an identifier. Tracking sees moving objects and provides a modeling sequence for every location of the data. Control refers to the evaluation and monitoring carried out without the awareness of the object [28]. RFID is used to prevent misplacement or to locate items quickly. One approach is to track the movement of objects in the database. For example, an RFID reader may attach to a door in a building between rooms. Thus, the location of the object can be determined by analyzing RFID reader recordings. It mainly used in supply chain management systems, item monitoring processes, and industrial process control. 3 Great advantages of identification of RFID supply chain properties as seen in the following Table 1 [29]. The use of RFID is also developing in manufacturing, agricultural management, health care management and tele-medicine, maritime operations, management of payment transactions, and others.
Table 1: 3 Great advantages of identification of RFID supply chain [29]
| Item | Advantages |
| Increase the visibility of assets | RFID asset monitoring to increase inventory usability and visibility. This ensures that RFID tags can be read from all over the facility so that workers can easily display each item’s location and value. Supplier chains can overcome issues created by bad management, misplaced components, tracking and manual process failures by increased transparency. Naturally, it can easily move things and make decisions about fly changes. |
|
Improve employee productiv- ity |
RFID technology workers do not have to search for any items. No wasting time on tedious processes like scanning individual barcodes, finding the wrong tools and devices, and calculating inventory. This technology will increase the speed of sales of jobs and projects, lower labor and transportation costs, and improve the plant’s overall productivity. Manufacturing and shipping products in unmanaged facilities are challenging and slow. By eliminating manual steps, human error and monitoring can avoid. Corrections can take a long time to improve inventory and asset visibility. |
|
Reducing risk, theft and loss |
RFID asset tracking to quickly and easily access inventory information and locations to track during items storing, distributing, or replenishing. With this type of visibility, there is little room for mistakes or mischief. Track each asset’s movement in the facility to consider all items and pallets, minimizing costly risks and reducing misalignment’s and losses. Struggle against counterfeiting and theft; Promote callbacks. It is imperative to avoid such errors as much as possible, since fixing these errors can lead to litigation, high fines, or loss of customers, as well as time and money. Full transparency and real-time information on inventory and assets increase profitability for significant organizational and productivity improvements. |
2.1 Review Papers of RFID applications
This section discusses recent studies related to RFID applications in the IoT world.
- In [30], building the Green Campus in IoT Architecture, RFID technology is used to detect students entering the lab. The system will read, and store data related to students or any-one entering the lab. Middleware acts as a connector between temperature sensors, air conditioners, RFID, and computers [31]. Each of these tools has its information. This information is used to determine the number of labs that should open to students, when the air conditioner needs to turn on, and finally, to monitor computer usage correctly [32]. The effectiveness of this system is when:
- Laboratory management runs smoothly according to consumer demand.
- The computer management mechanism can adequately monitor to save energy on laboratory equipment.
- Energy-saving can do excellently when the air conditioner was only functioning when the laboratory temperature reached.
- In [33], the System of global positioning and geographical information, RFID, general packet radio service and webcam combined into one device. The RFID reader in the camion reads both the customer and the bin details [34, 35]. This system improves waste management and decreases waste emissions resulting in ozone pollution [36].
- Researchers in [37] introduced a new authentication strategy for home health applications using low-cost RFID tags. For systems where RFID tags need not be measured, only data stored for their storage sent. A tablet container has stored with the RFID tag inside the patient. The RFID reader receives the details when the patient recovers the [38] bag. In the RFID tag, the information is encrypted. Only valid ID tags and ID readers can decrypt the data decryption key – valid RFID tag ID and RFID reader, which generate the use key. Authentication between RFID tags and readers of RFID will combat several attacks, including tag-spoofing, reading readers. One of the benefits is that it reduces the likelihood of human error in data collection and that doctors can also provide reliable information on patients [39].
- The environment, including the distribution system, has changed considerably in the past few years in [40]. With consumer demand changing, distribution structures are becoming increasingly centralized and globalized, and public changes such as deregulation, innovation and IT dissemination are moving forward. Simultaneously, there is a substantial demand for reducing CO2 in logistics processes to solve global environmental problems. As a result, RFID (Supply Chain Management) technology was designed to use CO2 reduction levels, deemed an impact identification object, to be identified and thought that improvement would be a criterion. To deploy an SCM with high efficiency, the information would be necessary, namely in real-time, which is a turning point for success
or loss. In this respect, the RFID tag can be a useful tool for automatically defining status by merely placing at the point of departure or arrival items, collapse containers and pallet vehicles using RFID technology. This process would help to understand conditions in real-time, such as the transportation of stocks and shipments [41]. They, therefore, expect RFID to be a practical tool rather than an existing barcode system and argue that the introduction of RFID is a new way to view the information in the SCM. The CO2 reduction ratio is estimated by researchers as a function of transport expenses, with decreased labor costs, thus, reducing transport expenses. The amount of energy used, such as a roadway, is commensurate with transport weight (t) and distance (km). It means that transport costs and energy consumption are positively correlated. Since CO2 is proportional to the amount of energy consumed, emissions of CO2 may also decrease if power is reduced. The decreasing costs of transport can thus reduce CO2 emissions, with a definite link between energy reduction and CO2 emissions [42]. Consequently, the transport CO2 emissions reduction rate was 3.2% as an effect of RFID introduction.
- In [43], while metal fractures in the automotive industry have been a topic of productive study, plastic recycling in vehicles is poorly understood. It is now key to effective recycling of vehicles, due to legal requirements. Besides, the key problems faced are recognizing plastics and the technological standard of logistics activities, as well as scarce resources related to plastics. Therefore, authors in [44] introduce the RFID framework that automatically recognizes, register, distribute, and search for information during the product life-cycle. The research produces an efficient decision support solution (DSS) in a case study on automotive plastic recycling. DSS has applied during the life-cycle of the drug. It can be divided into three phases depending on the product life cycle management (PLM), initial life expectancy (BOL), life expectancy (MOL) and end-of-life (EOL) of the contemporary product [45]. BOL functions as product design, a manufacturer’s preparation, and process management. MOL is used to assist with product repair, condition diagnosis, and prognosis. At the other hand, the classification of EOL has many meanings, including the duty to comply with economic benefits and legal requirements. The DSS method is as follows [46, 47]:
- Throughout the BOL and MOL phases of the product life cycle, the flow of knowledge completely facilitated by knowledgeable systems such as CAD / CAM, Product Data Management (PDM) and other Knowledge Management systems used successfully in the Automotive Plastic Recycling industry.
- Often the knowledge that comes to the consumer about the product is incomplete during the transfer process from MOL to EOL.
- Data sources from MOL tell BOL that drug producers disrupted after product sales. The findings are typically based on BOL data, or limited but imperfect practical experience, based on full knowledge of past transactions.
Then, experiments used to produce missing information, but the cost of EOL operations increased significantly.
- RFID technology is then used to fill the knowledge gap and make product information reliable, accessible, timely, complete and available whenever needed during its life cycle. Different information can be collected and transmitted using RFID technology via MOL and EOL phases.
- Using the unique identifier stored in the RFID tag, EOL will obtain the information required to evaluate the recovery path from the product life-cycle information service. At the end of the support phase, the data collection unit is integrated to collect information from the stores using RFID technology.
- Researchers in [48] provide the RecycleBank with the resources it requires to organize recycling activities for households, using RFID systems to allow municipalities to calculate the number of recycled materials per household. They have created a community-friendly approach with advanced, creative technology to tackle the rising cost of waste collection. Weight of recycled plastic turned into incentives for RecycleBank. Hundreds of local and national participants can award it. In collaboration with Texas Instruments, RecycleBank offers an RFID that adds low-frequency RFID tags with exact recycling containers and includes integrated RFID readers fitted to a counterbalancing system [49]. RFID tags developed and implemented for RecycleBank, stores Serial Number (referring to the name and address of the container owner), reads and data transmitted to the internal computer of the vehicle. The data collected are then transferred to the data collection and processing system of RecycleBank. Personal data (name, address, etc.) not scheduled for the tag. Only the recorded serial numbers are kept in the secure database of RecycleBank. The proprietary RFID tag stores provide unique advantages for waste and recycling applications with low-frequency technology as a weather-resistant, all-weather, secure solution that works in snowy, wet, or harsh environments throughout the world. Labels must be physically cute while preserving their technical characteristics over the life of the [50] container. The results are as follows:
- Within one week, the recycling rate in New Jersey, Cherry Hill City, increased by 135%. The average household recycled 12 pounds of recyclables before RecycleBank. Homes now earn an average of over 26 pounds each week.
- The city of Wilmington, Delaware, has been recycling in just six months from 0% to 37% using the RecycleBank programme.
- Elk City, New Jersey, averages 16 tons per week before RecycleBank of recyclable material. The municipality generates an average of 42 tons of recyclable material per week after the usage of RecycleBank, a rise of 136%.
- The case study in [51] demonstrates a highly advanced waste electrical and electronic equipment reuse and recycling program (WEEE). This center is named the Multi Life Cycle Center (MLC), using state-of-the-art advances in automation and IT to provide cost-effective and environmentally sustainable processes. WEEE is back to a valuable commodity [52]. IT and communicators, household appliances, electrical and mobile devices, toys, and recreational equipment are product categories subject to reuse. All other classes of items are stored and recycled. RFID technology is used for communication and organization, together with reverse logistics systems. This technology can be used as a monitoring device that transparentizes and prevents misuse of the WEEE stream. Furthermore, container level measurements are currently being tested, so that it can improve the collection route of the truck and prevent theft. A special reading station is located at the collection point to allow continuous monitoring to collect RFID information [53]. IoT is the link to the Internet of objects utilizing several information recognitions tools such as RFID, infrared sensors, global positioning systems, laser scanners and the identification of certain system information according to the accepted protocols. The computer is a large network. IoT can be used to define wisely, locate, map, control and manage to share information and communications [54]–[55]. Main IoT technologies, software, research and development technologies, external layers, network layers and device layers.Table 2 displays main perception layer technologies.
Table 2: Key technologies in the perceptive layer [53]
| Key Technology | Performance Description | Application |
| RFID | Recognition and identification of objectives. Its purpose is to describe the object. | Application stage |
| Sensor | Sensitive organs, providing raw data. | The exploratory stage |
| Intelligent embedded technology | Intelligence is the target of IoT. | Experimental stage |
| Nanotechnology | Enables the interaction and connection of small objects and reduces system power consumption | Research stage |
- IoT requires finding, scanning, monitoring, and handling, and not just ”connecting objects.” As RFID is a ”speaker” technology, RFID technology plays a vital role in critical technologies in the IoT layer of perception [56, 57]. RFID technology is, therefore, the first choice to establish a full system for IoT identification. EPC encoding, RFID EPC systems and EPC network systems are critical applications of RFID technology with RFID tags in the ”IoT” EPC environment. In addition to handling individual objects, IoT encoding discovers objects at any time and enables coded requests, statistical tests, unique e-commerce categories and open information for objects. ”One single-code entity.” EPC encoding technology [58, 59] can best serve this need. The EPC RFID framework is a module for collecting codes automatically and shapes the EPC information network systems for local internet networks.
In the meantime, the global internet network is a platform for handling and flowing knowledge [60].
- The goal of the analysis in [61] is to establish an overview of current RFID research from an IoT overview. The analysis includes passive UHF (860-960 MHz) devices ( e.g. low battery) that can provide an effective sensor network to track human health and control the efficiency of the controlled environment [62, 63], with sufficient measurements and readings. Environmental sensors that calculate physical parameters such as temperature, humidity, and toxic substances may calculate the health of the environment and evaluate their human health relations [64]. Wearable and implantable labels offer more contextual knowledge about a person’s in-room appearance, activity, contact with the individual, and innovative applications based around the body. Data on the health status of artificial organs can be produced [65]. When operating with special compounds or inter-linked with chips which include detection functions, passive RFID tags can detect changes in environmental chemical / physical parameters. Autonomous RFID tags are an important instrument for designing body-centric healthcare systems that are fully transparent to the consumer [66, 67] for touching and approaching the body. Most specifically, wearable passive UHF tags have long been technical tabus because of the significant power outages caused by human tissues. Previous body center network studies are mainly focused on active computers [68, 69]. Over the past five years, the development of commercially available low-power RFID (COTS) chips has changed gaming entirely, creating and testing of several prototypes of bodycentered, sensitive, distance-readable tags compatible with remote-controlled monitoring [70, 71]. Since high electromagnetic losses characterize the human body, antenna power output is meager and the required reading distance for passive devices. The performance of the antenna power is deficient. This combination of wearable and ambient tags helps to track the situation of children, people with disabilities, and the elderly, identify human behaviors, and build passive RFID systems in a fully-passive manner [72, 73].
- Researchers in [74], which explicitly addresses the safety criteria for RFID validation schemes, have submitted an authentication scheme based on elliptical curve cryptography (ECC) suitable for their protection and health care climate. The aircraft device Classify Friend or Foe (IFF) was the beginning of the RFID technology used during World War II. The benefits of RFID are that it is easy to use RFID tags, has read/write power, does not need long-distance RFID readers communication, and can simultaneously read multiple RFID tags [75]. RFID technology in the healthcare field is applied to the verification [76, 77], birth and patient recognition [78], medical treatment detection and confirmation [79], healthcare centers [80] and surgery sites [81]. A typical healthcare network with RFID technology [82], as shown in Figure 4. RFID authentication is one of the most critical measures to ensure secure communication inside the RFID system. However, there is a wide range of security features in the process of sending messages between RFID tags and RFID read-
ers. Some researchers have established the safety criteria for secure RFID communication and reliable and effective authentication schemes when it is applied [83]. Mutual authentication between RFID tags, RFID readers, and servers are among the security requirements. Besides, before transmission, the confidentiality of sensitive information contained in the RFID tag must be encoded. The identity of the tag must also be protected for the protection of the owner [84]. The next requirement of protection is to validate the RFID authentication scheme during the life cycle of the RFID tag that gives alerts updating the confidential details that have shared during the implementation of the authentication scheme. It meant that the verification scheme would be invalid if the modified coordinate is lost. To ensure secure transfer [85], Transfer Protection requires an RFID authentication scheme. For certain RFID authentication systems, if the enemy successfully retrieves sensitive information from the RFID tag, it can detect the last position in the tag. It will severely breach the privacy of the user. As the RFID tag validation process is required, scalability, RFID authentication scheme must scale, an RFID device server must find the corresponding records in their database [86].

Figure 4: Typical RFID-based healthcare system [82]
As the number of RFID tags increases, the device does not scale if the workload of the search algorithm is significantly increased. RFID authentication processes must defend against multiple attacks, duplicate attacks, tag defense attacks, server spoofing attacks, mid-level attacks, cloning points, and others. Resistance to attacks to ensure the security of RFID communication [87]. The researchers found that the ability and memory of tag calculations were minimal when comparing the performance and safety aspects of the ECC-based RFID authentication schemes to determine whether ECCbased RFID validation schemes are adequate for practical applications. Cost measurements, communication costs, and storage requirements for practical applications are, therefore, important. The researchers investigated and found that most of the current ECC-based authentication scheme proposed cannot comply with all safety requirements. To ensure secure contact, researchers will first build acceptable safety models for ECC-based RFID systems by using ECC-based techniques in RFID systems. They then developed an ECC-based RFID authentication system that protected security models securely.
- IoT consists of an increasing number of interconnected smart devices that reduce hardware costs and architectural complexity, where communications occur at any time or anywhere. The reading of ultra-high frequency RFID tags is a cost-effective operation because of its technology and the reading system for these frequencies. The researcher proposes an architecture that reduces the cost of ultra-high frequency RFID reading equipment operating with cloud computing and micro-services in an infrastructure. Due to the scalability and management of large quantities of data that can be produced using ultra higher frequency RFID tags and the nature of the architecture linked to the theme of the research, the use of cloud and micro-computing was required [88]. To collect data and analyze the findings, the architecture proposed to address the research questions intended for the case study of this work has been created. After the RFID read tag has been detected by SparkFun Simultaneous RFID Reader — M6E Nanoboard, the Asset Micro-service must interact with the Read microservice to see if a similar physical object remains.
This test takes place via the RFID tag area Electronic Product Code (EPC) present in the Asset microservice relational database and the Read microservice NoSQL database. Since the RFID tag EPC is a unique identifier, this is the only field needed to check whether an RFID tag is in the Asset Microservice database, identified by the SparkFun Simultaneous RFID Reader — M6E Nanoboard and registered in the Read microwave database. The monitoring microservice is used to view the collected data after telemetry information has been collected from the SparkFun Simultaneous RFID Reader — the M6E Nano Temperature, Position and Intermittent Connectivity Information through Microsoft Azure, the IoT Hub service. The result obtained from the case study as below:
- The board was able to read RFID tags with a distance of approximately 1 m and could read approximately 100 RFID tags per second only with its internal antenna. Having an external UHF antenna together with the board will improve the board’s reading power. If the reading distance has a minimum value of the required project execution, the use of an external UHF antenna is needed.
- There were no charges for the software provided by Microsoft Azure. The non-cost is due to the use of all the free layer services. The cost will slowly increase as additional resource resources such as further computing, memory, or monitoring of other IoT boards increases.
3. Security of RFID
Some of the advantages of using an RFID device is that it performs tasks to classify, achieve efficiency and simplify its implementation automatically. Even these added benefits do not guarantee personal data protection. Therefore, when designing an RFID device, several criteria must be addressed to provide the highest degree of security. They are exchanged for the user or included in tags sent to the backend server. Data is private, accessible, and not modifiable (CIA). The safe maintenance and operation of the entire network A fully secure network continue to be a challenging challenge with numerous attacks and threats which that happen in various scenarios at the same time. RFID forgery: RFID can split into three groups by processing ability, which are simple tags, symmetrical key tags, and public-key tags. Basic tags are not encrypted and can be fooled easily. Supply chain and the operation of the travel industry are well established. To access or test product reliability [89], an attacker might write information to a primary black tag or change the data in a simple write tag. Many articles listed in the solution identified typical attacks which can occur on RFID systems during the investigation. Some of the most common attacks are shown below. In the literature, many steps and features have been suggested, including pseudorandom solutions, anonymous authentication schemes, symmetric and asymmetric cryptographic algorithms, and other hash-based systems. Several review studies related to the following security attacks are discussed in subsection
3.1.
- Eavesdropping
These attacks include eavesdropping on the network and recording examples of all interactions between the tag and the reader. The primary purpose of this attack is to collect data and use the information collected.
- Denial of service
Denial of service is the creation of a device that cannot use in an RFID system. An example of a use case for this attack is spam, which is sent to readers requesting a specific tag frequency to deactivate the reader.
- Cloning
The primary purpose of a clone attack is to spread RFID tags. Reverse engineering technology allows it to change and duplicate the label by extracting all the functions of the vehicle, precisely the secret key.
- Tracking
When detecting attacks, the tags voluntarily tied to a person, and their presence and movement are detected while the attacker’s leader is inside the tag.
3.1 Security Review Studies
- The IoT is the opportunity to have a means of distinguishing everyday objects and another way of interacting with each other. There is an extensive range of IoT technology domains like smart houses, smart cities, wearables, e-health, and others. Thus, tens and even hundreds of billions of devices are related. These machines would have intelligent capabilities for collecting, evaluating, and even making decisions without any human contact. Under these situations, protection is a supreme necessity, and authentication under particular is of great importance given the harm that might result from a malicious, unauthenticated device in an IoT network [90]. This paper provides a general overview of the security issues and requirements in a layer-based approach in the IoT context. Instead, it offers an updated survey of the various IoT authentication schemes. It contrasts and analyzes the current authentication protocols through a multi-criteria framework, showing their advantages and disadvantages. The researchers found out the following:
- The authors proposed a lightweight RFID tag authentication protocol based on Physical Unclonable Functions (PUF) functions. There are three transactions in the protocol: tag identification, authentication, and update. The tag reader identifies the tag in the first transaction. The second transaction is a test where the reader and the tag verify each other’s validity. The latest used key for the next check should be retained in the last transaction (Update).
- The authors have allowed the authentication and perceptibility of the IoT devices to secure the supply chain of connected devices through an RFID-based solution. The process of authentication consists of two steps: the verification of the connection between the tag and the IoT system and the tag perceptibility.
- The RFID reader is connected to the Internet in an IoTRFID network to form an IoT end unit. On the other hand, it is linked via RFID communication protocols to the tagged objects. The tagged object is portable and transfers from a reader to another, so authentication is necessary to verify another identity. The device is vulnerable to security attacks, such as impersonation or clone attack, because of the absence of cryptographic features in RFID. The authors proposed an authentication protocol to be used with lightweight encryption algorithms in the case of IoT-RFID use.
- The authors suggested an offline authentication for PUFbased RFID-tags to prevent cloning attacks on the RFID tags. It combined security protocols for identification and digital signature. The tag generates a hidden key in authentication by questioning the PUF and gathering the answer. Such a reaction with the support data will create a certificate that will be stored inside the tag’s ROM. First, the tag is authenticated by the verifier verifying the certificate validity. The authors proposed a PUFbased authentication scheme for the classic RFID tags to provide anonymous authentication for RFID systems. Then, they created an enhanced PUF noisy atmosphere scheme. The main downside of this scheme is not to re-feed the server with new Challenge-Response Pair (CRP) when the current pool is empty.
- The authors suggested a shared authentication scheme for IoT RFID-based applications in fifth generation of mobile networks (5G) by providing a cache to the user, storing the keys (used for authentication) for the tags recently visited, speeding up authentication, minimizing computation costs and the storage security. On the other hand, the authors in [91] has been proposed authentication methods for heterogeneous networks which can be applied to RFID systems as well.
- The detection of ultra-high frequency radio frequencies (UHF RFID) is becoming a central technology in the Internet of Things. It allows batteryless and wireless nodes to be deployed like sensors and actuators. Safety is a critical issue because of its possible transmission range is greater than 10 m, and the ability to hold sensitive information. For this reason, in 2014 the International Organization for Standardization released several UHF RFID crypto packages under the ISO-29167 standard. Nevertheless, no UHF RFID readers are currently available. In order to cope with the rapid growth of software-defined radios, ”simple” and versatile readers are required. This paper illustrates a way to implement the decryption of ISO 29167-19 RAMON on a prototyping reader platform based on National Instruments PXIe chassis. PXIe programming is based on LABView. The first LABView implementation revealed that decryption only requires 51.3 s. It would mean being able to process just one tag per minute.
Therefore, a prototyping platform intended to conduct practical experiments in the creation of new technology in UHF RFID systems is not suitable. Therefore, they prefer a different approach. The LabVIEW also acts as a platform and monitors the transceivers which are integrated. Nevertheless, a TCP/IP connection to a Java application is also provided. This Java code is decrypted. A TCP/IP link is used to return the decrypted plain message to LabVIEW and can be further processed [92]. The results are as follows:
- The average time spent with LabVIEW in tandem with the Java app is 2.2 ms, which improves the timeoptimized approach to LabVIEW by 23,318 times. Within LabVIEW, the principal difficulty is that large numbers are difficult to deal with since they are widely used in encryption. The problem is not limited to the implementation of the RAMON method by outsourcing the calculation in a Java program. The approach can be used for any encryption method and for other processes in LabVIEW which handle large numbers. In this way, the RAMON encryption can be incorporated into the existing reader protocol and a fully working, easy to adapt reader can be obtained. Particularly for UHF RFID systems, it creates entirely new possibilities for rapid growth.
- The medium of contact between the tag and the reader is vulnerable to multiple threats in conventional RFID systems, including denial of service, spoofing, and desynchronization. Therefore, the confidentiality and validity of the data transmitted can not be guaranteed. In this paper, the researcher proposes a new RFID authentication protocol based on a lightweight block cypher algorithm, SKINNY (short for LRSAS), in order to solve these security problems. The 128-bit block size and key size n SKINNY encryption algorithm are being used to test the implementation in passive 96-bit EPC-encoded radio frequency identification systems. The tag and the reader need to be mutually authenticated when implementing the LRSAS protocol, and the SKINNY algorithm encrypts the information used by the tag and the reader for mutual authentication. The key is already stored during the initialization process. This paper selects a SKINNY lightweight block cypher that has the advantages of low hardware power consumption and low computational complexity based on ensuring safe encryption. It can be used in Things terminal equipment’s low-cost Internet [93]. The results are as follows:
- The protocol conceived in this paper uses one of the algorithms for SKINNY encryption and can accommodate 96-bit EPC encoding. In the encryption process, the calculation time for the round function used by the SKINNY encryption algorithm is shorter than the calculation for Hash, ECC, and Present encryption. However, the overhead measure also applies to low-cost RFID tags. Additionally, the tag’s overhead storage is 3 L which significantly reduces the tag’s storage capacity compared to other protocols, and reduces the complexity of the storage structure’s logic gate design. Besides, the protocol has five information interactions in the mutual authentication of the tag and the user, and the total amount of data collected and transmitted is 6 L, which is relatively high, thereby ensuring the efficiency of the information interaction.
- Concerning the number of logic gates equivalent, multiple versions of SKINNY have varying numbers of logic gates equivalent. This protocol uses version SKINNY128-128; the equivalent number of logical gates is 2391, less than 3K. It can also be used in low-cost tags. Furthermore, the number of equivalent logic gates for other protocols often allows specific security attacks to become vulnerable.
4. Challenges and environmental implication of RFID application
RFID is an exciting technology, but it does pose many technological problems and implications.
4.1 Challenges
The challenges of RFID technology applications in IoT were divided into seven: collision problems, privacy and security concerns, interference issues, miscellaneous challenges, technical issues, interoperability issues and energy efficiency.
4.1.1 Collision Problems
Electromagnetic interference can cause tags and readers to fail, leading to wrong choices. For tags and readers using the same radio frequency channel, multiple transmissions between the reader and the tag can cause problems in a collision. To recognize multitag communication to promote the implementation of large-scale RFID systems, a secure and active collision avoidance protocol is required—a database tree protocol, a binary tree protocol, a split system protocol and others. Nevertheless, not all protocols produce the requisite efficiency as their identification efficiency is less than 50% commercial. For a new, better protocol will look for the best features of the detection protocol [94, 95].
4.1.2 Privacy and Security concerns
RFID authentication tags and security issues can affect people and organizations significantly. Tags are not properly secured and they considered an easy target to eavesdropping, DoS strike, analyze traffic and others. Besides, unauthorized readers can view multiple codes, which can breach privacy, without single access control. Predictable perceptions of tags can accompany secure tags. Traffic analysis attacks may jeopardize the privacy of the user. Appropriate confidentiality and protection protocols are needed for RFID systems given the associated costs. Extensive work is underway to define and incorporate cost-effective protection and privacy protections to improve RFID systems’ reliability and usability. Several light-weight protocols have been proposed, but still have high costs and low protection and do not completely solve security issues. An excellent work section is available to develop ultra-light encryption protocols for low-cost RFID systems [96].
4.1.3 Interference Issues
Recently, a very high-frequency passive RFID (UHF) system has received much coverage. UHF RFID systems are widely agreed that many commercial applications, such as supply chain management will revolutionize UHF RFID systems. In the 860-960 MHz band more popular supply chain companies like Wal-Mart and Tesco will promote the use of UHF RFID systems in supply chains. However, with this distribution, dozens or hundreds of readers will work closely together and trigger to severe interference [97]. The UHF RFID interference has three types: tag interference, reader-to-multitag interference and reader-to-reader interference. The specifics of the intrusion issues are shown below.
- Tag interference
It happens when the reader simultaneously supplies power to several tags, and each signal reflects the reader. Owing to the dispersion of dispersed waves, readers cannot differentiate between individual IDs and marks. Anti-collision mechanisms, called binary trees and aloha, are therefore essential.
- Reader-to-multi-tag interference
It occurs when the mark is at the intersection of two or more reader requests, and the reader tries to interact with the tag simultaneously causing the tag to behave and interact unwantedly.
- Reader-to-reader interference
These are activated when a signal from one reader hits another and can also take place if the readers’ surveys are not intersected. Interference between readers can cause serious problems when using UHF RFID systems, as remote reader transmitted signals are so powerful that precise decoding of messages transmitted by neighbouring tags is prevented.
Active, semi-passive and passive RFID tags add comfort and prominence to RFID technology in our environment. Such tags are cheaper to produce and can be small enough to suit virtually any product. The type of RFID device works is shown below. Readers and tags focused on wireless two-way communication. The reader transmits a signal in passive RFID tags which induces a current in the tag to supply power to the transmitter of the tag. On the contrary, an active RFID device does not require an induced current to transmit its presence. Wireless communication may create a difference between RFID and other wireless technologies that are used in the workplace or data center since other RFID technologies often operate in the atmosphere and cause significant disruption [97]. Two classes ought to consider for new action. First, interruptions prevent data transmission properly and reduce the efficiency of one or more devices. Second, the danger of interpreting one signal from one device is that data from another is valid. The key cause of this disturbance is the environmental implications of use. This problem occurred in the past when the RFID tags placed on metal or liquid containers. The tag is inactive in both cases and refuses to respond to the reader. Recent advances allow these problems with proper antenna and tunnel design to tackled during the planning process. The UHF system may cause interference with the radiation of the power signal. Passive systems, on the other hand, are less vulnerable to intrusion than active systems with markers continually shifting. Crosstalk between RFID and WLAN or WPAN such as Bluetooth is another interference scenario when devices have a joint or an adjacent frequency band. Several cases of interference between wireless microphones and wireless endoscopy recorded in the medical field [98, 99].
- Active and semi-passive RFID tags
It uses an internal battery for the circuit. Active tags use an array to transmit radio waves to the reader, while semi-passive tags depend on the reader for transmitting power. Active and semi-passive tags reserved for expensive items capable of reading long distances, transmitting high frequencies from 850 to 950 MHz and reading more than 30.5 metres. If the label needs to read from a distance, an additional battery can increase the name range to more than 100 metres. It occurs when the mark is at the intersection of two or more reader requests, and the reader tries to interact with the tag simultaneously causing the tag to behave and interact unwantedly.
- Passive RFID tags
It entirely depends on the reader as strength. These tags are read and produced for use up to 20 feet (6 meters) and with disposable consumer goods.
4.1.4 Miscellaneous Challenges
Several other issues prevent RFID devices from spreading too. The key issue here is cost. The RFID tags are more expensive than the [100, 101] written stickers. A further issue is the complexity of the RFID system. They are owing to their high-reliability readers, and labels are not on the market yet. Moreover, there is no guarantee of accurate recognition. The incorporation of RFID systems into the current network is another big problem needing a solution for using [102], large RFID systems. The designers need to know the approach to incorporate the new RFID system into the current network in a successful development phase.
4.1.5 Technological Issues
Implementation issues are most apparent and should be dealt with immediately. Some papers dealing with technological issues such as durability, precision, and contact with metals are still in the pilot process. For DHL, read speed accuracy is not 100%, because Tag interaction readers do not comply with defined specifications [97]. Even, it is not feasible to prohibit maximum use of short contact tags. The concept in citeb101 is to make sure that the people do not forget the process of activating RFID devices.
4.1.6 Interoperability Issues
If the RFID device is not working alone, but in conjunction with other electronic devices, the issue of information becomes apparent. For example, an RFID Smart Vareflyt system can operate independently, but will not work if it combined with an existing data system [100]. This question occurs when the real data is different from the reported data, does not change, or involves correction from other sources. On average, the accuracy rate in Nestle Italy’s system is only 80-90% [99], due to the order output depending not only on the role of the RFID portion but also on the RFID system and the entire enterprise policy [99]. However, one of the hardest problems facing RFID technology is privacy and security. As corporations and public agencies continue to search for collaborations, sharing resources poses obstacles that involve sophisticated organizational solutions. The most challenging problem in the case of Smart Vareflyt is not just the issue of data incorporation at the knowledge level, but also the exchange of information and resources and the application of competition law to the level of the company [100].
4.1.7 Energy efficiency
The energy-efficient passive tag in the RFID device is a preferred option because it used without the need for an on-board energy source. The selection of passive tags is, however, limited compared to the active tag, which used on a broader scale. Nevertheless, the inactive energy efficiency tag is still an open research field that needs to be addressed [103]. As power usage decreased, energy efficiency improved. Several studies on power usage when using the RFID technology are discussed below .
- The first large-scale backscatter communication system was developed by researchers in [104] for reflecting signal from an RF source to synthesize data packets, which are then decoded by a receiver. It has two significant drawbacks, and the backscatter must first organize the information so that the receiver can transmit it at a signal force less than -135 dBm and work efficiently in the event of robust external interference. Secondly, backscatter signals developed using simple, affordable standard hardware, which makes it simpler to implement and improve the design needed instead of dedicated receivers for costly backscatter signals (e.g. RFID readers).
- The result shows that wireless power consumption, including Wi-Fi, BLE, ZigBee, Lora, and SigFox, consumes 10-50 mW of electricity, which is 3 to 4 magnitude orders higher than the system’s energy consumption. Backscattering technologies, including RFID, passive Wi-Fi, and LoRa backscattering technologies, however, consume just 9.25µW for continuous frequencymodulated chirps generation and harmonic cancellation.
- Researchers in [105] introduce an on-board digital temperature sensor with perovskite PV-RFID. This sensor can transmit temperature data wirelessly under sufficient lighting within a distance of up to 4 m. It is converted from light with perovskite PV into ICs and RF signals that used as contact links. The user acts as a portal to the Internet between these hundreds of nodes.
- According to the simulation performance, the overall energy consumption of the sensor depends on the sensor load (the number of sensor measurements per hour). For instance, a 20,000 / hour measurement requires approximately 20µW of power (calculated with a constant current of 6/muA in stand-by mode and 30µA in 8 mm a 1,5V input voltage each measurement).
- Photovoltaics (PV) for use by researchers in [106] are the use of photovoltaics (PVs) to increase the energy available during the day, enhance read range and detection capability and add to integrated circuits (ICs) with minimum additional electronics.
- The researchers found that the IC’s additional power not only enhances the ability to disperse the RF energy needed for additional tag areas but also enhances the ability to measure and transmit sensor data. This versatile sensor is also suitable for long-term detection embedding in 3D structures if the battery can not replace it. Thus, using PV-RFID can build wireless sensors that are autonomous, inexpensive, and reliable over a longrange. The frequency of PV-RFID measurements is about eight times that of traditional passive tags. By reading a wide area of PV-RFID tags with a limited number of readers and antennas, it lowers the network costs. The PV-RFID sensor additionally records 0.14 million measurements in 24 hours. It shows how sensors can monitor and transmit critical environmental data at low cost, without batteries.
- PLoRa, an environmental backcast architecture that enables a remote wireless link for IoT devices without a battery, is available from the researchers. PLoRa uses the current LoRa transmission as a new signal, modulates the new signal into the standard LoRa chirping signal, transfers the data to another LoRa channel received by a remote gateway, and adjusts this original signal [107].
- The results of experiments show that the prototype of the PCB-PLoRa tag backscatters an environmental broadcast of LoRa that is transmitted from a local LoRa node (20 cm) to an entrance up to 1.1 km away, with data accessible indoors or 284 bytes every 14 minutes. Simulate a lower power FPGA 28 nm prototype whose digital baseband processor delivers 220µW in power consumption.
4.2 Environmental Implication
RFID tags are used for managing product movement from factories to store in cartons and pallets. RFID has a great many useful applications for the world. RFID also has environmental drawbacks at the same time. The next topic will concentrate on ways and concerns that help create useful solutions and reduce possible impacts on the environment.
4.2.1 Reduced traffic using RFID
In order to pay for tolls, RFID congestion, and area pricing systems now deliver major environmental advantages. Automatic charging reduces downtime as well as braking and acceleration at the mail stop. Through the use of RFID repeaters on the New Jersey Turnpike tolls, 1.2 million gallons can save annually, air pollutant emissions decrease, and travel times decrease dramatically [101]. London has lowered the congestion level by 26%, nitrogen oxide, and particulates (PM-10) by 15%, and oil usage inside the congestion billing zone by 20% [102]. With the surface charging network introduced in Singapore since 1975, circulation has dropped by 45%. In 2006, the Stockholm scheme had reduced carbon dioxide emissions by 10 to 14% [108]. While it is very effective to reduce traffic, air pollution, and energy usage, plans for congestion charges are not common. The framework became popular after implementation [107].
4.2.2 RFID transponders on curbside waste and recycling bins
The waste truck fitted with an RFID reading panel. The device recognizes the bin when a truck gathers it. In 2001, a German public waste management firm surveyed RFID schemes, unimplemented containers, and productive waste collection routes through data that were exposed and evaluated. The RFID system implemented reported an average increase of 2.85%. In cities with invoices focused on waste numbers, non-recyclable waste decreased by 35% on average, and total waste decreased by 17% cent on average. Contains recycling and non-recycling stuff [109]. As a result, almost half of the overall waste reduction accounts for a 35% percent drop in the garbage disposal, and the other half is for recycling. This finding is consistent with the US surrender program, which reduces municipal waste by 25-35% for disposal [110].
4.2.3 RFID for information on the consumer environment
Item level RFID tags may provide information about different goods as well as generic products. That sort of knowledge can use to identify tainted beef, poultry, or fast food. Regulators, the foodservice industry, and regular customers are helpful with this [111]. At the same time, users will test how far they have transported, greenhouse gas emissions, allergens, and much more. Manufacturers and retailers have commodity carbon labels where a UK Tesco supermarket network sets carbon labels on each product sold, calculating the amount of greenhouse gas released during the manufacture, transport, and consumption of each product [112].
4.2.4 RFID for refurbishment and reuse
The RFID tag increases the efficacy of recycling as the UPC process enhances companies’ productivity in the supply chain. For example, battery labels may make the sorting of cell types cheaper and more effective for recycling. Electronic equipment labels may connect to websites that show how to disassemble the device. Tags on hazardous goods, such as household chemicals, will define the material, how, and where to dispose of these [113]. Attributes on consumer goods make it easier to sell products online and are an extension of how UPCs used in the one-way supply chain where the majority of items sold today have UPCs. This code is intended for revenue estimation as well as for inventory control [114], distribution, consolidation, and managing. For RFID, instead of being discarded with it, it will leave the object’s security code. The product code will allow many kinds of recycling opportunities. It may create systems that encourage recycling or punish improper disposal by recognizing when recyclable (or harmful or valuable) products placed into the garbage (or garbage can or trash can). Recycling opportunities, such as bottling, are not new, but an automated product-based solution will minimize costs and promote for innovation [115]. RFID systems provide a modest incentive for recyclable low-value goods and a significant incentive for high-value and high-risk goods. One sidewalk recycling company will handle specific items electronically for different goods, different markets, and various geographic areas [116].
Product codes can be applied both as UPC and RFID barcodes. When a large amount of device is picked up in a curb or code and put into a truck quickly, RFID could be preferred over bar code, as RFID can read from other devices at the same time. The benefits of recycling not deemed adequate to justify the expense of the productlevel RFID tags. However, if RFID correlated with an item for other purposes, the side benefits of RFID processing can be significant [117]. The use of RFID for electronics replacement, roadside recycling, smart household waste disposal, the management of product deposits and returns in stores and recycling centers, and the collection of waste and recyclables in incinerators, landfills and resource recovery plants addressed in many different applications.
- RFID for Electronics Refurbishment
Electronic recycling companies typically recognize multiple labels, computer models, printers, or mobile devices related to the most crucial element of the faulty parts market in their product instruction codes. The recycling industry, the product supplier, or the whole industry union RFID labels in products may use these instructions to connect with databases where both parties may learn how to recycle papers. Will major component can have its RFID tag so that repairs can easily recognize parts and updates [113].
- Item-Level Curbside Recycling
The use of RFID transponders has addressed in waste management and recycling containers. Through extending this kind of method, residual or recyclable material can detect at the item level. It opens up a whole variety of reward schemes. Incentives (rebates and fees) sent to the customer based on what put on the bin. Municipalities can also pay recyclable collectors extra fees to transport dangerous and challenging things to handle, such as mercury-containing fluorescent lamps, and recycled collectors can quickly sell their collections if they know what they have in-depth. This approach raises problems of a technological nature. The objects in the bin are one or two feet of the antenna for recycling vehicles, and probably other side and rear products which can absorb radio signals. Although RFID tags can be detected theoretically in products in recycling bins and empty bins can be ejected in lorries, this has not commercially demonstrated.
- Smart Trash Cans
The RFID reader can read each object in the container for home recycling tanks. Drum items may either be sold online or published by traders. Consumers and businesses will automatically check for waste material and schedule recycling services. Online retailers check for the recycling containers, buy recyclable and reselling items, give back some of the consumer’s income, and leave vital recycling services (paper, plastics, artistry, metal). Home intelligent trash will play mostly the same role as the item level curb set. Intelligent home trash can be technically pure but probably a more expensive alternative than the identification of congestion objects.
- In-Store Recyclables Collection
RFID allows the storage in shop or recycling centers of recyclable items. Some retailers use recycled items already. Recycling Corporation Recycling Corporation (RBRC) provides electronics and electronic stores with batteries throughout the United States and Canada. For different computer producers
Costco has a standard marketing and recycling plan [114]. Mobile telephone providers accept used telephones as well. Retailers often use UPC bar codes to handle returns. The use of product codes to provide customers with discounts using RFID tags is economical and straightforward. Like every other voucher or swap system, retailers may benefit from a discount plan. Selling machines can also accept recyclable goods and offer cash refunds or credits based on details on the product label.
- RFID at Materials Recovery Facilities
To organize things in warehouses, incinerators, and dumps, using RFID readers. Modern materials recovery facilities include magnetic steel seams, aluminum vortex separators, and plastic seam infrared detectors. RFID devices can track small electronics and batteries. Previous studies have shown that RFID-labeled items such as batteries, small electronics, and mobile devices can obtain at a much cheaper collection facility than recycled [113].
4.2.5 Environmental drawbacks of RFID
Many consumer goods include RFID tags, including food packaging. Over time, the number of tags produced and discarded increases. Usage of the global tag will reach 2 trillion a year [115]. Such marks end up in urban solid waste or systems for recycling paper, carton, metal, glass, and plastic. RFID tags typically include copper, aluminum, or silver antennas as well as integrated silicon circuits, adhesives, plastics [116]. In short, the use of RFID materials and removable tag properties allows the avoidance of problems that cannot be degraded or recycled as RFID tags can prevent the recycling of various products and other materials [117]. When carbon-based conductive ink used as a substrate antenna and bio-based plastic, most RFID tags can be biodegradable or ecologically friendly. However, silicone chips may have environmental effects, which at the development and not the stage of life are challenging to deal with reliably. The processing of silicon chips requires considerable energy and water and significant emissions of pollutants. A specific problem was the pollution of glass, steel, aluminum, paper, and plastics recycling, discussed in turn below.
- Glass Recycling
Since silicon melts at speed other than glass, silicon RFID chips can pose problems for RFID tags attached to glass containers. If the silicon remains in the glass of the entire recycling line and the glass furnace, silicon beads can create in a new package. It is a potential weakness, especially for the media, and it shows that RFID tags used in the glass must be removed entirely or placed inside the lid and not on the glass itself [117].
- Steel Recycling
RFID tags can contain approximately 20 mg of copper. On a regular 20 g steel box, this corresponds to a working copper concentration of 0.1%, and the steel copper content accumulates with continuous recycling. It is rising steel consistency. Therefore, RFID tags for steel goods should be entirely removable or made with copper-free antennas. RFID tags mounted on aluminum do not impact the recycling of steel. Inadvertent aluminum falls from tags removed during the exothermic reaction at very high steel temperatures [117].
- Aluminium Recycling
Aluminum can be recycled with high-value many times. Flows of feed do not permit pollution. Pollutants shall be picked or removed by other means. RFID tags for aluminum items are either produced or made of eco-friendly materials.
- Paper Recycling
RFID tags will join an old carboard container in the recycling facility. The National Aeronautical Research Committee (NCA) tests have shown that copper foil antennas are kept intact and can be easily captured and removed during the entire hydro pumping process. The silver ink antennas, however, contain 2 to 3 microns of silver particles. Pilot experiments using labels containing around 16 mg of silver found that much of the silver in the dough remained. In certain cases, however, there was insufficient proof of rates exceeding the limits and regulations. Found in reverse water.
- Plastic Recycling
The use of High-density polyethylene (HDPE) for milk bottles, washing machines, and other applications. Application of polyethylene terephthalate (PET) in bottles and other applications for soda and wine. Some of the most often recycled plastics are HDPE and PET. In general, RFID labels applied to substrates of PET. Thanks to the denser RFID tags than HDPE and their isolation during the first stage of the HDPE recycling process, RFID labels are anticipated to differentiate easily from HDPE bottles during the recycling process. However, it is a struggle to remove RFID tags from PET bottles. PET is more than one (1.2–1.4 g / cm3) in specific gravity, and both RFID and PET fragments immersed in water. As RFID tags typically performed in PET substrates, the mass difference between PET and RFID tags may not be sufficient using cyclonic separation. Every RFID tag used on PET bottles should also be designed to be easily removed, either by non-PET substrates or other methods.
- Towards RFID biodegradable systems However, most RFID tags can not be biodegraded. These include petrochemicals-based metal parts, plastics, or other materials. Smaller tags also make it hard to isolate and recycle different label components. Recent researchers have developed completely biodegradable tags, in particular for medical and feed supply chain applications [118].
4.2.6 Environmental Sustainability
While most case studies at various rates have achieved environmental sustainability, Walmart’s case shows that the bigger the size, the higher the effect. A breakthrough in RFID implementation by Walmart that replaced the barcode system by Walmart decreased carbon footprint by 3.2% by allowing less product movement because of improved product visibility and handling and improved inventory management [116]. The TruckTag project is another new environmental protection program. RFID tags allow for automatic high-speed safety checks, reducing traffic jams, and improving air quality by reducing the lorry idle time [116].
4.2.7 Business Value
The average organization aims to reduce costs when introducing a green RFID scheme. The City of London School for Girls, with its RFID temperature sensor networks, will reduce the cost up to 80% compared to its wired networks and gain greater control over room temperature via RFID [117]. Using RFID to monitor temperature, Nestle can save up to 10% on energy-related costs, reduce harm, and boost efficiency. Although direct cost savings are legendary, indirect cost savings should also be acknowledged (such as loss-oflife insurance and increased quality). Many businesses use RFID for revenue generation. Recycle Bank, and Recycling Rewards offer recycling coupons to customers to launch a new business model and promote more recycling families. Bank Recycle has raised its sales by collecting more recyclable products. The use of RFID saved over 318,000 trees and 21 million gallons of petroleum in the Recycle Tank [44].
4.2.8 Social Responsibility
Green RFID initiatives have an impact not only on the safety and sustainability of the ecosystem of business but also on environmental conservation, which adds value to customer-to-company relationships. It is because consumers know what they want in investment in the environment. Nestle Italia uses an RFID-compliant´ management framework to support green ads and to boost brand identity successfully. Under public demand scrutiny, major businesses urgently have to meet their social obligations [99]. Through its smart truck initiative, DHL has minimized CO2 emissions and fuel consumption by automating package scans to speed up driver handling of the parcels and idle periods to shorten the truck engines during delivery. In more environmentally aware businesses, the culture in which they work may have a positive effect. People and economies with their bank recycle point have raised more than one million dollars [97].
5. Benefit of Greening IT
Green technology is a concept that includes almost every type of practical use of technology to benefit the environment. Despite industrial technology advancing so far, its green predecessors are supposed to do the same. Many green technology examples include items that come under the given use of the subject, such as green chemistry, environmental monitoring, and others. Anything that fits the accepted concept of green technology will do one or two things. It is either to preserve or to help the ecosystem in any way. The words ”environmental technology” or ”clean technology” can also be used for this technology. Green tech’s primary goal is to protect nature and help reverse the adverse effects humans have had on the planet [118]. Green technology enables us to turn our contaminants and waste from unnecessary by-products into a sustainable workforce that benefits humans and the environment. Green technology has some of the best recycling methods: turning waste into fertilizer. One of the most significant benefits of green technology is that it helps people recycle things like water and air. Green technology leads to emissions reduction and air purification for future generations. Above all, green technology has permitted people to save vast quantities of resources, dramatically reducing the remaining carbon footprint. Alternatives to systems that use a high volume of electricity and fuel are provided to the public at this very moment. The use of items such as electric vehicles and solar panels has become natural, daily, and the Planet could not be the best. It is highly recommended that people use environmentally friendly tools and appliances to help facilitate this energy saving. The ability to rejuvenate ecosystems that have suffered a great deal because of the effects of human carbon emissions and other factors is also a tremendous use of green technology. The use of this technology replants trees, replaces plants, and replaces entire habitats to their original glory. Besides, waste is collected and recycled, so that animals, which once existed, will now return to these destroyed habitats. It means a new beginning for many species worldwide[119].
Environmental concerns [120] again impact the IT industry’s competitive landscape, and businesses with the expertise and vision to offer goods and services that tackle environmental problems profit from a competitive advantage. For example, when making transactions, leases, or contracting decisions, many consumers consider service provider registration and environmental initiatives. Companies face rising energy prices and could be subject to additional government taxes if they do not recognize the effect of environmental activities. Investors and customers are starting to seek more information about carbon emissions and environmental measures and business outcomes. Because of these issues, businesses start proving environmental efficiency, such as the Carbon Disclosure Project (https://www.cdp.net/en) an initiative that allows multinational companies to report their CO2 emissions. The implementation of green IT practices gives companies and individuals economic and other benefits. IT operations increase energy efficiency, especially when electricity is costly and energy prices are increasing, through economically beneficial green initiatives. In a Sun Microsystems Australia survey, which included 1,500 responses from 758 Australian and New Zealand organizations, interviewed respondents said energy conservation and cost management were focused on environmentally sustainable environmental policies and environmental impacts. The primary reason for using the method shown in Figure 5 is that less is better said.
Figure 5: Reasons and benefits for using green IT practices[120]
Many businesses will concentrate on environmental conservation, energy usage, and cost control issues. The organization focuses on environmental protection through the frameworks for resolving business demands, legislation, and climate change. Business and institutional customers ask manufacturers to ”relive” their goods and processes. For instance, businesses like Dell and Wal-Mart take actions that compel suppliers to follow environmental-friendly practices. People start evaluating the essence of the IT environment, and green IT will become a regular function in the next five years. The company provides a range of innovative green goods and services, generating new markets for companies.
6. Future Work of RFID in Green IoT
Green IoT’s promising future will make our future world safer and greener, very high quality, socially and environmentally sustainable and economically viable. Today, green communication and networking, green architecture, green IT and application infrastructure, energy-saving techniques, integrated RFIDs and networks, mobility and network management, the co-operation of homogenous and diverse networks, intelligent artefacts and green location all concentrate on exciting areas [121]. From two points of view, green IoT architecture can be applied to achieve outstanding performance and high quality. Identifying suitable techniques to improve QoS parameters (i.e. bandwidth, delay, and throughput) will make an effective and useful contribution to greener IoT. It would need to use less energy when it comes to greening IoT, searching for new resources, mitigating the adverse effects of IoT on human health, and disruption to the environment. Green IoT will then make a significant contribution to sustainable, intelligent, and green societies. Radio-frequency energy harvesting should be taken into account in order to achieve an energy balance to help green communication between IoT devices. Energy saving and CO2 emission reduction is a major challenge for smart and green environment.
Logistics, Aero-ID, counterfeiting, supply chain control, spaces and much more will accelerate the growth of modern society and technology in the coming decades. Mobility, climate, safety, protection and energy, including medical, pharmaceutical and military applications, will become the leading technological drivers of the future, further growing the need for sustainability—wireless and electronic modules that are reliable, versatile, robust, low power and durable. Work on electronics and RFID seeks to develop versatile systems, based on organic/inorganic substrates and materials, to solve the limitations of ceramics and silicone in order to address these significant challenges. A challenge for potential applications is the convergence of elegant, lightweight, heterogeneous, versatile, environmentally sustainable, newer materials and cost-effective processes in a wide area. Continuous development and innovation involve a wide range of electrical components that can directly produce and incorporate from coils to affordable methods, mainly using organic electronics, along with work into a variety of electrical conductivity and semiconductor materials. Organic materials can be printed and modeled using several methods, each with its advantages and disadvantages, such as flexographic, width, offset, sorting, and injection. Based on these materials and techniques, primarily low-cost RFID transponders, different types of sensors, storage devices, photovoltaic cells, passive devices such as displays or batteries have tested active components such as diodes and transistors with the production of them. Though seen only in the low UHF (RF) range, the trend moves to higher speeds, resolutions and frequencies without compromising versatility, eco-friendliness and low costs. To address these problems includes a new approach to RFID and the design of electronic systems in terms of alternative materials, processes and functions. The researchers in [122] are proposing an innovative approach focused on developing a new low-cost inkjet printing platform with efficient diode integration for applications with optimized metallization traces and enhanced recognition capabilities. The method theoretically proposed can form the basis for the first generation of precise ”smart” RFID devices.
More fields of research need to be explored to establish optimal and efficient Greening IoT solutions:
- Crewless aerial vehicles ( UAVs), particularly in agriculture, traffic, and surveillance, are required to replace many IoT devices, which will reduce power consumption and emissions. UAV is a promising technology that leads to low cost and efficient green IoT.
- Sensor data to the mobile cloud must be more useful. Sensorcloud combines a network of wireless sensors and a mobile cloud. It is a hot and promising IoT greening technology. The device, service, WSN, and cloud management’s energy efficacy can be examined through a green social network such as service (SNaaS).
- M2M connectivity plays a crucial role in reducing energy consumption and harmful emissions. In order to allow automated systems, smart machines must be smarter. In the event of traffic, computer automation delays must be reduced and intervention required and immediate.
7. Conclusion
IoT has an enormous influence on transforming our everyday lifestyle. IoT technology connects a large number of devices and items linked to the Internet around the world. The main concern is how data from these devices can be collected and analyzed effectively. RFID is one of the leading IoT tools, used for the identification and processing of information from IoT devices due to its cost and energy consumption characteristics. Studying this technology is therefore essential and paying attention to mitigating its adverse effects. This paper discusses and summarizes the latest RFID applications, including studies that have improved RFID applications in Green IoT efficiency. This paper also addressed the challenges and implications of green, IoT RFID applications. However, there are still some challenges to this field, such as sophistication, protection and lack of trust. These problems form a relevant research field for future study.
Conflict of Interest
The authors declare no conflict of interest.
Acknowledgment
The authors would like to thank Majlis Amanah Rakyat (MARA) and Universiti Sains Malaysia, for providing the financial support under Research Grant RUI(1001/PELECT/8014049) to carry out this research.
- “What Is Green Power,” https://www.epa.gov/greenpower/what-green-power, accessed: 15-July-2020.
- “Benefits of Using Green Power,” https://www.epa.gov/greenpower/benefits- using-green-power, accessed: 15-July-2020.
- “Energy Efficiency,” https://www.eesi.org/topics/energy- efficiency/description, accessed: 16-July-2020.
- C. Zhu, V. C. Leung, L. Shu, E. C.-H. Ngai, “Green internet of things for smart world,” IEEE access, 3, 2151–2162, 2015, doi:10.1109/ACCESS.2015.
7312. - H. Eakin, P. M. Wightman, D. Hsu, V. R. Gil Ramo´n, E. Fuentes-Contreras, M. P. Cox, T.-A. N. Hyman, C. Pacas, F. Borraz, C. Gonza´lez-Brambila, et al., “Information and communication technologies and climate change adapta- tion in Latin America and the Caribbean: a framework for action,” Climate and Development, 7(3), 208–222, 2015, doi:doi.org/10.1080/17565529.2014. 951021.
- A. P. Upadhyay, A. Bijalwan, “Climate change adaptation: services and role of information communication technology (ICT) in India,” American Journal of Environmental Protection, 4(1), 70–74, 2015, doi:10.11648/j.ajep.20150401. 20.
- O. Balaban, J. A. P. de Oliveira, “Sustainable buildings for healthier cities: assessing the co-benefits of green buildings in Japan,” Journal of Cleaner Production, 163, S68–S78, 2017, doi:doi.org/10.1016/j.jclepro.2016.01.086.
- S. Rani, R. Talwar, J. Malhotra, S. H. Ahmed, M. Sarkar, H. Song, “A novel scheme for an energy efficient Internet of Things based on wireless sen- sor networks,” Sensors, 15(11), 28603–28626, 2015, doi:doi.org/10.3390/ s151128603.
- A. H. Sodhro, S. Pirbhulal, Z. Luo, V. H. C. de Albuquerque, “Towards an optimal resource management for IoT based Green and sustainable smart cities,” Journal of Cleaner Production, 220, 1167–1179, 2019, doi: doi.org/10.1016/j.jclepro.2019.01.188.
- R. Arshad, S. Zahoor, M. A. Shah, A. Wahid, H. Yu, “Green IoT: An inves- tigation on energy saving practices for 2020 and beyond,” IEEE Access, 5, 15667–15681, 2017, doi:10.1109/ACCESS.2017.2686092.
- M. M. K. M. S. Akshaya, M. M. N. Priya, “Green Internet of Things for Smart World,” .
- C. Xiaojun, L. Xianpeng, X. Peng, “IOT-based air pollution monitoring and forecasting system,” in 2015 international conference on computer and com- putational sciences (ICCCS), 257–260, IEEE, 2015, doi:10.1109/ICCACS. 2015.7361361.
- F. K. Shaikh, S. Zeadally, E. Exposito, “Enabling technologies for green internet of things,” IEEE Systems Journal, 11(2), 983–994, 2015, doi: 10.1109/JSYST.2015.2415194.
- C. Zhu, V. C. Leung, L. Shu, E. C.-H. Ngai, “Green internet of things for smart world,” IEEE access, 3, 2151–2162, 2015, doi:10.1109/ACCESS.2015. 2497312.
- C. S. Nandyala, H.-K. Kim, “Green IoT agriculture and healthcare applica- tion (GAHA),” International Journal of Smart Home, 10(4), 289–300, 2016, doi:dx.doi.org/10.14257/ijsh.2016.10.4.26.
- B. Nath, F. Reynolds, R. Want, “RFID technology and applications,” IEEE Pervasive computing, 5(1), 22–24, 2006, doi:10.1109/MPRV.2006.13.
- I. Bose, S. Yan, “The green potential of RFID projects: A case-based analysis,” It Professional, 13(1), 41–47, 2011, doi:10.1109/MITP.2011.15.
- Y. Karakasa, H. Suwa, T. Ohta, “Evaluating effects of RFID introduction based on CO2 reduction,” in Proceedings of the 51st Annual Meeting of the ISSS-2007, Tokyo, Japan, 2007.
- A. Ilic, T. Staake, E. Fleisch, “Using sensor information to reduce the carbon footprint of perishable goods,” IEEE Pervasive Computing, 8(1), 22–29, 2008, doi:10.1109/MPRV.2009.20.
- S. Murugesan, “Harnessing green IT: Principles and practices,” IT profes- sional, 10(1), 24–33, 2008, doi:10.1109/MITP.2008.10.
- F. Al-Turjman, A. Kamal, M. Husain Rehmani, A. Radwan, A.-S. Khan Pathan, “The Green Internet of Things (G-IoT),” 2019, doi:doi.org/ 10.1155/2019/6059343.
- S. Park, “A development of UHF RFID device for mobile IoT service,” in 2016 IEEE 7th Annual Ubiquitous Computing, Electronics & Mobile Commu- nication Conference (UEMCON), 1–7, IEEE, 2016, doi:10.1109/UEMCON. 2016.7777830.
- R. Colella, L. Catarinucci, L. Tarricone, “Improved RFID tag characterization system: Use case in the IoT arena,” in 2016 IEEE International Conference on RFID Technology and Applications (RFID-TA), 172–176, IEEE, 2016, doi:10.1109/RFID-TA.2016.7750760.
- R. Colella, L. Catarinucci, L. Tarricone, “Evaluating the suitability of specific RFID tags for IoT applications through a new characterization platform,” 2016 International Multidisciplinary Conference on Computer and Energy Science (SpliTech), 1–3, 2016, doi:10.1109/SpliTech.2016.7555934.
- F. Nekoogar, F. Dowla, “Passive RFID for IOT using UWB/UHF hybrid sig- naling,” 2016 IEEE/ACES International Conference on Wireless Information Technology and Systems (ICWITS) and Applied Computational Electromag- netics (ACES), 1–2, 2016, doi:10.1109/ROPACES.2016.7465304.
- “The 3 Biggest Benefits of RFID Asset Tracking in the Supply Chain,” https://lowrysolutions.com/blog/the-3-biggest-benefits-of-rfid-asset- tracking-in-the-supply-chain/, accessed: 15-February-2020.
- Kubo, “The Research of IoT Based on RFID Technology,” 2014 7th Interna- tional Conference on Intelligent Computation Technology and Automation, 832–835, 2014, doi:10.1109/ICICTA.2014.199.
- H. Wang, “Constructing the Green Campus within the Internet of Things Architecture,” International Journal of Distributed Sensor Networks, 10, 2014, doi:10.1155/2014/804627.
- “Green Campus at the University of Copenhagen,” https://greencampus.ku.dk/greencampus20/, accessed: 15-July-2020.
- B. Singh, D. K. Lobiyal, “A novel energy-aware cluster head selection based on particle swarm optimization for wireless sensor networks,” Human- centric Computing and Information Sciences, 2, 1–18, 2011, doi:10.1186/ 2192-1962-2-13.
- B. S. Malapur, V. R. Pattanshetti, “IoT based waste management: An appli- cation to smart city,” 2017 International Conference on Energy, Communi- cation, Data Analytics and Soft Computing (ICECDS), 2476–2486, 2017, doi:10.1109/ICECDS.2017.8389897.
- T. Anagnostopoulos, A. Zaslavsky, “Effective Waste Collection with Short- est Path Semi-Static and Dynamic Routing,” in NEW2AN, 2014, doi: 10.1007/978-3-319-10353-2 9.
- P. Jajoo, A. Mishra, S. Mehta, V. Solvande, “Smart Garbage Management Sys- tem,” 2018 International Conference on Smart City and Emerging Technology (ICSCET), 1–6, 2018, doi:10.1109/ICSCET.2018.8537390.
- T. Anagnostopoulos, A. Zaslavsky, A. Medvedev, “Robust waste collection exploiting cost efficiency of IoT potentiality in Smart Cities,” 2015 Interna- tional Conference on Recent Advances in Internet of Things (RIoT), 1–6, 2015, doi:10.1109/RIOT.2015.7104901.
- S. Jisha, M. Philip, “Rfid based security platform for internet of things in health care environment,” 2016 Online International Conference on Green Engineering and Technologies (IC-GET), 1–3, 2016, doi:10.1109/GET.2016. 7916693.
- D. He, S. Zeadally, “An Analysis of RFID Authentication Schemes for Inter- net of Things in Healthcare Environment Using Elliptic Curve Cryptography,” IEEE Internet of Things Journal, 2, 72–83, 2015, doi:10.1109/JIOT.2014. 2360121.
- C. Occhiuzzi, G. Contri, G. Marrocco, “Design of Implanted RFID Tags for Passive Sensing of Human Body: The STENTag,” IEEE Transactions on Antennas and Propagation, 60, 3146–3154, 2012, doi:10.1109/TAP.2012. 2198189.
- G. Calcagnini, F. Censi, M. Maffia, L. Mainetti, E. Mattei, L. Patrono, E. Urso, “Evaluation of thermal and nonthermal effects of UHF RFID exposure on bio- logical drugs,” IEEE Transactions on Information Technology in Biomedicine, 16(6), 1051–1057, 2012, doi:10.1109/TITB.2012.2204895.
- W. Zhou, S. Piramuthu, “Framework, strategy and evaluation of health care processes with RFID,” Decision Support Systems, 50(1), 222–233, 2010, doi:doi.org/10.1016/j.dss.2010.08.003.
- P. Schmitt, F. Michahelles, “Economic impact of RFID report,” Retrieved
November, 1, 2009, 2008. - Z. Lu, H. Cao, P. Folan, D. Potter, J. Browne, “RFID-based information management in the automotive plastic recycling industry,” in Information Technologies in Environmental Engineering, 397–408, Springer, 2007, doi: 10.1007/978-3-540-71335-7 41.
- D. Duval, H. Maclean, “The role of product information in automotive plas- tics recycling: a financial and life cycle assessment,” Journal of Cleaner Production, 15, 1158–1168, 2007, doi:10.1016/J.JCLEPRO.2006.05.030.
- T. C. Poon, K. L. Choy, H. K. H. Chow, H. Lau, F. Chan, K. Ho, “A RFID case-based logistics resource management system for managing order-picking operations in warehouses,” Expert Syst. Appl., 36, 8277–8301, 2009, doi: 10.1016/j.eswa.2008.10.011.
- N. Wu, M. A. Nystrom, T. R. Lin, H. C. Yu, “Challenges to Global RFID Adoption,” 2006 Technology Management for the Global Future – PICMET 2006 Conference, 2, 618–623, 2006, doi:10.1109/PICMET.2006.296595.
- J.-S. Park, “Evaluating Green IT Initiatives Using the Sustainability Balanced Scorecard,” Journal of the Korea Safety Management and Science, 19(3), 81–87, 2017, doi:doi.org/10.12812/ksms.2017.19.3.81.
- A. Nasir, U. Kasimu, B. Ige, A. Mohammed, “Characterization and manage- ment of solid waste generated in Nasarawa LGA in Nasarawa state, Nigeria,” Middle-East J Sci Res, 24, 1128–1134, 2016, doi:10.5829/idosi.mejsr.2016. 24.04.23231.
- R. Knoth, B. Kopacek, P. Kopacek, “Case study: multi life cycle center for electronic products,” in Proceedings of the 2005 IEEE International Sym- posium on Electronics and the Environment, 2005., 194–198, IEEE, 2005, doi:10.1109/ISEE.2005.1437022.
- M. Favot, R. Veit, A. Massarutto, “The evolution of the Italian EPR system for the management of household Waste Electrical and Electronic Equip- ment (WEEE). Technical and economic performance in the spotlight,” Waste management, 56, 431–437, 2016, doi:doi.org/10.1016/j.wasman.2016.06.005.
- H. R. Culver, J. R. Clegg, N. Peppas, “Analyte-Responsive Hydrogels: Intel- ligent Materials for Biosensing and Drug Delivery.” Accounts of chemical research, 50 2, 170–178, 2017, doi:10.1021/acs.accounts.6b00533.
- N. Deng, “RFID technology and network construction in the internet of things,” in 2012 International Conference on Computer Science and Service System, 979–982, IEEE, 2012, doi:10.1109/CSSS.2012.248.
- R. H. Weber, “Internet of Things–New security and privacy challenges,” Com- puter law & security review, 26(1), 23–30, 2010, doi:10.1016/J.CLSR.2009. 11.008.
- R. H. Weber, “Internet of things–Need for a new legal environment?” Com- puter law & security review, 25(6), 522–527, 2009, doi:doi.org/10.1016/j.clsr. 2009.09.002.
- M. Balaji, S. K. Roy, “Value co-creation with Internet of things technology in the retail industry,” Journal of Marketing Management, 33(1-2), 7–31, 2017, doi:10.1080/0267257X.2016.1217914.
- X. Zhu, S. K. Mukhopadhyay, H. Kurata, “A review of RFID technology and its managerial applications in different industries,” Journal of Engineering and Technology, 29, 152–167, 2012, doi:10.1016/J.JENGTECMAN.2011.09.011.
- T. Taleb, M. Corici, C. Parada, A. Jamakovic, S. Ruffino, G. Karagiannis,T. Magedanz, “EASE: EPC as a service to ease mobile core network deploy- ment over cloud,” IEEE Network, 29, 78–88, 2015, doi:10.1109/MNET.2015. 7064907.
- E. Welbourne, L. Battle, G. Cole, K. Gould, K. Rector, S. Raymer, M. Bal- azinska, G. Borriello, “Building the Internet of Things Using RFID: The RFID Ecosystem Experience,” IEEE Internet Computing, 13, 2009, doi: 10.1109/MIC.2009.52.
- B. Fabian, O. Gu¨nther, “Security challenges of the EPCglobal network,” Com- mun. ACM, 52, 121–125, 2009, doi:10.1145/1538788.1538816.
- J. Cooper, A. James, “Challenges for database management in the in- ternet of things,” IETE Technical Review, 26(5), 320–329, 2009, doi: 10.4103/0256-4602.55275.
- M. Z. Hasan, F. Al-Turjman, “Optimizing multipath routing with guaran- teed fault tolerance in Internet of Things,” IEEE Sensors Journal, 17(19), 6463–6473, 2017, doi:10.1109/JSEN.2017.2739188.
- S. F. Khan, “Health care monitoring system in Internet of Things (IoT) by using RFID,” in 2017 6th International Conference on Industrial Technology and Management (ICITM), 198–204, IEEE, 2017, doi:10.1109/ICITM.2017. 7917920.
- S. Amendola, R. Lodato, S. Manzari, C. Occhiuzzi, G. Marrocco, “RFID technology for IoT-based personal healthcare in smart spaces,” IEEE Internet of things journal, 1(2), 144–152, 2014, doi:10.1109/JIOT.2014.2313981.
- S. Manzari, G. Marrocco, “Modeling and applications of a chemical-loaded UHF RFID sensing antenna with tuning capability,” IEEE transactions on antennas and propagation, 62(1), 94–101, 2013, doi:10.1109/TAP.2013. 2287008.
- S. Manzari, A. Catini, G. Pomarico, C. Di Natale, G. Marrocco, “Develop- ment of an UHF RFID chemical sensor array for battery-less ambient sensing,” IEEE Sensors Journal, 14(10), 3616–3623, 2014, doi:10.1109/JSEN.2014. 2329268.
- S. Amendola, L. Bianchi, G. Marrocco, “Combined passive radiofrequency identification and machine learning technique to recognize human motion,” in 2014 44th European Microwave Conference, 1044–1047, IEEE, 2014, doi:10.1109/EuMC.2014.6986617.
- J. Zhang, G. Y. Tian, A. M. Marindra, A. I. Sunny, A. B. Zhao, “A review of passive RFID tag antenna-based sensors and systems for structural health monitoring applications,” Sensors, 17(2), 265, 2017, doi:doi.org/10.3390/ s17020265.
- L. K. Fiddes, N. Yan, “RFID tags for wireless electrochemical detection of volatile chemicals,” Sensors and Actuators B: Chemical, 186, 817–823, 2013, doi:doi.org/10.1016/j.snb.2013.05.008.
- E. Moradi, K. Koski, L. Ukkonen, Y. Rahmat-Samii, T. Bjo¨ rninen, L. Syda¨nheimo, “Embroidered RFID tags in body-centric communication,” in 2013 International Workshop on Antenna Technology (iWAT), 367–370, IEEE, 2013, doi:10.1109/IWAT.2013.6518367.
- R. Krigslund, S. Dosen, P. Popovski, J. L. Dideriksen, G. F. Pedersen, D. Fa- rina, “A novel technology for motion capture using passive UHF RFID tags,” IEEE Transactions on Biomedical Engineering, 60(5), 1453–1457, 2012, doi:10.1109/TBME.2012.2209649.
- S. Manzari, C. Occhiuzzi, S. Nawale, A. Catini, C. Di Natale, G. Marrocco, “Humidity sensing by polymer-loaded UHF RFID antennas,” IEEE Sensors Journal, 12(9), 2851–2858, 2012, doi:10.1109/JSEN.2012.2202897.
- A. A. Babar, S. Manzari, L. Sydanheimo, A. Z. Elsherbeni, L. Ukkonen, “Passive UHF RFID tag for heat sensing applications,” IEEE Transactions on Antennas and propagation, 60(9), 4056–4064, 2012, doi:10.1109/TAP.2012. 2207045.
- G. Li, Y. Huang, G. Gao, X. Wei, Z. Tian, L.-A. Bian, “A handbag zipper antenna for the applications of body-centric wireless communications and Internet of Things,” IEEE Transactions on Antennas and Propagation, 65(10), 5137–5146, 2017, doi:10.1109/TAP.2017.2743046.
- T. Kellomaki, “On-body performance of a wearable single-layer RFID tag,” IEEE Antennas and Wireless Propagation Letters, 11, 73–76, 2012, doi: 10.1109/LAWP.2012.2183112.
- S. Manzari, C. Occhiuzzi, G. Marrocco, “Feasibility of body-centric passive RFID systems by using textile tags,” IEEE Antennas Propag. Mag, 54(4), 49–62, 2012, doi:10.1109/MAP.2012.6309156.
- J. Kim, A. Banks, H. Cheng, Z. Xie, S. Xu, K.-I. Jang, J. W. Lee, Z. Liu,P. Gutruf, X. Huang, et al., “Epidermal electronics with advanced capa- bilities in near-field communication,” small, 11(8), 906–912, 2015, doi: doi.org/10.1002/smll.201402495.
- S. Wang, S. Liu, D. Chen, “Analysis and construction of efficient RFID authen- tication protocol with backward privacy,” in China Conference on Wireless Sensor Networks, 458–466, Springer, 2012, doi:10.1007/978-3-642-36252-1 43.
- Y.-P. Liao, C.-M. Hsiao, “A secure ECC-based RFID authentication scheme integrated with ID-verifier transfer protocol,” Ad hoc networks, 18, 133–146, 2014, doi:10.1016/j.adhoc.2013.02.004.
- J. Chou, “An efficient mutual authentication RFID scheme based on ellip- tic curve cryptography,” The Journal of Supercomputing, 70, 75–94, 2013, doi:10.1007/s11227-013-1073-x.
- C. Jin, C. Xu, X. Zhang, J. Zhao, “A secure RFID mutual authentication pro- tocol for healthcare environments using elliptic curve cryptography,” Journal of medical systems, 39(3), 24, 2015, doi:10.1007/s10916-015-0213-7.
- Z. Zhang, Q. Qi, “An efficient RFID authentication protocol to enhance pa- tient medication safety using elliptic curve cryptography,” Journal of medical systems, 38(5), 47, 2014, doi:10.1007/s10916-014-0047-8.
- A. K. Singh, B. Patro, “Elliptic Curve Signcryption Based Security Proto- col for RFID,” Ksii Transactions on Internet and Information Systems, 14, 344–365, 2020, doi:10.3837/tiis.2020.01.019.
- C. Lai, H. Li, X. Liang, R. Lu, K. Zhang, X. Shen, “CPAL: A condi- tional privacy-preserving authentication with access linkability for roam- ing service,” IEEE Internet of Things Journal, 1(1), 46–57, 2014, doi: 10.1109/JIOT.2014.2306673.
- Z. Ali, A. Ghani, I. Khan, S. A. Chaudhry, S. H. Islam, D. Giri, “A robust authentication and access control protocol for securing wireless healthcare sensor networks,” J. Inf. Secur. Appl., 52, 102502, 2020, doi: 10.1016/j.jisa.2020.102502.
- Y.-l. Liu, X.-l. Qin, C. Wang, B.-h. Li, “A lightweight RFID authentication protocol based on elliptic curve cryptography,” Journal of computers, 8(11), 2880–2887, 2013, doi:10.4304/jcp.8.11.2880-2887.
- Y.-P. Liao, C.-M. Hsiao, “A secure ECC-based RFID authentication scheme using hybrid protocols,” in Advances in Intelligent Systems and Applications- Volume 2, 1–13, Springer, 2013, doi:10.1007/978-3-642-35473-1 1.
- J. Bongaarts, “Global fertility and population trends,” in Seminars in repro- ductive medicine, volume 33, 005–010, Thieme Medical Publishers, 2015, doi:10.1055/s-0034-1395272.
- M. E. Beqqal, M. Azizi, “Review on security issues in RFID systems,” Ad- vances in Science, Technology and Engineering Systems Journal, 2, 194–202, 2017, doi:10.25046/AJ020624.
- “Top 10 RFID Security Concerns and Threats,” https://securitywing.com/top- 10-rfid-security-concerns-threats/, accessed: 10-September-2020.
- M. El-hajj, A. Fadlallah, M. Chamoun, A. Serhrouchni, “A Survey of Internet of Things (IoT) Authentication Schemes ,” Sensors (Basel, Switzerland), 19, 2019, doi:10.3390/s19051141.
- G. Saxl, M. Ferdik, M. Fischer, M. Maderboeck, T. Ussmueller, “UHF RFID Prototyping Platform for ISO 29167 Decryption Based on an SDR,” Sensors (Basel, Switzerland), 19, 2019, doi:10.3390/s19102220.
- L. Xiao, H. Xu, F. Zhu, R. Wang, P. Li, “SKINNY-Based RFID Lightweight Authentication Protocol,” Sensors (Basel, Switzerland), 20, 2020, doi: 10.3390/s20051366.
- K. Fan, C. Liang, H. Li, Y. Yang, “LRMAPC: A Lightweight RFID Mutual Authentication Protocol with Cache in the Reader for IoT,” 2014 IEEE International Conference on Computer and Information Technology, 276–280, 2014, doi:10.1109/CIT.2014.80.
- O. Hongzhi, G. Jin-yun, L. Ke-sheng, “An UHF RFID reader in IOT,” Proceedings 2013 International Conference on Mechatronic Sciences, Electric Engineering and Computer (MEC), 672–675, 2013, doi:10.1109/MEC.2013. 6885148.
- C. P. Schuch, G. Balbinot, M. Jeffers, M. W. McDonald, D. Corbett, “An RFID-based activity tracking system to monitor individual rodent behavior in environmental enrichment: Implications for post-stroke cognitive recovery,” Journal of Neuroscience Methods, 324, 2019, doi:10.1016/j.jneumeth.2019. 05.015.
- “DHL Says Its SmartTrucks Save Money, Time and CO2,” Accessed: 15- September-2020.
- “Communities Turn to RFID to Boost Recycling,” http://www.rfidjournal.com/article/articleview/4259/1/1, accessed: 03- June-2020.
- “Nestle´ italy finds rfid brings roi for ice cream,” Accessed: 03-June-2020.
- X. Chen, X. Wang, M. Zhou, “Firms’ green R&D cooperation behaviour in a supply chain: Technological spillover, power and coordination,” International Journal of Production Economics, 2019, doi:10.1016/j.ijpe.2019.04.033.
- X. Zhu, Y. Zhang, Z. Zhao, J. Zuo, “Radio frequency sensing based envi- ronmental monitoring technology,” in International Workshop on Pattern Recognition, 2019, doi:10.1117/12.2541098.
- T. Litman, London congestion pricing: Implications for other cities, Victoria Transport Policy Institute, 2012.
- L. Ecola, T. Light, “Making congestion pricing equitable,” Transportation working and Internet Architecture, 2017, doi:doi.org/10.1145/3130970.
- L. Batina, S. Seys, D. Singele´e, I. Verbauwhede, “Hierarchical ECC-based RFID authentication protocol,” in International Workshop on Radio Fre- Research Record, 2187(1), 53–59, 2010, doi:doi.org/10.3141/2187-08.
- V. Talla, M. Hessar, B. Kellogg, A. Najafi, J. R. Smith, S. Gollakota, “LoRa quency Identification: Security and Privacy Issues, 183–201, Springer, 2011,
doi:10.1007/978-3-642-25286-0 12. - C. Lv, H. Li, J. Ma, Y. Zhang, “Vulnerability analysis of elliptic curve cryptography-based RFID authentication protocols,” Transactions on Emerging Telecommunications Technologies, 23(7), 618–624, 2012, doi:10.1002/ ett.2514.
- S. N. R. Kantareddy, I. Peters, I. Mathews, S. Sun, M. Layurova, J. Thapa, J.-P. Correa-Baena, R. Bhattacharyya, T. Buonassisi, S. Sarma, “Perovskite PV-Powered RFID: Enabling Low-Cost Self-Powered IoT Sensors,” IEEE Sensors Journal, 20, 471–478, 2020, doi:10.1109/JSEN.2019.2939293.
- B. Chander, K. Gopalakrishnan, “Security Vulnerabilities and Issues of Traditional Wireless Sensors Networks in IoT,” 2020, doi:10.1007/ 978-3-030-33596-0 21.
- K. Fan, Y. Gong, Z. Du, H. Li, Y. Yang, “RFID Secure Application Revocation for IoT in 5G,” 2015 IEEE Trustcom/BigDataSE/ISPA, 1, 175–181, 2015, doi:10.1109/Trustcom.2015.372.
- Y. L. Santos, E. Canedo, “On the Design and Implementation of an IoT based Architecture for Reading Ultra High Frequency Tags,” Inf., 10, 41, 2019, doi:10.3390/info10020041.
- S. N. R. Kantareddy, I. Mathews, R. Bhattacharyya, I. Peters, T. Buonas, S. Sarma, “Long Range Battery-Less PV-Powered RFID Tag Sensors,” IEEE Internet of Things Journal, 6, 6989–6996, 2019, doi:10.1109/JIOT.2019. 2913403.
- Y. Jabareen, “An assessment framework for cities coping with climate change: The case of New York City and its PlaNYC 2030,” Sustainability, 6(9), 5898– 5919, 2014, doi:doi.org/10.3390/su6095898.
- V. M. Thomas, “Environmental implications of RFID,” in 2008 IEEE International Symposium on Electronics and the Environment, 1–5, IEEE, 2008, doi:10.1109/ISEE.2008.4562916.
- J. Su, Z. Sheng, V. C. M. Leung, Y. Chen, “Energy Efficient Tag Identification Algorithms For RFID: Survey, Motivation And New Design,” IEEE Wireless Communications, 26, 118–124, 2019, doi:10.1109/MWC.2019.1800249.
- R. Gradus, G. C. Homsy, L. Liao, M. E. Warner, “Which US municipalities adopt Pay-As-You-Throw and curbside recycling” Resources, Conservation and Recycling, 143, 178–183, 2019, doi:doi.org/10.1016/j.resconrec.2018.12. 012.
- N. E. Weckman, N. Ermann, R. Gutierrez, K. Chen, J. Graham, R. Tivony, Heron, U. F. Keyser, “Multiplexed DNA identification using site specific dCas9 barcodes and nanopore sensing,” ACS sensors, 4(8), 2065–2072, 2019, doi:doi.org/10.1021/acssensors.9b00686.
- V. M. Thomas, “A universal code for environmental management of products,” Resources, Conservation and Recycling, 53(7), 400–408, 2009, doi: doi.org/10.1016/j.resconrec.2009.03.004.
- S. Saar, M. Stutz, V. M. Thomas, “Towards intelligent recycling: a proposal to link bar codes to recycling information,” Resources, Conservation and Recycling, 41(1), 15–22, 2004, doi:doi.org/10.1016/j.resconrec.2003.08.006.
- A. Condemi, F. Cucchiella, D. Schettini, “Circular Economy and E-Waste: An Opportunity from RFID TAGs,” Applied Sciences, 9(16), 3422, 2019, doi:doi.org/10.3390/app9163422.
- P. Krauchi, P. Wager, M. Eugster, G. Grossmann, L. Hilty, “End-of-life im- pacts of pervasive computing,” IEEE Technology and Society Magazine, 24(1), 45–53, 2005, doi:10.1109/MTAS.2005.1407747.
- M. Brink, F. Berkemeyer, J. Ohlendorf, G. Dumstorff, K. Thoben, W. Lang, “Challenges and Opportunities of RFID Sensortags Integration by Fibre- Reinforced Plastic Components Production,” Procedia Manufacturing, 24, 54–59, 2018, doi:10.1016/J.PROMFG.2018.06.008.
- K. Kunz, N. Lui, “Process Chemistry and Copper Catalysis,” Copper- Mediated Cross-Coupling Reactions, 725–743, 2013, doi:10.1002/ 9781118690659.
- L. Guest, W. Guibe`ne, S. Guruacharya, “Wireless Communications and Mobile Computing Green Internet of Things ( IoT ) : Enabling Technologies , Architectures , Performance , and Design Issues,” 2018, doi: https://doi.org/10.1155/2018/3747562.
- Y. Duroc, D. Kaddour, “RFID potential impacts and future evolution for green projects,” Energy Procedia, 18, 91–98, 2012, doi:doi.org/10.1016/j.egypro. 2012.05.021.
- S. H. Alsamhi, O. Ma, M. Ansari, Q. Meng, “Greening Internet of Things for Smart Everythings with A Green-Environment Life: A Survey and Future Prospects,” ArXiv, abs/1805.00844, 2018.
- G. Orecchini, L. Yang, A. Rida, F. Alimenti, M. Tentzeris, L. Roselli, “Green Technologies and RFID : Present and Future,” 2010.
- A. Ahmed, “Benefits and Challenges of Internet of Things for Telecommunication Networks,” 2019, doi:10.5772/INTECHOPEN.81891.
- K. A. Alezabi, F. Hashim, S. J. Hashim, B. M. Ali, A. Jamalipour, “Efficient authentication and re-authentication protocols for 4G/5G heterogeneous networks,” EURASIP Journal on Wireless Communications and Networking, 2020, 1–34, 2020, doi:10.1186/s13638-020-01702-8.
