Hand-Based Biometric Recognition Technique – Survey
Volume 5, Issue 6, Page No 689-698, 2020
Author’s Name: Katerina Prihodovaa), Miloslav Hub
View Affiliations
Faculty of Economics and Administration, University of Pardubice, 532 10, Czech Republic
a)Author to whom correspondence should be addressed. E-mail: st30351@student.upce.cz
Adv. Sci. Technol. Eng. Syst. J. 5(6), 689-698 (2020); ![]() DOI: 10.25046/aj050683
DOI: 10.25046/aj050683
Keywords: Hand geometry, Biometric recognition, Hand-base authentication
Export Citations
In today’s modern world, reliable automatic personal recognition is a crucial area of discussion, primarily because of the increased security risks. A large number of systems first require the recognition of a person before they can access their services. Biometric recognition can be used, which can be understood as automatic identification or automatic verification of persons based on physiological or behavioural characteristics. Examples of biometric characteristics may be the fingerprint, face, signature, hand geometry. There are many approaches, and each has its pros and cons. However, there is currently no current extensive research and evaluation of hand-based biometric systems. Given the user-friendliness of these systems and the needs of society, this article aims to compare different methods of biometric recognition based on hand, so that the article reduces the entry barrier into this area of research. Furthermore, the article aims to determine the research gap and suggest possible directions for research in the future.
Received: 31 August 2020, Accepted: 01 November 2020, Published Online: 24 November 2020
1. Introduction
This paper is an extension of work originally presented in International Conference on Information and Digital Technologies [1]. In today’s modern society, there is an increasing emphasis on working with information. Information is one of the most valuable assets we can own, so it needs to be protected. Among the basic requirements for their security are their confidentiality, integrity and availability. The requirement of confidentiality information requires that only authorized entities have access to it. One way to ensure the confidentiality of information is through authentication, during which the identity of the entity to which the relevant rights are subsequently assigned is verified [2].
Authentication can be defined as: “A method of verifying a user’s identity on a system to control access to the system or resources.” [3] Authentication can be performed using knowledge (password, pin), an authentication object (token, mobile phone), or using what we are physically and mentally (biometric characteristics). The last option is used by biometric recognition systems, which have come to the fore, especially in recent years, thanks to scientific and technical progress.
Biometric systems are applications of biometric technologies that allow automatic identification or verification of a specific natural person, using physicavl (e.g. face, fingerprint) or behavioural (e.g. voice, gait) characteristics. Biometric characteristics must be universal (the characteristics must exist for all persons), they must have high external variability (high diversity for different persons) and low internal variability (low diversity for one person).
Identification (“One-To-Many Matching”) is understood in this article as the process of comparing a set of biometric features obtained from a scanned biometric sample with all reference templates stored in a database. If there is a reference template in the database that sufficiently corresponds to the set of biometric features, the biometric system identifies the person by the identity associated with this reference template, otherwise the person is not identified [4].
Verification (“One-To-One Matching”) is understood in this article as the process of verifying that the person being examined is who he or she claims to be. The set of biometric features obtained from the scanned sample is compared with one own biometric template, which is stored in a database. If the set of biometric features sufficiently matches this reference template, the identity is verified, otherwise it is not verified [4].
Biometric recognition of people is based on their biometric characteristics, and it is their unique physiological and behavioural characteristics. Physiological characteristics are those characteristics with which we were born and include, e.g. iris [5, 6], retina [7], face [8], shape of the outer ear [9], fingerprints [10], palmprints [11] and footprints [12], fingers geometry [13], hand geometry, [14], topography (layout and shape) of wrist veins [15], DNA [16]. Behavioural characteristics include, e.g. voice [17], writing [18], signature [19], and gait [20].
From the biometric characteristics, distinguishing repeatable biometric features can be obtained for biometric recognition. Biometric features are numbers or designations obtained from biometric samples that are used for subsequent comparison. Biometric samples are an analogue or digital representation of biometric characteristics before the actual extraction of biometric features [21].
The article aims to provide a comprehensive survey with the inclusion of most recent research papers up to 2020, covering a total of 117 journal publications, conference proceeding, patents, and papers. The aim is also lower the entry barrier to this research area by providing a comprehensive reference for novices. Offer a wide range of comparisons in diverse research angles and perspectives in hand geometry recognition. Identify current trends in this area and the need for future research.
2. Development of Hand-Based Biometric Systems
The first modern biometric systems used the hand geometry as a biometric characteristic, and then it was an authentication system in the verification mode (the user submitted an identity and it was subsequently confirmed or rejected). Robert Miller dealt with the issue of hand-based biometric systems in the 1960s and based on research, and he created a device at the Stanford Research Institute, which he patented in 1971. This device performed the pattern recognition by purely mechanical means, where four spring bars slid towards the user’s fingers and subsequently the length of the user’s fingers was measured. If the finger lengths matched the pattern embossed on the user’s identity card, a simple switch was activated, which was used to operate the electric lock [4, 22].
The first commercial hand scanner was the Identimat, based on the patent Robert Miller’s as mentioned above [22]. The measurement of the hand was performed by scanning the photocells located under grooves on which the user placed the hand (fingers). The light source was light with a power of 1000 watts. A reading head with a magnetic stripe was attached to this scanning mechanism, to which a user’s magnetic card was attached during verification. If the pulses on the card matched the signal times from the photocell sensors within the threshold value, the user’s identity was verified. This system was successfully used in various applications. The first use was of a military nature, and it was the security of nuclear weapons. Later, Identimat was used to access US nuclear power plants and also to control employee attendance at an investment company on Wall Street. The second development line of Identimat was already two-dimensionally oriented, measuring not only the length but also the width of all fingers on one hand [4, 23].
The history of the practical implementation of hand geometry recognition is further associated with the name David Sidlauskas and his company Recognition System Inc., which he founded in 1986. This company was the first in the world to start developing and selling modern hand scanners. In the mid-1980s, David Sidlauskas patented the first biometric system to use a three-dimensional hand image. The patented system consists of a camera and an optical measuring board. The camera has a plan view and a side view of the hand. The identification code is entered using the keypad [24]. Based on this patent, the first commercially successful biometric system using the hand geometry of the Handkey ID3D scanner was created.
BioMet Partners, Inc. developed a two-finger version of the Digi-2 hand scanner and was launched in 1995. The scanner uses a CCD camera to scan only the index finger and middle finger and obtain their 3D image [4].
In the 1990s, biometric hand scanners were used in the INSPASS program, a program at selected US airports that accelerated the check-in of frequent travellers. These persons could apply for inclusion in a program in which their hand geometry was scanned and then obtained an identification card with a reference template. These persons were able to complete check-in quickly at selected airports with the help of installed hand scanners [25].
Another hand-scanner recognition project was an Israeli project that automated motion control on the Israeli-Palestinian border. During the creation of the biometric system, suitable biometric characteristics were selected. Biometric characteristics face, hand geometry and fingerprints were considered. A multi‑biometric system was chosen that combined face recognition and hand geometry, which was chosen mainly because most people crossing the border are workers whose fingerprints are not reliable for biometric verification [26].
In terms of security, hand scanners were also used at the 1996 Atlanta Olympics, which controlled access to the Olympic Village. Hand scanners were also used by the Colombian legislature, which voted safely through them [27]. Until 1998, only two scientific articles in the field of hand-based biometric systems were published, namely: “Vital Signs of Identity” a “A Performance Evaluation of Biometric Identification Devices.” [2, 23, 28] From 1998 to 2006, there was an almost exponential increase in the number of publications in this area [29].
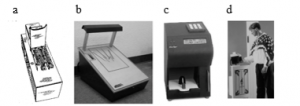
Figure 1: a) Drawing of mechanical hand reader [22] b) Identimat [30] c) two-finger scanner from Biomet [31] d) utilization hand geometry scanner at the Atlanta Olympics [32]
3. Current methods in hand-based biometric systems
Current hand-based biometric systems can be divided into the following groups according to biometric characteristics [33]:
- hand geometry and handshape,
- palmprint,
- fingerprint,
- topography (finger, hand).
At the beginning of the research of hand-based biometric systems, hand geometry was used, e.g. widths, lengths, angles [35‑37], later the silhouette of the hand was added as another biometric characteristic [38-40].
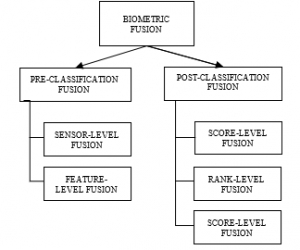
Figure 2: Fusion at various levels of multi-biometric systems (source: [34])
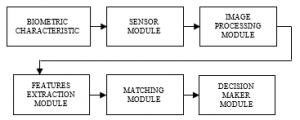
Figure 3: General model of biometric system
Currently, there are also multi-biometric systems that use a combination of multiple biometric characteristics. A palmprint [41-45] or bloodstream topography [46-48] is used in combination with hand geometry or silhouette. The topography of bloodstream is measured either on the palm or back of the hand when the whole hand is scanned. Systems have also been developed that combine more than two characteristics, such as hand geometry, palmprint, and fingerprint [49, 50]. Multi‑biometric systems achieve higher accuracy [51] than biometric systems using only one biometric characteristic. Newly emerging biometric systems also use as a characteristic the heartbeat captured on the finger [52], pores on the hands [53], or hand gestures [44].
Combining multiple biometric characteristics in one biometric system requires fusion, which is the interconnection of information. Fusion can be achieved at different levels of the biometric system. Fusion levels can be divided into two large groups: pre-classification fusion and post-classification fusion. Pre-classification fusion include sensor-level fusion and feature-level fusion while post-classification fusion includes score-level fusion, rank-level fusion rank and decision-level fusion [34]. The individual fusion levels are shown in Figure 2.
The biometric recognition system has several modules: the sensor captures the biometric characteristic, followed by image processing, extraction of identification features, comparison with the biometric template and decision. The individual modules of the biometric system are shown in its general model in Figure 3.
3.1. Sensor
CCD chip cameras, a light-sensitive image detector used by digital cameras, camcorders, and webcams, e.g. are most commonly used to capture biometric characteristics [24, 53]. The scanner can also be a biometric sensor [42, 49, 54]. The sensor captures either a 2D [55-57] or a 3D [48, 58, 59] image of the hand. 3D images are obtained using two cameras, with the help of mirrors, or they can be obtained using a 3D digitizer [60].
Lighting also plays an essential role in obtaining a biometric sample. Some systems have their own light source, mainly commercial biometric scanners. Most sensors acquire images of the hand in visible light, but some also use infrared radiation [47, 61], which achieves a higher accuracy of biometric recognition [62].
Today, commercially available hand readers use spacer pins that firmly determine the position of the hand when scanning [48, 58, 63]. As spacer pins can deform the silhouette of the hand [64], systems without spacer pins have come to the fore in scientific circles [53, 65, 66]. The latest possibilities are contactless systems [38, 61, 67, 68], where, in addition to the spacer pins, direct contact with the reader is not required. These systems are considered to be the most user-friendly, mainly due to the elimination of the need for physical contact.
3.2. Image processing
After obtaining the image of the hand, it is necessary to process the acquired image. The first step in image processing is image pre-processing. It is a set of methods that are applied to an image because only a minimal percentage of hand images are taken under optimal conditions. Almost no captured image is completely noise-free, not entirely focused, obtained in optimal lighting conditions. For this reason, filters are used to sharpen the image or to remove noise. It is also possible to change the brightness using geometric transformation methods. [69]
The second step of image processing is image segmentation, i.e. dividing the image into segments with common properties. The aim of segmentation in hand-based biometric systems is to separate the hand from the rest of the image automatically. The more hand the image is obtained in more limited conditions, the easier the segmentation and can be done by faster methods. Segmentation methods can be divided into groups [69]:
- statistic methods,
- methods based on edge detection,
- hybrid methods (morphological),
- knowledge methods.
If the hand image is acquired on a scanner, the background is constant, and segmentation is relatively simple, then the segmentation method of image thresholding can be used. Image thresholding is the simplest statistical segmentation method based on pixel brightness evaluation. During thresholding, problems arise with rings, bracelets, or dirty skin [70-72].
Segmentation of the hand image can also be performed using edge detection methods. Edges are detected by edge detectors based on significant differences in the values of neighbouring pixels [37, 73].
There are also multi-stage segmentation methods where multiple methods are combined. These multi-stage methods can detect a hand from a crowded background. An example of such a method is a method that first detects the skin by colour (knowledge) and then detects the shape of the hand [74].
Another method of segmentation and at the same time localization of biometric features is AAM (Active Appearance Model) [55]. The AAM method presents the hand using an appearance model, which is created from a shape model and a hand texture model based on a statistical method – principal component analysis (PCA). The advantage of the method is the complexity of the information it contains about the hand [75].
The disadvantage of some segmentation methods is that their use breaks the silhouette of the hand. Mathematical morphology is a mathematical tool that can solve this problem and connect disconnected fingers. Mathematical morphology is also used to remove rings, bracelets or watches [56, 76, 77].
If the position of the hand is not fixed when acquiring the image, it is necessary to align the image of the hand after segmentation within the image processing. This can be done using landmarks, which can be extremes (fingertips, finger valleys) [36, 57, 78], of the centre of gravity, or a fixed reference point on the wrist [79].
Image processing is performed to facilitate the extraction of the region of interest. Biometric features are then extracted from the area of interest.
3.3. Extraction of biometric features
The image processing is followed by the extraction of biometric features. Extraction of biometric features is defined in [21] as: “A process applied to a biometric sample to isolate and obtain a repeatable output of characteristic numbers or designations that can be compared with features extracted from other biometric samples.” For the biometric characteristic of hand geometry, biometric features are geometric measurements, such as finger lengths and widths, finger area, radii of circles on fingers and palms, and angles between fingers. Figure 4 shows 17 geometric measurements, but some systems use a different number of measurements, most often 13-50 measurements [35, 49, 80].
Figure 4: Geometric measurements (source: [81])
More information than hand measurements is provided by the silhouette of the hand, which is used by many systems [40,70]. These systems use biometric features to extract generic or customized feature extractors. For example, customize shape extractors [40, 82, 83] or figure features extractors algorithms Scale Invariant Feature Transform (SIFT) [82], LBP [84]. They are also used palm-based textures [85]. The silhouette is also distinguishable by its contour pixels; it represents the real shape of the hand [67].
Contours are less explored than geometric features, especially since geometric features are easier to determine from a normalized hand image. The issue of normalization of various hand positions and accurate localization of fingertips and finger valleys in unrestricted and contactless systems requires further research. [67]
Some systems extract biometric features of hand geometry and hand shape at the same time, extractors are specially adapted to the shape and geometry of the hand [86, 79].
Recent research uses deep neural networks, such as convolutional neural networks [87, 88] or Siamese networks, to extract biometric features of the hand [87].
3.4. Comparison with the reference template
In this phase, a set of biometric features obtained from a recognized person’s biometric sample is compared with a reference template or templates (stored in a database). The score is then generated using the following methods:
- statistic methods,
- minimum distance (Euclidean metric, Hamming metric, Chebyshev metric),
- Kullback–Leibler divergence,
- correlation coefficient,
- Gaussian mixture models (GMM),
- machine learning,
- support vectors machine (SVM),
- k-nearest neighbours,
- Bayesian networks,
- neural networks.
Statistic methods
Statistical methods of comparing a set of biometric features with a reference template when recognizing a person based on the geometry and shape of the hand include a comparison by a minimum distance. If M reference templates are stored in the database x1R, x2R, …, xMR, the minimum distance of the hand biometric sample x from the reference template is calculated as follows:
![]()
…… reference templates
…… number of reference templates
…… biometric features set (vector)
When recognizing a person based on hand geometry and hand shape, various metrics are used to determine the distance, such as the Euclidean metric [37, 56, 70], the Hamming metric [39], or the Chebyshev metric [80].
- Euclidean metric is defined by the relation:
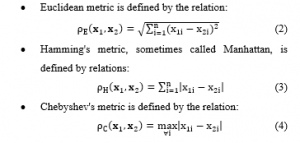
The Kullback – Leibler divergence can also be used to express “distance”, which expresses the degree of dissimilarity between two probability distributions [36]. The correlation coefficient can also be used as a measure of similarity [81, 89].
Gaussian mixture models are located at the interface of statistical and machine methods (GMM). It is a pattern recognition method that is based on the GMM’s ability to approximate any probability density using a mixture of Gaussian densities. The probability of the vector of characteristics xn is estimated as a weighted sum of Gaussian densities. The result is, therefore, the probability with which the pattern (hand image) belongs to a given class. This method gives better results in the field of recognizing a person based on hand geometry than methods working with distance [37, 59].
The Gaussian mixture model is defined by the relation:
![]()
……identity of the person to whom the hand image is assigned with probability p
.…… vector of biometric features
…… weight of individual Gaussian models
…… average vector model
…… covariance matrix
…… number of models
.…… dimension vector of biometric features
Machine learning
Machine learning is a group of algorithms that allow a computer system to learn. Mittchell [90] d defined machine learning as follows: “A computer program is said to learn from experience E concerning some classes of T and the measured power P, if its performance P improves with experience E.”
A large and used group of machine learning are algorithms called support vectors or support vector machines (SVM). These are classifiers that use boundaries in image space. SVM aims to find a superstructure that divides the symptom space. SVM used Vinodkumar and Srikantaswamy as a classifier in a multi-biometric system, where the biometric characteristics were hand geometry, fingerprints and palmprint [91]; however, they have also been used in many other hand-based multi-biometric systems [41, 42, 49, 92].
A frequently used machine learning method in hand-based biometric systems is the nearest neighbour (k-NN) method [54, 93]. It is one of the simplest classification methods. Bayesian networks [93, 94] or random forest [84] can also be used for comparison with the pattern.
Some types of neural networks, multilayer perceptron (MLP) can also be used as classifiers [95]. Generalized regression neural network (GRNN) [96] and convolutional neural network (CNN) were used as classifiers that were not preceded by classical features extraction, classification was performed using SOFTMAX [86].
3.5. Decision
In most systems, the final decision on a user’s identity is based on a threshold that is chosen so that the biometric system meets security and throughput requirements. The score calculated in the previous system module is compared with the threshold value. If the score is higher than the threshold, the user is identified or verified, but if the score is lower than the threshold, the user is not identified or verified. The outcome of decisions for hand-based biometric systems is significantly influenced by user training, with the right habits of users, the score increases (agreement of the compared samples) [97, 98].
4. Quantitative evaluation of biometric system
Possible identification results are shown in Table 1.
| Decision | |||
| Accept | Reject | ||
| Actual output | Authorized user | Correct acceptance | Incorrect rejection |
| Unauthorized intruder | Incorrect acceptance | Correct rejection | |
Table 1: Possibilities of recognition decision
Source: [2]
Based on the decision, the performance of biometric systems can be quantified. Selected quantified identifiers are [99].
False Rejection Rate – FRR
The probability that the biometric system does not recognize the authorized user will lead to an erroneous rejection, i.e. a type 1 error. If an error of this type occurs, the user can try to prove his identity again. The FRR is calculated according to the formula:
![]()
… occurrence of a rejection error
… recognition (verification or identification) by an authorized user
… number of false rejections
… number of attempts by authorized users to recognize
False Acceptance Rate – FAR
The probability that the biometric system will accept an unauthorized intruder will lead to incorrect acceptance, i.e. a type 2 error.
The FAR calculation is considered according to the formula:
![]()
… occurrence of an acceptance error
… recognition by an unauthorized intruder
… number of incorrect acceptances
… the number of attempts by an unauthorized intruder to recognize
The FAR and FRR rates depend on the threshold and are also inversely proportional. The higher the threshold, the more secure the biometric system, but the more common the type 1 error occurs and the user-friendliness decreases. On the contrary, the lower the threshold value, the more user-friendly the biometric system, but more often an unauthorized intruder, i.e. a type 2 error, is admitted, and the security of the system is reduced. The threshold value must always be set according to the requirements that are placed on the biometric system.
Equal Error Rate – EER
Value where the error rates of both FAR and FRR are equal, (i.e. FAR = FRR). With such a setting, the system incorrectly rejects and incorrectly identifies the same number of people. The lower the EER value, the higher the accuracy of the system. It is the most widely used indicator for evaluating and comparing biometric systems.
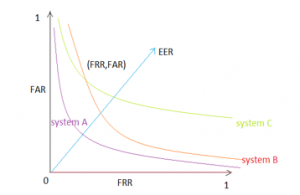
Figure 5: ROC Curves [100]
Receiver Operating Characteristic – ROC
The probability’s curve that is given by the relationship between the probability of false acceptance (FAR) on the x-axis and the corresponding probability of correct acceptance on the y-axis for all allowable threshold values. Using ROC curves, multiple models can be compared with each other. Comparison and evaluation of multiple ROC curves are performed using the Area Under Curve (AUC) areas, which are located below the individual ROC curves [101]. Figure 5 shows the ROCs of the three systems, system A being the best system under the circumstances.
EER, FRR, FAR, ROC was selected for this work. They are a good indicator and the most frequently used tool for evaluating and managing biometric systems.
In articles dealing with biometric systems, we also encounter the concept of accuracy. The accuracy is calculated according to the formula:
![]()
… correct decision (correct rejection and correct acceptance)
… number of recognition attempts
5. Comparison
The most commonly used physiological characteristics in biometric are fingerprint, face, hand geometry, and iris [102]. Table 2 compares biometric systems that use commonly biometric characteristics based on EER. Of these biometric characteristics, most often the lowest EER is achieved, biometric systems working with the iris, but as can be seen in Table 2, other systems, such as fingerprints, also achieve very low EER. However, in addition to error rates compilation speed, acqurability, privacy, cost and ease of use, should also play a role in choosing a biometric system [102].
Table 2: Comparison of selected hand other biometric systems
| Sources | Biometric Characteristic of Recognition | Size of the Database | Performance |
| Chen et al. [103] | Iris | 3 500 | EER = 0.43 |
| Yingzi et al. [104] | Iris | 610 | EER = 0.0295 |
| Wijaya [105] | Face | 2 268 | EER = 0.0457 |
| Marvadi [106] | Face | 427 | EER = 0.1525 |
| Liu et al. [107] | Fingerprint | 350 | EER = 0.0042 |
| Jain & Feng [108] | Fingerprint | 449 | EER = 0.081 |
| Varchol & Levický [109] | Hand geometry | 408 | EER = 0.0462 |
| Jain et al. [110] | Hand geometry | 500 | EER= 0.06 |
Table 3 summarizes the essential characteristics of some systems and methods that appeared in the journal and conferences. Some systems have been tested in identification mode, some in verification mode. Only some papers report EER, FAR / FRR or Accuracy values, some authors evaluate systems using ROC curves. The selection in Table 3 seeks to compare a representative sample of hand-base systems by characteristics (Hand-base Biometric Characteristic, Mode, Techniques Applied for Features Extraction, Techniques Applied for Recognition, Size of the Database, Performance).
Older systems use geometric measurements as features and are mostly in verification mode [110, 115]. Newer systems [111, 117] use a combination of multiple biometric characteristics such as hand shape and hand texture and use deep learning methods. Today’s systems are mainly in identification mode, and FRR or EER has less than 1%.
Table 3: Comparison of selected hand based biometric system
| Sources | Biometric characteristic / Mode | Techniques Applied for Features Extraction | Techniques Applied for Recognition | Size of the Database | Performance |
| Afifi [111] | Hand texture and shape / identification | CNNs + LBP | Support vector machine (SVM) | 11 076 | EER = 0.009 |
| Kumar & Zang [112] | Hand geometry / identification | discretization of hand-geometry features | SVM | 1 000 | Accuracy = 0.94 |
| Shanmukhappa & Sanjeevakumar [113] | Hand geometry /identification | Feature vector construct by hand image graph | SVM (Radial basic function) | 1 440 | FRR = 0.0205 |
| Jain et al. [110] | Hand geometry/ verification | Geometric measurements | Euclidean distance | 500 | EER= 0.06 |
| Varchol & Levický [109] | Hand geometry/ verification | Geometric measurements | Hamming distance | 408 | EER = 0.0973 |
| Villegas et al. [114] | Hand geometry /identification | Wavelet Features | Nearest Neighbour | 120 |
FAR = 0.11 FRR = 0.1 |
| Varchol & Levický [109] | Hand geometry/ verification | Geometric measurements | Gaussian Mixture Model | 408 | EER = 0.0462 |
| Burques et al. [115] | Hand geometry/ verification | Geometric measurements | Distance measure | 12 800 | EER = 0.0016 |
| Charfi et al. [116] | Hand shape/identification |
Scale Invariant Feature Transform (SIFT) |
SIFT Matching | 1 170 | EER = 0.0586 |
|
Yoruk et al. [29]
|
Hand shape /identification | Independent Component Analysis (ICA) | L1/L2 norm of the difference of the feature vectors | 458 | Accuracy = 0.9731 |
|
Yoruk et al. [29]
|
Hand texture /identification | Principal Component Analysis (PCA) | L1/L2 norm of the difference of the feature vectors | 458 | Accuracy = 0.9791 |
|
Yoruk et al. [29]
|
Hand texture /identification | Angular radial transform (ART) | L1/L2 norm of the difference of the feature vectors | 458 | Accuracy = 0.976 |
| Prihodova & Hub [117] | Hand texture and shape / identification | CCN (GoogLeNet) | CCN (Softmax) | 456 | FRR= 0.001 |
6. Research gap
It was not possible to cover all the literature dealing with hand biometric systems, but we included a representative sample of modern methods. However, we were able to identify some research gaps. To make hand-based biometric systems more efficient in real-world applications, the following challenges need to be overcome:
A large number of users – In the real world, it is often necessary to recognize millions of identities. However, the variability between some individuals may be minimal.
Quality of input data – Thanks to the progress of sensing sensors, the input image obtained in a real application under standard lighting conditions is correctly exposed. However, the image quality deteriorates in poor lighting conditions. Other problems we face despite the significant progress of the sensors are accurate colour capture and noise.
The permanence of biometric characteristics – Hand-based biometric characteristics have high stability over time but are not 100 %. For the hand geometry and hand shape, the topography of the bloodstream is primarily a problem of biological ageing and injury.
Attacks on systems – Hand-based biometric systems must face attacks at various levels in real-world applications. One of them is an attack on an input device, where the attacker forged a biometric sample, as a defence against this type of attack is the detection of liveliness.
Datasets – Small datasets are also a problem in this area of research, most current systems are tested on small datasets.
Costs – Costs should always be considered, and efforts should be made to make systems more accessible.
7. Discussion
Given the current state of hand-based biometric recognition, which was described in previous chapters of the article and due to the unresolved challenges in the field, one of the possibilities for further research is the use of a multi-biometric system, which uses hand geometry and thermal properties of hand. The thermal characteristic can be used in the form of blending two images (thermogram and image from the visible part of the electromagnetic spectrum), this blending creates a multispectral image. The multispectral image provides more significant variability between certain individuals than the mere geometry of the hand. A multispectral image is also advantageous in low lighting conditions, the quality of input data decreases less because the thermogram is not dependent on lighting conditions. When using a multispectral image, some types of attacks on biometric systems are also eliminated, because the thermal map of the hand, which is captured by the thermogram, is complicated to imitate and at the same time liveness is detected. At the same time, the multi-biometric system should increase recognition accuracy.
Another research option is also a multi-biometric system using hand geometry or palmprint in combination with skin colour (soft biometrics). This multi-biometric system could help to solve the problem of low variability between specific individuals.
Conflict of Interest
The authors declare no conflict of interest.
Acknowledgement
This article was supported by grant No. 2020_018 supported by the Student Grant Competition.
- K. Prihodova, M. Hub. “Biometric Privacy through Hand Geometry – A Survey” International Conference on Information and Digital Technologies (IDT). IEEE; 395-401, 2019. https://doi.org/10.1109/DT.2019.8813660
- M. Hub. “Bezpečnost a ochrana informací v prostředí internetu” (book in Czech) Pardubice: University of Pardubice, 2013.
- T. Doseděl. “Počítačová bezpečnost a ochrana dat.” (book in Czech) Brno: Computer Press, 2004. ISBN 80-251-0106-1.
- A. Jain, P. Flynn, A. Ross. “Handbook of biometrics” New York: Springer, c2008. ISBN 978-038-7710-419.
- A. W. K. Kong, D. Zhang, M.S. Kamel. “An Analysis of IrisCode” IEEE Transactions on Image Processing. 19(2), 522-532, 2010. DOI: 10.1109/TIP.2009.2033427. ISSN 1057-7149.
- D. Nguyen, T. Pham, Y. Lee, K. Park. “Deep Learning-Based Enhanced Presentation Attack Detection for Iris Recognition by Combining Features from Local and Global Regions Based on NIR Camera Sensor” Sensors. 2018, 18(8). DOI: 10.3390/s18082601. ISSN 1424-8220.
- S. M. Lajevardi, A. Arakala, S. A. Davis, K. J. Horadam. “Retina Verification System Based on Biometric Graph Matching” IEEE Transactions on Image Processing. 22(9), 3625-3635, 2013. DOI: 10.1109/TIP.2013.2266257. ISSN 1057-7149.
- D. Wang, H. Lu, M-H Yang. “Kernel collaborative face recognition” Pattern Recognition. 48(10), 3025-3037, 2015. DOI: 10.1016/j.patcog.2015.01.012. ISSN 00313203.
- Ž. Emeršič, V. Štruc, P. Peer. “Ear recognition: More than a survey” Neurocomputing., 255, 26-39, 2017. DOI: 10.1016/j.neucom.2016.08.139. ISSN 09252312.
- A. K. Jain, J. Feng, K. Nandakumar. “Fingerprint Matching” Computer, 43(2), 36-44, 2010.
- N. Nedjah, R. S. Wyant, L. De Macedo Mourelle. “Efficient biometric palmprint matching on smart-cards for high security and privacy” Multimedia Tools and Applications. 76(21), 22671-22701, 2017. DOI: 10.1007/s11042-016-4271-8. ISSN 1380-7501.
- V. D. Ambeth Kumar, M. Ramakrishnan. “Multiple Feature Extraction for FootPrint Image” National Journal of System and Information Technology. 2012, 5(2), 142, 2012.
- L. Zhu, S. Zhang. “Multimodal biometric identification system based on finger geometry, knuckle print and palm print” Pattern Recognition Letters. 31(12), 1641-1649, 2010. DOI: 10.1016/j.patrec.2010.05.010. ISSN 01678655.
- B. Aghili, H. Sadjedl. “Personal Authentication Using Hand Geometry” In: 2009 International Conference on Computational Intelligence and Software Engineering. IEEE, 2009, 2009, s. 1-4. DOI: 10.1109/CISE.2009.5363947. ISBN 978 1 4244-4507-3.
- Y. Wang, D. Zhang, Q. Ql. “Liveness detection for dorsal hand vein recognition” Personal and Ubiquitous Computing. 20(3), 447-455, 2016. DOI: 10.1007/s00779-016-0922-z. ISSN 1617-4909.
- D. Frumkin, A. Wasserstrom, A. Davidson, A. Grafit. “Authentication of forensic DNA samples” Forensic Science International: Genetics. 2010, 4(2), 95-103. DOI: 10.1016/j.fsigen.2009.06.009. ISSN 18724973.
- “Voice biometrics growth likely” Biometric Technology Today. 2009, 17(6), 3-4. DOI: 10.1016/S0969-4765(09)70085-2. ISSN 09694765.
- T. Scheidat, M. Kalbitz, C. Vielhauer. “Biometric authentication based on 2D/3D sensing of forensic handwriting traces” IET Biometrics. 2017, 6(4), 316-324. DOI: 10.1049/iet-bmt.2016.0127. ISSN 2047-4938.
- T. Hafs, L. Bennacer, M. Boughazi, A. Nait-Ali. “Empirical mode decomposition for online handwritten signature verification” IET Biometrics. 2016, 5(3), 190-199. DOI: 10.1049/iet-bmt.2014.0041. ISSN 2047-4938.
- T. K. M. Lee, M. Belkhatir, S. Sanei. “A comprehensive review of past and present vision-based techniques for gait recognition” Multimedia Tools and Applications. 2014, 72(3), 2833-2869. DOI: 10.1007/s11042-013-1574-x. ISSN 1380 7501.
- Information technology – Biometric performance testing and reporting – ISO/IEC 19795-1. City, 2006.
- R. Miller. “Finger dimension comparison identification system” USA. US3576538 (A). Written down 27.4.1971.
- B. Miller. “Vital signs of identity [biometrics]” IEEE Spectrum. 1994, 31(2), 22 30. DOI: 10.1109/6.259484. ISSN 0018-9235.
- D. Sisdlouskas. “3D hand profile identification apparatus” 1988. USA. US4736203A. Written down 5.4.1988.
- Immigration and naturalization service passenger accelerated service system pilot program. Office of the Inspector General [online]. Washington, DC.
- Technology assessment. Edtion ed. Washington, DC (PO Box 37050, Washington 20013): US General Accounting Office, 2002.
- D. Maltoni. “Handbook of fingerprint recognition” 2nd ed. London: Springer, c2009. ISBN 978-184-8822-542.
- X. Fan, H. Zhang, C. Leung, C. Miao. “Comparative study of machine learning algorithms for activity recognition with data sequence in home-like environment” In: 2016 IEEE International Conference on Multisensor Fusion and Integration for Intelligent Systems (MFI). IEEE, 2016, 2016, s. 168-173. DOI: 10.1109/MFI.2016.7849484. ISBN 978-1-4673-9708-7.
- E. Yoruk, H. Dutagaci, B. Sankur. “Hand biometrics. Image and Vision Computing” 2006, 24(5), 483-497. DOI: 10.1016/j.imavis.2006.01.020. ISSN 02628856.
- D. P. Sidlauskas, S. Tamer. “Hand Geometry Recognition” 2008, In: Jain A.K., Flynn P., Ross A.A. (eds) Handbook of Biometrics. Springer, Boston, MA. https://doi.org/10.1007/978-0-387-71041-9_5
- R. Rak, V. Matyáš, Z. Říha. “Biometrie a Identita Člověka: Ve Forenzních a Komerčních Aplikacích” (book in Czech) 1electronic edition ed. Prague: Grada; 2008.
- B. Lindstrom “Hand Geometry A Biometric Technology with a Pedigree BiometriTech June 2003 Bruce Lindstrom, Regional Sales Manager” 2003. https://slideplayer.com/slide/5032579/
- J. A. Unar, W. C. Seng, A. Abbasi. “A review of biometric technology along with trends and prospects” Pattern Recognition. 2014, 47(8), 2673-2688. DOI: 10.1016/j.patcog.2014.01.016. ISSN 00313203.
- A. Ross “An introduction to multibiometrics.” IEEE; 2007.
- B. Aghili, H. Sadjedi. “Personal Authentication Using Hand Geometry” In: 2009 International Conference on Computational Intelligence and Software Engineering. IEEE, 2009, 2009, s. 1-4. DOI: 10.1109/CISE.2009.5363947. ISBN 978 1 4244-4507-3.
- G. Fouquier, L. Likforman, J. Darbon, B. Sankur. “The Biosecure Geometry-Based System for Hand Modality” In: 2007 IEEE International Conference on Acoustics, Speech and Signal Processing – ICASSP ’07. IEEE, 2007, 2007, I-801-I-804. DOI: 10.1109/ICASSP.2007.366029. ISBN 1-4244-0727-3.
- R. Sanchez-Reillo, C. Sanchez-Avila, A. Gonzalez-Marcos. “Biometric identification through hand geometry measurements” IEEE Transactions on Pattern Analysis and Machine Intelligence. 2000, 22(10), 1168-1171. DOI: 10.1109/34.879796. ISSN 01628828.
- De Santos Sierra, A. J. G. Casanova, C. S. Avila, V. J. Vera. “Silhouette-based hand recognition on mobile devices” In: 43rd Annual 2009 International Carnahan Conference on Security Technology. IEEE, 160-166, 2009. DOI: 10.1109/CCST.2009.5335548. ISBN 978-1-4244-4169-3.
- C. Oden, A. Ercil, B. Buke. “Combining implicit polynomials and geometric features for hand recognition” Pattern Recognition Letters. 2003, 24(13), 2145-2152. DOI: 10.1016/S0167-8655(03)00087-4. ISSN 01678655.
- E. Yoruk, E. Konukoglu, B. Sankur, J. Darbon. “Shape-based hand recognition” In: IEEE Transactions on Image Processing. IEEE, 2006, 15(7), s. 1803-1815. DOI: 10.1109/TIP.2006.873439. ISSN 1057-7149.
- S. A. Angadi, S. M. Hatture. “Biometric Person Identification System: A Multimodal Approach Employing Spectral Graph Characteristics of Hand Geometry and Palmprint” International Journal of Intelligent Systems and Applications. 2016, 8(3), 48-58. DOI: 10.5815/ijisa.2016.03.06. ISSN 2074904X.
- M. Ferrer, C. Travieso, J. Alonso. “Multimodal Biometric System based on Hand Geometry and Palm Print Texture” In: Proceedings 40th Annual 2006 International Carnahan Conference on Security Technology. IEEE, 2006, 2006, s. 92-97. DOI: 10.1109/CCST.2006.313435. ISBN 1-4244-0174-7.
- A. Kirthika, S. Arumugam. “Texture and colour intensive biometric multimodal security using hand geometry and palm print. “International Journal of Advances in Engineering & Technology. 2012, 4(1), 226-235. ISSN 2231-1963.
- T. O. Oladele, K. Adeniyi, T. O. Aro. “Framework for User Authentication at a Distance for Mobile Phones Using Contactless Hand-based Multimodal Biometric System” Journal of Computer Science and Control Systems. ProQuest Central, 2019, 12(1), 24-27. ISSN 1844-6043.
- W.-C. Wang, W.-S. Chen, S.-W. Shih. “Biometric recognition by fusing palmprint and hand-geometry based on morphology” In: 2009 IEEE International Conference on Acoustics, Speech and Signal Processing. IEEE, 2009, 2009, s. 893-896. DOI: 10.1109/ICASSP.2009.4959728. ISBN 978-1-4244-2353-8.
- P. Gupta, S. Srivastava, P. Gupta. “An accurate infrared hand geometry and vein pattern-based authentication system” Knowledge-Based Systems.103, 143-155, 2016. DOI: 10.1016/j.knosys.2016.04.008. ISSN 09507051.
- E. C. Lee, H. Jung, D. Kim. “New Finger Biometric Method Using Near Infrared Imaging” Sensors. 11(3), 2319-2333, 2011. DOI: 10.3390/s110302319. ISSN 1424-8220.
- C. Oden, A. Ercil, B. Buke. “Combining implicit polynomials and geometric features for hand recognition “Pattern Recognition Letters.24(13), 2145-2152, 2003. DOI: 10.1016/S0167-8655(03)00087-4. ISSN 01678655.
- M. A. Ferrer, A. Morales, C. M. Travieso, J. B. Alonso. “Low Cost Multimodal Biometric Identification System Based on Hand Geometry, Palm and FingerPrint Texture” In: 2007 41st Annual IEEE International Carnahan Conference on Security Technology. IEEE, 2007, 2007, s. 52-58. DOI: 10.1109/CCST.2007.4373467. ISBN 978-1-4244-1129-0.
- F. Yang, B. Ma. “A New Mixed-Mode Biometrics Information Fusion Based-on Fingerprint, Hand-geometry and Palm-print” In: Fourth International Conference on Image and Graphics (ICIG 2007). IEEE, 2007, 2007, s. 689-693. DOI: 10.1109/ICIG.2007.39. ISBN 978-0-7695-2929-5.
- A. Ross, A. Jain. “Information fusion in biometrics. Pattern” Recognition Letters. 2003, 24(13), 2115-2125. DOI: 10.1016/S0167-8655(03)00079-5. ISSN 01678655.
- M. Kim, W.-Y. Kim, J. Paik. “Optimum Geometric Transformation and Bipartite Graph-Based Approach to Sweat Pore Matching for Biometric Identification” Symmetry. 2018, 10(5), 175. DOI: 10.3390/sym10050175. ISSN 2073 8994.
- M. Adán, A. Adán, A. S. Vázquez, R. Torres. “Biometric verification/identification based on hands natural layout” Image and Vision Computing. 2008, 26(4), 451-465. DOI: 10.1016/j.imavis.2007.08.010. ISSN 02628856.
- S. Gonzeilez, C. M. Travieso, J. B. Alonso, M. A. Ferrer. “Automatic biometric identification system by hand geometry” In: IEEE 37th Annual 2003 International Carnahan Conference onSecurity Technology, 2003. Proceedings. IEEE, 2003, s. 281-284. DOI: 10.1109/CCST.2003.1297573. ISBN 0-7803-7882-2.
- R. Gross, Y. Li, L. Sweeney, X. Jiang, W. Xu, D. Yurovsky “Robust Hand Geometry Measurements for Person Identification using Active Appearance Models” In: 2007 First IEEE International Conference on Biometrics: Theory, Applications, and Systems. IEEE, 2007, 2007, s. 1-6. DOI: 10.1109/BTAS.2007.4401936. ISBN 978-1-4244-1596-0.
- N. Charfi, H. Trichili, A. M. Alimi, B. Solaiman. “Personal recognition system using hand modality based on local features” In: 2015 11th International Conference on Information Assurance and Security (IAS). IEEE, 2015, 2015, s. 13-18. DOI: 10.1109/ISIAS.2015.7492764. ISBN 978-1-4673-8715-6.
- S. Xu, M. Li, J. F. Ding, Y. Q. Cui. “Personal Identification by Fusing Hand Shape Geometry and Palmprint Features” Applied Mechanics and Materials, 278-280, 1228-1231, 2013. DOI: 10.4028/www.scientific.net/AMM.278-280.1228. ISSN 1662-7482.
- A. Iula, G. Hine, A. Ramalli, F. Guidi. “An Improved Ultrasound System for Biometric Recognition Based on Hand Geometry and Palmprint” Procedia Engineering.87, 1338-1341, 2014. DOI: 10.1016/j.proeng.2014.11.709. ISSN 18777058.
- R. Sanchez-Reillo. “Hand geometry pattern recognition through Gaussian mixture modelling” In: Proceedings 15th International Conference on Pattern Recognition. ICPR 2000. IEEE Comput. Soc, 2000, s. 937-940. DOI: 10.1109/ICPR.2000.906228. ISBN 0-7695-0750-6.
- V. Kanhangad, A. Kumar, D. Zhang. “Human hand identification with 3D hand pose variations” In: 2010 IEEE Computer Society Conference on Computer Vision and Pattern Recognition – Workshops. IEEE, 2010, 2010, s. 17-21. DOI: 10.1109/CVPRW.2010.5543236. ISBN 978-1-4244-7029-7.
- J.M. Guo, C.-H. Hsia, Y.-F. Liu, J.-C. Yu, M.-H. Chu, T.-N. Le. “Contact-free hand geometry-based identification system. Expert Systems with Applications” 2012, 39(14), 11728-11736. DOI: 10.1016/j.eswa.2012.04.081. ISSN 09574174.
- A. Morales, M. A. Ferrer, J. B. Alonso, C. M. Travieso. “Comparing infrared and visible illumination for contactless hand based biometric scheme.” In: 2008 42nd Annual IEEE International Carnahan Conference on Security Technology. IEEE, 2008, 2008, s. 191-197. DOI: 10.1109/CCST.2008.4751301. ISBN 978-1-4244-1816-9.
- A. Jian, N. Duta. “Deformable matching of hand shapes for user verification” In: Proceedings 1999 International Conference on Image Processing (Cat. 99CH36348). IEEE, 1999, s. 857-861. DOI: 10.1109/ICIP.1999.823019. ISBN 0 7803 5467-2.
- M. Ferrer, A. Morales, C. M. Travieso, J. B. Alonso. “Influence of the pegs number and distribution on a biometric device based on hand geometry” In: 2008 42nd Annual IEEE International Carnahan Conference on Security Technology. IEEE 2008, 221-225, 2008. DOI: 10.1109/CCST.2008.4751305. ISBN 978-1-4244-1816-9.
- G. Boreki, A. Zimmer. “Hand Geometry: A New Approach for Feature Extraction” In: Fourth IEEE Workshop on Automatic Identification Advanced Technologies (AutoID’05). IEEE, 2005, s. 149-154, 2005. DOI: 10.1109/AUTOID.2005.33. ISBN 0-7695-2475-3.
- M. Faundez-Zanuy. “Biometric verification of humans by means of hand geometry” In: Proceedings 39th Annual 2005 International Carnahan Conference on Security Technology. IEEE, 2005, 2005, s. 61-67. DOI: 10.1109/CCST.2005.1594816. ISBN 0-7803-9245-0.
- A. Bera, D. Bhattacharjee, M. Nasipuri. “Finger contour profile-based hand biometric recognition” Multimedia Tools and Applications. 2017, 76(20), 21451-21479. DOI: 10.1007/s11042-016-4075-x. ISSN 1380-7501.
- J. Doublet, O. Lepetit, M. Revenu. “Contactless Hand Recognition Based on Distribution Estimation” In: 2007 Biometrics Symposium. IEEE, 2007, 2007, s. 1-6. DOI: 10.1109/BCC.2007.4430547. ISBN 978-1-4244-1548-9.
- M. Španěl, V. Beran. “Obrazové segmentační techniky: Přehled existujících metod” (book in Czech) Brno, 2006. Brno University of Technology.
- G. Amayeh, G. Bebis, A. Erol, M. Nicolescu. “Peg-Free Hand Shape Verification Using High Order Zernike Moments.” In: 2006 Conference on Computer Vision and Pattern Recognition Workshop (CVPRW’06). New York: IEEE, 2006, s. 40-40. DOI: 10.1109/CVPRW.2006.155. ISBN 0-7695-2646-2. ISSN 2160-7508.
- A. M. Badawi, M.S. Kamel. “Free style hand geometry verification system” In: 2003 46th Midwest Symposium on Circuits and Systems. IEEE, 2003, s. 324-327, 2003. DOI: 10.1109/MWSCAS.2003.1562284. ISBN 0-7803-8294-3. ISSN 1548-3746.
- M. Golfarelli, D. Maio, D. Malton. “On the error-reject trade-off in biometric verification systems” IEEE Transactions on Pattern Analysis and Machine Intelligence. 1997, 19(7), 786-796. DOI: 10.1109/34.598237. ISSN 01628828.
- J. Mintalvao, L. Molina, J. Canuto. “Robust hand image processing for biometric application” Pattern Analysis and Applications. 2010, 13(4), 397 407, 2010. DOI: 10.1007/s10044-010-0185-7. ISSN 1433-7541.
- A. Bapat, V. Kanhangad. “Segmentation of hand from cluttered backgrounds for hand geometry biometrics” In: 2017 IEEE Region 10 Symposium (TENSYMP). IEEE, 2017, 2017, s. 1-4. DOI: 10.1109/TENCONSpring.2017.8070016. ISBN 978-1-5090-6255-3.
- J. Král, “Rozpoznávání výrazu práce” Brno, 2010. Thesis. Technical University Brno.
- N. Covavisaruch, P. Prateepamornkul, P. Ruchikachorn, P. Taksaphan. “Personal verification and identification using hand geometry” ECTI Transactions on Computer and Information Technology (ECTI-CIT), 1(2), 134-140, 2005.
- V. Kanhangad, A. Kumar, D. Zhang. “Combining 2D and 3D hand geometry features for biometric verification” In: 2009 IEEE Computer Society Conference on Computer Vision and Pattern Recognition Workshops. IEEE, 2009, 39-44, 2009. DOI: 10.1109/CVPRW.2009.5204306. ISBN 978-1-4244-3994-2
- X. Jiang, W. Xu, L. Sweeney, Y. Li, R. Gross, D. Yurovsky. “New Directions in Contact Free Hand Recognition” In: 2007 IEEE International Conference on Image Processing. IEEE, 2007, – 389-392, 2007. DOI: 10.1109/ICIP.2007.4379174. ISBN 978-1-4244-1436-9.
- S. Sharma, S. R. Dubey, S. K. Singh, R. Saxena, R. K. Singh. “Identity verification using shape and geometry of human hands” Expert Systems with Applications. Elsevier, 2015, 42(2), 821-832, 2015. DOI: 10.1016/j.eswa.2014.08.052. ISSN 09574174.
- T. Fotak, P. Koruga, M Baca. “Trends in Hand Geometry Biometrics” In: Central European Conference on Information and Intelligent Systems. Varazdin: Faculty of Organization and Informatics Varazdin, 2012, s. 319-324.
- D. L. Woodard, P. J. Flynn. “Finger surface as a biometric identifier. Computer Vision and Image Understanding” Elsevier, 2005, 100(3), 357-384, 2005. DOI: 10.1016/j.cviu.2005.06.003. ISSN 10773142.
- N. Charfi, H. Trichili, A. M. Alimi, B. Solaiman. “Novel hand biometric system using invariant descriptors” In: 2014 6th International Conference of Soft Computing and Pattern Recognition (SoCPaR). IEEE, 2014, 2014, s. 261-266. DOI: 10.1109/SOCPAR.2014.7008016. ISBN 978-1-4799-5934-1.
- W. Kang, Q. Wu. “Pose-invariant hand shape recognition based on finger geometry” IEEE Transactions on Systems, Man, and Cybernetics: Systems 44(11):1510–1521. 2014.
- A. Ungureanu, S. Salahuddin, P. Corcoran. “Towards unconstrained palmprint recognition on consumer devices: A literature review”, 2020. DOI:10.1109/ACCESS.2020.2992219
- R. S. Choraś, M. Choraś. “Hand shape geometry and palmprint features for the personal identification” 2006. IEEE Proc. of 6th Intl Conf. on Intelligent Systems Design and Applications, p 1085–1090.
- A. Bera, D. Bhattacharjee. “Human Identification Using Selected Features From Finger Geometric Profiles” IEEE Transactions on Systems, Man, and Cybernetics: Systems. 2020, 50(3), 747-761. DOI: 10.1109/TSMC.2017.2744669. ISSN 2168-2216.
- A. Ungureanu, S. Salahuddin, P. Corcoran. “Towards unconstrained palmprint recognition on consumer devices: A literature review” 2020. DOI:10.1109/ACCESS.2020.2992219.
- K. Příhodová. “Convolutional neural networks in hand-based recognition system” In: 34th International Business Information Management Association Conference. 2019, 4744 4750. ISBN 978-0-9998551-3-3.
- A. Kumar, D. C. M. Wong, H. C. Shen, A. K. Jain. “Personal Verification Using Palmprint and Hand Geometry Biometric” In: Audio- and Video-Based Biometric Person Authentication. Berlin, Heidelberg: Springer Berlin Heidelberg, 2003, 2003-6-24, s. 668-678. Lecture Notes in Computer Science. DOI: 10.1007/3-540-44887-X_78. ISBN 978-3-540-40302-9.
- T. Mitchell, “Machine learning” Boston: McGraw-Hill, c1997. ISBN 00 704 2807-7.
- Vinodkumar, R. Srikantaswamy. “Fusion of fingerprint, palmprint and hand geometry for an efficient multimodal person authentication system” In: 2016 2nd International Conference on Applied and Theoretical Computing and Communication Technology (iCATccT). IEEE, 2016, 2016, s.
- J. J. Fuertes, C. M. Travieso, M. A. Ferrer, J. B. Alonso. “Intra-modal biometric system using hand-geometry and palmprint texture” In: 44th Annual 2010 IEEE International Carnahan Conference on Security Technology. IEEE, 2010, 2010, s. 318-322. DOI: 10.1109/CCST.2010.5678697. ISBN 978-1-4244-7403-5.
- A. Kumar, D. Zhang. “Hand-Geometry Recognition Using Entropy-Based Discretization. IEEE Transactions on Information Forensics and Security” 2007, 2(2), 181-187. DOI: 10.1109/TIFS.2007.896915. ISSN 1556-6013.
- X.Fan, X. H. Zhang, C. Leung, C. Miao. “Comparative study of machine learning algorithms for activity recognition with data sequence in home-like environment” In: 2016 IEEE International Conference on Multisensor Fusion and Integration for Intelligent Systems (MFI). IEEE, 2016, 2016, s. 168-173. DOI: 10.1109/MFI.2016.7849484. ISBN 978-1-4673-9708-7.
- M. Ferrer, J. Fabregas, M. Faundez, J. B. Alonso, C. Travieso. “Hand geometry identification system performance” In: 43rd Annual 2009 International Carnahan Conference on Security Technology. IEEE, 2009, 2009, s. 167-171. DOI: 10.1109/CCST.2009.5335545. ISBN 978-1-4244-4169-3.
- O. Polat, T. Yildirim. “Hand geometry identification without feature extraction by general regression neural network” Expert Systems with Applications. 2008, 34(2), 845-849. DOI: 10.1016/j.eswa.2006.10.032. ISSN 09574174.
- S. J. Elliott, B. Senjaya, E. P. Kukula J. M. Werner, M. Wade. “An evaluation of the Human Biometric Sensor Interaction using hand geometry” In: 44th Annual 2010 IEEE International Carnahan Conference on Security Technology. IEEE, 2010, 2010, s. 259-265. DOI: 10.1109/CCST.2010.5678710. ISBN 978 1 4244 7403-5.
- E. P. Kukula, B. P. Gresock, S. J. Elliott, N. W. Dunning. “Defining Habituation using Hand Geometry” In: 2007 IEEE Workshop on Automatic Identification Advanced Technologies. IEEE, 2007, 2007, s. 242-246. DOI: 10.1109/AUTOID.2007.380627. ISBN 1-4244-1299-4.
- ISO/IEC 19795-1. Information technology: Biometric performance testing and reporting. 2016.
- M. R. Rajput and G. S. Sable, “IRIS biometrics survey 2010–2015,” 2016 IEEE International Conference on Recent Trends in Electronics, Information & Communication Technology (RTEICT), Bangalore, 2016, pp. 2028-2033, DOI: 10.1109/RTEICT.2016.7808195.
- J. Továrek, “Využití umělé inteligence pro vícenásobnou bezkontaktní biometrickou autentizaci” (in Czech) Ostrava, 2017. Ph.D Thesis. VSB – Technical University of Ostrava.
- R.M. Bolle, J.H. Connell, Pankanti S., Ratha N.K. and Senior A.W. The Common Biometrics. In: Guide to Biometrics. Springer Professional Computing. Springer, New York, NY. 2004.
- R. Chen, X.R. Lin, T.H. Ding “Iris segmentation for non-cooperative recognition systems” IET Image Process., 5 (2011), 448-456, 2011.
- Y. Du, E. Arslanturk, Z. Zhou, C. Belcher. “Video-Based Noncooperative Iris Image Segmentation” IEEE Transactions on Systems, Man, and Cybernetics, Part B (Cybernetics), 41(1):64-74, 2011.
- I G. P. Suta Wijaya. “Face Recognition Using Map Discriminant on YCbCr Color Space.” 2018.
- D. Marvadi, C. Paunwala, M. Joshi, A. Vora. “Comparative analysis of 3D face recognition using 2D-PCA and 2D-LDA approaches” IEEE; 2015;2016.
- F. Liu, G. Liu, Q. Zhao, L. Shen. “Robust and high-security fingerprint recognition system using optical coherence tomography” Neurocomputing (Amsterdam). 2020. 402:14-28, 2020.
- F. Liu, J. Liang, L. Shen, M. Yang, D. Zhang, Z. Lai. “Case study of 3D fingerprints applications” PLoS ONE. 2017; 12(4) 0175261.
- P. Varchol and D. Levický, “Using of hand geometry in biometric security systems”, Radio Eng., 16(4), 82-87, 2007.
- A.K. Jain, A. Ross and S. Pankanti, “A prototype hand geometry-based verification system”, Proc. Second Int. Conf. Audio and Video based Personal Authentication, pp. 166-171, 1999.
- M. Afifi. “11K Hands: Gender recognition and biometric identification using a large dataset of hand images” Multimedia tools and applications. 2019;78(15):20835-54.
- A. Kumar, D. Zhang “Hand-Geometry Recognition Using Entropy-Based Discretization” IEEE Transactions on Information Forensics and Security. 2007;2(2):181-7.
- S. Angadi, S. Hatture “Hand geometry-based user identification using minimal edge connected hand image graph” IET computer vision. 2018;12(5):744-52.
- O. Vergara Villegas, H. J. Ochoa Dominguez, V. G. Cruz Sanchez, L. Ortega and H. Madero. “Biometric Human Identification of Hand Geometry Features Using Discrete Wavelet Transform” Discrete Wavelet Transforms – Biomedical Applications. InTech, 2011, 2011 09-12, 251-266. ISBN 978-953-307-654-6.
- J. Burgues, J. Fierrez, D. Ramos, M. Puertas and J. Ortega-Garcia, „Detection Invalid Samples in Hand Geometry Verification via Geometric Measurements”, 2010 International Workshop on Emerging Techniques and Challenges for Hand-Based Biometrics, Istanbul, 2010, s. 1-6, DOI: 10,1109 / ETCHB.2010.5559296.
- N. Charfi, H. Trichili, A. M. Alimi and B. Solaiman, “Novel hand biometric system using invariant descriptors,” 2014 6th International Conference of Soft Computing and Pattern Recognition (SoCPaR), Tunis, 2014, pp. 261-266, doi: 10.1109/SOCPAR.2014.7008016.
- K. Prihodova and M. Hub. “Hand-Based Biometric System Using Convolutional Neural Networks”. Acta Informatica Pragensia, 9(1), 48-57. 2020. doi: 10.18267/j.aip.131.

