LEACH Based Protocols: A Survey
Volume 5, Issue 6, Page No 1258-1266, 2020
Author’s Name: Nour Najeeb Abdalkareem Qubbaja), Anas Abu Taleb, Walid Salameh
View Affiliations
Computer Science Department, Princess Sumaya University of Technology, Amman, 11941, Jordan
a)Author to whom correspondence should be addressed. E-mail: nou20188107@std.psut.edu.jo
Adv. Sci. Technol. Eng. Syst. J. 5(6), 1258-1266 (2020); ![]() DOI: 10.25046/aj0506150
DOI: 10.25046/aj0506150
Keywords: Fuzzy Logic, Energy efficiency, Hierarchical routing protocols, LEACH, CHs (clusters Head), WSN
Export Citations
Advances in the world of communications and information technology, as well as the urgent necessity to monitor particular areas and regions, have led to a considerable and influential development in the world of wireless sensor nodes. As they are small, low-cost multi-purpose nodes with limited energy and capabilities. The most important points that deserve research and solution is the problem of energy conservation and increasing the lifetime of the network as a whole. Whereas, many routing protocols have been proposed in the wireless sensor network, some of which are based on homogenous networks while others are not, some are location-based, some are based on hierarchical orientation, some are based on the hybrid approach and many more. Despite the long time that has passed since the discovery and activation of the Low Energy Adaptive Clustering Hierarchy (LEACH) protocol, it and its descendants still have the lion’s share of attention, research, and development. In this research, we will be presenting the most prominent routing protocols while pointing to some pros and cons of each protocol.
Received: 10 October 2020, Accepted: 06 December 2020, Published Online: 16 December 2020
1. Introduction
“This paper is an extension of work originally presented in “11th International Conference on Information and Communication Systems (ICICS). IEEE, 2020” [1].
Wireless sensor networks (WSN) can be defined as collection of thousands or hundreds of thousands of small self-configuring sensor nodes that bond together and collaborate to aggregate information and send it to a central station. The purpose simply is to get rid of the human aspect [2]. Usually, (these nodes being distributed randomly by aircrafts to serve military interests, detecting natural disasters like fires and earthquakes, also it plays a huge role in some peaceful applications such as detection of a specific disease in a specific crop, health care, electronic sales, and others [2]. On the other hand, routing is defined as the process of exactly determining the path from the main source to the final destination, and it must be fast and reliable as well.
As a reminder, these nodes are thrown from aircraft randomly and to places that are difficult for humans to reach, so they must remain functional as long as possible. Unfortunately, the only energy source for them is the battery and it is known that the battery depletes quickly and the node dies at that time. Therefore, the most important challenge is to keep the nodes alive as much as possible and distribute the total energy wisely, and not lose their energy, especially in the early stages. Researchers have provided a massive number of routing protocols and classify them on several levels, considerations, and parameters [1].
The rest of our research is split into the following sections: in section II the problems of routing are presented. In section III. Most important WSN routing methods. In section IV. Furthermore, Low energy adaptive clustering hierarchy (LEACH), the before the last section V. Different routing protocols based on (LEACH) protocol, the last VI. Conclusion and future work subsequently reference.
2. The Problems of Routing
In WSN, routing protocols can be considered to be dependent on the application, the data to be collected, and the good use of limited energy. A good routing protocol is a protocol that has several advantages, including simplicity, ability to know its energy level, ability to expand and adapt under the limited capabilities of the nodes, to name a few: power, memory, computation capabilities, and bandwidth allocated to the network according to [3]. The main purpose of the network design is to deliver all the information from the deployed nodes to the base station (BS) with the lowest possible power. This design faces several obstacles, including [1,3]:
2.1. Deployment of nodes
Deployment of nodes relies on the type of application that massively affects the efficiency of the routing protocol. Where the deployment of the sensor nodes may be random (self-organizing), by plane, for example, or be in a specific and thoughtful place. The node may be fixed, not moving, and it may be mobile, or all of them are stationary and the main station is mobile.
Location and movement play an important bit part in energy efficiency.
2.2. Conservation of energy
Data and information are transmitted by radio through the network, the power of the radio is inversely proportional to the square of the distance traveled, and the power consumption will be affected in the event of obstacles. Therefore, it is better to use the multi-hop approach rather than one-hop. It is worth noting that the one-hop orientation is suitable for a network with a small number of nodes and close to each other, which confirms that energy is affected by the paths that you take.
2.3. Tolerance of Faults
Error tolerance can be described as the ability of the network to continue its operation in the presence of obstacles. Such as the nodes death. For example, the routing protocol must quickly find an alternate route to cancel an insufficiency of information to the main (Base) station.
2.4. WSN Scalability
The number of nodes in the target area to be monitored will exceed hundreds or thousands. Thus the routing protocol must be able to accommodate this large density of nodes.
2.5. Constraints on hardware
All components of the nodes including, the power unit (battery), the processing unit (memory and the microprocessor unit), the sensor unit (sensor), and the radio communication unit, must be smaller in size, less expensive, and energy-consuming.
2.6. The surrounding environment
The node must be prepared for the difficult conditions in which it will monitor.
2.7. Transmission Media
From the name (WSN), we find that the mean of communication is wireless communication, as it is vulnerable to the rate of error and greatly influences the correct operation of the network.
2.8. Models for data delivery
Delivering the data to the main station is related to the type of application, it may be continuous, where all the data is sent to the station continuously and periodically. While if the connection is related to an event, the node sends its data when a specific event occurs. The communication may also be inquiry-oriented, so that when the station needs to inquire about a specific piece of information from the nodes, and the connection may be a hybrid connection consisting of two or more of the mentioned methods. Finally, it’s worth pointing that the routing protocol being influenced by the type of that connection significantly.
2.9. Information aggregation (fusion)
The cluster head (CH) collects data from more than one node, so there is a possibility of duplicating data, especially adjacent nodes, so CH does this data fusion process to minimize the volume of the transmitted data to the main station.
2.10. Capacity of node
The capacity of a node this means that it is possible to assign a specific sensor node to one of the functions(tasks) (relaying, sensing, aggregation) according to the application, instead of giving the node all the functions(tasks) together to avoid consuming excess energy.
3. Most Important WSN Routing Methods
Route pathways may be defined in one of three forms i.e. reactive, proactive, or mixed, the reactive paths calculate the paths when the actual necessity of them. While the proactive route precedes the occurrence of the real event and stores the possible paths in a table for each node, it is heavy-duty due to the huge number of network nodes. The last type is the combination of the characteristics of both proactive and reactive see Fig 1.
Based on the design of network flow, the routing protocols are classified into flat-routing, hierarchical and location-based routing. In flat-based routing, all nodes execute the same task such that data is transferred from each sensor node with a strong data repetition [3].
Hierarchical Protocols, the clusters are formed in this type to raise energy efficiency and accommodate a large number of nodes and cover a larger area of the network with better efficiency by applying two main steps. The first one is determining the head of the cluster. The second is the path from the head of the cluster to the main station. [3].
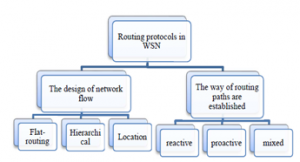
Figure 1: Routing protocols kinds [1].
Location-based protocols, some applications may require the location of the node to calculate the distance between the nodes. There are several ways to calculate this, including (Global Positioning System) GPS or other ways [3]. See Fig 1.
The most rudimentary way to transfer data from the nodes to the base station is that each node does this by itself without an intermediary, which is known as Direct Transmission (DT), as it is considered one of the flat and simple protocols. And another example of it too is Minimum Transmission Energy (MTE). Whereas, the nodes that are farther from the base station and the nodes with a large volume of data require more energy than others. Therefore, the hierarchical protocols are distinguished from the flat and simple protocols, such as the ones mentioned.
The working principle of the clustering methods of WSN, is based on dividing the entire network into groups called the clusters, and in each cluster, there is a header that gathers data from the rest of the nodes, merges them, reduces their size, and sends them at once to the Base Station (BS) and the role of this head is exchanged with the rest of the nodes in the clustering according to the followed protocol [4]. Cluster formation has several characteristic and advantages, so it excels over flat protocols, including [5]:
- Easily handle the complexity of the network: The network is composed of nodes that act as the head of the cluster and that communicate directly with the main station on behalf of all the nodes of the cluster, and other nodes that collect data from the surrounding environment and send it to the head of the cluster that does not have another load, thus the master station receives data from a small number of nodes rather than all of the cluster members and thus facilitates control of the network as a whole see Figure 2.
- Aggregation / Fusion of information: Where the CH integrates and collects information from the rest of the members and reduces its size before sending it to the base station, the base station receives data from a small number of nodes rather than all of the cluster members.

Figure 2: Creation of clusters [6].
- The life of the network is stronger and longer: By rotating the head of the cluster in every round to distribute an equal distribution of energy among the network members.
- Reducing collisions and traffic: In a WSN with a flat communication model, all the nodes must send their information to the main station at the same time. In the clustering organized, the communication with the main station is limited only to the head of the clusters.
4. Low Energy Adaptive Clustering Hierarchy (LEACH)
It is the parent protocol for hierarchical routing based on Clustering proposed by W.B. Heinzelman [7]. As has been reported, the clustering protocols have proven effective in distributing energy consumption among members and increasing the life of the network as a whole.
LEACH works on the principle of dividing the network into random groups (clusters) and then choosing a node from each group to be the head node to represent its group while connecting to BS. The role of the cluster head rotates to keep the energy consumption distributed among the network members. It’s worth pointing that the head nodes have the heading role as an additional role to their original tasks (tasks of the non-cluster head nodes). It is also a kind of one-step approach (one-hop routing) to the BS. The LEACH principle is divided into several rounds, and each round contains two basic stages: One is the Setup stage, and the other is the Steady stage as shown in Figure 3.
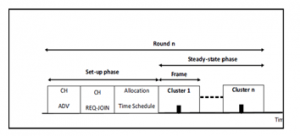
Figure 3: Operation of LEACH [8].
The node must initially pick a random number (n). If this number (n) is less than the threshold specified in the first equation T(n), then the node is selected as the cluster header (CH).

while p is the possibility of a cluster head (CH), G is a list of nodes that will never be chosen as cluster-head (CH) nodes until the 1 / p level.
After selecting the heads of the cluster according to the number (n), each cluster head will broadcast its status to all other nodes via CDMA (Code Division Multiple Access). After receiving broadcast messages from CHs, each normal node uses the Received Signal Strength (RSS) to determine which CHs are closest to it. Then the CH creates TDMA (Time Division Multiple Access) to divide a schedule for members of the same group (cluster) so that the normal node is activated and connected to CH at the time allotted to it according to the TDMA schedule. It will be inactive at other times to preserve its energy, which means that CH deals with all nodes from the same cluster and is the only one who deals with BS from cluster members [9]. Note that the period of the Steady stage is longer than the Setup stage.
The significant drawbacks of LEACH are the following, according to [1,2,10]:
- Since LEACH (one-hop routing) to the BS is never suitable for a large network of sensors.
- Not suitable for time-compulsory applications due to delays.
- Unacceptable distribution for cluster heads: as have been stated earlier, a random selection of CH that is not based on clear criteria such as the distance between CH and BS, causes an imbalance in the power consumption of the network and this is considered a significant drawback.
- Unacceptable selection of cluster head: The randomness in choosing the head of the cluster so that the primordial energy of each node is not taken before it is considered as the head of the cluster.
- Note that the types of data delivery to the base station may be continuous, event-related, directed to an inquiry, or a mixture between them. The LEACH protocol is more appropriate with continuous delivery only.
- Different sizes for each cluster: The randomness of choosing the cluster causes the existence of large-numbered clusters and other small-number without specific study due to randomness only.
Several routing protocols have been proposed to solve some of these problems faced by the LEACH protocol, the most prominent of which will be presented in section Five.
5. Different Routing Protocols Based On (LEACH) Protocol
5.1. Low Energy Adaptive Clustering Hierarchy Centralized (Leach-C)
LEACH-C is one of the LEACH versions, which is a centralized protocol. It is divided into several rounds as the LEACH protocol and each round into two basic stages. This protocol assumes that each node can communicate directly with the BS and can calculate its energy and current position.
Unlike LEACH, LEACH-C take into consideration the distance from the node to the base station. The base station determines who is the CH in this round based on its energy and the distance between the node and the base station.
Where in the setup stage all nodes send their energy and location to the base station, the station calculates the average value of the energy values, and the node that contains energy higher than the average value is elected as CH for this round. In the Steady stage, the non-head nodes send their information to the head of their cluster, and the head of the cluster, in turn, collects the data and sends it back to the base station [5].
5.2. LEACH-Balanced (LEACH-B)
The LEACH-B protocol overcomes the original LEACH protocol by taking into account the remaining energy of the node and also strives to maintain the optimum number of cluster heads per round of the protocol. The optimum value for the number of cluster heads varies from 3 to 5% based on what was mentioned in [11]. Thus reduce energy consumption, it is a decentralized protocol, LEACH-B has improved energy performance compared to the parent LEACH protocol see Figure 4.

Figure 4: System life of LEACH and LEACH-B [11].
5.3. Fixed Number of Clusters LEACH (LEACH- F)
This protocol is a centralized approach, like the LEACH-C protocol. clusters are set, and rotation is just for the CH inside the same cluster. The steady-state is identical to the original LEACH since the number of clusters has been determined in advance, the energy wanted for re-clustering is saved. It is not elastic in the case of extension, elimination, or death of a sensor node [12].
5.4. Advanced Low Energy Adaptive Clustering Hierarchy) A-LEACH)
As a result of the overload on CH, it is likely to die early before the other nodes, A-LEACH prolongs the duration of stability (the time before the death of the first node). It worth mentioning mention that A-LEACH is a heterogeneous protocol.
Its working principle is as follows: Every sensor knows how to continue each round utilizing the synchronized clock. Let’s assume that the total number of nodes is (n), and (m) is the number of nodes that contain more power than others (also called (CGA) nodes that chosen as gateways or CH), so the number of nodes other than nodes can be found using equation 2, see Fig 5.

A-LEACH is defined as a Distributed Algorithm because the selection of clusters is independent of the base station. CAG nodes can start to transmit data even when all the non-cluster head nodes collapse [12].
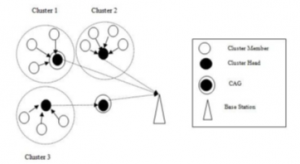
Figure 5: LEACH -A system [1].
5.5. Energy Low Energy Adaptive Clustering Hierarchy (LEACH-E)
E-LEACH is a variant of the LEACH protocol that takes into account the residual energy of a node selected as a cluster head. So the node with the maximum and most appropriate energy is chosen. In other words, E-LEACH is concerned with the number of CHs where the large number of cluster heads consumes higher energy while the small number of cluster heads will cover a greater distance. If the nodes are scattered away from the BS, it will consume more energy. The most appropriate number of cluster heads should be determined, their location and energy. The minimal spanning tree of cluster heads is used in the E-LEACH see Figure 6 [1,2].

Figure 6: LEACH -E system [1].
5.6. Vice Cluster Head LEACH (V- LEACH)
V-LEACH is another version of the LEACH protocol. It is known that the load on the cluster head is greater because it aggregates data from the rest of the nodes and performs simple operations to reduce its size and transfer it to the main station.
If the CH energy is reduced, it will die thus, the whole cluster is useless because it does not communicate its information to the main station. V-LEACH suggested that the presence of a deputy head of the cluster in the event of his death. The vice-CH is responsible for transferring the information to the main station thus, the whole cluster remains connected with the main station, but in case of death of the vice-CH, there is no solution in this protocol see Figure 7 [10].
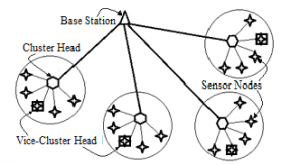
Figure 7: LEACH -V system [13].
5.7. I-LEACH
A new algorithm, I-LEACH, has been proposed, which takes into account the following: the geographic location of the CH, the number of neighbors, and the residual energy to improve network performance and lengthen its life. So the node with the most residual energy and closest to the BS is chosen. This protocol overcame a set of drawbacks of the original LEACH protocol some of them: Different size for each cluster, Unacceptable distribution for cluster heads, and Unacceptable selection of cluster head.
I-LEACH has been evaluated and proven to be effective in average energy consumption, the number of data packets received, and the flexibility to change the location of the BS in the network. Where it reduced energy consumption by approximately 62%, increased the percentage of data packets received by approximately 56%, and increased the life of the network each by 65% at least [14].
I-LEACH, has some of the following assumptions:
- All nodes have the same primary energy, are not rechargeable, and in the same random position when the nodes are thrown from the airplane. They remain in place and never move.
- All nodes have their identifier and can know their exact location and the remaining energy in its battery.
- It is known that each node contains a processing unit and a memory unit, and it can also define the sensed and the aggregated data.
- A node can sense different types of data.
- Each node can communicate directly with the BS and has the power required for this.
5.8. Cell Low Energy Adaptive Clustering Hierarchy (Cell-LEACH)
Cell-LEACH is another version of the LEACH, as in the original LEACH protocol, the entire network is split into groups (clusters). Here too, the network is divided into groups where each group is divided into 7sub-groups called cells. Each group has a cell head whose task is collecting the information from the members of the cell and communicates directly with the head of the cluster. The cell is randomly assigned and then chosen based on its remaining energy to be cell head see Figure 8 [15]. Cell-LEACH has proven its ability to lengthen the network life without reducing efficiency as can be seen in Figure 9.
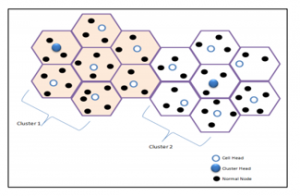
Figure 8: LEACH -Cell system [16]

Figure 9: Average power consumed with network size [15].
5.9. Multi-Hop LEACH
5.9.1. TL-LEACH (Two levels LEACH)
Two levels LEACH) was suggested in [17]. Instead of aggregating and transmitting data in one hop, the data in CH being aggregated at a certain level and transferred to a closer CH level to BS thus, reducing the transmission power, which enhances energy efficiency, and extending the network life. To illustrate the idea further, we have Fig 10 that shows that there are 3 CHs at the top level is closest to BS and also 5 CHs on the second level closest to the normal nodes sensor, and the other 10 SN (Sensor Node) normal nodes at the final level. It has been shown that TL-LEACH increases network life by nearly 30 percent and also increases the percentage of packets received by 20 percent [17].
5.9.2. Multi-Hop LEACH:
Due to the disadvantage in ” LEACH (one-hop routing) to the BS”, and as mentioned earlier, the task of the cluster head is to transfer the collected data from the non-head nodes to the BS. This implies that if the distance is large, then the energy of the cluster head runs out quickly. So a midway cluster head has been considered to reduce distance, thus reducing energy consumption this is known as multi-hop communication [6].

Figure 10: The TL-LEACH network format after the setup phase [17].
The original LEACH protocol does not take into account the primitive energy of the head of the cluster, CH may lose its energy more quickly than others and die, and this cluster loses its connection with the main station. Therefore, it has been proposed to amend the basis of CH selection to take into account energy.
A term was added to the original formula for the original LEACH protocol as in Equation 3 [6].

while p is the possibility of a cluster head (CH), G is a list of nodes that will never be chosen as cluster-head (CH) nodes until the 1 / p level. is the remaining energy level of the node, is the total energy network. This happens in the setup phase.

Fig 11: Freshly revised TDMA description [6].
In several protocols associated with an event, the most appropriate thing to do is to take advantage of the free time of the nodes. For example, when a node does not have information to send to the main station, an allocation technique activates to allocate the time assigned to the free node in the TDMA schedule to another node that has information to send. Thus, reducing energy and time consumption as well, as can be seen in Fig 11 [6].
5.10. Clustering Process Based on Fuzzy Logic
Fuzzy logic simulates human decision-making and experience to judge things and deals with decisions better than probabilistic approaches. Also, it is more suitable for real-time applications [18]. Due to the suspicion and doubt in the WSN environment, some protocols use Fuzzy Logic technology, as it simulates human logic less than others, which include computational complexities and the need for memory. Fuzzy Logic protocols used to choose CH more effectively and flexibly due to its flexibility and error tolerance choose CH more. The Fuzzy Logic model requires four steps to accomplish, namely:
- Fuzzification: In it, the inputs are inserted with clear values and are distorted into a fuzzy group, and this happens in the fuzzifier.
- Rule evaluation (Fuzzy Rule base): This is storing Rule IF-THEN.
- Fuzzy Inference Engine: This engine handles both input and law IF-THEN to produce a fuzzy group.
- Defuzzification: Converts the fuzzy group to clear values.
These steps are shown in Figure 12. Most of the Fuzzification methods use Mamdani’s Method Fuzzy Inference technique to select the CH.
This block is called fuzzy logic controller (FLC). Not too long ago, the authors began leveraging Fuzzy Logic (FL) and incorporating it into WSN to lengthen the life of the network and improve the method for selecting the appropriate CH. Some of the popular Clustering Process Based on Fuzzy Logic will be featured in this section:
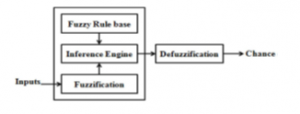
Figure 12: The Fuzzy Inference Process structure diagram.
5.10.1 Cluster Head Election using Fuzzy Logic (CHEF):
In this type, CH is chosen by entering two inputs: power and local distance. (The local distance is the total distance between the temporary CH in that round and the cluster members (normal nodes) within a predetermined fixed competition radius) [19]. So that the likelihood of the closest and more energy nodes to be selected as CH is higher than others, As the experiments of [18] show that CHEF is 22.7% more effective than LEACH.
However, some of the disadvantages of this type are that not all sensor nodes have a GPS device and sometimes are not able to know their geographical location [18]. Besides, this type is not suitable for network sized about 200m × 200m or more [19,20]. clusters closer to BS, run out of energy faster because traffic becomes congested the closer to BS, so an unequal clustering has been suggested to balance energy consumption [19].
5.10.2 Energy Efficient Unequal Clustering (EEUC):
This type divides all nodes into clusters that are not equal in number so that the clusters close to the BS contain fewer nodes. The distant clusters contain a greater number because the closer we get to the base station, the congested the traffic becomes, causing the closest nodes to consume more energy from the farthest [21]. As in the LEACH, the choice of CH is random here is random as well, a random number between 0 and 1 assigned for each node. The number indicates whether the node is going to be a CH or not [19]. Experiments proved that EEUC is more efficient than LEACH see Figure 13.
5.10.3. Energy-Aware Unequal Clustering with Fuzzy (EAUCF):
Battery level goes down to the CH [19]. In other words, when the residual energy of the temporary CH and the distance to the BS is large then the competition radius is large and vice versa [21]. Let us say that each temporary CH will forward its remaining energy and also if it is within the competition radius of this CH, another temporary CH will be compared between their energy, and the least energy will be out of competition and not CH [20]. In the experiments. It has been proven that EAUCF is more efficient than LEACH, CHEF, and EEUC see Figure 13. While this type does not pay attention to the degree of the node, it means the density of the internal cluster, as the density of communication inside the cluster costs energy and reduces the life of the wireless network as a whole [20].
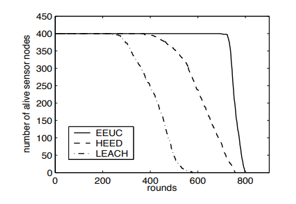
Figure 13: Over time, the number of live sensor nodes [22].
5.10.4. Fuzzy Cluster Head Selection Algorithm based on LEACH:
The authors of [16] noticed that when more than one entry is taken into account to determine one output (appropriate CH selection), Fuzzy Logic, is more accurate and appropriate than others. This type requires three fuzzy input variables. The first variable expresses the number of surviving neighbors, the second variable expresses residual (remaining) energy, the last variable expresses the distance to BS. The one variable of fuzzy output is named a chance [20] as shown in Figure 15. The CH is selected with the most living neighbors, the highest residual energy, and the least distant to BS [20].

Figure 14: Unequal clustering architecture at WSN [22]].
Table 1: At round 250, the total remains energy for each algorithm [19]
| Algorithm | Total Remaining Energy (J) |
| LEACH | 27.14 |
| CHEF | 43.66 |
| EEUC | 44.78 |
| EAUCF | 46.41 |
Just like the LEACH, in each cycle, every node picks a random number between 0 and 1, and if the number was chosen is less than the threshold T, then it becomes within the Concurrent CH. Then each Concurrent CH node calculates its chance from the output of the Fuzzy and shares it with the rest of the Concurrent CH who are within its competition radius. Consequently, each Concurrent node CH has a list of all CH node and its chance, where the highest is elected as CH node, and the rest within the competition radius is a normal node and the elected CH node joins. Also, as usual, the elected CH node is required to create a TDMA schedule and to publish it to the rest of the cluster. The normal nodes send their information to the selected CH node in the time allotted to them and turn off their transmitter device at other times to conserve energy [20]. Compared to LEACH, this form improves network life by 58.38 percent see Table 1.

Figure 15: The Fuzzy-Logic system which controls the clustering
5.10.5. A Fuzzy-Logic based Energy-Efficient Clustering algorithm (FLEEC):
The authors of [21] noticed that when more than one entry is taken into account to determine one output (appropriate CH selection), Fuzzy Logic, is more accurate and appropriate than others. It should be noted that the process of calculating the distance between the node and the BS is done based on the Received Signal Strength (RSS).

Figure 16: The full remaining energy of every cycle [20].
If clusters of the same size are created without taking into account the distance to the BS, then a “hot spot problem” begins to arise. As was evident from Figure 14, it requires more energy for the cluster closer to the BS. To create uneven clusters, the first fuzzy logic controller (FLC) is constructed, which takes two inputs (The distance to the base station and Node Density), and one output (cluster Radius) see Figure 15. Then the head of potential clusters measures the total distance of the neighbors that are in their radius [21]. The total distance to the CH and Residual energy are inputs to the second FLC, and the output is the probability of each node to be CH. The node that has the highest likelihood to become CH is when the node has the largest residual energy and more neighbors.
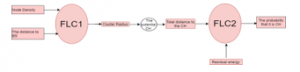
Figure 17: The Fuzzy-Logic system which controls the clustering in (FLEEC)
FLLEC is composed of three major stages [21]:
- Determination of cluster size process: First of all, the BS node broadcasts a welcome message to every node in the region, and then each node would like to calculate its distance from BS via Received Signals Strength (RSS). Each node sends to the BS node an ACK message, which contains its ID, residual energy, geographic distance from the BS node. Then the BS computes the density distribution from the information it obtained from every node. Here comes the role of the first FLC by calculating the corresponding cluster radius for each sensor node, and this information is saved in the memory of each node.
- Determination of likelihood to be a cluster head process: After the cluster radius determined successfully, all nodes would like to broadcast a message of exploring the neighbors around it, and each would like it to receive that message followed an ACK message. After that, the nodes calculate the total distance of their neighbors according to RSS. Here comes the role of the second FLC to calculate the likelihood to be CHs depending on the fuzzy rules reserved in the fuzzy rules base.
- Determination of CH process: Each Node broadcasts the HELLO message to all of its neighbors within the competition radius that it has both CH and its ID. During this information exchange process, the CH that has the greatest probability is the one who becomes CH and the rest is a normal node. CH broadcasts an advertisement message (ADV). If the normal node receives more than the ADV, then it determines the most suitable one that will belong to it, then each node sends a request message to the most appropriate CH.
Comparing FLEEC to LEACH (the main clustering algorithm) and CHEF (the main fuzzy-logic-based algorithm) algorithms. As can be seen from Figure 18, the results showed the superiority of FLEEC over both LEACH and CHEF, especially in the issue of energy consumption.

Figure 18: The energy consumed by the three main algorithms is comparable [21].
6. Conclusion and future work
Due to the emergence of nanotechnology and the persistence of multiple computing fields, the field of WSN and the optimal management of node energy remains a fertile field for research and experiment. This study covered two main topics, presenting and discussing some of the most paramount routing protocols and describing their key types and issues, and going through the most prominent hierarchical protocols and their development process.
We concluded from this research that the clustering design is one of the most energy-saving designs. Where we noticed that Multi-Hop LEACH saves energy because it reduces the distance over the CH and also excels and the fuzzy logic strategy based on clustering is superior to other clustering strategies because it is in line with human logic and its ability to convert more from one input to one output, and as it was presented in the research, it was saving more energy than any other algorithms.
In future work, machine learning with the wireless sensor network can be studied to further rationalize energy consumption and merge data before sending it to BS.
- N. Qubbaj, A.A. Taleb, W. Salameh, “Review on LEACH Protocol,” 2020 11th International Conference on Information and Communication Systems, ICICS 2020, 414–419, 2020, doi:10.1109/ICICS49469.2020.239516.
- K. Sohraby, D. Minoli, T. Znati, Basic Wireless Sensor Technology, 2007, doi:10.1002/9780470112762.ch3.
- P. Kumar, M.P. Singh, U.. Triar, “A review of routing protocols in wireless sensor networks,” 2008 International Conference on Wireless Communications, Networking and Mobile Computing, WiCOM 2008, 1(4), 1–14, 2012, doi:10.1109/WiCom.2008.946.
- A. HNINI, A. EZZATI, M. FIHRI, A. HAJAMI, “Time Slots Investment of a dead node in LEACH protocol on Wireless Sensor Network,” International Journal of Advanced Computer Science and Applications, 4(2), 8–12, 2014, doi:10.14569/specialissue.2014.040202.
- A. Kumar, R.. Saini, E. Brijbhusahn, “Comparison and Review of LEACH ,” (June), 2016.
- C.T. Sony, C.P. Sangeetha, C.D. Suriyakala, “Multi-hop LEACH protocol with modified cluster head selection and TDMA schedule for wireless sensor networks,” in Global Conference on Communication Technologies, GCCT 2015, 2015, doi:10.1109/GCCT.2015.7342720.
- J.S. Leu, T.H. Chiang, M.C. Yu, K.W. Su, “Energy efficient clustering scheme for prolonging the lifetime of wireless sensor network with isolated nodes,” IEEE Communications Letters, 19(2), 259–262, 2015, doi:10.1109/LCOMM.2014.2379715.
- N. Nejah, “Propagation Approach for Clustering in Wireless Sensor Network,” (March), 2018.
- S. Nasr, M. Quwaider, “LEACH Protocol Enhancement for Increasing WSN Lifetime,” 2020 11th International Conference on Information and Communication Systems, ICICS 2020, 102–107, 2020, doi:10.1109/ICICS49469.2020.239542.
- S. Varshney, R. Kumar, “Variants of LEACH Routing Protocol in WSN: A Comparative Analysis,” 199–204, 2018.
- T. Mu, M. Tang, “LEACH-B: An improved LEACH protocol for wireless sensor network,” in 2010 6th International Conference on Wireless Communications, Networking and Mobile Computing, WiCOM 2010, 2010, doi:10.1109/WICOM.2010.5601113.
- H. Dhawan, S. Waraich, “A Comparative Study on LEACH Routing Protocol and its Variants in Wireless Sensor Networks: A Survey,” International Journal of Computer Applications, 117(12), 27–33, 2015, doi:10.5120/20608-3231.
- P. Maurya, A. Kaur, “A Survey on Descendants of LEACH Protocol,” International Journal of Information Engineering and Electronic Business, 8(2), 46–58, 2016, doi:10.5815/ijieeb.2016.02.06.
- Z. Beiranvand, A. Patooghy, M. Fazeli, “I-LEACH: An efficient routing algorithm to improve performance & to reduce energy consumption in wireless sensor networks,” in IKT 2013 – 2013 5th Conference on Information and Knowledge Technology, 2013, doi:10.1109/IKT.2013.6620030.
- A. Yektaparast, F.-H. Nabavi, A. Sarmast, “An improvement on LEACH protocol (EZ-LEACH),” Conference Proceedings of 2015 2nd International Conference on Knowledge-Based Engineering and Innovation, KBEI 2015, 956–960, 2016, doi:10.1109/KBEI.2015.7436173.
- M. Al-Shalabi, M. Anbar, T.C. Wan, A. Khasawneh, “Variants of the low-energy adaptive clustering hierarchy protocol: Survey, issues and challenges,” Electronics (Switzerland), 7(8), 1–28, 2018, doi:10.3390/electronics7080136.
- V. Loscrì, G. Morabito, S. Marano, “A two-levels hierarchy for low-energy adaptive clustering hierarchy (TL-LEACH),” IEEE Vehicular Technology Conference, 3, 1809–1813, 2005, doi:10.1109/VETECF.2005.1558418.
- P. Nayak, A. Devulapalli, “A Fuzzy Logic-Based Clustering Algorithm for WSN to Extend the Network Lifetime,” IEEE Sensors Journal, 2016, doi:10.1109/JSEN.2015.2472970.
- H. Bagci, A. Yazici, “An energy aware fuzzy unequal clustering algorithm for wireless sensor networks,” in 2010 IEEE World Congress on Computational Intelligence, WCCI 2010, 2010, doi:10.1109/FUZZY.2010.5584580.
- W. Abidi, T. Ezzedine, “Fuzzy Cluster Head Election algorithm based on LEACH protocol for wireless sensor networks,” 2017 13th International Wireless Communications and Mobile Computing Conference, IWCMC 2017, 993–997, 2017, doi:10.1109/IWCMC.2017.7986421.
- Q. Wang, D. Lin, P. Yang, Z. Zhang, “A Fuzzy-logic Based Energy-efficient Clustering Algorithm for the Wireless Sensor Networks,” 2018 26th International Conference on Software, Telecommunications and Computer Networks, SoftCOM 2018, 424–428, 2018, doi:10.23919/SOFTCOM.2018.8555848.
- C. Li, M. Ye, G. Chen, J. Wu, “An energy-efficient unequal clustering mechanism for wireless sensor networks,” 2nd IEEE International Conference on Mobile Ad-Hoc and Sensor Systems, MASS 2005, 2005, 597–604, 2005, doi:10.1109/MAHSS.2005.1542849.
