5G, Vehicle to Everything Communication: Opportunities, Constraints and Future Directions
Volume 5, Issue 6, Page No 1089-1095, 2020
Author’s Name: Boughanja Manalea), Tomader Mazri
View Affiliations
Advanced Systems Engineering, Electrical Engineering, Networks and Telecommunications System, Ibn Tofail Science University, Kenitra, 14070, Morocco
a)Author to whom correspondence should be addressed. E-mail: boughnja.manale@gmail.com
Adv. Sci. Technol. Eng. Syst. J. 5(6), 1089-1095 (2020); ![]() DOI: 10.25046/aj0506132
DOI: 10.25046/aj0506132
Keywords: 5G, V2X, Security, Challenges
Export Citations
The 5G, as a new source of telecommunication infrastructure technology, has attracted many stakeholders to promote the progress of its standards and the development of its technology industry. The 5G reinforces new technologies and delivers vehicles for everything services (V2X) to drivers and passengers. It also offers several advantages. On the other hand, due to pervasive network connectivity, there are significant trust, security, and privacy issues for vehicles this affects the overall performance of 5G V2X. This paper provides a comprehensive review; and particularly; an overview of the mobile communication system and introduces the Next Generation (NG). additionally, the paper concentrates on the fifth-generation structure and its use cases. The 5G-V2X as a new field of communication requires more attention and focus, moreover, it aims to present the problems facing this new technology as well, and some future directions for research have been highlighted.
Received: 31 August 2020, Accepted: 14 November 2020, Published Online: 14 December 2020
1. Introduction
Telecommunication changed radically in recent years, from traditional wired telephony oriented services to data-based services, from non-shrewd devices to smart handheld and versatile mobile computers.
Mobile ad hoc networks (MANET) formed a network without infrastructure because the mobile nodes in the network dynamically establish a path to transmit data packets. The strength of this network is its rapid development, robustness, flexibility, and mobility. With the rapid growth of this network and the massive focus on data creation through mobile phones and devices. Previous generations become unable to manipulate this data because they achieve their limits. For this purpose, a fifth-generation has been developed. The appearance of 5G has given several advantages to mobile involvement and some new technologies appear with it [1] to enhance communication between devices:
- Millimeter waves
- Small cells
- Massive multi-input multi-output (MIMO)
- Beamforming
- Full-duplex.
The 5G named also next-generation (NG), is emerging the network. Due to their capacity to handle large and diverse sets of devices, the NG is expected to bring a true wireless worldwide web (WWWW) which will have the ability to support massive data rates and a huge number of user applications and services. Moreover, it will reduce latency and will improve energy efficiency.
The 5G aims to create a networked society, where anyone can view and share information anytime from anywhere [2]. It will bring wireless connectivity for everything that is connected. Due to this fact, 5G faces some issues that can be summarized as follows:
- The number of connected devices has increased considerably;
- Traffic has increased significantly;
- Wide variety of applications with various characteristics and demands.
Our goal is to provide a detailed review where we will show the development brought to 5G and present some use cases and application of 5G, especially we will discuss the relation between 5G and V2X communication and application. This paper is an extension of an original work presented at the international conference of computer science and renewable energies (ICCSRE) [3]. In the previous article, we have shown that with the application of 5G the generation of data will increase. For that, it is essential to implement a dedicated storage method to manage this large quantity of data. In this article, we will focus more on NG itself; explain the difference between 5G and prior generation, and some applications that allow generating this data. For this reason, our paper is organized as follows: In the first section, we will present an overview of the development of mobile networks. Then, we will introduce the 5G new radio access technologies in section two. We will provide some applications for 5G in section four. Further, in section five, we will introduce the 5G V2X application, and we will present the security issues that face the 5G V2X services. To address this security issue, we present some future directions for further studies to promote greater efforts on trust, confidence, assurance, and trustworthiness in 5G V2X services. Finally, we will conclude our paper.
2. Overview
So far, four generations of cellular communication systems have already been adopted [4]. Starting with the 1G that relies on an analog FM cellular system to 4G. With the huge interest in data creation and connected devices, the past generation achieved their limits. To deal with this problem the 5G has been created to solve the problem of the frequency spectrum cutting [5]. The 5G performances will develop later on with the progressive introduction of new technologies: use of millimeter waves, small cell, massive MIMO (or smart micro antennas), beamforming, and full-duplex [6], we will briefly explain those new advances.
- Massive MIMO: the concept was created in [7]. The purpose is to permit the system to achieve higher throughput. The massive MIMO can provide multiple services to various customers simultaneously in all directions.
- Millimetric waves: mobile wireless systems have been always in the band 300MHz – 3GHz. However, the spectrum becomes congested with the huge increase in mobile data traffic and the number of connected devices and the frequency band is coming to an end, creating a signal cutoff [8]. The proposed solution was to use millimeter waves. This latter refers to the wave between 30 and 300 GHz, and their wavelength varies between 1 and 10 mm [9].
- Small cells: are considered to be low-power radio switching equipment controlled by the administrator [10]. We can describe a small cell as a little power base station that will be very nearby to the usual towers and transmit the signal without having any break of connection or attenuation of the signal bypassing all obstacles.
- Beamforming: given the number of antennas used in 5G, the signal will be transmitted from the base station to the devices in an unmonitored manner [11]. This technique permits the orientating of the signal.
- Full duplex (FD): this technique brings to the device the capability to Send and get the data on the identical frequency band. FD improves the efficiency of the network.
The figure 1 summarizes those advances.
3. 5G new radio access technology
5G wireless is conceived to provide a connected environment, where information can be accessed and shared anywhere and anytime, by anyone and deliver a wireless connection for anything. However, with this requirement, the 5G will face several challenges like the volume of traffic the large variety of applications, and so on. To overcome this difficult task, 5G wireless access demands not just new functionality, but also a much more spectrum and larger frequency bands. The millimeter waves provide a huge spectral range, wide transmission bandwidth for the 5G [12]. The figure 2 shows the frequency spectrum.

Figure 1: 5G Advances
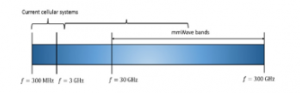
Figure 2: The frequency spectrum of the current and NG communication system
The past generations of cellular mobile systems were operating below 6 GHz frequencies, but with the implementation of the mm waves frequencies, much more spectrum is available and can deal with the huge amount of connected devices With the use of this principle in both 5G and Long Term Evolution (LTE), will have covered to have wireless access [13]. The appearance of 5G did not stop the evolution of LTE. LTE continues its evolution to meet the growing demand for 5G. This evolution is called the LTE evolution [14]. Figure 3 shows the LTE and 5G radio access.
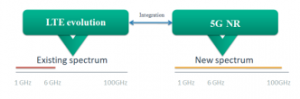
Figure 3: 5G radio access
3.1. Spectrum for 5G
Due to the lack of spectrum in the conventional mobile wireless band regulator started to envisage alternative approaches to manage the spectrum availability. For this reason, one of the major adjustments between the past generation of mobile communication and the fifth generation is the use of a higher frequency spectrum in the millimeter-wave interval [15]. It is about technological evolution and revolution, mixed to the spectrum. This approach is made to make the spectrum more available with a higher frequency to exploit the frequency above 6 GHz and provide more bandwidth for mobile applications. The regulators have taken some measures for the proper functioning of the new generation among them:
- Spectrum sharing: technologies that will allow wireless broadband applications to operate bands assigned to multiple sites.
- Spectral efficiency: to minimize the bandwidth needed to supply a given quality of service level.
- Advanced MIMO: for higher modulation and lower signaling throughput.
- Densification: 5G communication system aims to get mobile customers closer to base stations, particularly by implementing a dense network of small cells.
All these developments reduce the amount of spectrum required for a single user, which indirectly leads to a greater spectrum availability to serve more users with an increased Quality of Services (QoS).
3.2. Use cases for 5G
5G will need to bring solutions for a variety of equipment running within a completely heterogeneous environment. The new human-centric applications include several fields: augmented reality, virtual reality, and gaming. This requires an extremely higher flow rate and reduced delay. In other words, we can differentiate two segments for machine-model communication:
- The Massive Internet of things (MIoT): which is categorized by a large number of low-cost device connections, in this case, a small amount of data supported by each device with extended battery lifetime and a wide range of coverage. This type is used more in the field of intelligent building, transport logistics, and agriculture.
- The critical internet of things (CIoT): shaped with highly dependable, extremely low-latency connectivity. For example, it can support autonomous vehicles, robotic surgery, and road safety.
Unlike previous products, 5G aims to bring improved support for a diversity of distinct services. 5G target three sets of use cases with very unique features:
- Enhanced Mobile Broadband (eMBB): This kind of use case is a direct extension of the conventional mobile broadband connection scenario based on the current mobile telecommunication standards. This set of boxes addresses broadband access everywhere, and in highly inhabited areas. This later provides the user with multiple services such as multimedia and 3D video [16].
- Large scale machine to machine communication (mMTC): with high latency and stability demands. This type of use case mainly relates machine to machine communication (MTC). It enables mobile communication with vehicles, this type requires simultaneous broadband and high mobility capacity. The problem with the mMTC that requires increased reliability and decreased latency [17].
- Ultra-Reliable Low Latency Communication (URLLC): the development of IoT is leading to a multiplication of wireless attached devices carrying TCM network traffic. It is intended that the expected number of these devices will soon surpass. The goal of mMTC is to provide the ability to connect a large set of equipment that may occasionally send a small quantity of data. mMTC devices are categorized by having long battery life and can be deployed remotely [16].
3.3. The key feature of 5G
The 5G was defined by the 3rd generation partnership project (3GPP) as a collection of key functionalities with associated parameters. In addition to the technological and protocolling environment and architecture inherited from the 4G system. We can summarize those technologies as follows:
- 3D MIMO: to ensure high performance in terms of spectral effectiveness. MIMO was firstly implemented in the LTE system was improved than the third generation [18]. The old system was composed of traditional antennas and composed of 8 to 10 elements stacked in a column, but with the evolution, restraint adjustments have been made and provide a downward tilt angle for network convergence. In this situation, the identical radio frequency (RF) pulses are delivered to everyone on the antenna. In such a manner, with the implementation of 3D MIMO, the signal will be simultaneously monitored in both the horizontal and vertical levels.
- Software-Defined Air Interface (IA): the fifth generation intended to handle various use scenarios and a broad range of the spectrum with a signal AI. For this reason, a unified framework was defined to handle different usage scenarios.
- User-Centric Network: to ensure the most suitable operator environment on the entire network, based on user requirements and the network conditions. Therefore, to provide a better user-centric experience the 5G network should handle a user context awareness where the network can serve the user more effectively when there is more information or expertise which means that the more information is loaded onto the network, the better the customer is served. Also, it should have the MEC functionality that includes traffic, security, transport isolation computing, and storage resources. Last and not least it should have a core network perspective to plan the use of the base stations.
- SDN/NFV: This technology enables the management and coordination of various network tranches on a shared physical infrastructure [19].
4. 5G applications
4.1. 5G and Mobile Ad Hoc Network
Mobile Ad Hoc Network (MANET) refers to a signal type of cellular network that contains mobile wireless nodes for communication [20]. These nodes are dynamically organized in random and volatile topologies. The utility to use the 5G for wireless communication in the field of MANET is to give more efficiency to the network. With the implementation of the NG, the MANET network achieves high levels of flexibility and intelligence. Figure 4 illustrates an example of MANET using the 5G connection.

Figure 4: An example of MANET applied in 5G
The NG allows the connection of several devices and provides communication between multiple types of equipment. This communication can be classified into two different parts the device to device communication (D2D) and the vehicle for everything communication (V2X).
D2D communication: also known as proximity service communication (ProSe). The main objective of this functionality is to allow mobile devices to explore the presence of any other close devices within a radius of 500 meters and establish direct communication with it. The basic D2D procedures consist of three main steps:
- Device detection (ProSe discovery): detects if there are other devices nearby.
- Link parameters: establish a link between the associated devices.
- Data communication (ProSe communication): send or receive data via a set of links.
Figure 5 shows the D2D communication.

Figure 5: Basic ProSe procedure
V2X communication: are the exchanges between the vehicle and any device that may impact the vehicle, and the opposite. The X can for instance be on a different vehicle (V), an area of infrastructure (A/I), a pedestrian (P), a domicile (D), or any entity that communicates with the vehicle. We can summarize the cases of use of the vehicle with X as follows:
- Vehicular internet: user experience similar to that provided by their home and network.
- Pre-collision detection and mitigation: detect impending collisions and exchange relevant data from the vehicles involved.
- Cooperative vehicles: V2V and V2I communication to safely operate vehicles such as a train of autonomous cars on a highway.
- V2V information exchange: allows the vehicle to communicate on road to avoid any congestion.
5. 5G and V2X
The 5G mobile communication system will continue to emerge to meet unprecedented requirements beyond the capabilities of the past generations. The NG will not only be used for human interaction but also will be implemented in-vehicle communication. Therefore, the 5G has to support:
- Connection density: to handle million of demands and links across the square kilometer.
- Continuous latency from end to end.
- The density of road traffic volume: several dozens of terabytes created each second per square km.
- Mobility and maximum data rate.
- Network efficiency and high network capacity.
Continuous improvement and the increase in the number of applications have led to the development of new usages, in particular, that of connected objects. Vehicular communications or V2X communications allow vehicles to communicate in real-time with their environment to enhance road control, traffic performance, and energy savings. Figure 6 illustrates the different modes of communication, grouped under the term V2X.
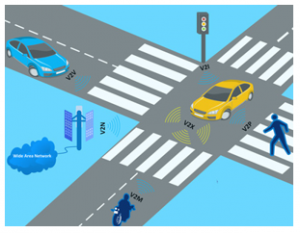
Figure 6: V2X communication modes
Embedded 5G will reform the experience of users in the transport sector (vehicles, subways, planes, trains, etc.), in particular by developing internet connectivity, which will make it possible to create an environment connected to the vehicle. V2X (Vehicle to Everything) communication technology will enable enormous changes the almost instantaneous exchange can be summarized as follows:
- Vehicle-to-vehicle (V2V): that permit inter-vehicle communication.
- Vehicle to infrastructure (V2I): it another type of communication that allows the vehicle to communicate with its surrounding like the communication between the roadside unit and the vehicle.
- Vehicle to pedestrian (V2P); that permits the exchange between the vehicles and the pedestrian into the road.
- Vehicle to motorcycle (V2M): Communication between vehicles and motorcycles to decrease the high rate of collisions and deaths in motorcycle crashes.
The concept of a connected vehicle is based on sensors that operate in line-of-sight such as radars, cameras, or laser remote sensing. The 5G will play a key role in making road transport more efficient and safe. Indeed, the automotive industry will require a more robust, stable, and low-latency network.
5.1. 5G V2X architecture
The structure of the fifth generation and vehicle to everything architecture is based on four network levels:
- 5G Access Network;
- Network Edge;
- 5G Core Network;
- Data Network.
The 5G Access Network is composed of a Next Generation Radio Access Network (NG-RAN) or/and a non 3GPP access network, which interconnects the 5G Core Network and the User Equipment (UE). Figure 6 shows the 5G V2X architecture:

Figure 7: 5G V2X architecture
5.2. Security issues in 5G V2X services: problems and risks
Even though 5G guidelines are as yet being defined it will confront a few difficulties the moment of its implementation. The new radio (NR) will require a steady improvement in security. In this specified situation, portable security and oversaw security services are one of the most escalated areas regarding advancement, to react to the difficulties in the field of digital security inborn to computerized change for the communication service providers and their clients. Moreover, 5G vows to reshape services and advance development by providing an expanded transfer speed, multitenant edge processing, and a few creative services, high-data transmission networks, and high-bandwidth connectivity to machine learning and artificial intelligence (AI). The insurance of services in 5G V2X requires ground-breaking, versatile, and coordinated security. The implementation of 5G V2X brings with it several security threats. The attack on the vehicle can lead to serious problems and can affect all sides of the security requirement
- Attacks on availability: the attacks that focus on the availability of data are the riskiest in V2X communication since they have a real impact on the basic circumstances of well-being. We can find attacks such as the jamming attack which is a radio interference attack that can be carried out across any communication based on wireless technology.
- Attack on data integrity: where the attacker intercepts the data circulated into the network. the attacker can launch attacks such as GPS spoofing or even replay attacks.
- Attack on confidentiality: as an important security requirement in V2X communication and all sent data in the V2X should be secured. An attack such as eavesdropping and location tracking are launched in the network to break through the V2X confidentiality
- Attack on authenticity: Assuring authenticity consists of the process to verify that nodes are granted access to the network according to their identities using certificates and digital signatures. Some threats that infringed this requirement are certificate replication where the nodes use replicated certificates that were added to the blacklist. Moreover, the Sybil attacks where one node (the attacker node) pretends to be many identities in the road network.
- Attack on the non-repudiation: Non-repudiation is concerned with the ID of the effective node that is performing a particular behavior.
The table below shows some attacks that impact the security requirement:
Table 1: Threats of security for 5G V2X
| Security Requirement | Attack | External | Internal |
| availability | Blackhole Grey hole | ü | × |
| Flooding | ü | × | |
| Jamming | × | × | |
| Coalition | ü | × | |
| data integrity | Messages Alteration | ü | × |
| False messages injection | ü | × | |
| Replay | ü | ü | |
| GPS Spoofing | × | × | |
| confidentiality | Eavesdropping | ü | × |
| Location tracking | × | × | |
| authenticity | Certificate replication | ü | ü |
| Sybil | ü | ü | |
| non-repudiation | Masquerading impersonation | ü | ü |
5.3. Security solutions for 5G V2X communication
Vehicular communication experiences numerous difficulties, hence, guaranteeing safe communication is viewed as a complicated process due to the lack of safety features in both empowering innovations of the vehicle to everything interchanges, an additive safety scheme is required to secure vehicle networks. The fields of security for 5G V2X was not deeply discussed. In this section, we will try to gather the mean full strategy that has been implemented to secure the 5G V2X communication. In [21], they proposed a lightweight and protected navigation system for VANET. Each vehicle implements a cryptographic and digital signature to manage the secured correspondence process from the vehicle to the roadside unit (RSU). The system dealt with the replay attack and the man-in-the-middle attack. Another solution was proposed by [22], consisting of a trusted and smart forwarding protocol using double ciphering for data packets and implemented strong verification schemes to gauge the trust of the node. In [23], they proposed a new technique depends on a one-time Identity-Based confirmed asymmetric gathering key consent to make cryptographic blend areas that oppose malicious Eavesdroppers. There are several types of research have proposed potential solutions for 5G from a machine learning (ML) perspective. In [24], the authors suggested a monitoring system employing a Support Vector Machine (SVM) learning algorithm to prevent the replay attack. Also in [25] an anti-jamming methodology for auxiliary users to choose the correspondence channel and mobility. Another researcher [26], based on deciding the arrangements of conceivable interfacing neighboring vehicles, and design the boundaries reserving the joint V2V network. In [27], they have introduced a trusted and standard secure signature solution for collecting plain text for vehicle system applications. The authors in [28], have suggested an algorithm for VANET that delivers authenticate delivered messages. He gave oversight roles to some specified nodes referred to as verification nodes. The authors in [29], suggested a model framework as an IDS based on compartmental attacks. it addressed various attacks in VANET such as the black hole, wormhole, and Sybil attacks.
6. Discussion
This article presents the state of the art on 5G technology applied to transportation to make roads safer. The security of 5G V2X communication presents a great challenge, for this reason, a security layer should be added to strengthen security, and the communication must respect the CIA principle (confidentiality, integrity, and availability):
- Confidentiality concerns the condition under which the vehicle user has the right to know what information is sent by the On-Board Unit (OBU) and for how long this information exists.
- Integrity to verify that all data has been transferred.
- Availability, to ensure that the protocols must remain operational even in the event of a failure, and remains fault-tolerant and stabilize once the failure has been eliminated.
In addition to two other aspects: privacy, this technique implies the preservation of the privacy of the driver and the vehicle. Also, the authentication which consists of ensuring that the intended recipient receives messages from a real sender.
As we have already presented, many applications and solutions have been implemented to ensure the security of 5G V2X communication to preserve and maintain the security of users. We can summarize these in three categories:
- Identity-Based Cryptography (IBC): The concept of IBC is a cryptographic scheme very suitable for devices with limited computing resources. It has been presented in many articles, to encrypt and effectively sign the messages interchanged.
- Behavior-Based: The concept is quite simple this solution is based on the behavior of the attached vehicles communicating in the network and the messages transmitted by the RSU.
- Machine Learning-Based (ML): This provides threat and attack prediction based on suspicious network activities and anomaly detection. The implementation of ML enables automation, adaptability, and enables efficient orchestration and dynamic provisioning for scaled network resources cognition and prediction of mobility
Last and not least the security of such a network can be done depending on four parameters:
- Arrangement: shows if the model is mounted on a flat or cluster network.
- Structure: specifies if the model has used structured, distributed, or hybrid.
- Purpose: specify if the goal of the system is an IDS, the implementation of a safe route, or the protection of the message content.
- Targeted attacks: specifies the attacks handled in the model.
7. Open issues and future orientations
Open issues and future perspectives were highlighted in this section. Securing the 5G V2X is a quite difficult challenge, For this reason, both security solutions and possible cures for identified and unidentified menaces rely on 5G-V2X implementation approaches. We can divide two approaches for 5G V2X. The first one the V2X is implemented with non-autonomous-5G (NA-5G), possible assaults on LTE-V2X are real and can leverage 5G-V2X capabilities. However, with the second implementation Autonomous-5G (A-5G), the attack window diminishes and safeguarding from threats can be augmented. Network deployment plays a critical factor in the 5G-V2X security policy decision. for this purpose, we have encountered the security needs at two levels in the 5G V2X field:
- Secure network caching at the network edge: Storing commonly demanded data in the cache at the edges of storage is an important and effective way to decrease the delay of V2X operations. Yet, it is difficult to maintain the privacy of stored and buffered content, from which opponents can determine which are the relevant services for a given target. To ensure network caching is secure, these key issues need to be resolved: knowing when and where to cache the desired data for a given vehicle, choosing trusted peripheral devices for data storage, and ensuring the confidentiality of buffered data when peripheral nodes are under attack. For this reason, cache placement could be well planned.
- Security-enhanced network slicing: The security and confidentiality of the grid segmentation have not yet gained a lot of attention. Therefore, it is essential to perform both authentication and authorization for a specified part of a network. For this reason, it is crucial to guarantee authentication with low latency to V2X services.
8. Conclusion and perspectives
Five generation and V2X services have expanded tremendously and have benefited our day-to-day lives. While providing a range of advantages to conductors and passengers on the road, 5G V2X’s connectivity has as well raised several concerns about security, trust, and privacy. In this article, we have presented the fifth generation and its characteristics. Besides, we have identified the key challenges that face this new generation. We also briefly outlined the main issues in securing the 5G V2X by determining its issues of reliability, safety, and privacy. Finally, we brought some open issues and future orientations in this field. This latter should have more attention in the future our perspective is to build a system that will be able of securing the communication between the vehicle and everything basing on the 5G connection.
- V. Jungnickel, K. Manolakis, W. Zirwas, B. Panzner, V. Braun, M. Lossow, M. Sternad, R. Apelfröjd, T. Svensson, “The role of small cells, coordinated multipoint, and massive MIMO in 5G,” IEEE Communications Magazine, 52(5), 44–51, 2014, doi:10.1109/MCOM.2014.6815892.
- E. Dahlman, G. Mildh, S. Parkvall, J. Peisa, J. Sachs, Y. Selén, “5G radio access,” Ericsson Review (English Edition), 91(1), 42–47, 2014.
- B. Manale, M. Tomader, “A survey of different storage methods for NGN mobile networks,” in Proceedings of 2019 International Conference of Computer Science and Renewable Energies, ICCSRE 2019, 2019, doi:10.1109/ICCSRE.2019.8807526.
- M. Iwamura, “NGMN view on 5G architecture,” IEEE Vehicular Technology Conference, 2015, 2015, doi:10.1109/VTCSpring.2015.7145953.
- T.L. Marzetta, “Noncooperative cellular wireless with unlimited numbers of base station antennas,” IEEE Transactions on Wireless Communications, 9(11), 3590–3600, 2010, doi:10.1109/TWC.2010.092810.091092.
- A. Gupta, R.K. Jha, “A Survey of 5G Network: Architecture and Emerging Technologies,” IEEE Access, 3, 1206–1232, 2015, doi:10.1109/ACCESS.2015.2461602.
- S. SEN, J. CLARK, J. TAPIADOR, Security Threats in Mobile Ad Hoc Networks, 2010, doi:10.1201/ebk1439819197-9.
- M.Á. Vázquez, L. Blanco, A. Pérez-Neira, “Sparse beamforming for mmWave spectrum sharing systems,” European Signal Processing Conference, 2018-Septe(1), 1517–1521, 2018, doi:10.23919/EUSIPCO.2018.8553148.
- E. Al Abbas, A.T. Mobashsher, A. Abbosh, “Polarization reconfigurable antenna for 5G cellular networks operating at millimeter waves,” Asia-Pacific Microwave Conference Proceedings, APMC, 772–774, 2017, doi:10.1109/APMC.2017.8251562.
- M. Tayyab, X. Gelabert, R. Jantti, “A simulation study on handover in LTE ultra-small cell deployment: A 5G challenge,” IEEE 5G World Forum, 5GWF 2019 – Conference Proceedings, 388–392, 2019, doi:10.1109/5GWF.2019.8911616.
- T. Varum, A. Ramos, J.N. Matos, “Planar microstrip series-fed array for 5G applications with beamforming capabilities,” 2018 IEEE MTT-S International Microwave Workshop Series on 5G Hardware and System Technologies, IMWS-5G 2018, 2018, doi:10.1109/IMWS-5G.2018.8484697.
- E. Dahlman, S. Parkvall, “NR – The new 5G radio-access technology,” IEEE Vehicular Technology Conference, 2018-June, 1–6, 2018, doi:10.1109/VTCSpring.2018.8417851.
- X. Lin, A. Grovlen, K. Werner, J. Li, R. Baldemair, J.F.T. Cheng, S. Parkvall, D.C. Larsson, H. Koorapaty, M. Frenne, S. Falahati, “5G New Radio: Unveiling the Essentials of the Next Generation Wireless Access Technology,” IEEE Communications Standards Magazine, 3(3), 30–37, 2019, doi:10.1109/MCOMSTD.001.1800036.
- O. Teyeb, G. Wikström, M. Stattin, T. Cheng, S. Faxér, H. Do, “Evolving LTE to Fit the 5G Future,” Ericsson Technology Review, 1–17, 2017.
- S. Parkvall, E. Dahlman, A. Furuskär, M. Frenne, “WIRELESS AND RADIO COMMUNICATION NR: The New 5G Radio Access Technology,” IEEE Communications Standards Magazine, 1(December), 24–30, 2017, doi:10.1109/MCOMSTD.2017.1700042.
- M.A. Abu-Rgheff, 5G Physical Layer Technologies, 2019, doi:10.1002/9781119525547.
- B. Badic, C. Drewes, I. Karls, M. Mueck, Rolling out 5G: Use cases, applications, and technology solutions, 2016, doi:10.1007/978-1-4842-1506-7.
- G. Liu, Y. Huang, F. Wang, J. Liu, Q. Wang, “5G features from operation perspective and fundamental performance validation by field trial,” China Communications, 15(11), 51–61, 2018, doi:10.1109/CC.2018.8543047.
- J. Ordonez-Lucena, P. Ameigeiras, Di. Lopez, J.J. Ramos-Munoz, J. Lorca, J. Folgueira, “Network Slicing for 5G with SDN/NFV: Concepts, Architectures, and Challenges,” IEEE Communications Magazine, 55(5), 80–87, 2017, doi:10.1109/MCOM.2017.1600935.
- R. Bruzgiene, L. Narbutaite, T. Adomkus, “MANET Network in Internet of Things System,” Ad Hoc Networks, (May 2017), 2017, doi:10.5772/66408.
- G. Li, M. Ma, C. Liu, Y. Shu, “A lightweight secure VANET-based navigation system,” 2015 IEEE Global Communications Conference, GLOBECOM 2015, 2015, doi:10.1109/GLOCOM.2014.7417462.
- S.K. Bhoi, P.M. Khilar, “A Road Selection Based Routing Protocol for Vehicular Ad Hoc Network,” Wireless Personal Communications, 83(4), 2463–2483, 2015, doi:10.1007/s11277-015-2540-x.
- L. Zhang, “OTIBAAGKA: A New Security Tool for Cryptographic Mix-Zone Establishment in Vehicular Ad Hoc Networks,” IEEE Transactions on Information Forensics and Security, 12(12), 2998–3010, 2017, doi:10.1109/TIFS.2017.2730479.
- Q.G. Fan, L. Wang, Y.N. Cai, Y.Q. Li, J. Chen, “VANET Routing Replay Attack Detection Research Based on SVM,” MATEC Web of Conferences, 63, 4–7, 2016, doi:10.1051/matecconf/20166305020.
- G. Han, L. Xiao, H.V. Poor, “Two-dimensional anti-jamming communication based on deep reinforcement learning,” ICASSP, IEEE International Conference on Acoustics, Speech and Signal Processing – Proceedings, 2087–2091, 2017, doi:10.1109/ICASSP.2017.7952524.
- L.T. Tan, R.Q. Hu, “Mobility-aware edge caching and computing in vehicle networks: A deep reinforcement learning,” IEEE Transactions on Vehicular Technology, 67(11), 10190–10203, 2018, doi:10.1109/TVT.2018.2867191.
- M.S.I. Mamun, A. Miyaji, H. Takada, “A multi-purpose group signature for vehicular network security,” Proceedings – 2014 International Conference on Network-Based Information Systems, NBiS 2014, 511–516, 2014, doi:10.1109/NBiS.2014.93.
- U. Khan, S. Agrawal, S. Silakari, “Detection of Malicious Nodes (DMN) in vehicular ad-hoc networks,” Procedia Computer Science, 46(Icict 2014), 965–972, 2015, doi:10.1016/j.procs.2015.01.006.
- H. Sedjelmaci, S.M. Senouci, “An accurate and efficient collaborative intrusion detection framework to secure vehicular networks,” Computers and Electrical Engineering, 43, 33–47, 2015, doi:10.1016/j.compeleceng.2015.02.018.
