Mobile Money Wallet Attack Resistance using ID-based Signcryption Cryptosystem with Equality Test
Volume 5, Issue 6, Page No 988-994, 2020
Author’s Name: Seth Alornyo1,a), Mustapha Adamu Mohammed1,2, Francis Botchey1,3, Collinson Colin M. Agbesi1
View Affiliations
1Koforidua Technical University, Computer Science Department, KTU, Koforidua, Ghana
2Kwame Nkrumah University of Science and Technology, Computer Science Department, KNUST, Kumasi, Ghana
3University of Electronic Science and Technology of China, School of Information and Software Engineering, UESTC, Chengdu, China
a)Author to whom correspondence should be addressed. E-mail: sabigseth@ktu.edu.gh
Adv. Sci. Technol. Eng. Syst. J. 5(6), 988-994 (2020); ![]() DOI: 10.25046/aj0506118
DOI: 10.25046/aj0506118
Keywords: ID-based encryption, Signcryption, Equality test
Export Citations
This paper is an extension of a research work presented at ICSIoT 2019. An attack continuum against the insider attack in mobile money security in Ghana using a witness based crypto- graphic method proposed by Alornyo et al. resisted the service provider from peddling with users data for economic gains. Our improved scheme achieves a simultaneous benefit of digital signature in public key encryption (PKE). The adoption of signcryption cryptosystem in our scheme achieved a desired security property of EUF-CMA using the random oracle model.
Received: 18 September 2020, Accepted: 17 November 2020, Published Online: 08 December 2020
1. Introduction
Ghana and other African countries have seen a tremendous growth in mobile money service patronage in recent times. The use of the mobile money services platform requires the use of a less-resource constraint mobile devices that do not require access to internet or mobile app for mobile payment. Thus, any mobile device that does not have access to internet but can access the mobile money service provider cellualr network can perform financial transactions and other utility payments. This and many other reasons has lead to the high patronage of mobile money services in Ghana. However, the mobile money system is not immune to data forgery and re-play attacks. The system model of our scheme is depicted in 1
Our research work is an extension of a publication presented at ICSIoT 2019. The construction presented at ICSIoT 2019 [1] considered the service provider as the adversary who could launch the insider attack. The service provider had access to users token information and transaction details and was possible for the service provider to peddle with users data via the following:
The mechant receives valid transaction details such as trans- action ID, tdID and finds out the content M1 as well as the token information tdID from the transaction details TS D.
- The adversary (insider) attains the ciphertext CT1 of a guessed
message Mj and token tdkID.
• in deriving the token information from the transaction details. How- ever, the scheme utilized the witness based cryptographic primitive with an added pairing operation to resist the insider attack contin- uum.The adversary checks if the test Test(CT1, TS D, tdj ) = 1 In the above scenario, the insider wins the game if it succeeds
In spite of their construction, there were a possible attack during data transmission such as forgery and re-play attacks in mobile money payment systems. To solve the problem, we propose a scheme using a signcryption cryptographic primitive to achieve the simultanoeus benefit of digital signature and PKE in mobile money systems deployed in Ghana (West Africa). This approach resist data forgery and re-play attacks.
The first generic construction of identity-based signcryption was unveiled [2]. Their work fulfilled a dual function of digital signature and public key cryptosystem (PKE). Other traditional approaches that employed signature-then-encrypt had a high cost computations as compared to [2]. However, the scheme [2] adopted data encapsulation method instead of key encapsulation method [3]–[6] to achieve confidentiality and unforgeability instantiation in the standard model.
Signcryption scheme unveiled in [7] did not propose a security proof even though their construction were based on discrete logarithm assumptions. In view of this, several research in signcryp- tion and signature schemes have been unveiled [8]–[15] with other functional extensions [16]–[19]. In 2011, a survey of identity-based signcryption cryptosystem was examined by Li et al.[20] to examine the security models as well as a comparative study of their security properties and efficiency. Analysis of other flavours of signcryption constructions [4], [11]–[13], [21]–[24], threshold signcryption [25]–
[30], proxy signcryptions [31]–[37] and ring signcryption [38]–[42] have been proposed and constructed. Subsequently, Xiong et al.
[43] did a cryptanalysis on the scheme [21]. The security notion of CPA in their work was diffused by Xiong et al. [43]. Hence, [43] showed that their scheme did not achieve chosen plaintext attack (CPA) security as they claimed.
Due to the need to resist the cloud server from peddling users outsourced data, efficient signcryption cryptosystem was unveiled in [44]. According to him, some existing signcryption schemes in [45]–[55] had certain lapses such as lack of data integrity, authenti- cation and non-repudiation. Hence the need to construct a scheme to deny the insider adversary in the cloud from data peddling and modification for economic gains became paramount. Furthermore, the emergence of distributed computing and interconnected systems propelled [56] to unveiled a signcryption scheme in heterogeneous systems. Although in [57], the author earlier discussed the above problem, they could not construct a scheme to solve the problem of signcryption in heterogeneous systems. However, the constructions in [57, 58] and [59] achieved insider and outsider attack resistant respectively.
Recently, secure identity-based cryptosystem has been unveiled in [60]. Their security improvement was based on certain proposed signcryption algorithms [11]–[14], [61] constructed using the ran- dom oracle, and as well as schemes designed using the standard model [21, 23, 24, 62] with certain deficiencies such as IND-CCA2 and existential unforgeable chosen message attack (EUF-CMA). However, an attack was launched in [63] to unveil a new functional secure identity-based signcryption cryptosystem in [60]. A scheme to curtail an attack continuum in mobile money wallet system in Ghana to prevent message forgeability and re-play attack is still an open problem.
1.2 Paper Organization
The rest of this work is organized as follows; In Section 2, our scheme outlines preliminaries for the construction and formulate the definitions of MWAR-ID-SET. In Section 3, the definitions of our scheme are outlined, section 4 outlines the security model of MWAR-ID-SET. Section 5 details the construction of our scheme, and proof the security in Section 6. Section 7 compares our work with existing schemes. Section 8 concludes our work.
2. Preliminaries
Definition 1: Bilinear Map. Let G and GT be two multiplicative cyclic groups of prime order p. Suppose that q is agenerator of G. A bilinear map e : G × G → GT satisfies the following properties:
- Bilinearity: For any g ∈ G, and b ∈ Zp, e(ga, gb) = e(g, g)ab .
2. Non-degenerate: e : (g, g) ≠ 1.
- Computable: There is an efficient algorithm to compute e(g, g) for any g ∈ G.
Definition 2: Bilinear Diffie-Hellman (BDH) problem. Let
G and GT be two groups of prime order q. Let e : G G GT
be an admissible bilinear map and let q be a generator of G. The BDH problem in (q, G, GT , e) is as follows: Given (q, qa, qb, qc), for random c, d, f ∈ Z∗p, for any randomized algorithm. A computes the value e(q, q)cd f GT with advantage:
We say that the BDH assumption holds if for any polynomial- time algorithm A, its advantage ADVBDH is negligible.
Private key generator (PKG)
Cellular network provider
By considering that the integrity, authentication and non-repudiation of the data in mobile money wallet system in Ghana, we proposed the mobile money wallet attack resistant scheme using the ID-based
Mobile money subscriber
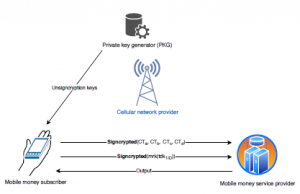
Figure 1: System model of our scheme Mobile money service provider
signcryption cryptographic primitive with equality test (known as MWAR-ID-SET) to achieve a simultaneous benefit of digital signa- ture with public key encryption, and with equality test. Concretely, the formal definition, security model and concrete construction of MWAR-ID-SET are proposed in this paper. Further, our proposed scheme was shown to achieve the security property of existential un- forgeable chosen message attack (EUF- CMA) by using the formal security proof.
3. Definitions
In this section, the formal definition of our proposed scheme is outlined. MWAR-ID-SET achieves a formal security property of EUF-CMA. The construction specifies six(6) steps: S etup, MW Extract, TokenGen, MW S igncrypt, MW Unsigncrypt, MW Test. MT and CT are considered as the plaintext space and ciphertext space respectively.
1. S etup: The construction on input a security parameter k, output public parameter K with MS K as master secret key.
- MW Extract: The scheme on input MS K, ID 0, 1 arbi- trary and gives out a message recovery key mrk corresponding to an
3. TokenGen: With the input message recovery key mrk, arbi- trary ID 0, 1 ∗ and it return token tdk1 corresponding to an identity (ID1).
- MW − S igncrypt: The scheme on input ID ∈ {0, 1}∗, random witness w ∈ W, a chosen plaintext m1 ∈ M1, and output ci- phertext CT1 = (x1, c1) where x ∈ X from generated witness
the challenger randomly chooses t 0, 1 and returns CT1 = MW S igncrypt(mt, ID∗, w∗). Again, a challenge ciphertext token mrk∗ = (ID∗, x∗) is issued by the execution of TokenGen phase mrk∗ mrk(tdk, mt, x∗) and it output mrk∗ to A.
4. MW Unsigncrypt: The merchant executes an unsigncryp- tion algorithm to unsigncrypt CT1. The merchant obtains mrk1 which corresponds to a public key of IDi. The plaintext mi is forwarded to A.
- Phase 2: The merchant adversary issue the query (z1, z2, …, zn). The query is of the form:
• MW − Query. A similar response as in phase 1 is given
WInsGen(w) = x with the relation R satisfied [1]. because IDi ≠ ID∗.
5. MW Unsigncrypt: On input the ciphertext CT1, message recovery key mrk with a random chosen witness w W, the plaintext m1 M1 is uncovered provided CT1 is deemed as a valid ciphertext derived from a witness relation R.
- 4. Security ModelMW Test: The scheme on input the ciphertext CTA CT1 with its corresponding receiver IDA derived from the token tdk1A with its corresponding IDA, the ciphertext CTA CT1 with its corresponding receiver IDB derived from the token tdk1 with its corresponding IDB. The scheme respond 1, pro- vided CTA and CTB have same message. Otherwise it respond as ⊥.
We assume = S etup, MW Extract, TokenGen, MW
S igncrypt, MW Unsigncrypt, MW Test as the scheme and poly- nomial time algorithm adversary A. MWAR ID S ET achieves two main security notion of IND CCA2 and EUF CMA. How- ever, our scheme adds the security notion of ID-based indistinquisha- bility to IND-CCA2 and is coined as IND-ID-CCA2, similarly pre- sented in [55] via the standard model..
- S etup: The challenger A executes the security parameter k and outdoors K with a randomly chosen witness w W and generates x X of the relation R. It gives out the relation R to the adversary A.
2. Phase 1: The mobile merchant adversary A then issues (z , z , …, z ). It is assumed that such query is of:
TokenGen(ID1). Given x ≠ x∗, the merchant respond same as in phase 1.
6. Result. The adversary A does a guess vj of v. Since vj = v, then the adversary will win the game.
The adversary advantage in breaking the scheme is noted as:
ADVMWAR−ID−S ET (k) = Pr[vj = v] 1 as a negligible proba- bility.
5. Construction
A detailed construction of our proposed scheme is outlined as fol- lows:
- On input a secured parameter k, the algorithm output public parameter K, with MS K as master secret
Two multiplicative group G and GT are generated by the system with the same order of lemgth θ bits with a bilinear map e : G × G → GT . The group generater
P ∈ G is selected.
• The algorithm exploits keyed permutation F : {0, 1}s ×
{0, 1}n → Z∗p with a positive interger D = k(i) and
L = b(i), it then activate a random value r1 from 0, 1 L. Message authentication code (MAC), MAC = GS V. Thus, generate, sign, verify (GSV). After executing G(i), it obtains r2. It then set master token key as MTK1 = (r1, r2).
- A hash functions Ha : {0, 1}τ → Z∗p, Hb : {0, 1}∗ → G,
Hc : A×G ×GT → {0, 1}τ+r1 , where r1 represent random
MW Query(IDi): The merchant executes H(.) and gen- erates mrki which corresponding to IDi as the identity. The recovered mrki is forwarded to A.
TokenGen(IDi): The merchant executes the MW
Unsigncryption to generates tdki via the witness rela- tion R. The algorthm then forwards tdki to A. numbers and τ as length of message. (τ1, τ2) Z2 is ran- domly chosen and Rv = Pτ1 , Rm = Pτ2 . The paramrter K = (A, τ, G, GT , P, Rv, Rm, MAC, Ha, Hb, Hc) is made public (published)3. MW Challenge: When the phase comes to an end, two messages (m1, m2) with equal-length and ID∗ is submitted by A to the challenger and wishes to be challenged. But (m1, m2) were both not issued during signcryption and ID∗ was never extracted during phase 1 section. Given this,
- MW Extract: With an ID 0, 1 as string, the system com- putes QID = Hb(ID) G and private key mrkID = (Qτ1 , Qτ2 ). It should therefore be noted that (τ1, τ2) are secret value ran- domly chosen by the
- CTc = Pq2 CTd = (m1||w) ⊕ Hb(CTa||CTb||Z||e(QID, Rv)q2 ).TokenGen: The algorithm with an input string ID ∈ {0, 1}∗, the computation QID = Hb(ID) ∈ G is executed and the token
- CTa = Hb(e(QID, Rm)q1 ) · mq1 , CTb = Pq1MW S igncrypt: The algorithm with an input public pa- rameter K, string ID, it executes QID = Hb(ID) G and a signcryption m1 G is triggered by choosing two random values (q1, q2) Z∗p. The ciphertext is set as CT1 = (CTa, CTb, CTc, CTd) as :
The signature Z S (r2, CTc) is used to signcrypt the cipher- text of the employed MAC. The signcrypted tag Z is used to verify signcrypted ciphertext CTc
- 6. Security AnalysisMW Unsigncrypt: To unsigncrypt, the algorithm with an input the ciphertext CT1, private unsigncryption key mrk = (Qτ1 , Qτ2 ) with CT1 = (CTa, CTb, CTc, CTd) corre-
In this section, we consider a formal security property of IND-CCA2 and EUF-CMA [60]. Our scheme adds the notion of ID-based in- distinquishability to IND-CCA2 and referred to as IND-ID-CCA2.
- IND-CCA2 Security
sponding to an identity ID. The algorithm executes (m1||w ) = qks +qus +3 qnsCTb ⊕ Hb(CTa||CTb||CTc||e(CTc, Qτ1 )). The algorithm do aOur MWAR-ID-SET is (S ETε, ts, qks, qns, qus)-IND-CCA2 secure if (εmdbdh, ts) mDBHDH assumption holds. Thus, H1 and H2 serves as (εH1 ) and (εh2 ) are both collision resistant hash functions,
check of CTa = (mj )||xj and CTb = P 1 to determine whether
εS ET ≤ εmdbdh + εH1 + εH2 +
p + p2 .
they are equal. If they are equal, the algorithm returns m1, contrarily, it returns ⊥.
- MW Test: With a given signcrypted ciphertext CT1A with trapdoor tdk1A and a different signcrypted ciphertext CT1B with a trapdoor tdk1B . The algorithm determines whether m1A = m1B is equal or not. The algorithm does this by execut- ing:
Where ts refers to index period time, qks refers to number of extraction key queries, qns represent number of signcryption queries and qus represents number of unsigncryption queries. Therefore, the security analysis with a collission resistant hash function proves our scheme secured.
6.2 EUF-CMA Unforgeability
TDA = CTaA
Hb(e(CTaA , RmA ))
, TDB = CTaB .
Hb(e(CTaB , RmB ))
Proof Theorem: This section outlines the security proof of un- forgeability against adaptive CMA derived from the security con-
If the above equation holds, the algorithm then output 1 on success and 0 on failure.
Construction Correctness.
We assume that CT1 = (CTa, CTb, CTc, CTd).). Test algorithm executes:
structions in Chow[41] ID-based signcryption cryptosystem. Thus, it is expected that the adversary can forge a ciphertextof a mes- sage m1, if the assumption CT1 = (CTa, CTb, CTc, CTd) corre- sponding to a user identity ID holds. Thus, CTd = (m1 w) H3(CTa CTb CTc e(QID, Rv))q2 is regarded as the signature of the message m1 w, where e(QID, Rv)q2 is regarded as the pairing of a corresponding user with secret signcryption key Rv. It is however noted that the difficulty of CDH problem makes the scheme unforgeable via the random oracle model.
Further details on the token security analysis can be accessed in [1].Security Analysis of Token Key
Hence, mq1 = mq1
The token security analysis experiment to our scheme is defined as:
From the above, the algorithm output 1 on success and 0 on failure.
Therefore:
e(CTbA , RmB ) = e(CTbA , RmB ).
e(CTb , Rm ) = (Pq1 , Pτ2 ) = e(P, P)q1 τ2 ,
With a security parameter k, a master token key MTK1 = (r1, r2) and A adversary against token security. According to [1], the adver- sary A win the game if bj = b, which shows that the output of the experiment is 1 on success and 0 on failure. Adversary A advantage in the experiment is defined as:
However, the probability for the adversary to win the game is negligible, hence proves our construction secured.
7. Comparison
A security strength comparison computations with existing sign- cryption schemes are outlined in Table 1. Constructions in ID- based Signcryption cryptosystem in [21, 23, 60, 64] are compared to with respect to security strength. The parameters for our compar- ison includes group multiplication, group exponentiation, inverse computations, pairing operation, test for equality, and support for EUF-CMA.
Table 1: The performance computational cost and Communication overheads
|
Legend: jjGMult”: multiplication in group G, jjGjEjxpa : exponentiation in group G, jjGTjjExpa : exponentiation in group GT , GTInv : inverse computation in group GT , jjnm, njj: length of identity in bits string, jjPr”: pairing operations in the form x(+y) as in [23], jj ET jj: equality test, jj jj: not supportive, jj jj: supportive .
Table 2: Running Times with Symbols
| Symbols | Description | Times |
| GExpa | G exponentiation operation | 6.3937 |
| GTExpa | GT exponentiation operation | 1.9518 |
| Tpa | Operation with pairing | 11.4173 |
| Tha | Hash functions | 000853 |
| GMult | Multiplication operation in G | 0.047 |
| GTMulta | Multiplication operation in GT | 0.0119 |
The Pairing-Based Cryptography (PBC) Library [65] is used to quantify the time consumption of signcryption, unsigncryption and test operations. We use the code of a program in VC++ 6.0 and executed on a computer (Windows 10 Pro, operating system), Capacity of Intel(R) Core (TM) i5-4460 CPU with 3.20GHZ and 4Gb RAM. The code was executed several times and average time of execution extracted (see Table 2 ). With respect to the scheme in [66], and other pairing-based constructions with a security level of 1024-bit RSA, a supersingular curve z2 = x3 + x with an em- bedded degree of 2 is adopted. Also, q = 2159 + 217 + 1 noted as a 160 bit Solinas prime noted as a 512 bit prime. With regards to ECC-based schemes, an equivalent security level of Koblitz elliptic curve of y = x3 + ax2 + b defined on a F2163 is used to provide the same security level in the ECC group. The computational units are in millisecond (ms) and bytes respectively. The execution times of each respective algorithm were calculated and Matlab program was used to generate Table 1 and computational results in Table 2.
Therefore, it is clear that our scheme support equality test as compared with other schemes without equality test. The compu- tation of trapdoor and trapdoor delegation to the tester is equally achieved in our scheme. In terms of computational cost, our scheme has a lower computation cost as compared to existing schemes. Also, the support for IND-ID-CCA2 is featured in our sccheme as
compared to other existing scheme with IND-CCA support. How- ever, the inverse compuatation to recover the message achieves a ligh computational cost as compared to others in Table 1. This is pardonable due to the additional trapdoor computations featured in our scheme.
8 Conclusion
|
The construction MWAR ID S ET achieves a security improve- ment in mobile money service security in Ghana via the adoption signcryption cryptosystem. Data forgery and re-play attack is cur- tailed in our construction and the simultaneous benefit of PKE and digital signature is achieved in our scheme using the random oracle model. A desirable security property of EUF-CMA is achieved in our construction. In spite of other applications and extentions of identity based cryptosystem [67]–[70], our scheme achieves a remarkable achievement in indentity based cryptosystem.
Conflict of Interest The authors declare no conflict of interest.
Acknowledgment We will like to use this opportunity to thank the anonymous reviewers for their kind support and consideration.
- S. Alornyo, K. K. Mireku, A. Tonny-Hagan, X. Hu, “Mobile Money Wallet Security against Insider Attack Using ID-Based Cryptographic Primitive with Equality Test,” in 2019 International Conference on Cyber Security and Internet of Things (ICSIoT), 82–87, IEEE, 2019, doi:10.1109/ICSIoT47925.2019. 00021.
- F. Li, H. Xiong, Y. Liao, “A generic construction of identity-based signcryption,” in 2009 International Conference on Communications, Circuits and Systems, 291–295, IEEE, 2009, doi:10.1109/ICCCAS.2009.5250509.
- K. Bentahar, P. Farshim, J. Malone-Lee, N. P. Smart, “Generic constructions of identity-based and certificateless KEMs,” Journal of Cryptology, 21(2), 178–199, 2008, doi:10.1007/s00145-007-9000-z.
- L. Chen, Z. Cheng, J. Malone-Lee, N. P. Smart, “An Efficient ID-KEM Based On The Sakai-Kasahara Key Construction.” IACR Cryptol. ePrint Arch., 2005, 224, 2005.
- E. Kiltz, D. Galindo, “Direct chosen-ciphertext secure identity-based key encapsulation without random oracles,” in Australasian Conference on Information Security and Privacy, 336–347, Springer, 2006, doi:https://doi.org/10.1007/ 11780656 28.
- A. Shamir, “Identity-based cryptosystems and signature schemes,” in Workshop on the theory and application of cryptographic techniques, 47–53, Springer, 1984, doi:https://doi.org/10.1007/3-540-39568-7 5.
- Y. Zheng, “Digital signcryption or how to achieve cost (signature or encryption) cost (signature)+ cost (encryption),” in Annual international cryptology confer- ence, 165–179, Springer, 1997, doi:https://doi.org/10.1007/BFb0052234.
- A. Fiat, A. Shamir, “How to prove yourself: Practical solutions to identification and signature problems,” in Conference on the theory and application of cryptographic techniques, 186–194, Springer, 1986, doi:https://doi.org/10.1007/3-540-47721-7 12.
- L. C. Guillou, J.-J. Quisquater, “A “paradoxical” indentity-based signature scheme resulting from zero-knowledge,” in Conference on the Theory and Application of Cryptography, 216–231, Springer, 1988, doi:https://doi.org/10. 1007/0-387-34799-2 16.
- J. Malone-Lee, “Identity-Based Signcryption.” IACR Cryptol. ePrint Arch., 2002, 98, 2002.
- P. S. Barreto, B. Libert, N. McCullagh, J.-J. Quisquater, “Efficient and provably- secure identity-based signatures and signcryption from bilinear maps,” in International conference on the theory and application of cryptology and information security, 515–532, Springer, 2005, doi:https://doi.org/10.1007/11593447 28.
- X. Boyen, “Multipurpose identity-based signcryption,” in Annual International Cryptology Conference, 383–399, Springer, 2003, doi:https://doi.org/10.1007/ 978-3-540-45146-4 23.
- S. S. Chow, S.-M. Yiu, L. C. Hui, K. Chow, “Efficient forward and provably secure ID-based signcryption scheme with public verifiability and public ciphertext authenticity,” in International Conference on Information Secu- rity and Cryptology, 352–369, Springer, 2003, doi:https://doi.org/10.1007/ 978-3-540-24691-6 26.
- B. Libert, J.-J. Quisquater, “A new identity based signcryption scheme from pairings,” in Proceedings 2003 IEEE Information Theory Workshop (Cat. No. 03EX674), 155–158, IEEE, 2003, doi:10.1109/ITW.2003.1216718.
- T. H. Yuen, V. K. Wei, “Constant-Size Hierarchical Identity-Based Signature/Signcryption without Random Oracles.” IACR Cryptol. ePrint Arch., 2005, 412, 2005.
- Y. Zheng, H. Imai, “How to construct efficient signcryption schemes on elliptic curves,” Information processing letters, 68(5), 227–233, 1998, doi: https://doi.org/10.1016/S0020-0190(98)00167-7.
- F. Bao, R. H. Deng, “A signcryption scheme with signature directly verifiable by public key,” in International Workshop on Public Key Cryptography, 55–59, Springer, 1998, doi:https://doi.org/10.1007/BFb0054014.
- J.-B. Shin, K. Lee, K. Shim, “New DSA-verifiable signcryption schemes,” in International Conference on Information Security and Cryptology, 35–47, Springer, 2002, doi:https://doi.org/10.1007/3-540-36552-4 3.
- D. H. Yum, P. J. Lee, “New signcryption schemes based on KCDSA,” in International Conference on Information Security and Cryptology, 305–317, Springer, 2001, doi:https://doi.org/10.1007/3-540-45861-1 23.
- F. Li, M. K. Khan, “A survey of identity-based signcryption,” IETE Technical Review, 28(3), 265–272, 2011, doi:https://doi.org/10.4103/0256-4602.81236.
- Y. Yu, B. Yang, Y. Sun, S.-l. Zhu, “Identity based signcryption scheme with- out random oracles,” Computer Standards & Interfaces, 31(1), 56–62, 2009, doi:https://doi.org/10.1016/j.csi.2007.10.014.
- K. G. Paterson, J. C. Schuldt, “Efficient identity-based signatures secure in the standard model,” in Australasian Conference on Information Security and Privacy, 207–222, Springer, 2006, doi:https://doi.org/10.1007/11780656 18.
- Z. Jin, Q. Wen, H. Du, “An improved semantically-secure identity-based signcryption scheme in the standard model,” Computers & Electrical Engineering, 36(3), 545–552, 2010, doi:https://doi.org/10.1016/j.compeleceng.2009.12.009.
- F. Li, Y. Liao, Z. Qin, “Analysis of an identity-based signcryption scheme in the standard model,” IEICE transactions on fundamentals of electronics, communications and computer sciences, 94(1), 268–269, 2011, doi: https://doi.org/10.1587/transfun.E94.A.268.
- F. Li, J. Gao, Y. Hu, “ID-based threshold unsigncryption scheme from pairings,” in International Conference on Information Security and Cryptology, 242–253, Springer, 2005, doi:https://doi.org/10.1007/11599548 21.
- S. Duan, Z. Cao, R. Lu, “Robust ID-based threshold signcryption scheme from pairings,” in Proceedings of the 3rd international conference on Information security, 33–37, 2004, doi:https://doi.org/10.1145/1046290.1046298.
- C. Peng, X. Li, “An identity-based threshold signcryption scheme with seman- tic security,” in International Conference on Computational and Information Science, 173–179, Springer, 2005, doi:https://doi.org/10.1007/11596981 26.
- F. Li, Y. Yu, “An efficient and provably secure ID-based threshold signcryption scheme,” in 2008 International Conference on Communications, Circuits and Systems, 488–492, IEEE, 2008, doi:10.1109/ICCCAS.2008.4657820.
- S. S. D. Selvi, S. S. Vivek, C. P. Rangan, N. Jain, “Cryptanalysis of Li et al.’s identity-based threshold signcryption scheme,” in 2008 IEEE/IFIP International Conference on Embedded and Ubiquitous Computing, volume 2, 127–132, IEEE, 2008, doi:10.1109/EUC.2008.187.
- F. Li, X. Xin, Y. Hu, “ID-based threshold proxy signcryption scheme from bi- linear pairings,” International Journal of Security and Networks, 3(3), 206–215, 2008, doi:https://doi.org/10.1504/IJSN.2008.020095.
- X. Li, K. Chen, “Identity based proxy-signcryption scheme from pairings,” in IEEE International Conference onServices Computing, 2004.(SCC 2004). Proceedings. 2004, 494–497, IEEE, 2004, doi:10.1109/SCC.2004.1358050.
- M. Wang, H. Li, Z. Liu, “Efficient identity based proxy-signcryption schemes with forward security and public verifiability,” in International Conference on Networking and Mobile Computing, 982–991, Springer, 2005, doi:https: //doi.org/10.1007/11534310 103.
- Q. Wang, Z. Cao, “Two proxy signcryption schemes from bilinear pairings,” in International Conference on Cryptology and Network Security, 161–171, Springer, 2005, doi:https://doi.org/10.1007/11599371 14.
- S. Duan, Z. Cao, Y. Zhou, “Secure delegation-by-warrant ID-based proxy signcryption scheme,” in International Conference on Computational and Information Science, 445–450, Springer, 2005, doi:https://doi.org/10.1007/ 11596981 65.
- M. Wang, Z. Liu, “Identity based threshold proxy signcryption scheme,” in The Fifth International Conference on Computer and Information Technology (CIT’05), 695–699, IEEE, 2005, doi:10.1109/CIT.2005.129.
- J. Zhang, J. Mao, “A novel identity-based multi-signcryption scheme,” Computer Communications, 32(1), 14–18, 2009, doi:https://doi.org/10.1016/j. comcom.2008.07.004.
- S. S. D. Selvi, S. S. Vivek, C. P. Rangan, “Breaking and fixing of an identity based multi-signcryption scheme,” in International Conference on Provable Security, 61–75, Springer, 2009, doi:https://doi.org/10.1007/978-3-642-04642-1 7.
- M. Zhang, B. Yang, S. Zhu, W. Zhang, “Efficient secret authenticatable anonymous signcryption scheme with identity privacy,” in International Confer- ence on Intelligence and Security Informatics, 126–137, Springer, 2008, doi: https://doi.org/10.1007/978-3-540-69304-8 14.
- F.-g. Li, S. Masaaki, T. Tsuyoshi, “Analysis and improvement of authenticatable ring signcryption scheme,” Journal of Shanghai Jiaotong University (Science), 13(6), 679–683, 2008, doi:https://doi.org/10.1007/s12204-008-0679-2.
- Z. Zhu, Y. Zhang, F. Wang, “An efficient and provable secure identity-based ring signcryption scheme,” Computer standards & interfaces, 31(6), 1092–1097, 2009, doi:https://doi.org/10.1016/j.csi.2008.09.023.
- Y. Yu, F. Li, C. Xu, Y. Sun, “An efficient identity-based anonymous signcryption scheme,” Wuhan University Journal of Natural Sciences, 13(6), 670–674, 2008, doi:https://doi.org/10.1007/s11859-008-0607-1.
- L. Zhun, F. Zhang, “Efficient ID–based ring signature and ring signcryption schemes,” in 2008 International Conference on Computational Intelligence and Security, volume 2, 303–307, IEEE, 2008, doi:10.1109/CIS.2008.51.
- H. Xiong, Z. Qin, F. Li, “Cryptanalysis of an Identity Based Signcryption without Random Oracles,” Fundamenta Informaticae, 107(1), 105–109, 2011, doi:10.3233/FI-2011-395.
- F. Li, B. Liu, J. Hong, “An efficient signcryption for data access control in 99(5), 465–479, 2017, doi:https://doi.org/10.1007/s00607-017-0548-7.
- V. Kirtane, C. P. Rangan, “RSA-TBOS signcryption with proxy re-encryption,” in Proceedings of the 8th ACM workshop on Digital rights management, 59–66, 2008, doi:https://doi.org/10.1145/1456520.1456531.
- J. Malone-Lee, W. Mao, “Two birds one stone: signcryption using RSA,” in Cryptographers’ Track at the RSA Conference, 211–226, Springer, 2003, doi:https://doi.org/10.1007/3-540-36563-X 14.
- C. Wang, X. Cao, “An improved signcryption with proxy re-encryption and its application,” in 2011 Seventh International Conference on Computational Intelligence and Security, 886–890, IEEE, 2011, doi:10.1109/CIS.2011.200.
- W. Huige, W. Caifen, C. Hao, “ID-based proxy re-signcryption scheme,” in 2011 IEEE International Conference on Computer Science and Automation Engineering, volume 2, 317–321, IEEE, 2011, doi:10.1109/CSAE.2011.5952478.
- X. Tian, X. Wang, A. Zhou, “DSP RE-Encryption: A flexible mechanism for access control enforcement management in DaaS,” in 2009 IEEE International Conference on Cloud Computing, 25–32, IEEE, 2009, doi: 10.1109/CLOUD.2009.65.
- Q. Liu, C. C. Tan, J. Wu, G. Wang, “Reliable re-encryption in unreliable clouds,” in 2011 IEEE Global Telecommunications Conference-GLOBECOM 2011, 1–5, IEEE, 2011, doi:10.1109/GLOCOM.2011.6133609.
- S. Yu, C. Wang, K. Ren, W. Lou, “Achieving secure, scalable, and fine-grained data access control in cloud computing,” in 2010 Proceedings IEEE INFOCOM, 1–9, Ieee, 2010, doi:10.1109/INFCOM.2010.5462174.
- M. Li, S. Yu, Y. Zheng, K. Ren, W. Lou, “Scalable and secure sharing of personal health records in cloud computing using attribute-based encryption,” IEEE transactions on parallel and distributed systems, 24(1), 131–143, 2012, doi:10.1109/TPDS.2012.97.
- M. Nabeel, N. Shang, E. Bertino, “Privacy preserving policy-based content sharing in public clouds,” IEEE Transactions on Knowledge and Data Engineering, 25(11), 2602–2614, 2012, doi:10.1109/TKDE.2012.180.
- K. Yang, X. Jia, “Expressive, efficient, and revocable data access control for multi-authority cloud storage,” IEEE transactions on parallel and distributed systems, 25(7), 1735–1744, 2013, doi:10.1109/TPDS.2013.253.
- J. Hur, “Improving security and efficiency in attribute-based data sharing,” IEEE transactions on knowledge and data engineering, 25(10), 2271–2282, 2011, doi:10.1109/TKDE.2011.78.
- F. Li, H. Zhang, T. Takagi, “Efficient signcryption for heterogeneous systems,” IEEE Systems Journal, 7(3), 420–429, 2013, doi:10.1109/JSYST.2012. 2221897.
- Y. Sun, H. Li, “Efficient signcryption between TPKC and IDPKC and its multi- receiver construction,” Science China Information Sciences, 53(3), 557–566, 2010, doi:https://doi.org/10.1007/s11432-010-0061-5.
- Q. Huang, D. S. Wong, G. Yang, “Heterogeneous signcryption with key privacy,” The Computer Journal, 54(4), 525–536, 2011, doi:10.1093/comjnl/bxq095.
- J. H. An, Y. Dodis, T. Rabin, “On the security of joint signature and encryption,” in International Conference on the Theory and Applications of Cryptographic Techniques, 83–107, Springer, 2002, doi:https://doi.org/10.1007/ 3-540-46035-7 6.
- F. Li, T. Takagi, “Secure identity-based signcryption in the standard model,” Mathematical and Computer Modelling, 57(11-12), 2685–2694, 2013, doi: https://doi.org/10.1016/j.mcm.2011.06.043.
- L. Chen, J. Malone-Lee, “Improved identity-based signcryption,” in International Workshop on Public Key Cryptography, 362–379, Springer, 2005, doi:https://doi.org/10.1007/978-3-540-30580-4 25.
- B. Waters, “Efficient identity-based encryption without random oracles,” in An- nual International Conference on the Theory and Applications of Cryptographic Techniques, 114–127, Springer, 2005, doi:https://doi.org/10.1007/11426639 7.
- Y. Ming, Y. Wang, “Cryptanalysis of an Identity Based Signcryption Scheme in the Standard Model.” IJ Network Security, 18(1), 165–171, 2016, doi: 10.6633/IJNS.
- G. Zhu, H. Xiong, Z. Qin, “Fully secure identity based key-insulated signcryption in the standard model,” Wireless personal communications, 79(2), 1401–1416, 2014, doi:https://doi.org/10.1007/s11277-014-1936-3.
- B. Lynn, et al., “The stanford pairing based crypto library,” Privacy preservation scheme for multicast communications in smart buildings of the smart grid, 324, 2013.
- H. Xiong, Q. Mei, Y. Zhao, “Efficient and provably secure certificateless parallel key-insulated signature without pairing for IIoT environments,” IEEE Systems Journal, 14(1), 310–320, 2019, doi:10.1109/JSYST.2018.2890126.
- S. Alornyo, M. Asante, X. Hu, K. K. Mireku, “Encrypted Traffic Analytic using Identity Based Encryption with Equality Test for Cloud Computing,” in 2018 IEEE 7th International Conference on Adaptive Science & Technology (ICAST), 1–4, IEEE, 2018, doi:10.1109/ICASTECH.2018.8507063.
- S. Alornyo, E. Aidoo, K. K. Mireku, B. Kwofie, X. Hu, M. Asante, “ID-Based Outsourced Plaintext Checkable Encryption in Healthcare Database,” in 2019 International Conference on Cyber Security and Internet of Things (ICSIoT), 48–53, IEEE, 2019, doi:10.1109/ICSIoT47925.2019.00016.
- S. Alornyo, Y. Zhao, G. Zhu, H. Xiong, “Identity Based Key-Insulated Encryption with Outsourced Equality Test.” IJ Network Security, 22(2), 257–264, 2020, doi:10.6633/IJNS.860.
- S. Alornyo, A. E. Mensah, A. O. Abbam, “Identity-based Public Key Cryptographic Primitive with Delegated Equality Test Against Insider Attack in Cloud Computing,” International Journal of Network Security, 22(5), 743–751, 2020, doi:10.6633/IJNS.202009 22(5).04.
