Offline Signature Recognition and Verification Using ORB Key Point Matching Techniques
Volume 5, Issue 4, Page No 01-07, 2020
Author’s Name: Aravinda Chickmaglore Venkataramu1,a), Atsumi Masahiko2, Akshaya1, Amar Prabhu Gurupura1, Udaya Kumar Reddy Kyasambally
Rajashekar1
View Affiliations
1Department of Computer Science and Engineering, N.M.A.M Institute of Technology,Nitte 574110, India
2Department of Electronic and Computer Engineering,Ritsumeikan University, Kusatsu,5258577,Japan
a)Author to whom correspondence should be addressed. E-mail: araivnda.cv@nitte.edu.in
Adv. Sci. Technol. Eng. Syst. J. 5(4), 01-07 (2020); ![]() DOI: 10.25046/aj050401
DOI: 10.25046/aj050401
Keywords: Image matching, robust independent elementary features (BRIEF), oriented FAST, rotated BRIEF (ORB)
Export Citations
An extensive work has been carried out in the field of human transcribe-verification and transcribe-recognition by extensive scholars across the globe from past decades. In order to demeanour immense experiments for considering the performance of the newly intended models and to substantiate the efficacy of the proposed model which is moderately required. This paper monologue the problem of signature-verification and recognition using diverse ORB key points and Convolution Neural Network. This method reckons on descriptors for detection and matching. The systematic approach is tested more on an few real and few fake signatures. Many features and combination of features were proposed for signature substantiation and acknowledgement. Numerous experiments are conducted to determine the capability of the proposed models in selective genuine and forgery signature. In this context, a large signature corpus comprising of 29950 offline signatures from 605 persons is created during the course of the research work. Finally the achievement was achieved about 90% of correct accuracy of the given original signature.
Received: 08 May 2020, Accepted: 17 June 2020, Published Online: 06 July 2020
1. Introduction
In modern society there is a greater demand for reliable methods of personal authentication because authentication is a crucial aspect of our daily life activities such as document authentication, having access to computing facilities or information, seeking entry to secured zone, etc. These activities require fast and effective automatic personal authentication systems. Existent classes in handwritten signatures: 1) Online/dynamic signatures 2) Offline/static signatures. A specially designed electronic device like digitizing tablet is used to record online-signature along with features like position, pressure, elevation etc., whereas, an offline signature is a digitized signature image taken using electronic devices like scanner, camera etc.[1][3] During the present day situation the digital images play a very basic role in many applications and have become a important source of information. As we all knew that feature detection and feature matching will plays the vital role in image processing applications, like image retrieval, object detection and many more. The offline signature and verification are related to probing the components of the signature into integral elements for extracting features by matching techniques is as shown in the Figure 1. The SURF technique is a feature finder which estimate of SIFT and performs faster than SIFT without reducing the quality of identified points[4]-[5]. These two techniques are thus based on descriptor and a detector. One more well-known technique BRIEF is an alternative for SIFT which requires less complexity with similar matching performance.Rublee et al. proposed Oriented FAST and Rotated BRIEF (ORB) as another efficient alternative for SIFT and SURF. In this paper the main concentration was on the ORB feature rather than SIFT and SURF. The experiment was carried out for the robustness of the signature key point techniques against rotation, scaling, and deformity due to horizontal or vertical shears.
2. Related work carried out so far
As we all knew that signature verification and recognition are considered to be most complex and challenging problem in pattern recognition area by virtue of large intraclass divergence between individual and less interclass deviations between signatures of individuals in toady’s’ global field.
2.1 Template Matching
This is one of the oldest analogous artistry used for pattern-matching. This technique is used for a signature class denoted by a template and is being compared with the original to establish its authentication. As referred in the ”Dynamic time warping”, (DTW) is the materialistic technique used to establish a match between a test signature and a template[6].
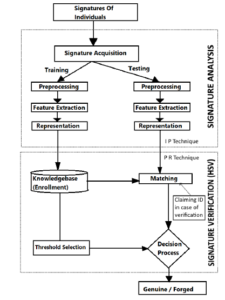
Figure 1: Depiction of HSVR system
2.2 Distance Classifiers
By using this technique such as Euclidean distance experiments were carried out for tracing the solutions and considered this technique by taking comprehensive features such as ”heights”, ”width”, ”slant angles”, ”maximum horizontal projection shift as measure of similarity”. Fang et al. used Mahalanobis distance for computing similarity among the local and global feature vectors. This work used a data set which was consisting of 800 signatures from 20 individuals. In this method the nearest neighbor and a threshold classifier are used[7].
2.3 Bayesian Classifiers
As per the author considered the pertinence of the refitted version of Bayesian network for offline. This kind of network is different from the traditional Bayesian. This network node are splits into two classes namely common and alternative hypothesis, to build the network in tree structure. This captures the conditional probability of every node and topological relations between the components with the nodes of the network. this method uncertainties in structure description between various components which are encoded. The FRR of 20% and the FAR of 14% were reported on a small database of 160 signatures from eight individuals [8].
2.4 Support Vector Machines
As per the author measured a Human Signature Verification and Recognition system as 2 class pattern-recognition problem. By this method ”DTW technique”, ”SVM classifier”, ”PCA” and ”Bayes, concepts are used. First the test signature is combined with referred signature using DTW to find authenticity of test signatures. This feature is then classified as authentic or forgery. For this case linear classifier in combination with PCA, Bayes, SVM classifier are used for classification purposes. The FRR of 1.64% and the FAR of 3.85% are obtained on a dataset of 306 signatures.
3. Overview of Feature matching techniques
3.1 SIFT
The SIFT mainly projected for solving the image rotation, transformations and opinion point in matching features, as per the author Lowe. The main key functionality is as follows (a) Evaluating the scale space using Gaussian techniques (b) point localization (c) orientation (d) generator.
3.2 SURF
The SURF is nearly alike to DoG features. The replacement of Gaussian average, the squares are used for approximation. It uses Binary Large Object detector based on Hessian matrix to find the point of interest and wavelet response for feature description as mentioned [9]-[10].
3.3 ORB
The ORB is an amalgamation of FAST key point and BRIEF descriptor with minor changes. The main technique of FAST is to identify the key points along with Harris corner to find top N points. This will not figure out the orientation and rotation variant but computes the weighted centroid of the located point. The resultant gives the corner point to centroid and this leads to orientation. The ORB rotation matrix is calculated using the orientation of patch and BRIEF descriptors are controlled to orientation[11].
3.4 Feature matching and representation
Even though there has been widely published papers and solved problem based on this offline signature, still there is lot of research problems which is still being carried out for analysis purpose. The vital issue of this analysis is to resolve the most pertinent features. Special features like characterization of signatures based on feature and formulate the corresponding between the insinuation and test scribbles are the significant issue in authentication[12]-[13]. This study mainly relies on the effectual representation of signatures and learning similar features. These features are derived from geometrical properties for offline signatures as shown in the Figure 2.
- CNN classifier is used to recognize which person the signature belongs to
- If the recognition threshold is >80% feature matching technique is used, else it will be rejected.
- Extracting the signature part from signature database and resize the same
- Calculating the keypoints using ORB technique.
- Comparing the key points with original sample within database.
- If the number of matches between the given sample and the original image is > than the average number of matches between the original signatures it will be accepted else rejected.
- Carried out the experiment for matching and classifying the genuine and forgery.
5. Feature Detection And Matching Using ORB
The most relevant for problem solving the task relating to application as mentioned in the paper [14]. The offline signature samples specific structures like point, edges were considered. The resultant neighbourhood operation is applied on the sample. The ORB featured was measured for the experimental purpose, whereas the SIFT performed better detection on the same problem. This builds wellknown ”Features from accelerated segment test”, ”Features from accelerated segment test”, key-point detector and ”Binary Robust Independent Elementary Features descriptor”.
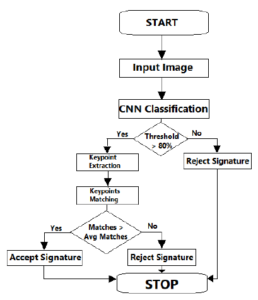
Figure 3: Architecture flow of Human Signature Verification Recognition
”Features from accelerated segment test”, is a corner detection method, which could be used to extract feature points is as shown in Figure 5. The ”Features from accelerated segment test”, Algorithm applied on the signature sample to find the key points is as follows
- Chosen a pixel p on the signature sample which is to identified as key point or not a key point. This intensity be Ip.
- Applied the appropriate threshold value t.
- After this the pixel p was considered as a corner set of n contiguous pixels in the circle and then all the brighter pixels than Ip +t was considered.
- To improve the accuracy of the algorithm, first the intensity of the pixel was compared 1,5,9,13 of the circle with Ip. Finally all least three pixels out of these four pixels were considered because of satisfying the threshold criterion.
- The least three of the four pixel values I1, I5, I9, I13 were not found above nor below the Ip + t, then p is not an interest point was discarded.
- These steps were repeated to all the pixels in the signaturesThe BRIEF performance is used to find the key points which was recognized by the prior FAST algorithm where this method was considered for processing and converting this into binary feature vector to epitomize the image of the given sample [15]-[17]. This consist of 0 and 1 were every keypoint is designated by a feature vector which is 128-512-bit string and the selected random pair of pixels by default was identified as neighbourhood key point. The discern neighbourhood around pixel is known as a patch, which is a square of some pixel width and height. The first pixel in the random pair was drawn from Gaussian and centred around the key point with standard deviation. This creates a vector for each key-point in an signature sample is as shown in the Figure 7.
Algorithm 1: The rBRIEF() algorithm for ORB is as follows
Result: Greedy Search
Run each test against all training patches obtained from the sample;
Order the tests by their distance from a mean of 0.5, forming the vector T;
ORB feature matching with Brute Force Technique To attain the fast and accurate key-point matching BFT was instigated. The gain of using this descriptor was one feature in first set and it is matched with all residual features and the second using some distance calculation. Finally, the adjoining one is returned.
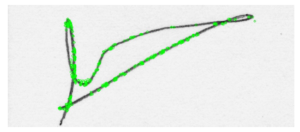
Figure 4: Detected keypoints
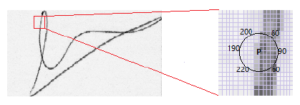
Figure 5: FAST Algorithm work flow

Figure 6: BRIEF Algorithm work flow

Figure 7: Good matches of keypoints from 2 signature samples
6. Experimental Results Conducted
F.A.R Choosing the counterfeit signature sample and discerning it is a genuine signature. It is as given by the equation 1
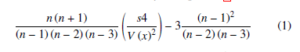
False Acceptance Rate=Number of Forgery Signature Accepted/Number of Forgery Tested
False Rejection Rate (F.R.R) Snubbing the signature though it is frank sampled signature discerning it is a forgery sample. This is given by the equation 2
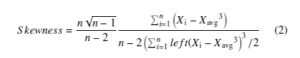
Skewness can also be defined as ratio of the 3rd moment and 2nd moment raised to the power of 3/2 ratio of the 3rd moment and the standard deviation as mentioned in the equation.
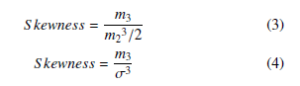
F.R.R=Number of Genuine Signature Rejected/Number of Geniune Tested
Table 1: Online signature dataset for research purpose
| Datasets | No. of | No. of | No. of | total no. of |
| Signers | Genuine | Forgeries | signatures | |
| MCYT
-75[151] |
75 | 75*15 | 75*15 | 2250 |
| GDPS
-signature |
160 | 160*24 | 160*30 | 8640 |
Table 2: Summary of DB-605 datase
| Datasets | No. of | No. of | No. of | total no. of |
| Individuals | Genuine | Forgeries | signatures | |
| DB
-200 |
200 | 200*28 | 200*28 | 11200 |
| MCYT
-300 |
330 | 330*25 | 330*25 | 16500 |
| DB
-605 |
605 | 14975 | 14975 | 29950 |

Figure 8: Images of MCYT-75: (a) Accurate signatures (b) Corresponding fraudulence signatures
Table 3: Representation of C.N.N Architecture
| Layer(type) | Output-Shape | Parameter |
| convl2d 1 (Convl2D) | (None, 173, 173, 32) | 320 |
| convl2d 2 (Convl2D) | (None, 169, 169, 64) | 51264 |
| batch normalization 1 | (Batch (None, 169, 169, 64) | 256 |
| activation 1 (Activation) | (None, 169, 169, 64) | 0 |
| max pooling2d 1 | (MaxPooling2 (None, 84, 84, 64) | 0 |
| global average pooling2d 1 | ( (None, 64) | 0 |
| dense 1 (Dense) | (None, 70) | 4550 |
Total-parameters: 56,390
Trainable-parameters: 56,262
Non-trainable-parameters: 128
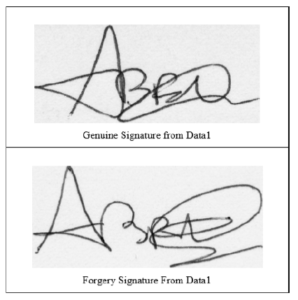
Figure 9: Sample of Feature extraction
6.1 Neural Network setup for experiment
Initialize position: This is the first stage, where NN is put up by describing the Network architecture (i/p and o/ps) . Further, the additive the number of patterns which will be used to train the network has to be considered along with the number of units in output layers are decided Generate Training Set:The quality of cognitive process is deliberated as important to the neural network; this gives an ability to recognize any changes in the signature images of the same person. Many individual learning algorithms have been developed for the verification/recognition purposes.
Create Neural-Network Set:In the antecedent period, the signature samples of every persons are divided into training and testing set. The training set are fed into a multilayer network. Multilayer NN is nothing but network with multiple hidden layers. In this work, data flow in the forward direction that is from input layer to output layer.
Table 4: Summary of datasets used
| Sample | FAR | FER | Accuracy |
| 0 | 0 | 100 | |
| 0 | 20 | 90 | |
| 0 | 20 | 90 | |
| 0 | 40 | 80 | |
| 0 | 0 | 100 | |
| 0 | 20 | 90 |
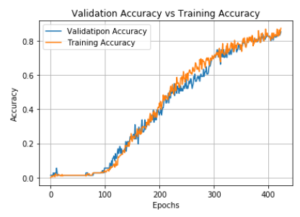
Figure 10: Training Accuracy and Validation Accuracy
In this phase, weights are stated for every construction using the simple weighting equation which is preferred to be forwarded that is, data flows from the input layer to the output layer. This stage specifies the weights which are available on every connection using the simple weighting equation. Weight(t + 1) = weight (t) + η(ωweight (t)) the weight t+1 is equal to the weight at time t plus the learning rate times the calculated weight change.
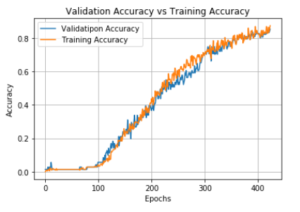
Figure 11: Training Accuracy and Validation Accuracy
In the paper Contour based technique was used to classify signature into 2 classes (genuine and fake) the accuracy achieved was around 81% though this method used was fast and robust, the main disadvantage posed by the method was it required 2 classes of each signature and about 15 samples from each class. By applying the Multiple classifiers technique using Hu and Hog features, it was able to achieve an accuracy of around 90%. In this experiment, we set out to find various methods which proved effective for signature classification. Though the method was fast, it posed the same disadvantage of having to use 2 classes per person (genuine and fake) and consider about 15 samples each. This was far from a practical approach as collecting 15 samples for each person was not possible. In this paper, we sought out to find a practical approach to classify signatures into real and fake considering practicality of the problem. Hence as a practical approach, we collected 3 genuine signatures from each person and used a combination of deep learning and machine learning to classify signatures. The accuracy in this case was found to be around 92% but this method gets rid of the disadvantages faced in the previous 2 cases and makes the classification task suit the real world problem.
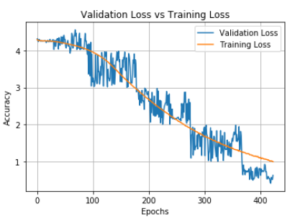
Figure 12: Training Loss and Validation Loss
Conflict of Interest
The authors declare no conflict of interest.
Acknowledgment
We would like to thank to N.M.A.M Institute of Technology, Nitte, INDIA and Ritsumeikhan University Japan,for there support towards this paper.
- Wilkinson, T.S., Pender, D.A., Goodman, J.W., 1991. Use of synthetic dis- criminant functions for hand-written signature verification. Appl. Opt. 30 (23), 33453353
- Ward JE, Wendell RE. A new norm for measuring distance which yields linear location problems. Operation Reasearch. 1980;28:836844
- Xiao,Signature verification using a modified Bayesian network, Article in Pattern Recognition 35(5):983-995. May 2002,10.1016/S0031-32030100088-7
- MB Yilmaz, B Yanikoglu, C Tirkaz, Offline signature verification using clas- sifier combination of HOG and LBP features- 2011 international joint 2011- ieeexplore.ieee.org.DOI: 10.1109/IJCB.2011.6117473
- David G. lowe, Distinctive Image Features from Scale-Invariant Key-Points, International Journal of Computer Vision, 2009, Vol.60, No.2, pp.91-110.
- Mohan Ramakrishna, Shylaja SS, Is ORB efficient Over Surf for Object Recog- nition? , International Journal of Advanced Research in Science Engineering and Technology, 2014,Vol.3,No.8, pp.2783-2788, ISSN: 2278 1323
- Jian Li, Xialong Li, Nin Yang, Xingming, Segmentation Based Im- age Copy-Move Forgery Detection Scheme, IEEE Transactions on In- formation Forensics and Security, 2015,Vol.10, No.1,pp.507-518. DOI: 10.1109/TIFS.2014.2381872
- David G. lowe, Distinctive Image Features from Scale-Invariant Key-Points, International Journal of Computer Vision, 2009, Vol.60, No.2, pp.91-110. DOI https://doi.org/10.1023/B:VISI.0000029664.99615.94.
- B. Moghaddam, C. Nastar and A. Pentland, A Bayesian similarity measure for deformable image matching, Image and Vision Computing, vol. 19, no. 5, pp. 235-244, 2001. https://doi.org/10.1016/S0262-8856(00)00059-7
- M. Gzel, ’A Hybrid Feature Extractor using Fast Hessian Detec- tor and SIFT’, Technologies, vol. 3, no. 2, pp. 103-110, 2015. https://doi.org/10.3390/technologies3020103
- Xu Bo, Wang Junwen, Liu Guangie and Dai Yuewei, Image Copy- Move forgery Detection Based on SURF, International Conference on Multi-media Information Networking and Security, 2010, pp.889-89. DOI: 10.1109/MINES.2010.189
- Ethan Rublee Willow Garage, Menlo Park, ORB: An efficient alternative to SIFT or SURF, IEEE International Conference on Computer Vision, 2011, pp.2564-2571. DOI: 10.1109/MINES.2010.189.
- Toqeer Mohmood, A survey on Block based Copy-Move Image Forgery detection Techniques, International Conference,2015,pp.1-6.DOI: 10.1109/ICET.2015.7389169
- P. Sykora, P. Kamencay and R. Hudec, Comparison of SIFT and SURF Methods for Use on Hand Gesture Recognition based on Depth Map, AASRI Procedia, vol. 9, pp. 19-24, 2014. https://doi.org/10.1016/j.aasri.2014.09.005.
- Ethan Rublee, Vincent Rabaud, Kurt Konolige and Gary Bradski, ORB: and efficient alternative to SIFT or SURF, IEEE International Conference on Com- puter Vision, 2011.DOI: 10.1109/ICCV.2011.6126544.
- Aravinda C.V, Lin Meng, Akshaya, Udaya Kumar Reddy K R, Signa- ture Recognition and Verification Using Multiple Classifiers Combina- tion of Hus and HOG Features, 2019 International Conference on Ad- vanced Mechatronic Systems (ICAMechS) 2019-08-18 conference-paper DOI: 10.1109/icamechs.2019.8861686ISBN: 9781728134802
- Aravinda C.V, Lin Meng, Akshaya, Udaya Kumar Reddy K R, An ap- proach for signature recognition using contours based technique, 2019 In- ternational Conference on Advanced Mechatronic Systems (ICAMechS) 2019-08-18, conference-paper DOI: 10.1109/icamechs.2019.8861686
Citations by Dimensions
Citations by PlumX
Google Scholar
Scopus
Crossref Citations
- M. S. Sannidhan, Jason Elroy Martis, C. V. Aravinda, Roheet Bhatnagar, "Correction of an Image for Colour Blindness Using the Fusion of Ishihara Filter and Histogram Equalization." In The 3rd International Conference on Artificial Intelligence and Computer Vision (AICV2023), March 5–7, 2023, Publisher, Location, 2023.
- Joel Adeyanju Adewuyi, Gabriel Babatunde Iwasokun, Arome Junior Gabriel, "Transformation technique for derivation of similarity scores for signatures." Iran Journal of Computer Science, vol. 5, no. 4, pp. 317, 2022.
No. of Downloads Per Month
No. of Downloads Per Country
