Securing Hybrid SDN-based Geographic Routing Protocol using a Distributed Trust Model
Volume 5, Issue 2, Page No 567–577, 2020
Adv. Sci. Technol. Eng. Syst. J. 5(2), 567–577 (2020);
 DOI: 10.25046/aj050271
DOI: 10.25046/aj050271
Keywords: IoV, Routing protocols, SDN, QoS, Security, Availability, Reliability, Integrity, Trust
In this paper, the vulnerabilities and the security attacks against vehicular networks, SDN architecture and some security solutions for SDVN are studied. Secondly, a complete and improved version of the secure HSDN-GRA routing protocol based on a distributed trust model is proposed where public keys of the vehicles are managed in a distributed way. Besides, in this approach, a weight is assigned to every vehicle, which is calculated from its freeload and its trust values per those of the neighbors. The trust value is deduced from the historical interactions stored in a log of communication errors. To measure the trust value, three unreliable behaviors occurred in a time interval are considered. The vehicle with the role of cluster head hosts a list of each vehicles misbehaviors forming a log of communication errors. A vehicle will be chosen as the next relay according to its weight. As a positive result of this complete proposed approach, the following security requirements are achieved: the vehicle’s authentication and the data integrity are guaranteed by a signature mechanism, whereas an encrypted function is used to ensure the confidentiality of the exchanged data. The goal is to protect the routing process against malicious and unstable nodes. Finally, the implementation details and simulation analysis are given, and a comparative study between the secure and the insecure HSDN-GRA is presented in the presence of a percentage of malicious nodes in the network. The perspective of managing non-collaborative vehicles is briefly introduced as future work.
1. Introduction
The Vehicular Adhoc Networks (VANET) suffers from many lacks such as delays of communication because of the multi hop scenarios, frequent links failures because of the nodes mobility, and also a low security due to the several attacks and intrusions against the wireless and the heterogeneous network.
In our previous works [1][2], the SDN paradigm has been identified as a suitable approach for dealing with: the dynamic and large scale environment, the robustness of communication, the heterogeneity of the network concerning applications and the communication technologies, the routing strategies and also the security issues [3].
However, find the best way to implement the controller to suit to vehicular networks constraints is unresolved, especially because of the SDVN vulnerabilities. The security and the routing features are controlled by the SDN Controller. Whereas, the data plane applies according to the controller rules, since it is devoid of intelligence. ity and the availability of this controller.
This paper represents an extended version of our previous work [1] untitled ”Securing Southbound Interface of HSDN-GRA Vehicular Routing Protocol using a Distributed Trust” that is published in 2019 Fourth International Conference on Fog and Mobile Edge Computing (FMEC). We described an IoV communication use case based on the SDN architecture, to root IoV’s data in a secure and robust manner from a source to a destination. The proposition was a preliminary approach without simulation analysis.
In this extended paper, we firstly discuss the security vulnerabilities of vehicular networks, SDN paradigm and SDVN networks. Secondly, we propose to secure the HSDN-GRA routing protocol by using a an encrypted function and trust model [1]. In this trust model, each new vehicle broadcast its public key to its neighbors, all the keys are managed in a distributed way. Besides, the described approach aims to assign a weight ω to each vehicle. ω is deduced from the free load value as well as the trust value of each vehicle per those of their neighbors.
To deduce the trust value of a vehicle, this approach uses the error log of HSDN-GRA protocol [4], as the historical misbehaviors of a vehicle gives its trust rate. three types of unreliable behaviors that a vehicle had in a period of time are considered. The list of each vehicle’s misbehavior is stored in an error log and embedded on a specific cluster head vehicle. A vehicle can be the next relay according to its weight walue.
the advantage of the proposed solution is the improvement of
security in the communication process, indeed, vehicle authentication and data integrity are obtained using a signature mechanism, while the confidentiality of the data exchanged is provided by an encryption function. the main purpose of secure HSDN-GRA is to protect the routing process from malicious and unstable vehicles.
The present paper is organized as follows: Section 2 studies the security attacks against vehicular networks and SDN architecture and some security solutions for SDVN. Section 3 describes our Secure HSDN-GRA approach. The implementation details and simulation analysis is presented in Section 4. Finally, Section 5 concludes the main contributions and summarizes the perspective of an incentive scheme in order to manage the non-collaborative vehicles.
2. Background and Related Work
In the survey [2] realized by Alouache et al., the SDN architecture is described as an alternative to secure the network and to ensure the data integrity. In fact, a global overview of the system is achievable thank to the SDN controller. It collects information about the entire network traffic instead of exchanging a large amounts of information. As a result, it provides a better and reliable security mechanism than those applied to the traditional network [5].
2.1 Security Attacks in Vehicular Networks
Vehicular networks suffer from several attacks which compromise the main security requirements. [6].
In Table 1 non exhaustive list of these attacks are given.
2.2 Security Attacks in SDN Architecture
The SDN paradigm also has its own vulnerabilities, they are principally related to the characteristics, the location and the crucial role of the controller, as well as the control data flow exchanged between the control plane and the data plane [7].
Table 2 exposes a non exhaustive list of attacks related to the SDN paradigm.
2.3 Security Solutions for SDVN
Despite the vulnerabilities exposed in Table 1 and those mentioned in Table 2, and since SDN exceeds the limits of traditional mechanisms, it can be beneficial for IoV security deficiencies.
Table 1: Vehicular Network Attacks vs Security Requirements
In fact, the SDN controller labels and isolates suspect flows and their sources, consequently, the data plane will not process the packets coming from these flows.
Besides, the IoV network is heterogeneous and uses a set of communication technologies such: WAVE, DSRC, LTE, etc. having their own security policies, therefore, due to the SDN controller and its given global overview, these security policies can be deployed without conflict, which reinforces the security of the whole IoV system.
In addition, the centralization and the abstraction provided by the controller give the administrators the possibility to update any security policy based on observed unreliable behaviors. Table 3 describes how SDN can be a solution for security issues.
Table 2: SDN Attacks vs Security Requirements
| SDN attacks in SDN Architecture | |||||
| DoS on the Data plane | x | ||||
| Distributed DoS on the Control plane | x | ||||
| Controller identity spoofing | x | x | x | x | x |
| Flow based forwarding attack | x | x | |||
| Flow table alteration | x | x |
Table 3: Security in IoV with SDN Architecture
| Action | details |
| Intrusion detection | The SDN controller manages the nodes
authentication and detects malicious intrusions. |
| Attacks identification | The SDN controller monitors the exchanged flows emanating from all the nodes to detect any setting alteration. |
| Self recovery mechanism | The SDN controller hosts rules to automatic recovery against any attack. |
Recently, some research papers deal with both routing and security issues in vehicular networks by adopting the SDN paradigm.
The Improvised Trust based Ad-hoc On-demand Distance Vector routing (I-TAODV) is proposed by Vasudes et al. in [8], it aims to secure routing in a multi hop scenario.
Based on a metric called trust value, the authors propose an algorithm to identify the trusted vehicles, and another one to identify the malicious ones.
This protocol is built on the SDN paradigm, where the control plane monitors forwarding, reversing, trust of forwarding Vehicle, trust of reverse vehicle, path trust and network performances.
Zhang et al. elaborate The Software-Defined Trust based Ad hoc On-demand Distance Vector routing (SD-TAODV) in [9]. The process of route discovery, route maintenance, the reverse and forwarding paths are chosen by the control plane.
They also use a trust management mechanism which is represented by a bi-objective function, it tries to optimize two objectives: the node trust and the path trust calculated respectively by Trust Node Calculation Process and Path Trust Calculation Process They are used to enhance the Route Discovery Process of TAODV.
3. Securing the HSDN-GRA
The HSDN-GRA protocol presented in the research [4] exploits a log of communication errors where three types of vehicle’s misbehavior are stored: link failures, random reception of Beacon messages, and non-acknowledgement of previous messages. To estimate the trust value, the vehicle communication history is observed and tracked from the log of communication error. In this extended paper, we use the trust value of each vehicle with comparison to the trust values of all its neighbors.
The trust is described as the expectation and the belief that a vehicle has about other vehicles concerning future behaviors. Its estimation is based on 1) experiences and evidences collected in the past either directly or indirectly, and 2) the knowledge about the vehicles nature, and/or on recommendations from trusted entities [10]-[12].
This trust value in addition to the free load value of each vehicle are aggregated to assign a weight ω to each vehicle. This weight will be used to elect the best relay at each step of the routing process.
The routing rules are commonly governed by two types of controllers in HSDN-GRA: the semi-centralized controller represented by the cluster head, and the distributed controllers represented by the cluster members.
Figure 1 shows an IoV communication scenario using the HSDN-GRA routing protocol based on a semi-centralized SDN architecture.
A vehicle tries to access to an Internet service is requested by a vehicle, but the request fails because the closest infrastructure is down. So it switches to the vehicles on the road for routing its request.
The network is divided on clusters and Cluster heads are elected. Each Cluster Head contains a part of the control plane (the error log). The second part is distributed on the rest of the cluster members.
until reaching the destination, the request transits through vehi-
cles with a hop by hop approach. Each vehicle selects its next relay with respect to the controller policy i.e,: The one who has the best relative trust value and the best relative free load value.
Hypothesis:
- In this extended paper, we opt for the highway scenario, this choice is guided by the stability of vehicle’s speed. • At first, the free load and the trust values of vehicles are equal and optimal.
- Malicious-Vehicles Reliable − Vehicles.
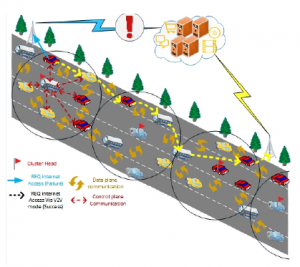
Figure 1: A Use Case of IoV Communication with a Hybrid SDN Architecture
The following subsections describe the securing HSDN-GRA steps.
3.1 Public key Distribution • all the vehicles exchange a define Beacon to form a a one hop neighboring.
- Each vehicle sends its Public Key Pkey to the one hop neighbors, and receives back their Pkey.
- At this initialization step, because of the absence of cluster head, only the distributed controllers embedded on each vehicle are operational.
- Each vehicle has a weight ω, it exploits the load capacity li deduced from the received Beacons, and the trust value Trusti calculated from the log of communication errors according to Formula 1. The weight ω of each vehicle is calculated from Formula 2 by all the neighbors, and the true value will be confirmed by the majority.
- The election of the Cluster Head is realized by a distributed consensus after the initialization period of time T has passed, the one with the largest weight ω will be the Cluster Head.
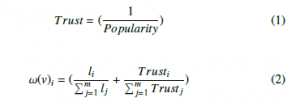
where m is the number of neighbors.
-To monitor the communication errors of each neighbor, in the beginning, before electing cluster heads, logs are distributed within all the vehicles. The trust rate is estimated by exploiting all the distributed logs. So, initially each vehicle:
-Monitors its neighbors and has it own log
-Calculates the weight ω of each neighbor
-Then, each vehicle broadcasts in a map the Pkeyi of each neighbor and their associated weight ω values:
NeighborPkeyMap = {Pkeyi, ωi)}, With i ∈ {1,m}
The algorithm 1 describes how the public key distribution as well as the weight of each vehicle is managed.
Algorithm 1: Public Key Distribution (PKD)
- Let Pkeyi be a the public key of vehicle Vi;
- Let NeighborsPkeyMap < Pkey,ω > be a the map in which a vehicle V store the public key and the weight of its neighbors;
input :Vehicle V output:NeighborsPkeyMap
- Initialization: NeighborsPkeyMap = ∅; ωVi=null; Pkeyi=null;
3.2 Cluster Head Election
-Using all the received NeighborsPkeyMapi, a vehicle V confirms the reliable weight value ωi of each neighbor Vi and the association (Vi/Pkeyi). i.e, a coherent contain of the NeighborsPkeyMap is deduced by the majority who give the same values. -On each vehicle a consensus occur to chose as Cluster Head the vehicle with the largest weight ω.
-The variable ”IsCh” will be True in the Beacon for the Cluster Head, while the rest of vehicles will keep the value False. -The elected Cluster Head, representing the Semi-Centralized SDN controller, will now hosts the log of communication errors related to it cluster.
The algorithm 2 details the Cluster Head election.
Algorithm 2: Secure Cluster Head Election (SCEA)
- Let NeighborsPkeyMapi < Pkey,ω > be a the maps received by V from each neighbor; input :Vehicle V output:ClusterHead
- Initialization: Maxω = ω;PkeyMax=Pkey; ClusterHead = null;
3.3 Secure Control Plane of HSDN-GRA
In this section, the Secure HSDN-GRA is detailed. Once the first election of the Cluster Head occurred, the vehicles signs all their Beacons. The objective is to guarantee the authentication.Figure 2 expose the Beacon message structure.
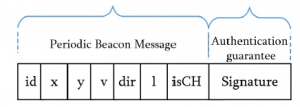
Figure 2: Beacon Message structure in Secure HSDN-GRA
The structure of the messages exchanged via the southbound interface are represented in Figure 3.
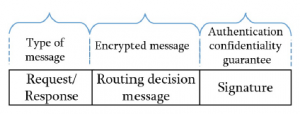
Figure 3: Structure of Southbound Messages in Secure HSDN-GRA
As the confidentiality of the control decisions, especially about the next hops, need to be preserve, we also propose to secure the southbound interface used in HSDN-GRA routing protocol.
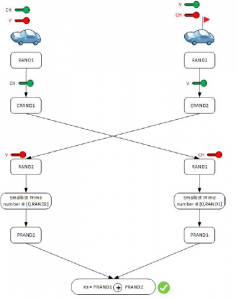
Figure 4: Secret Key creation between the Cluster Head and a vehicle V
To encrypt the data flow of the southbound interface, we are inspired from the symmetric encryption algorithm AES [13].A secret key Ks is exchanged between each vehicle and its Cluster Head. The public keys Pkey already shared are exploited to deduce Ks.
A vehicle V and its Cluster Head exchange two random numbers RAND1 and RAND2 encrypted respectively with PkeyCH and PkeyV .
Then, the Cluster Head decrypt with its private key RAND1
and choose the smallest prime number PRAND1 in the interval [0,RAND1]. The vehicle V decrypt also with its private key RAND2 and choose the smallest prime number PRAND2 in the interval [0,RAND2].
Finally, the secret key Ks is given using the formula 3. The symbol L representing the Exclusive Or logical operation.
![]()
Figure 4 illustrate how the secret key Ks is formed by the Cluster Head and a vehicle V in order to encrypt the southbound interface communications.
Figure 5 illustrate communications inside a cluster of Secure HSDN-GRA.

Figure 5: Communication inside a Cluster of Secure HSDN-GRA
3.4 Secure Incoming Vehicles in a Cluster
Three steps are required to integrate a new vehicle in a cluster:
- The new vehicle Vn broadcast its Beacon and its Pkey to announce its self.
- All the neighbors inside the Cluster reply to Vn with the identifier and the Pkey of the Cluster Head, while sending the triplet (Vn,Pkeyn, ωn) to the Cluster Head.
- The Cluster Head analyzes all the received triplets (Vn,Pkeyn,ωn) in order to confirm the identity of Vn. It deduces the percentage of veracity of this triplet, from the number of vehicles who affirm it. After that, a ChallengeResponse mechanism [14] is exploited associate definitively Vn to Pkeyn.
These steps are respectively illustrated by Figure 6, Figure 7 and Figure 8.
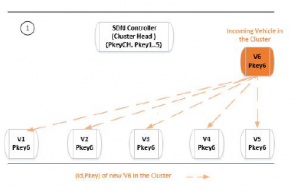
Figure 6: Incoming Vehicle in the Cluster: Phase 1

Figure 7: Incoming Vehicle in the Cluster: Phase 2
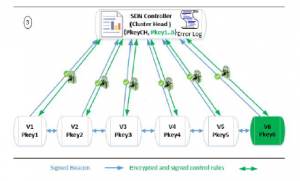
Figure 8: Incoming Vehicle in the Cluster: Phase 3
3.5 Secure Outgoing vehicle from a Cluster
This section shows the behaviour of secure HSDN-GRA in case of outgoing vehicle. Two cases are identified:
The first case deals with a cluster member which formulates a Request-To-Leave message the steps are:
- The Cluster member sends a Request-to-Leave message to the Cluster Head
- A Challenge-Response mechanism [14] is launched to confirm that the request is formulated by the pretending cluster member.
- After the authentication, an ACK message is sent by the Cluster Head to the leaving vehicle as an acknowledgement of its request. Meanwhile, the Cluster Head also broadcasts a Revoke(V, Pkey) message inside the cluster in order to delete the keys of the outgoing vehicle.
- ACK messages confirming the revocation of this vehicle are sent to the Cluster Head by all the cluster members.
Algorithm 3: Secure Outgoing Vehicle From a Cluster (SOC)
1 Let τ be the Beacon interval and ToF be the maximum delay of receiving Beacons; input :Vehicle V output:Cluster
The second case concerns the revocation of the vehicles that don’t respect the periodicity of Beacons, as they are considered as unreliable.
In this paper, at every time-out τ, vehicles are supposed to send and receive back Beacons. Besides, a Timer-of-Refresh ToF, initialized to 5τ, is assigned to each Cluster member sending a Beacon. The Cluster Head launches and decrements ToF when it receives a new Beacon message from a Cluster member.
If the Cluster Head receives t Beacon in the time interval [τ,5τ], the ToF value is refreshed and reset to its initial value. Otherwise, the Cluster member is considered as unreliable and need to be excluded from the cluster according to the following steps:
- If the ToF has passed, the Cluster Head broadcasts a
Revoke(V, Pkey) message within its cluster.
- ACK messages confirming the revocation of this vehicle are sent by all the Cluster members.
The two cases are combined in the algorithm 3.
Figure 9 shows a Cluster member outgoing scenario.
It encompasses the two cases. The black circle details the Request-to-Leave scenario, while the rest explains the revocation procedure.

Figure 9: Outgoing Cluster Member Management
4. Simulation Analysis
In this simulation, we simulate a scenario of the Secure HSDN-GRA routing packets in IoV.
We develop a simulation with traffic condition similar to the situation in Figure 1.
Table 4: NS2 Simulation Parameters
| Parameters | Specification |
| Simulation time | 300s |
| Simulation area | 1000m X 1000m |
| Number of nodes | [20-300] |
| Speed | [50-140] km/h |
| Propagation model | Two Ray Ground |
| Medium capacity | 6 Mbps |
| Transmission range | 310 m |
| Transport layer | UDP |
4.1 NS2 Implementation
The simulation is done under a Ubuntu 10.04 Linux machine where we have installed the new version of network simulator NS2.34[15] and VanetMobiSim[16].
The simulation parameters are summarized in Table 4.
Some simulation functions in C++ are summarized in listing 1 (cf. Appendix 5).
4.2 Experimental Results
The goal of this evaluation consist of the study of attack resilience and routing performances of the secure HSDN-GRA protocol against the insecure HSDN-GRA protocol.
Percentage rate of data delivery and average end to end delay are chosen as indicators of routing performances.
The comparative study is done for different combinations of metrics like: the presence of malicious nodes, the clusters density and the vehicles speed.
the routing decisions of HSDN-GRA protocol are guided by the one-hop neighbors, besides, the secure HSDN-GRA protocol aims to detect and avoid malicious nodes. So, the routing performances will be positively affected by the improvement of routing behavior in presence of malicious nodes
4.2.1 Effect of Malicious Nodes
In this section, we observe in Figure 10 that the Secure HSDN-GRA presents better packet delivery ratio than the baseline HSDN-GRA once an increased number of malicious nodes are introduced in the simulation.
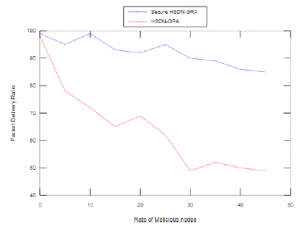
Figure 10: Packet Delivery Ratio vs. Number of Malicious Nodes
Indeed, the Secure HSDN-GRA elects as a relay the neighbor with the best trust value as well as the maximum free load with comparison to the whole neighbors, furthermore, the exchanged packets are signed and encrypted with a secret key Ks which makes the alteration and the destruction of packets more difficult.
Besides, the Secure HSDN-GRA also outperforms the baseline HSDN-GRA of delay in the presence of an increased number of malicious nodes in the simulation as shown in Figure 11.
In fact, the Secure HSDN-GRA takes into account the trust value of each relay with comparison to the whole neighbors as well as the corresponding average free load before choose it. It makes the HSDN-GRA more resilient.
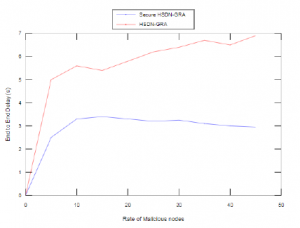
Figure 11: Average End to End Delay vs. Number of Malicious Nodes
4.2.2 Effect of Cluster nodes Density
Figure 12 and Figure 13 show respectively the impact of clusters density on the behaviour of both Secure HSDN-GRA and baseline HSDN-GRA in term of packet delivery ratio and delay especially in the presence of 20% of malicious nodes.
Firstly, for both Secure HSDN-GRA and baseline HSDN-GRA the increase density inside clusters offer better packet delivery ratio because more relays can be exploited. However, the packet delivery ratio is more satisfying when the relays are chosen according to the trust analysis estimated by the network.
Then, we observe in Figure 12 that Secure HSDN-GRA deliver an average of 30.28% of packets more that baseline HSDN-GRA in the presence of 20% of malicious nodes.
Besides, we can deduce that the authentication and the encrypted communications decrease the number of packets alteration, packet lost and malicious intrusion.
Secondly, we can observe that Secure HSDN-GRA reduce the delay comparing to baseline HSDN-GRA because the relays are chosen according to their trust values in order to guarantee the local acknowledgement of each packet sent and reduce the error recovery, consequently the delay is reduced.

Figure 12: Packet Delivery Ratio vs. Clusters Density with 20% of malicious nodes
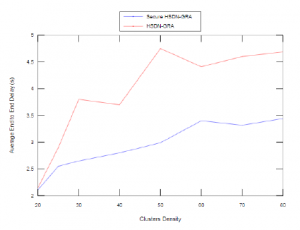
Figure 13: Average End to End Delay vs. Clusters Density with 20% of malicious nodes
4.2.3 Effect of Vehicles Speed
Figure 14 and Figure 15 show the impact of vehicles speed against the Secure HSDN-GRA and baseline HSDN-GRA in the presence of 20% of malicious nodes.
The results in Figure 14 show that the secure HSDN-GRA outperform the baseline HSDN-GRA in term of packet delivery ratio, besides, we can observe that the increase speed stabilizes the packet delivery ratio for the both protocols.
For the delay performances, we can observe in Figure 15 that Secure HSDN-GRA reduces the delay when the speed, furthermore, it surpasses the baseline HSDN-GRA, it is due to the stability of the clusters on the highways and the packets destination are reached faster, since the relays are chosen according to the direction of the destination.
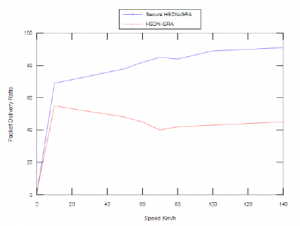
Figure 14: Packet Delivery Ratio vs. Speed with 20% of malicious nodes
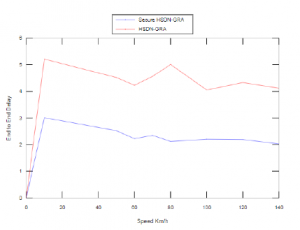
Figure 15: Average End to End Delay vs. Speed with 20% of malicious nodes
5. Conclusion
The result of applying the SDN architecture on vehicular network consist of making the routing strategies optimal, especially for with load balancing, security policies and also for the network heterogeneity management.
Indeed, it aims to select the most suitable channels and frequencies for data transmission at a specific time according to the context and the requirements.
Besides, it implements various security policies and exploits them adaptively according to the requirements. Finally,the nodes are balanced thanks to the global view given by the control plane.
In this paper, a secure HSDN-GRA for more robustness is exposed, a trust model is built between nodes, and the communications between the nodes as well as those of the southbound interface are secured with an encryption function.
Even if we have a performing and securing routing protocol, in a totally distributed system it is difficult to guarantee the cooperation of all the entities without any rewards in turn, the selfish nodes constitute an obstacle of communication in a totally distributed network, so as a future perspective, a solution based on blockchain paradigm will be integrated in secure HSDN-GRA in order to tackle selfish nodes and stimulate their cooperation.
Acknowledgment
This project was supported by Initiative d’Excellence Paris//Seine.
- Lylia Alouache et al. “Securing Southbound Interface of HSDN-GRA Vehicular Routing Protocol using a Distributed Trust”. In: Fourth International Conference on Fog and Mo- bile Edge Computing, FMEC 2019, Rome, Italy, June 10-13, 2019. 2019, pp. 90–97.
- Lylia Alouache et al. “Survey on IoV routing protocols: Se- curity and network architecture”. In: International Journal of Communication Systems 32.2 (2019), pp. 38–49.
- Antonio Di Maio et al. “Enabling SDN in VANETs: What is the Impact on Security?” In: Sensors 16.12 (2016).
- L Alouache et al. “Toward a hybrid SDN architecture for V2V communication in IoV environment”. In: 2018 Fifth In- ternational Conference on Software Defined Systems (SDS). Barcelona, Spain, 2018, pp. 93–99.
- P. Baskett et al. “SDNAN: Software-Defined Networking in Ad-Hoc Networks of Smartphones”. In: 2013 IEEE 10th Con- sumer Communications and Networking Conference (CCNC). Las Vegas, NV, USA, 2013, pp. 861–862.
- M. Azees, P. Vijayakumar, and L. Jegatha Deborah. “Com- prehensive survey on security services in vehicular ad-hoc networks”. In: IET Intelligent Transport Systems 10.6 (2016), pp. 379–388.
- M. Liyanage et al. “Opportunities and Challenges of Software-Defined Mobile Networks in Network Security”. In: IEEE Security Privacy 14.4 (2016), pp. 34–44.
- H. Vasudev and D. Das. “A trust based secure communication for software defined VANETs”. In: 2018 International Con- ference on Information Networking (ICOIN). 2018, pp. 316– 321.
- D Zhang et al. “Software-defined Vehicular Ad Hoc Net- works with Trust Management”. In: the 6th ACM Symposium on Development and Analysis of Intelligent Vehicular Net- works and Applications. DIVANet ’16. Malta, Malta: ACM, 2016, pp. 41–49. isbn: 978-1-4503-4506-4.
- Seyed Soleymani et al. “Trust Management in Vehicular Ad- Hoc Network: a Systematic Review”. In: 2015 (2015).
- N. Bimeyer et al. “Assessment of node trustworthiness in VANETs using data plausibility checks with particle filters”. In: 2012 IEEE Vehicular Networking Conference (VNC). 2012, pp. 78–85.
- Junhai Luo, Xue Liu, and Mingyu Fan. “A Trust model based on fuzzy recommendation for Mobile Ad-hoc Networks”. In: Computer Networks 53.14 (2009), pp. 2396 –2407. issn: 1389-1286.
- Jim Schaad. Use of the Advanced Encryption Standard (AES) Encryption Algorithm in Cryptographic Message Syntax (CMS). RFC 3565. 2003. url: https://rfc-editor.org/ rfc/rfc3565.txt.
- Margaret Rouse. Challenge – Response Authentication Def- inition: What does Challenge – Response Authentication mean? https : / / searchsecurity . techtarget . com / definition/challenge- response- system. Accessed: 2018-05-30.
- Teerawat Issariyakul and Ekram Hossain. Introduction to Net- work Simulator NS2. 1st ed. Springer Publishing Company, Incorporated, 2008. isbn: 0387717595, 9780387717593.
- Jrme Hrri et al. “Vehicular mobility simulation with Vanet-MobiSim”. In: SIMULATION 87.4 (2011), pp. 275–300.
- Kazuki Iehira, Hiroyuki Inooue, "Detection Method and Mitigation of Server-Spoofing Attacks on SOME/IP at the Service Discovery Phase", Advances in Science, Technology and Engineering Systems Journal, vol. 11, no. 1, pp. 25–32, 2026. doi: 10.25046/aj110103
- Shaista Ashraf Farooqi, Aedah Abd Rahman, Amna Saad, "Federated Learning with Differential Privacy and Blockchain for Security and Privacy in IoMT A Theoretical Comparison and Review", Advances in Science, Technology and Engineering Systems Journal, vol. 10, no. 6, pp. 65–76, 2025. doi: 10.25046/aj100606
- Robinson Lawrance, Nishith Kumar Reddy Gorla, "System-Level Test Case Design for Field Reliability Alignment in Complex Products", Advances in Science, Technology and Engineering Systems Journal, vol. 10, no. 6, pp. 55–64, 2025. doi: 10.25046/aj100605
- Vinton Morris, Kevin Kornegay, Joy Falaye, Sean Richardson, Marcial Tienteu, Loic Jephson Djomo Tchuenkou, "TIMeFoRCE: An Identity and Access Management Framework for IoT Devices in A Zero Trust Architecture", Advances in Science, Technology and Engineering Systems Journal, vol. 10, no. 6, pp. 1–22, 2025. doi: 10.25046/aj100601
- Mahdi Madani, El-Bay Bourennane, Safwan El Assad, "Hardware and Secure Implementation of Enhanced ZUC Steam Cipher Based on Chaotic Dynamic S-Box", Advances in Science, Technology and Engineering Systems Journal, vol. 10, no. 1, pp. 37–47, 2025. doi: 10.25046/aj100105
- Viktor Denkovski, Irena Stojmenovska, Goce Gavrilov, Vladimir Radevski, Vladimir Trajkovik, "Exploring Current Challenges on Security and Privacy in an Operational eHealth Information System", Advances in Science, Technology and Engineering Systems Journal, vol. 9, no. 2, pp. 45–54, 2024. doi: 10.25046/aj090206
- Fazalur Rehman, Safwan Hashmi, "Enhancing Cloud Security: A Comprehensive Framework for Real-Time Detection, Analysis and Cyber Threat Intelligence Sharing", Advances in Science, Technology and Engineering Systems Journal, vol. 8, no. 6, pp. 107–119, 2023. doi: 10.25046/aj080612
- Nizar Sakli, Chokri Baccouch, Hedia Bellali, Ahmed Zouinkhi, Mustapha Najjari, "IoT System and Deep Learning Model to Predict Cardiovascular Disease Based on ECG Signal", Advances in Science, Technology and Engineering Systems Journal, vol. 8, no. 6, pp. 08–18, 2023. doi: 10.25046/aj080602
- Hiroki Iwanaga, "Photoluminescence Properties of Eu(III) Complexes with Two Different Phosphine Oxide Structures and Their Potential uses in Micro-LEDs, Security, and Sensing Devices: A Review", Advances in Science, Technology and Engineering Systems Journal, vol. 8, no. 3, pp. 154–160, 2023. doi: 10.25046/aj080317
- Saidi Mohamed, Habib Cherif, Othman Hasnaoui, Jamel Belhadj, "Design and Comparative Analysis of Hybrid Energy Systems for Grid-Connected and Standalone Applications in Tunisia: Case Study of Audiovisual Chain", Advances in Science, Technology and Engineering Systems Journal, vol. 8, no. 3, pp. 144–153, 2023. doi: 10.25046/aj080316
- Mario Cuomo, Federica Massimi, Francesco Benedetto, "Detecting CTC Attack in IoMT Communications using Deep Learning Approach", Advances in Science, Technology and Engineering Systems Journal, vol. 8, no. 2, pp. 130–138, 2023. doi: 10.25046/aj080215
- Richard Romero Izurieta, Segundo Moisés Toapanta Toapanta, Luis Jhony Caucha Morales, María Mercedes Baño Hifóng, Eriannys Zharayth Gómez Díaz, Oscar Marcelo Zambrano Vizuete, Luis Enrique Mafla Gallegos, José Antonio Orizaga Trejo, "Prototype to Identify the Capacity in Cybersecurity Management for a Public Organization", Advances in Science, Technology and Engineering Systems Journal, vol. 8, no. 1, pp. 108–115, 2023. doi: 10.25046/aj080113
- Segundo Moisés Toapanta Toapanta, Rodrigo Humberto Del Pozo Durango, Luis Enrique Mafla Gallegos, Eriannys Zharayth Gómez Díaz, Yngrid Josefina Melo Quintana, Joan Noheli Miranda Jimenez, Ma. Roció Maciel Arellano, José Antonio Orizaga Trejo, "Prototype to Mitigate the Risks, Vulnerabilities and Threats of Information to Ensure Data Integrity", Advances in Science, Technology and Engineering Systems Journal, vol. 7, no. 6, pp. 139–150, 2022. doi: 10.25046/aj070614
- Tarek Nouioua, Ahmed Hafid Belbachir, "The Security of Information Systems and Image Processing Supported by the Quantum Computer: A review", Advances in Science, Technology and Engineering Systems Journal, vol. 7, no. 6, pp. 77–86, 2022. doi: 10.25046/aj070609
- Marzouk Hassan, Abdelmajid Badri, Aicha Sahel, "A Self-Adaptive Routing Algorithm for Real-Time Video Transmission in VANETs", Advances in Science, Technology and Engineering Systems Journal, vol. 7, no. 5, pp. 91–101, 2022. doi: 10.25046/aj070512
- Muhammad Musleh Uddin, Kazi Rafiqul Islam, Md. Monirul Kabir, "An Improved Model to Analyze the Impact of Cyber-Attacks on Power Systems", Advances in Science, Technology and Engineering Systems Journal, vol. 7, no. 5, pp. 27–34, 2022. doi: 10.25046/aj070504
- Kamil Halouzka, Ladislav Burita, Aneta Coufalikova, Pavel Kozak, Petr Františ, "A Comparison of Cyber Security Reports for 2020 of Central European Countries", Advances in Science, Technology and Engineering Systems Journal, vol. 7, no. 4, pp. 105–113, 2022. doi: 10.25046/aj070414
- Tiny du Toit, Hennie Kruger, Lynette Drevin, Nicolaas Maree, "Deep Learning Affective Computing to Elicit Sentiment Towards Information Security Policies", Advances in Science, Technology and Engineering Systems Journal, vol. 7, no. 3, pp. 152–160, 2022. doi: 10.25046/aj070317
- Afsah Sharmin, Farhat Anwar, S M A Motakabber, Aisha Hassan Abdalla Hashim, "A Secure Trust Aware ACO-Based WSN Routing Protocol for IoT", Advances in Science, Technology and Engineering Systems Journal, vol. 7, no. 3, pp. 95–105, 2022. doi: 10.25046/aj070311
- Khosro Salmani, Ken Barker, "Leakage-abuse Attacks Against Forward Private Searchable Symmetric Encryption", Advances in Science, Technology and Engineering Systems Journal, vol. 7, no. 2, pp. 156–170, 2022. doi: 10.25046/aj070216
- Clémentine Gritti, Hao Li, "Efficient Publicly Verifiable Proofs of Data Replication and Retrievability Applicable for Cloud Storage", Advances in Science, Technology and Engineering Systems Journal, vol. 7, no. 1, pp. 107–124, 2022. doi: 10.25046/aj070111
- Kartit Zaid, Diouri Ouafaa, "Taxonomy of Security Techniques for Routing Protocols in Mobile Ad-hoc Networks", Advances in Science, Technology and Engineering Systems Journal, vol. 7, no. 2, pp. 25–31, 2022. doi: 10.25046/aj070203
- Janusz Gurzynski, Lukasz Kajda, Marcin Tarasiuk, Tomasz Samotyjak, Zbigniew Stachowicz, Slawomir Kownacki, "Control and Monitoring Systems in Medium Voltage Distribution Networks in Poland – Current Status and Directions of Development", Advances in Science, Technology and Engineering Systems Journal, vol. 6, no. 6, pp. 112–118, 2021. doi: 10.25046/aj060615
- Boris Kontsevoi, Sergei Terekhov, "TETRA™ Techniques to Assess and Manage the Software Technical Debt", Advances in Science, Technology and Engineering Systems Journal, vol. 6, no. 5, pp. 303–309, 2021. doi: 10.25046/aj060534
- Osaretin Eboya, Julia Binti Juremi, "iDRP Framework: An Intelligent Malware Exploration Framework for Big Data and Internet of Things (IoT) Ecosystem", Advances in Science, Technology and Engineering Systems Journal, vol. 6, no. 5, pp. 185–202, 2021. doi: 10.25046/aj060521
- Maroua Barha, Soumaia Hmimou, Mounir Ait Kerroum, Hamid Ait Lemqeddem, "The Internal Reliability of a Questionnaire on the Impact of Enterprise Resource Planning on the Performance of Moroccan Companies", Advances in Science, Technology and Engineering Systems Journal, vol. 6, no. 5, pp. 59–64, 2021. doi: 10.25046/aj060508
- Jianhua Yang, Lixin Wang, Yien Wang, "Enhance Student Learning Experience in Cybersecurity Education by Designing Hands-on Labs on Stepping-stone Intrusion Detection", Advances in Science, Technology and Engineering Systems Journal, vol. 6, no. 4, pp. 355–367, 2021. doi: 10.25046/aj060440
- Yanshuo Wang, Jim (Jinming) Yang, Ngandu M. Mbiye, "Effectiveness and Suitability of the Automotive EHPS Software Reliability and Testing", Advances in Science, Technology and Engineering Systems Journal, vol. 6, no. 3, pp. 205–212, 2021. doi: 10.25046/aj060323
- Julies David Bryan, Tranos Zuva, "A Review on TAM and TOE Framework Progression and How These Models Integrate", Advances in Science, Technology and Engineering Systems Journal, vol. 6, no. 3, pp. 137–145, 2021. doi: 10.25046/aj060316
- Chibuzo Victor Ikwuagwu, Ikechukwu Emmanuel Okoh, Stephen Aroh Ajah, Cosmas Uchenna Ogbuka, Godwin Ogechi Unachukwu, Emenike Chinedozi Ejiogu, "Development of Electric Power Availability Recorder for Accurate Energy Billing of Unmetered Facilities", Advances in Science, Technology and Engineering Systems Journal, vol. 6, no. 3, pp. 7–14, 2021. doi: 10.25046/aj060302
- Anh Nguyen-Duc, Manh-Viet Do, Quan Luong-Hong, Kiem Nguyen-Khac, Hoang Truong-Anh, "On the Combination of Static Analysis for Software Security Assessment – A Case Study of an Open-Source e-Government Project", Advances in Science, Technology and Engineering Systems Journal, vol. 6, no. 2, pp. 921–932, 2021. doi: 10.25046/aj0602105
- Bismark Tei Asare, Kester Quist-Aphetsi, Laurent Nana, "Node-Node Data Exchange in IoT Devices Using Twofish and DHE", Advances in Science, Technology and Engineering Systems Journal, vol. 6, no. 2, pp. 622–628, 2021. doi: 10.25046/aj060271
- Zarina Din, Dian Indrayani Jambari, Maryati Mohd Yusof, Jamaiah Yahaya, "Challenges in IoT Technology Adoption into Information System Security Management of Smart Cities: A Review", Advances in Science, Technology and Engineering Systems Journal, vol. 6, no. 2, pp. 99–112, 2021. doi: 10.25046/aj060213
- Saliha Assoul, Anass Rabii, Ounsa Roudiès, "An Operational Responsibility and Task Monitoring Method: A Data Breach Case Study", Advances in Science, Technology and Engineering Systems Journal, vol. 6, no. 1, pp. 1157–1163, 2021. doi: 10.25046/aj0601130
- Karol Rástočný, Juraj Ždánsky, Jozef Hrbček, "Using a safety PLC to Implement the Safety Function", Advances in Science, Technology and Engineering Systems Journal, vol. 6, no. 1, pp. 1072–1078, 2021. doi: 10.25046/aj0601119
- Pham Hong Thinh, Tran Thi Thanh Huyen, Nguyen Ngoc Quang, Pham Ngoc Nam, Truong Cong Thang, Nguyen Viet Hung, Truong Thu Huong, "QoE-aware Bandwidth Allocation for Multiple Video Streaming Players over HTTP and SDN", Advances in Science, Technology and Engineering Systems Journal, vol. 6, no. 1, pp. 184–199, 2021. doi: 10.25046/aj060121
- Devika K N, Ramesh Bhakthavatchalu, "Modified Blockchain based Hardware Paradigm for Data Provenance in Academia", Advances in Science, Technology and Engineering Systems Journal, vol. 6, no. 1, pp. 66–77, 2021. doi: 10.25046/aj060108
- Pranay Bhardwaj, Carla Purdy, Nawar Obeidat, "A Novel Way to Design ADS-B using UML and TLA+ with Security as a Focus", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 6, pp. 1657–1665, 2020. doi: 10.25046/aj0506197
- Hesham Aly El Zouka, Mustafa Mohamed Hosni, "Time Granularity-based Privacy Protection for Cloud Metering Systems", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 6, pp. 1278–1285, 2020. doi: 10.25046/aj0506152
- Nour Najeeb Abdalkareem Qubbaj, Anas Abu Taleb, Walid Salameh, "LEACH Based Protocols: A Survey", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 6, pp. 1258–1266, 2020. doi: 10.25046/aj0506150
- Boughanja Manale, Tomader Mazri, "5G, Vehicle to Everything Communication: Opportunities, Constraints and Future Directions", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 6, pp. 1089–1095, 2020. doi: 10.25046/aj0506132
- Abdulla Obaid Al Zaabi, Chan Yeob Yeun, Ernesto Damiani, Gaemyoung, "An Enhanced Conceptual Security Model for Autonomous Vehicles", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 6, pp. 853–864, 2020. doi: 10.25046/aj0506102
- Jim Scheibmeir, Yashwant Malaiya, "Multi-Model Security and Social Media Analytics of the Digital Twin", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 6, pp. 323–330, 2020. doi: 10.25046/aj050639
- Ioana Marcu, Ana-Maria Drăgulinescu, Carmen Florea, Cristina Bălăceanu, Marius Alexandru Dobrea, George Suciu, "Agricultural Data Fusion for SmartAgro Telemetry System", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 5, pp. 1266–1272, 2020. doi: 10.25046/aj0505152
- Malik Khlaif Gharaibeh, Natheer Khlaif Gharaibeh, "An Empirical Study on Factors Influencing the Intention to use Mobile Learning", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 5, pp. 1261–1265, 2020. doi: 10.25046/aj0505151
- Emad Kareem Mutar, "Matrix-based Minimal Cut Method and Applications to System Reliability", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 5, pp. 991–996, 2020. doi: 10.25046/aj0505121
- Gautama Wijaya, Nico Surantha, "Multi-layered Security Design and Evaluation for Cloud-based Web Application: Case Study of Human Resource Management System", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 5, pp. 674–679, 2020. doi: 10.25046/aj050583
- Mika Karjalainen, Tero Kokkonen, "Review of Pedagogical Principles of Cyber Security Exercises", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 5, pp. 592–600, 2020. doi: 10.25046/aj050572
- Lambe Mutalub Adesina, Ademola Abdulkareem, James Katende, Olaosebikan Fakolujo, "Newton-Raphson Algorithm as a Power Utility Tool for Network Stability", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 5, pp. 444–451, 2020. doi: 10.25046/aj050555
- Sugiarto Hartono, Meyliana, Ahmad Nizar Hidayanto, Harjanto Prabowo, "Component of Trust for Developing Crowdwork System: A Systematic Literature Review", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 5, pp. 356–363, 2020. doi: 10.25046/aj050544
- Liana Khamis Qabajeh, Mohammad Moustafa Qabajeh, "Detailed Security Evaluation of ARANz, ARAN and AODV Protocols", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 5, pp. 176–192, 2020. doi: 10.25046/aj050523
- Pham Minh Nam, Phu Tran Tin, "Analysis of Security-Reliability Trade-off for Multi-hop Cognitive Relaying Protocol with TAS/SC Technique", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 5, pp. 54–62, 2020. doi: 10.25046/aj050508
- Adamu Abdullahi Garba, Maheyzah Muhamad Siraj, Siti Hajar Othman, "An Explanatory Review on Cybersecurity Capability Maturity Models", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 4, pp. 762–769, 2020. doi: 10.25046/aj050490
- Sultana Parween, Syed Zeeshan Hussain, "A Review on Cross-Layer Design Approach in WSN by Different Techniques", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 4, pp. 741–754, 2020. doi: 10.25046/aj050488
- Vu Nguyen Hoa Hong, Luong Tuan Anh, "Development Trends of Smart Cities in the Future – Potential Security Risks and Responsive Solutions", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 4, pp. 548–556, 2020. doi: 10.25046/aj050465
- Chafaa Hamrouni, Slim Chaoui, "Contribution in Private Cloud Computing Development based on Study and KPI Analysis", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 4, pp. 105–108, 2020. doi: 10.25046/aj050414
- Maximo Giovani Tanzado Espinoza, Joseline Roxana Neira Melendrez, Luis Antonio Neira Clemente, "A Survey and an IoT Cybersecurity Recommendation for Public and Private Hospitals in Ecuador", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 3, pp. 518–528, 2020. doi: 10.25046/aj050364
- Mainar Swari Mahardika, Achmad Nizar Hidayanto, Putu Agya Paramartha, Louis Dwysevrey Ompusunggu, Rahmatul Mahdalina, Farid Affan, "Measurement of Employee Awareness Levels for Information Security at the Center of Analysis and Information Services Judicial Commission Republic of Indonesia", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 3, pp. 501–509, 2020. doi: 10.25046/aj050362
- Fatima Lakrami, Najib El Kamoun, Hind Sounni, Ouidad Albouidya, Khalid Zine-Dine, "The Design of an Experimental Model for Deploying Home Area Network in Smart Grid", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 3, pp. 419–431, 2020. doi: 10.25046/aj050353
- Suchitra Abel, Yenchih Tang, Jake Singh, Ethan Paek, "Applications of Causal Modeling in Cybersecurity: An Exploratory Approach", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 3, pp. 380–387, 2020. doi: 10.25046/aj050349
- Gillala Rekha, Shaveta Malik, Amit Kumar Tyagi, Meghna Manoj Nair, "Intrusion Detection in Cyber Security: Role of Machine Learning and Data Mining in Cyber Security", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 3, pp. 72–81, 2020. doi: 10.25046/aj050310
- Mutuma Ichaba, Felix Musau, Simon Nyaga Mwendia, "Performance Effects of Algorithmic Elements in Selected MANETs Routing Protocols", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 3, pp. 62–71, 2020. doi: 10.25046/aj050309
- Segundo Moisés Toapanta Toapanta, Daniela Monserrate Moreira Gamboa, Luis Enrique Mafla Gallegos, "Analysis of the Blockchain for Adoption in Electronic Commerce Management in Ecuador", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 2, pp. 762–768, 2020. doi: 10.25046/aj050295
- Segundo Moisés Toapanta Toapanta, Andrés Aurelio García Henriquez, Luis Enrique Mafla Gallegos, "Analysis of Vulnerabilities, Risks and Threats in the Process of Quota Allocation for the State University of Ecuador", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 2, pp. 673–682, 2020. doi: 10.25046/aj050283
- Yakob Utama Chandra, Bahtiar Saleh Abbas, Agung Trisetyarso, Wayan Suparta, Chul-Ho Kang, "Comparison Analysis between Mobile Banking and Mobile Payment as Determinant Factors of Customer Privacy", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 2, pp. 469–475, 2020. doi: 10.25046/aj050260
- Ranyelson Neres Carvalho, Lucas R. Costa, Jacir Luiz Bordim, Eduardo Adilo Pelinson Alchieri, "Enhancing an SDN Architecture with DoS Attack Detection Mechanisms", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 2, pp. 215–224, 2020. doi: 10.25046/aj050228
- Segundo Moisés Toapanta Toapanta, José David López Cobeña, Luis Enrique Mafla Gallegos, "Analysis of Cyberattacks in Public Organizations in Latin America", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 2, pp. 116–125, 2020. doi: 10.25046/aj050215
- Karim El bouchti, Soumia Ziti, Fouzia Omary, Nassim Kharmoum, "New Solution Implementation to Protect Encryption Keys Inside the Database Management System", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 2, pp. 87–94, 2020. doi: 10.25046/aj050211
- José Alomía-Lucero, Jorge Castro-Bedriñana, Doris Chirinos-Peinado, "Rooftop Urban Agriculture Model with Two Tomato Varieties (Lycopersicum esculentum Mill) and Toppings in the High Jungle – Peru", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 1, pp. 446–450, 2020. doi: 10.25046/aj050157
- Amit Kumar Tyagi, A. Mohan Krishna, Shaveta Malik, Meghna Manoj Nair, Sreenath Niladhuri, "Trust and Reputation Mechanisms in Vehicular Ad-Hoc Networks: A Systematic Review", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 1, pp. 387–402, 2020. doi: 10.25046/aj050150
- Ivan Aleksandrovich Tarkhanov, Galina Pavlovna Akimova, Matvey Aleksandrovich Pashkin, Aleksander Vladimirovich Soloviev, "Modelling the Methodology to Assess the Effectiveness of Distributed Information Systems", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 1, pp. 86–92, 2020. doi: 10.25046/aj050111
- Amina Bengag, Asmae Bengag, Mohamed Elboukhari, "Routing Protocols for VANETs: A Taxonomy, Evaluation and Analysis", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 1, pp. 77–85, 2020. doi: 10.25046/aj050110
- Aref Hassan Kurd Ali, Halikul Lenando, Mohamad Alrfaay, Slim Chaoui, Haithem Ben Chikha, Akram Ajouli, "Performance Analysis of Routing Protocols in Resource-Constrained Opportunistic Networks", Advances in Science, Technology and Engineering Systems Journal, vol. 4, no. 6, pp. 402–413, 2019. doi: 10.25046/aj040651
- Amine Kardi, Rachid Zagrouba, "Attacks classification and security mechanisms in Wireless Sensor Networks", Advances in Science, Technology and Engineering Systems Journal, vol. 4, no. 6, pp. 229–243, 2019. doi: 10.25046/aj040630
- Evan Hurwitz, Chigozie Orji, "Multi Biometric Thermal Face Recognition Using FWT and LDA Feature Extraction Methods with RBM DBN and FFNN Classifier Algorithms", Advances in Science, Technology and Engineering Systems Journal, vol. 4, no. 6, pp. 67–90, 2019. doi: 10.25046/aj040609
- Allae Erraissi, Abdessamad Belangour, "A Big Data Security Layer Meta-Model Proposition", Advances in Science, Technology and Engineering Systems Journal, vol. 4, no. 5, pp. 409–418, 2019. doi: 10.25046/aj040553
- Segundo Moisés Toapanta Toapanta, Steven Xavier Romo Sañicela, Danny Wilfrido Barona Valencia, Luis Enrique Mafla Gallegos, "Analysis of Information Security for a Voting Process for Sectional Governments in Ecuador", Advances in Science, Technology and Engineering Systems Journal, vol. 4, no. 5, pp. 352–359, 2019. doi: 10.25046/aj040546
- Alghamdi Abdullah, Mohammed Thanoon, Anwar Alsulami, "Toward a Smart Campus Using IoT: Framework for Safety and Security System on a University Campus", Advances in Science, Technology and Engineering Systems Journal, vol. 4, no. 5, pp. 97–103, 2019. doi: 10.25046/aj040512
- Segundo Moisés Toapanta Toapanta, Allan Fabricio German Diaz, Darío Fernando Huilcapi Subia, Luis Enrique Mafla Gallegos, "Proposal for a Security Model for a Popular Voting System Process in Latin America", Advances in Science, Technology and Engineering Systems Journal, vol. 4, no. 5, pp. 53–60, 2019. doi: 10.25046/aj040507
- Segundo Moisés Toapanta Toapanta, Gabriel Enrique Valenzuela Ramos, Félix Gustavo Mendoza Quimi, Luis Enrique Mafla Gallegos, "Prototype of a Security Architecture for a System of Electronic Voting for the Ecuador", Advances in Science, Technology and Engineering Systems Journal, vol. 4, no. 4, pp. 292–299, 2019. doi: 10.25046/aj040437
- Segundo Moisés Toapanta Toapanta, Andrés Javier Bravo Jácome, Maximo Giovanny Tandazo Espinoza, Luis Enrique Mafla Gallegos, "An Immutable Algorithm Approach to Improve the Information Security of a Process for a Public Organization of Ecuador", Advances in Science, Technology and Engineering Systems Journal, vol. 4, no. 3, pp. 25–30, 2019. doi: 10.25046/aj040304
- Robert M. Beswick, "Computer Security as an Engineering Practice: A System Engineering Discussion", Advances in Science, Technology and Engineering Systems Journal, vol. 4, no. 2, pp. 357–369, 2019. doi: 10.25046/aj040245
- Abdullah Al-Shaalan, "Technical and Economic Merits Resulting from Power Systems Interconnection", Advances in Science, Technology and Engineering Systems Journal, vol. 4, no. 2, pp. 34–39, 2019. doi: 10.25046/aj040205
- Shruthi Narayanaswamy, Anitha Vijaya Kumar, "Application Layer Security Authentication Protocols for the Internet of Things: A Survey", Advances in Science, Technology and Engineering Systems Journal, vol. 4, no. 1, pp. 317–328, 2019. doi: 10.25046/aj040131
- Jonathan Lockhart, Carla Purdy, Philip Wilsey, "Critical Embedded Systems Development Using Formal Methods and Statistical Reliability Metrics", Advances in Science, Technology and Engineering Systems Journal, vol. 4, no. 1, pp. 231–247, 2019. doi: 10.25046/aj040123
- Nosiri Onyebuchi Chikezie, Onyenwe Ezinne Maureen, Ekwueme Emmanuel Uchenna, "Fuzzy Logic Implementation for Enhanced WCDMA Network Using Selected KPIs", Advances in Science, Technology and Engineering Systems Journal, vol. 4, no. 1, pp. 114–124, 2019. doi: 10.25046/aj040112
- Lin Dong, Akira Rinoshika, "Analysis and Methods on The Framework and Security Issues for Connected Vehicle Cloud", Advances in Science, Technology and Engineering Systems Journal, vol. 3, no. 6, pp. 105–110, 2018. doi: 10.25046/aj030611
- Uche Magnus Mbanaso, Gloria A Chukwudebe, "Holistic Access Control and Privacy Infrastructure in Distributed Environment", Advances in Science, Technology and Engineering Systems Journal, vol. 3, no. 6, pp. 46–55, 2018. doi: 10.25046/aj030604
- Mohamed Adel Serhani, Hadeel Al Kassabi, Ikbal Taleb, "Towards an Efficient Federated Cloud Service Selection to Support Workflow Big Data Requirements", Advances in Science, Technology and Engineering Systems Journal, vol. 3, no. 5, pp. 235–247, 2018. doi: 10.25046/aj030529
- Luis Guillen, Satoru Izumi, Toru Abe, Hiroaki Muraoka, Takuo Suganuma, "SDN-based Network Control Method for Distributed Storage Systems", Advances in Science, Technology and Engineering Systems Journal, vol. 3, no. 5, pp. 140–151, 2018. doi: 10.25046/aj030518
- Abhitosh Vais, Sonja Sioncke, Jacopo Franco, Vamsi Putcha, Laura Nyns, Arturo Sibaja-Hernandez, Rita Rooyackers, Sergio Calderon Ardila, Valentina Spampinato, Alexis Franquet, Jan Maes, Qi Xie, Michael Givens, Fu Tang, Xiang Jiang, Marc Heyns, Dimitri Linten, Jerome Mitard, Aaron Thean, Dan Mocuta, Nadine Collaert, "On The Development of a Reliable Gate Stack for Future Technology Nodes Based on III-V Materials", Advances in Science, Technology and Engineering Systems Journal, vol. 3, no. 5, pp. 36–44, 2018. doi: 10.25046/aj030506
- Md. Asadur Rahman, Md. Shajedul Islam Sohag, Rasel Ahmmed, Md. Mahmudul Haque, Anika Anjum, "Defined Limited Fractional Channel Scheme for Call Admission Control by Two-Dimensional Markov Process based Statistical Modeling", Advances in Science, Technology and Engineering Systems Journal, vol. 3, no. 4, pp. 295–307, 2018. doi: 10.25046/aj030430
- Akbor Aziz Susom, "Effectiveness of Routing Protocols for Different Networking Scenarios", Advances in Science, Technology and Engineering Systems Journal, vol. 3, no. 4, pp. 112–121, 2018. doi: 10.25046/aj030412
- Ola Surakhi, Mohammad Khanafseh, Yasser Jaffal, "An enhanced Biometric-based Face Recognition System using Genetic and CRO Algorithms", Advances in Science, Technology and Engineering Systems Journal, vol. 3, no. 3, pp. 116–124, 2018. doi: 10.25046/aj030316
- Abul Kalam Azad, Md. Yamin Mollah, "EAES: Extended Advanced Encryption Standard with Extended Security", Advances in Science, Technology and Engineering Systems Journal, vol. 3, no. 3, pp. 51–56, 2018. doi: 10.25046/aj030307
- Dhiman Chowdhury, Mrinmoy Sarkar, Mohammad Zakaria Haider, "A Cyber-Vigilance System for Anti-Terrorist Drives Based on an Unmanned Aerial Vehicular Networking Signal Jammer for Specific Territorial Security", Advances in Science, Technology and Engineering Systems Journal, vol. 3, no. 3, pp. 43–50, 2018. doi: 10.25046/aj030306
- Nicola Fabiano, "The Internet of Things ecosystem: the blockchain and data protection issues", Advances in Science, Technology and Engineering Systems Journal, vol. 3, no. 2, pp. 1–7, 2018. doi: 10.25046/aj030201
- Asma Meddeb, Hajer Jmii, Souad Chebbi, "Security Analysis and the Contribution of UPFC for Improving Voltage Stability", Advances in Science, Technology and Engineering Systems Journal, vol. 3, no. 1, pp. 404–411, 2018. doi: 10.25046/aj030149
- Luca Dariz, Gianpiero Costantino, Massimiliano Ruggeri, Fabio Martinelli, "A Joint Safety and Security Analysis of message protection for CAN bus protocol", Advances in Science, Technology and Engineering Systems Journal, vol. 3, no. 1, pp. 384–393, 2018. doi: 10.25046/aj030147
- Anass Sedrati, Abdellatif Mezrioui, "A Survey of Security Challenges in Internet of Things", Advances in Science, Technology and Engineering Systems Journal, vol. 3, no. 1, pp. 274–280, 2018. doi: 10.25046/aj030133
