An Integrated & Secure System for Wearable Devices
Volume 3, Issue 6, Page No 432-437, 2018
Author’s Name: Callum Owen-Bridge1, Stewart Blakeway1,2, Emanuele Lindo Secco1,a)
View Affiliations
1Robotic Laboratory, Department of Mathematics and Computer Science, Liverpool Hope University
2Faculty of Arts, Science and Technology, Wrexham Glynd?r University
a)Author to whom correspondence should be addressed. E-mail: seccoe@hope.ac.uk
Adv. Sci. Technol. Eng. Syst. J. 3(6), 432-437 (2018); ![]() DOI: 10.25046/aj030651
DOI: 10.25046/aj030651
Keywords: E-Health, Wearable sensors, Human Health Monitoring
Export Citations
Health services are under increasing pressure to reduce large waiting times for appointments. The delayed diagnosis of a human illnesses could have profound consequences for the patient. The large waiting times may be attributed to lack of data, the accuracy of the data or the timeliness of the availability of the data. In addition to this people often priorities their busy lives over their health. Other factors that affect delayed diagnosis of patients could be attributed to ill-health and the difficulty in the patient visiting the health-care practitioner, this is more evident in elderly patients that may have suffered a deterioration of their health. To overcome these obstacles eHealth systems could be put in place to facilitate the transmission of real-time and accurate data regarding a patient’s health directly to secure database that can be accessed by authorized practitioners. This paper outlines the use of eHealth (electronic health) to improve health care services which makes use of a wearable set of secure sensors and a secure database that is accessible using a web application. The proposed wearable system records and stores encrypted data which is related to the body’s physical parameters. Then, the encrypted data are transmitted using wireless technologies from the wearable device to a secure relational multi-user database using a protected protocol. The data can be accessed by the patient and professionals, such as general practitioners, using a web interface once authentication has taken place. This secure wearable architecture alleviates the problems of the lack of data, the inaccuracy of data and the timeliness of data by recording vital body parameters throughout the day and by sending real-time live data to a system that can be immediately accessed by the practitioner. The system also allows for the automatic analysis of data and presentation of the data using graphs which could aid the practitioner in determining patterns in the patients’ health statistics.
Received: 13 September 2018, Accepted: 27 November 2018, Published Online: 19 December 2018
1. Introduction
Health care services are struggling to diagnose people accurately and quickly, due to lack of data. Humans are becoming less proactive and unaware of their own health. Many people struggle to allocate time to see a health care professional due to their lifestyle and/or physical health.
This research presents a secure medical wearable device for patients with health issues, to help support in the monitoring of physical parameters in the daily life and in the Ambient Assisted Living (AAL) context. This paper focuses on the creation and implementation of a hardware device with sensors that captures patients health data and the development of secure software for data storage which can be accessed remotely by multiple authorised users.
The research undertaken details how the hardware was implemented, the software used to control the device, how data is secured before being transmitted over unsecured wireless media to a secure multiple-access relational database. This papers also discusses eHealth, health of the population, security, privacy and legal issues surrounding medical wearable devices. The result of this research shows that there are high expectations and standards for eHealth strategies. Providing that security and privacy mechanisms are put in place, there seems high motivation in the adoption of such systems.
The construction of the secure medical wearable device and development of the secure database with the front-end website application is outlined in the materials and methods section. The results of this research show that secure wearable devices for this purpose can be successful and the results of the application of these devices is discussed in the discussion and conclusion sections.
1.1. Population Health
It is reported that across the globe the causes of death in 2015, are related to cardiovascular and respiratory systems, these figures have risen since the year 2000 [1], for example, ischaemia heart disease had risen by 2 million in 2015 [1]. In 2015, diabetes mellitus caused around 1.7 million deaths and became one of many new causes of death and diseases related to the respiratory system caused around 1.8 million deaths [1].
A medical device which could record body parameters especially those parameters involving the cardiovascular system and respiratory system would be beneficial in monitoring the health of the population and improving healthcare. The device could provide crucial data to help reduce illness and diseases. The system could also be used to identify detestation of health so that preventative measure can be put in place.
1.2. eHealth
The eHealth field involves public health and medical informatics; it describes the enhancement of health services through use of technology [2].
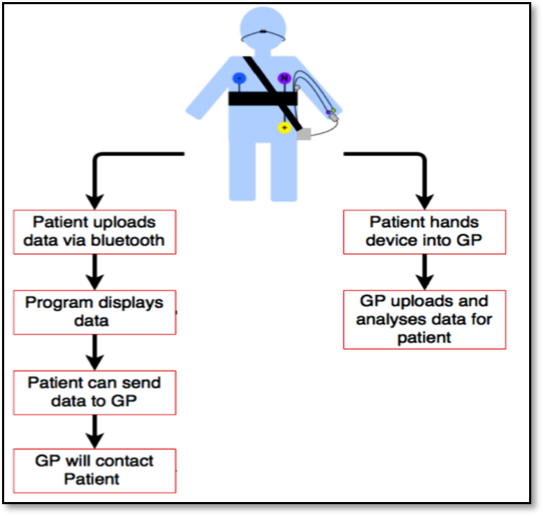 Figure 1: Functional overview of the Health Monitoring System
Figure 1: Functional overview of the Health Monitoring System
Research has shown that eHealth has provided improved support for patients whilst reducing the overall financial cost and improving the efficiency of healthcare. Portable health monitors have shown to increase self-care, improve quality of life and assist in providing better medical care [3]. An eHealth system can provide multiple benefits to the patient. The reasons for this are:
- Increasing the efficiency of health care by improving communication between the healthcare professionals and the patients. Prevention of data redundancy, increased availability of data and improved accuracy of the data play an important role in the correct diagnosis of patients.
- eHealth strategies should be evaluated scientifically for its effectiveness and efficiency [4] which allow for improved services to the patient.
- eHealth improves time efficiency of health care, servicessuch as telehealth save time because appointments can be made online or consultations could take place using video streaming services over the internet.
- eHealth also allows people to be more aware of their health and allows individuals to easily share data with their health care provider. Which provides for more effective and efficient health care because patients can be diagnosed more quickly and accurately.
- An eHealth System can also reduce administration as the health data can be digitally securely before being shared. This reduces hard copies (paper) which could be stored insecurely or even lost.
- Moreover, electronic systems could have validation built in which may reduce some human administrative errors resulting in more accurate data.
- Patients that are concerned with the security or the privacy of their data can be assured that the data is governed by The EU General Data Protection Regulation.
- Software for such systems is becoming easier to use. The technology should be simple to use and user-friendly [5] for accessibility to the patient.
eHealth is a successful mechanism in solving many health care issues. These innovative solutions could also be invaluable for developing countries by reducing the administrative burden involved in providing health care.
The eHealth platform has shown to be a widely used health care scheme by many countries and the use of eHealth is increasing as more countries are adopting the scheme. Since 1990 there has been a steady adoption of eHealth [6], more recently application of eHealth has seen a dramatic increase. Health care professionals usually assess a patient’s condition at regular intervals, which results in discreet data. eHealth devices provide continuous data which gives a more complete medical history, this could help health care professionals make better informed decisions regarding treatments for patients. This is crucial as the patient could form new symptoms between the intervals the health care professional assesses the patient [7].
1.3. Security, Privacy and Legal considerations surrounding Medical Wearable Devices
There are security, privacy and legal issues surrounding eHealth wearable devices which must be addressed for the service to be viable. It is essential that the devices are kept secure because the recorded data hold personal information of patients. If security were compromised there could be catastrophic consequences, for example, the patient being incorrectly diagnosed or receiving incorrect treatment, which may result in the death of the patient. Of course, this is true of all systems that store patient data and procedures must be in place to secure these systems.
The proposed medical wearable device in this research does transmit data over an insecure wireless medium and this connection link could be eavesdropped [8], but this is unlikely because of the proximity of the transmitter and receiver and the likely distance the signal will travel from the low powered transmitter (theoretically the signal should be confined to about 10m). However, even with such a low risk of interception of data, steps are in place to ensure that the data is encrypted prior to transmission. The data are also stored in a secure database in encrypted form and can only be accessed by authorised personal using the authentication scheme.
Listed below are some security and privacy concerns with medical wearable devices:
- The device’s system is vulnerable to eavesdropping, denial of service, unauthorized access to the device and data mining [9].
- In line with GDRP (General Data Protection Regulation), only required data should be stored. In addition to this the data stored should not allow an adversary to determine the identity of the patient.
The use of authentication mechanisms prevents unauthorized access to the data, examples of these are usernames, digital signatures and challenge-response protocols [10].
The eHealth system proposed in this paper encrypts the data at the source before any transmission of data has occurred. The data is then transmitted wirelessly and stored in a secure database. The mechanism of how the data is stored uses unique identification numbers which hides identifiable patient data and prevents patient identification. There is an authentication scheme and an access control list policy which prevents anyone without the correct authentication credentials from accessing the database.
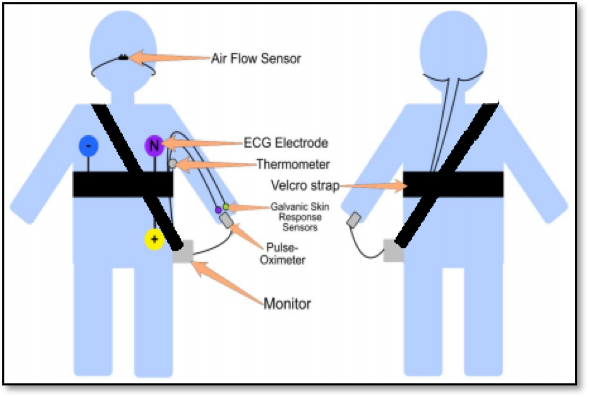 Figure 2 – Sensor configuration of the Health Monitoring System
Figure 2 – Sensor configuration of the Health Monitoring System
2. Materials & Methods
The overall system process shown in Figure 1 and the creation of the secure medical wearable device shown in Figure 2 and web application shown in Figure 4, will be outlined within this chapter. The goal was to create a secure medical wearable device for use on humans, to allow for independent health monitoring, health awareness, and improved health care, through use of eHealth.
2.1. Secure Medical Wearable Device
The wearable device was made up of an Arduino UNO Board, eHealth shield [11], data-logger shield and Bluetooth shield. The eHealth shield was used as it allows the Arduino to record and measure data of the human body parameters.
The sensors used with the eHealth shield are reported in Figure 2 and 3, which are:
- Electro cardiogram (ECG) and Electromyograph (EMG): A three electrode sensor. The electrodes can be used to either record data for an ECG or EMG. The ECG records data for heart health and the EMG records data for muscle health.
- Pulse-Oximeter: A non-invasive small battery-operated device which attaches to the index finger. Records blood oxygen levels and heart rate.
- Glucometer: Records blood glucose in Millimoles per litre.
- Body Thermometer: placed at the axillary point of the body. Records body temperature.
- Air Flow: Measures the breathing rate and is placed on the upper lip.
- Galvanic Skin Response: measures the electrical conductance of the skin. This consists of two sensors placed on two separate fingers.
The health monitoring system records the body parameter data via the connected sensors. This data is then stored on an SD card with the date and time it was recorded using a data-logging shield. This data is then transmitted securely to a PC either by Bluetooth or SD card using an application created to get information from the monitor, remotely to a multi-user relational secure database. The web application created allows the patient or health care professional to view uploaded logs, the patient can also upload data to the database from the monitor using the web application. The overall view of this system is shown in Figure 1.
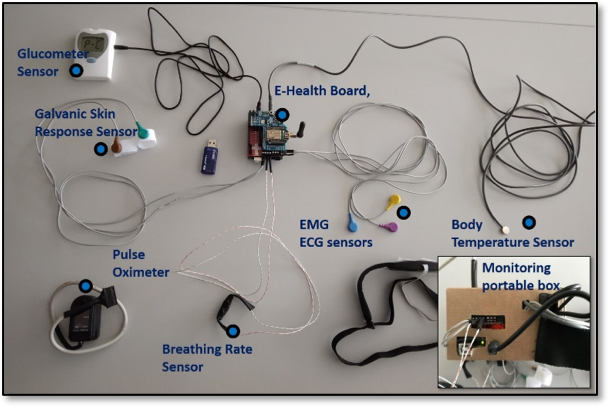 Figure 3 – The sensors and monitoring box set-up of the Health Monitoring System
Figure 3 – The sensors and monitoring box set-up of the Health Monitoring System
The data logger shield allows the Arduino to store all the measured data onto an SD Card, with the correct date due to an onboard real-time clock. This is programmed to store data every minute. Each log contains the date, time and the sensor readings. An authentication method was added to the SD card. To ensure the SD card was correct for the patient, so the data stored on the SD card had to match the data on the device before sensor recording would take place. The Bluetooth shield allows the Arduino to transfer data via a different medium. This shield uses a Bluetooth communication protocol (IEEE 802.15.1, Bluetooth 2.1 +EDR Class 2) and Asynchronous Encryption Standard with data transfers.
The Arduino board was used as it allows for these shields to be used and stacked together.
The Arduino Boards and shields was then encased within a box for protection of the user and the device. The box allowed access to ports and cables. A Velcro strap was attached to the box, so it can be worn over the shoulder and keep the cables tidy and managed. The strap also went across the chest supporting the ECG and thermometer cables. The device was powered by a 1200 mAh battery, with an output of 0.8 A and 5V. The power bank included LEDs to indicate charging and power.
2.2. Communication with the Device
An application was developed using Processing IDE, to communicate with the health monitor via Bluetooth or USB cable. This application was programmed to search for the Arduino board, once found it would display a window asking to name a file for which the data will be stored in. Once entered, three coloured steps were added to retrieve data, close the file of the stored data and reset the device.
2.3. Web application mask
A web application was designed and implemented using HTML5, CSS3, PHP 7.1.20, ECMAScript 2018, MySQL 8 and Apache Programming Languages. The application was performed to easily upload the collected data to a database server and then allow this data to be reviewed by both the patient and the health care professional.
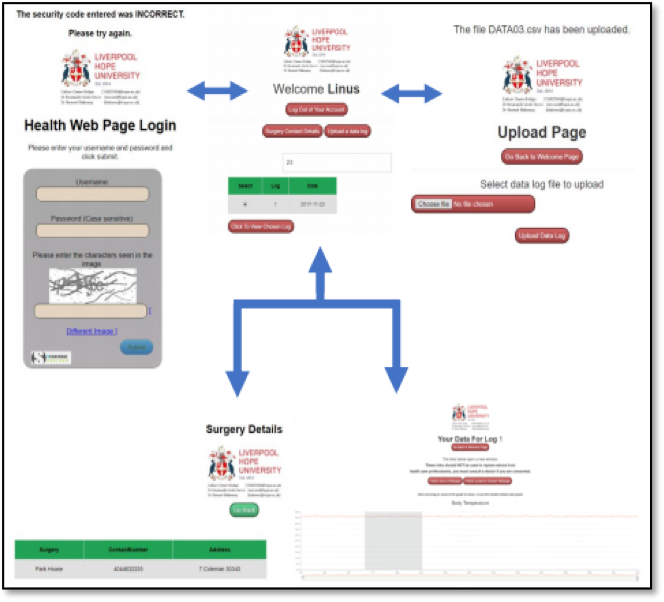 Figure 4 – The Web Application Masks for the Patient
Figure 4 – The Web Application Masks for the Patient
A database was also designed to store the patient information, the health care professional information and the data output of the health monitoring system. The database was stored on a WampServer version 3.1.0 [12]. This server allowed storage of a MySQL database, web application and the communication between them. This database held login information using SHA2 at 512 bits to hash passwords for the web application.
A website was also designed. A login page was added, containing field box for username, password and secure image text. Depending on the username, the user is directed to either the health care professional web page or patient web page. Moreover, a secure image capture was added to the login page to reduce brute force attacks. Text entered in the password field box is hidden and data transmitted between ages are hidden.
A patient welcome webpage was developed. This displays a search box for a table containing data logs, buttons for logging out, surgery details webpage, upload webpage and to continue to graphical webpage once a log is selected. Figure 4 reports an overall summary of the different webpages which are presented to the patient, a similar view is provided for the health care professional.
The upload webpage allows the user to upload files of data saved when importing data from the health monitor. The surgery details webpage, displays details of the surgery the patient is attending, this is shown in Figure 4.
When directed to the graphical webpage, the user can view all their sensor data in graphical form and are able to zoom into specific time points. Also, the user can go back to the previous page or go to webpages for a symptom checker or patient advice, this is shown in Figure 4.
The health care professional webpage, allows health care professionals to search for patients they have access to and view their data logs in graphical form.
3. Results
3.1. Secure Medical Wearable Device
The secure medical wearable device, shown in Figure 3, can measure vital body parameters and store the data with the date and time they are measured on the SD card. The communication with the device was successfully tested between the monitoring system and a personal computer; the data were also uploaded successfully to the database and accessed via the web application. The AES Bluetooth encryption algorithm properly encoded the data. The storage medium provides a mechanism for user authentication; therefore, data is stored in encrypted form before transmission via a public network or internet.
The device has been successful in these preliminary tests (i.e. sensing): the data are encrypted at the patients end before being transmitted to the secure database and the SD card is protected using authentication mechanisms.
3.2 Web Application
The successful implementation of the front-end web application is shown in Figure 4. This application is driven and populated using a secure relational database. The system allows for multiple types of users with different security policies, for example a patient user and a medical professional.
The system is designed such that only the patient can upload, and view data associated with them. The medical professional can only access data that is associated with their patients. The graphs were able to show all the data recorded, allowing for a more accurate diagnosis.
To ensure a secure system many security methods were implemented, from a simply masking of the password and the one-way hashing of passwords which guards against the possibility that someone who gains unauthorised access to the database can retrieve the passwords of the users in the system. Also, used were functions that removed unauthorised characters to prevent SQL code injection type attacks. In addition, the system prevents brute force attaches by using a secure image capture facility. The system would also use transport layer security and security certificates, by hiding passwords entered, using hashed passwords to hide what has been typed in the field box, HTML special chars was used to prevent the webpages from being exploited with code injections and the secure image capture was added to reduce brute force attacks.
3.3 Ethical Issues with the System
As with any system that collects data about individuals there must be consideration of the ethical issues related to this system.
The collected data could be used against the patient by health insurances or wellness programs run by employers. This data could be shared with of health care clinics without the patient knowing. This data could be misused to harm the patient. This health monitor could be misused to keep track of people. For example, a business company or insurance company could force employees or customers to wear this device to keep track of them, instead of using the device for its purpose of wellness improvement and health awareness. It would be imperative that the system complies with all GDPR and that users of the system are trained and authorised.
4. Conclusion and Discussion
In this paper we presented a novel integrated system for the real-time monitoring of physiological parameters. The system provides an SD card reader for saving the data locally, encryption algorithms to encrypt the data, authentication services, and other security procedures. The wireless IEEE 802.15.1 secure communication protocol for transferring the data and a web service was used for the patient and the health care professional.
The system outlined in this paper was implemented successfully. It records physiological parameters, transfer data securely to a computer where it was stored in a secure database and was accessible by different users of different security policies (i.e. patient and health care professional).
The system automatically performs some analysis of the data and presents the information in graphical form. for both the patient and health care professional in graphical form using the web application.
Despite the preliminary performed tests, the system will have to be validated vs. golden standard instrumentations, namely medical and certified equipment [13-15]. Moreover, further laboratory trials should be performed to optimize the portability of the system and to make the interface more user-friendly in a daily medical and hospital scenario/environment. On this matter, an assessment on the reliability and accuracy of the system was not performed at this stage. Therefore, a preliminary validation of this system vs. golden standard instrumentation should be performed in order to validate the system. Such a validation may be based on comparing the measurements of the system with the same parameters as obtained from a polygraph or similar devices and by processing this data with a similar approach to [16, 17], namely Bland Altman technique or similar ones.
The device developed is a prototype and currently we are looking into ways to reduce the size of the energy source and increase the overall lifetime of the system before a recharge is required, as the current system will only last up to 10 minutes. We are also investigating a better, smaller design for the housing of the hardware, so that it is less invasive for the wearer. It is believed however, that point of concept has been proven.
In future these devices could be medically certified which would result in trust of the devices, the processes, and with the accuracy of the data.
Acknowledgment
This work was presented in thesis form in fulfilment of the requirements for the BSc in Computer Science and Electronic Engineering for the student Callum Owen-Bridge under the supervision of Dr. S. Lakeway and Dr. E.L. Sacco from the Robotics Laboratory, Department of Mathematics & Computer Science, Liverpool Hope University
- World Health Organization. (2017). The top 10 causes of death. [online] Available at: [Accessed 6 Dec. 2017].
- Eisenach G. (2001). What is e-health?. Journal of Medical Internet Research, [online] Available at: https://www.ncbi.nlm.nih.gov/pmc/articles/PMC1761894/ [Accessed 6 Dec. 2017].
- Alnosayan N, Lee E, Alluhaidan A, et al (2014). MyHeart: An intelligent mHealth home monitoring system supporting heart failure self-care. 2014 IEEE 16th International Conference on e-Health Networking, Applications and Services.
- Government.nl. (2018). Benefits of eHealth. [online] Available at: https://www.government.nl/topics/ehealth/benefits-of-ehealth [Accessed 1 Mar. 2018].
- de Grood C, Raissi A, Kwon Y and Santana M (2016). Adoption of ehealth technology by physicians: a scoping review. Journal of Multidisciplinary Healthcare, 9, 335-344.
- World Health Organization. (2017). Global Diffusion of Ehealth. Geneva: World Health Organization.
- Virone G, Wood A, Selavo L, et al (2006). An Advanced Wireless Sensor Network for Health Monitoring. Transdisciplinary Conference on Distributed Diagnosis and Home Healthcare
- Li M, Lou W and Ren K (2010). Data security and privacy in wireless body area networks. IEEE Wireless Communications, 17(1), 51- 58..
- Omoogun M, Seeam P, Ramsurrun V, Bellekens X and Seeam A (2017). When eHealth meets the internet of things: Pervasive security and privacy challenges, 2017 International Conference on Cyber Security And Protection Of Digital Services.
- Meingast M, Roosta T and Sastry S (2006). Security and Privacy Issues with Health Care Information Technology. 2006 International Conference of the IEEE Engineering in Medicine and Biology Society.
- Cooking-hacks.com.(2018).e-HealthSensorPlatformV2.0forArduinoand Raspberry Pi [Biometric / Medical Applications]. [online] Available at: https://www.cooking-hacks.com/documentation/tutorials/ehealth-biometric- sensor-platform-arduino-raspberry-pi-medical [Accessed 22 Mar. 2018].
- Bourdon R (2018). WampServer. Alter Way.
- Secco EL, Curone D et al (2012). Validation of Smart Garments for Physiological and Activity-Related Monitoring of Humans in Harsh Environment, American Journal of Biomedical Engineering, 2(4), 189-196
- Magenes G, Curone D, Caldani L, Secco EL (2010). Fire fighters and rescuers monitoring through wearable sensors: The ProeTEX project, Annual International Conference of the IEEE Engineering in Medicine and Biology Society
- Curone D, Secco EL, et al (2012). Assessment of sensing fire fighters uniforms for physiological parameter measurement in harsh environment, 16(3), 501-511, IEEE Transactions on Information Technology in Biomedicine
- Secco EL, Curone D, Tognetti A, Bonfiglio A, Magenes G (2012). Validation of Smart Garments for Physiological and Activity-Related Monitoring of Humans in Harsh Environment, American Journal of Biomedical Engineering, Vol.2, No.4, 189-196
- Curone D, Secco EL, Caldani L et al (2012). Assessment of Sensing Fire Fighters Uniforms for Physiological parameter Measurement in Harsh Environment, IEEE Trans on Information Technology in Biomedicine, vol. 16, no. 3, pp. 501-511
Citations by Dimensions
Citations by PlumX
Google Scholar
Scopus
Crossref Citations
No. of Downloads Per Month
No. of Downloads Per Country
