Evolving AL-FEC Application on 5G NGMN-Edge Computing Systems
Volume 3, Issue 5, Page No 152-160, 2018
Author’s Name: Christos Bouras1,2,a), Nikolaos Kanakis2
View Affiliations
1Computer Technology Institute and Press “Diophantus”, Patras, Greece
2Computer Engineering and Informatics Department, University of Patras, Greece
a)Author to whom correspondence should be addressed. E-mail: bouras@cti.gr
Adv. Sci. Technol. Eng. Syst. J. 3(5), 152-160 (2018); ![]() DOI: 10.25046/aj030519
DOI: 10.25046/aj030519
Keywords: Forward error correction, Next generation mobile network, Online algorithms, Mobile edge computing
Export Citations
Fifth generation of mobile networks (5G) comes to cope with the context of the new mobile telecommunications era. Edge computing is a new collaborative technology under standardization utilizing end-user devices or near-end-user edge devices to operate processing, communication, or control operations. The achievement of efficient error control is a very critical aspect in the successful development of 5G Next Generation Mobile Networks (NGMN). Especially utilizing Forward Error Correction (FEC) codes on the application level is an efficient approach on improving error control on NGMN since it is adopted in several mobile multicast standards. FEC is a feedback free error control technique where redundant data are introduced with the source data to enable the recipient recovering from packet losses with an interesting approach on applying AL-FEC error protection introduces deterministic or randomized online algorithms. Based on this we present a novel online scheme on applying AL-FEC application on the context of the AL-FEC policy online problem. In this work we present an online algorithm based on feedback received from mobile end-users which adapts the introduced protection based on this. Another aspect of this work is the utilization of AL-FEC protection on the edge level based on RaptorQ FEC codes.
Received: 22 July 2018, Accepted: 16 September 2018, Published Online: 29 September 2018
1. Introduction
The design of an algorithm capable to adapt the transmission redundancy that will be introduced by AL-FEC protection can be addressed with online algorithms. Online algorithms [1] are utilized on problems where the algorithm does not have knowledge of the input in advance. Hence, online algorithms should be able to make a decision without a priori knowledge of the input since it is not available at present. On online algorithms design it is assumed that algorithm’s input arrives in steps and the online algorithm has to make a decision upon the arrival of each new input. Moreover, in problems where deterministic algoithms are not suitable or cannot even apply the simplest and several times the most efficient approach is utilizing randomized online algorithms [2]. Regarding the performance of online algorithms it is analyzed utilizing competitive analysis where the output produced by the evaluated online algorithm is compared with the optimal offline algorithm of an online problem is that this algorithm has a priori knowledge of the entire input and thus is able to confront with it with minimum cost. The metric used to describe the performance of an online algorithm A is the competitive ratio. The competitive ratio is always computed against an adversary knowing in advance the operation of the online algorithm and generating a sequence σ, based on this knowledge, with the online algorithm serving it. To compute the competitiveness of an online algorithm A, if A(σ) stands for the cost of the online algorithm and OP T (σ) stands for the cost of the optimal offline algorithm the online algorithm A is c-competitive if a constant α exists that A(σ)−c ·OP T (σ) ≤ α.
Edge computing [3] is a virtualization technology providing computation, and networking operations between devices located at the edge of the network deployment and cloud computing. The baseline context of Edge computing is having light-weight devices at the proximity of end users enabling the provision of custom and location-aware services. Such micro clouds can be easily integrated to Enhanced Packet Core (EPC) of mobile networks enabling on EPC new capabilities on deploying evolutionary architectures or service solutions via virtualization or not.
This paper is an extension of work originally presented in [4] focused on the application of AL-FEC error protection on NGMN multicast services where the novel MTO adaptive online algorithm aiming to efficiently apply AL-FEC protection is analyzed. In this work, we moreover concentrate on the migration of ALFEC protection to the edge of mobile edge networking architecture as presented in [5]. We provide an analysis on such an architecture and the operations required for such integration. Furthermore, we evaluate the ALFEC application performance on the edge revealing, apart from the benefits introduced from such a choice, the performance bounds on its deployment.
The context of this work has the following structure: In Section 2 we discuss relevant work of this paper. In Section 3 we describe the concept of Mobile Edge computing and in Section 4 we present the ALFEC reliability control. In Section 5 we present the proposed online algorithm and we analyze its performance. In Section 6 we analyze the migration of the AL-FEC error protection on the edge and we evaluate this design performance under several perspectives. Concluding in Section 7, we discuss the advantages introduced from the proposed online error protection scheme and the AL-FEC application on the edge and we refer to some possible future directions that could follow in order to extend this work.
2. Related Work
Many active research fields of communication networks utilize online algorithms. In the work of [6] the authors cope with routing alogorothms under energy efficiency constraints and they present an online algorithm improving the throughput on multihop networks, The authors of [7] utilize online to address energy-constrained limitations on ad-hoc networks in the context of multicast routing problems. Moreover, the authors of the work [8] provide distributed online algorithms for the frequency assignment online problem. In the work presented in [9] the authors cope again with energy efficiency in conjunction with delay constraints on wireless multicast deployments presenting an algorithm for online scheduling problems. The authors of [10] investigate the decision sending a source packet, retransmiting a lost packet or sending a redundant packet with competitive analysis, providing an online algorithm capable to pick the appropriate decision. Finally, the authors of this manuscript in [11] stated the online AL-FEC policy problem referring to reduction of the efficient selection of the introduced transmission overhead in an AL-FEC protected delivery to online problems for mobile multicast networks and they provided a first attempt on this newly introduced online problem with a randomized online algorithm. Moreover, the same authors in the work [12] designed a deterministic online algorithm utilizing weight assignments and afterwards the same authors provided an enhanced adaptive version of this deterministic online algorithm in [13].
On the edge computing field, the authors of [14] provide a thorough definition of this technology, analyzing several case studies and discussing the challenges and opportunities of edge computing. Moreover, the authors of the work [15] present the edge technology in the context of sensor networks, peer-to-peer networks and network virtualization functions. Finally, in the work [16] the authors investigate the feasibility of utilizing constrained devices as edge gateways in edge architectures. From the results of this work they conclude that under appropriate configuration and fine-tuning, scalability and reduced overhead can be achieved.
3. Mobile Edge Computing on 5G Multicast NGMN
The increased demands on network capacity and user experience drive the next generation mobile systems. The efficient utilization of the radio spectrum over common resources is one of the most major aspects for broadcast and multicast delivery towards 5G NGMN. Apart from the development of novel technologies there is the path where multicast services will cooperate and be enhanced by several existing ecosystems, like Internet of Things (IoT) or Device-to-Device (D2D) communication. To achieve this cooperation development is required on all layers of the protocol stack, from modulation and coding to transport protocols, and applications.
Mobile Edge Computing (MEC) [3] is a technology under standardization from the ETSI MEC Industry Specification Group (ISG). Mobile Edge Computing describes a service environment with cloud-enabled capabilities located at the edge of the mobile network in proximity to mobile end-users. The main goals of MEC is to achieve reduced latency, increased efficiency for network operation and services delivery, and as a result an enhanced user experience. MEC side by side with Functions Virtualization (NFV) and Software-Defined Networking (SDN)) [17] is one of the main focuses on the development of 5G evolved systems. One of the main advantages of MEC in conjunction with NFV and SDN is that will enable the transformation of traditional deployments to a programmable interface for various operations contributing on the achievement of the demanding requirements of 5G standard. MEC is itself based on virtualization, and comes to complement NFV, while NVF focuses on network functions while, MEC is responsible to enable applications running at the edge of the network. Another advantage of MEC is the fact that allows operators to reuse their infrastructure deployments since the infrastructure hosting MEC operations is similar with the equired
NFV infrastructure hence, it is possibl to host both VNFs (Virtual Network Functions) and MEC applications on the same infrastructure. Combining all of the above, MEC technology will allow 5G environments to provide improved latency, bandwidth, and location awareness and so new or existing services/operations could be hosted on the edge.
4. AL-FEC Error Protection
Fountain Codes are codes developed to provide reliability control on data delivery over unreliable channels characterized by unspecified probability of data corruptions [18]. Fountain code name comes from the fact that operate like water fountains infinite supplying water drops and anyone collecting those drops in a bucket under the fountain with the bucket removed when enough drops are collected. In the same context but with a digital source instead of a water fountain, a recipient receives encoded symbols from one or more transmitters and collects them till enough are obtained. Then the recipient is able to reconstruct the original transmitted object, and which symbols are received does not matter. Since the source can theoretically generate unbounded amount of encoded symbols, Fountain Codes are rateless codes.
Since random linear codes cannot be applied in proactice due to their complexity, Luby Transform (LT) codes presented in [19] which are able to provide applicable encoding and decoding and at the same time they are able to maintain low transmission overhead. In more details, LT codes can operate close enough to channel encoding under appropriate selecting the distributions of the edges in the Tanner graph. Moreover, if the reliability of the decoding process is decreased the complexity can be further reduced providing linear time for encoding and decoding complexity. Since all of the input symbols cannot be decoded with the lower degree distribution for the same overhead if an erasure correcting pre-code is utilized the erasures arising from the weakened decoder could be recovered. Raptor codes provide exceptional encoding and decoding performance if a linear time block code like LDPC is used for the precoding process.
RaptorQ codes [20] are the predecessor of Raptor codes providing much more efficiency on AL-FEC encoding and decoding process. They also present by far improved flexibility and error recovery. Encoding of RaptorQ codes is almost the same with Raptor code encoding. Of course RaptorQ codes introduced an enhanced design providing enhanced performance compared with their predecessor. The main difference on the operation of RaptorQ and Raptor codes is that the newly introduced RaptorQ codes utilize larger finite fields overcoming the performance limitations of Raptor code and achieving recovery from lost symbols with decreased transmission overhead. Apart from this RaptorQ codes are capable to operate over higher number of source symbols and thus increased number of generated encoding symbols. This expansion on the number of symbols RaptorQ codes can handle enables the simplification and increased flexibility of applying AL-FEC protection.
5. Online AL-FEC Protection
5.1. Online Model
In this work we assume a common mobile networks environment where multicast delivery of streaming flows to endusers is simulated. In more details, a multicast source injecting bunches of packets in the network which are handled as a continuous object and are delivered to endusers via multicast bearers encapsulated in RTP/UDP streaming flows.
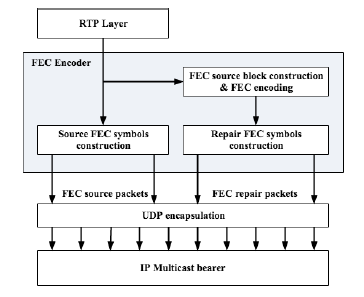 Figure 1: AL-FEC encoding process
Figure 1: AL-FEC encoding process
Regarding the application of AL-FEC protection in the transmitted object we utilize the newly introduced RaptorQ FEC codes. Fig. 1 presents the encoding process of AL-FEC protection The first step is to partition the transmitted object into one or more FEC source blocks with each one of the FEC source blocks having size k symbols, a value which is an encoding parameter and is called source block length (sbl). During the RaptorQ AL-FEC encoding process a number of redundact FEC symbols are generated from each FEC source block. Those redundant symbols are called repair symbols. The amount of generated repair FEC symbols depends on the desired AL-FEC protection introduced by the multicast source. The outcome of the Raptor AL-FEC encoding is a certain amount of FEC encoding symbols which can be either source or repair symbols. In the simulated environment each produced FEC encoding symbol receives a number which is unique for each one.
The decoding failure probability which is the metric characterizing the decoding performance of RaptorQ AL-FEC is described as (1) [21]:
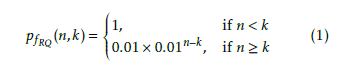 For a FEC source block of size k with an enduser received n encoding symbols, the quantity pfRQ(n,k) is the probability the enduser to fail to decode this source block. Regarding the successful reconstruction of a transmitted FEC source block From the receiver perspective with respect to the previous modeled ALFEC decoding failure probability we assume, forced from the results available in [22], that the threshold for the decoding failure probability of each FEC source block can be 10−2 to mark the FEC source block as successfully reconstructed or not.
For a FEC source block of size k with an enduser received n encoding symbols, the quantity pfRQ(n,k) is the probability the enduser to fail to decode this source block. Regarding the successful reconstruction of a transmitted FEC source block From the receiver perspective with respect to the previous modeled ALFEC decoding failure probability we assume, forced from the results available in [22], that the threshold for the decoding failure probability of each FEC source block can be 10−2 to mark the FEC source block as successfully reconstructed or not.
Finally, regarding the multicast bearer level we model the delivery or not of a transmitted packet with an independent loss transcript. That means that on each packet sequence transmitted on each enduser an independent packet loss mask is applied according to the desired packet loss rate defined in the environment. In this work p denotes the average network packet loss rate of the mobile multicast bearers.
5.2. Optimal Offline Algorithm
To provide the competitive analysis of the proposed online algorithm we need to utilize the optimal offline algorithm of the online problem. Since the optimal offline algorithm has a priori knowledge of the problem input, and according to the work presented in [23], the optimal offline algorithm in the context of a multicast source which has to select the appropriate amount of transmission overhead introduced in a delivery is a multicast source which will select the introduced transmission overhead to a value close to the average packet loss rate of the network.
Moreover, based on the enhanced recovery performance properties of RaptorQ codes as described in (1) and based on the assumption of this work for the failure probability of the decoding process of a received FEC protected source block the optimal offline algorithm can achieve the specific threshold introducing no more FEC repair symbols than the average number of lost encoding symbols computed by the average packet loss rate p of the multicast environment.
According to previous analysis, given that sbl is the number of symbols a source block contains and r is the number of repair symbols the optimal offline algorithm decides to introduce in each FEC source block r can be calculated as: (sbl +r)·p. Hence, the cost OP T of the optimal offline algorithm is: OP T = sbl +r.
5.3. Mean Transmission Overhead Algorithm
The baseline of the Mean Transmission Overhead (MTO) algorithm is the adaptation of the AL-FEC overhead based on feedback received from UEs of past deliveries. Hence, the operation of the MTO algorithm depends on the previous transmission rounds. On each round the input of the algorithm is the UE coverage attribute. UE coverage denotes a threshold on the number of UEs participating on the delivery and is used to indicate if the transmission round should be considered as sufficient protected or not. The outcome of the MTO algorithm is the computation of the mean ALFEC overhead after each round and the update of the introduced transmission overhead with the computed value for the current round.
Each UE is able to report the outcome of the ALFEC decoding process on the transmitted object enabling the algorithm to compute the overall UE coverage of a completed transmission round. Based on this, the MTO algorithm is able to compute the attribute ideal transmission overhead for each past transmission round. This attribute denotes the transmission overhead which should had been introduced in the delivery round to achieve the defined UE coverage for this round. After computing this ideal value transmission overhead of the completed round the algorithm is ready to update the value of the mean transmission with it. Finally, the MTO algorithm will update the current transmission overhead that will be introduced in the current transmission round with the updated value of the mean transmission overhead.
At this point, clarifying the feasibility of a crucial part on the MTO operation, i.e., the feedback received on the reception status of the transmission object from each UE, we have to mention that a various of mobile multicast standards describe a post-delivery process where the UE is able to provide feedback to the multicast source on several aspects i.e., report on delivery status, file repair status, etc. Such kind of capabilities enable a multicast source to track the status of a transmission and maintain extensive report information for past content deliveries.
Having analyzed the operation of the MTO algorithm we can compute the cost of the online algorithm. Denoting with r0 the number of source symbols that the online algorithm will introduce to the transmission of a FEC source block with length sbl the value of r0 is computed according to the attribute mean transmission overhead of the algorithm and the cost of the online MTO algorithm is: ALG = sbl +r0.
5.4. Performance Evaluation
Block Length First part of performance evaluation introduce a comparison on the percentage of UEs that are satisfied. Satisfied UEs are the ones which are able to reconstruct the original object. The comparison is done between the performance of the MTO online algorithm, an approach where AL-FEC overhead is fixed to a specific value approach performance, and lastly a common error recovery approach which is feedbackbased and lost packets are retransmitted to individual UEs.
Fig. 2 contains results for a transmitted entity encoded to source blocks with the size of each block varying between 2048 to 65536 symbols. The evaluated packet loss rate is 5%. 100 participating UEs in the multicast delivery and a 65536 symbol sized transmitted object are the other parameters utilized in this evaluation. Moreover, 90% is the target coverage for
60
10000 20000 30000 40000 50000 60000
Source Block Length
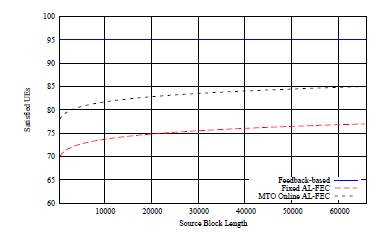 Figure 2: Satisfied UEs vs. Source Block Length
Figure 2: Satisfied UEs vs. Source Block Length
As was anticipated, we cannot have results regarding sbl increase for feedback-based packets retransmission case since AL-FEC protection is not used there at all. We can just note that the feedback-based approach is capable to maintain continuous and high volumes of satisfied UEs. However, this performance comes at its own expense, a fact discussed in next subsections of simulation results. Discussing the performance of the approaches utilizing AL-FEC, the performance enhancement by increasing the length of the source block, is clearly noticeable. RaptorQ codes are able to operate more efficiently by increasing the sbl since they are able to exploit protection spreading across the whole encoded entity.
In addition, the curve trend for the quantity of the satisfied UEs we notice that is exact same for the MTO algorithm, as well as for the fixed AL-FEC transmission overhead policy, since the evaluated loss rate remains fixed, hence packet delivery conditions are not altered for each simulation snapshot and the MTO algorithm operation is founded on the adaptation of the transmission overhead according to previous reception conditions.
Packet Loss Rate In this section, the network’s packet loss rate impact on the performance of the MTO algorithm is analyzed. In Fig.3 there is a presentation of the achieved return on satisfied UEs, for different packet loss rates relative to the approach introducing a constant amount of overhead and the approach where lost data are retransmitted on UEs request. On this evaluation the packet loss rate is gradually increased from 1% to 20% while delivering a 4096 packet length object to 100 UEs, assuming 4096 symbol sized ALFEC source blocks and one packet per symbol.
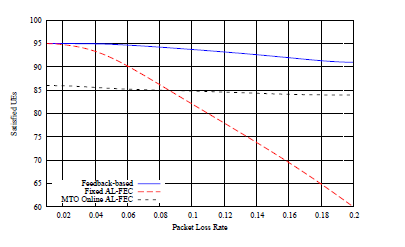 Figure 3: Satisfied UEs vs. Packet Loss Rate
Figure 3: Satisfied UEs vs. Packet Loss Rate
Once more, we can point out that the efficiency of the packet retransmission is superior to the one of the fixed transmission overhead protection. An expected remark is that, for only low average packet loss rates, the efficiency achieved is identical to the constant overhead protection. This is based on the fact that the introduced AL-FEC overhead is of fixed value for the fixed policy approach chosen at a higher value in comparison to the packet loss rate, and causes wasting valuable network resources. Another remark regarding the efficiency of the lost packets retransmission protection is the fact that, even slightly, it is reduced with the packet losses increase. This is an expected behavior, as for high rates of packet losses, the amount of UEs that will enter in bad reception or even dropped will constantly increase.
As shown in the curve trend, even though the performance would be ephemeral, the constant overhead approach can achieve high volumes of satisfied UEs for low average packet loss rates but this is observed just initially, i.e., for packet losses up to 2%. More on this, we can indicate that the constant overhead performance declines fast and the UEs coverage becomes 25% less than the MTO algorithm performance for packet loss 20% since the constant overhead scheme cannot respond to the increase of the packet loss. Regarding the MTO algorithm we observe that now the performance is constant. Of course, the coverage achieved is less than the lost data retransmission approach but, this has nothing to do with the MTO performance and it is just a consequence of the UEs coverage target of the simulation.
Network Resources Those latter simulations of Fig.4, examine the performance of the three evaluated approaches on a network utilization perspective
i.e. the amount of exchanged packets during a multicast delivery, against the increasing simulated average packet loss rates is examined. Once more, the packet loss rate ranges from 1% to 20%. For this evaluation we perform a simulation of a 4096 packet object transmission to 100 UEs. As for the AL-FEC protection parameters, we use a 4096 symbol sized source block. It is important to clarify that for the feedback-based protection scheme each UE is able to provide feedback, about the packets that need to be retransmitted, to the multicast source, through unicast bearers. Then, in a following repair transmission phase, the packets will be transmitted to the appropriate UEs from the multicast source, through unicast bearers. Finally, for AL-FEC protection application we assume exactly one FEC symbol per packet.
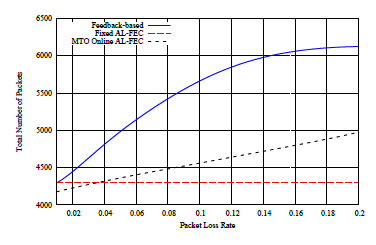 Figure 4: Total Number of Packets vs. Packet Loss Rate
Figure 4: Total Number of Packets vs. Packet Loss Rate
The first immediate remark comes for the constant overhead approach where the amount of packets exchanged remains constant too for any evaluated packet losses value. Of course this is the expected performance for this approach as previously analyzed. The cost regarding network resources to achieve the high performance noted for the retransmission based approach as discussed in previous parts is revealed in this subsection. Compared with MTO, This approach requires a significantly higher number of packets transmitted across the network, and more specifically, we can notice that for packet losses higher than 10% this approach adds on the network over 50% of additional traffic. Finally, on the MTO approach, the curve for the number of exchanged traffic matches the network packet losses trend. This is a direct consequence of the algorithm’s nature to adapt the overhead to the reception conditions. Although MTO’s approach can not reach the error recovery provided by the retransmission approach as discussed in previous part, its profit on resource utilization is higher than the degradation on error protection.
6. AL-FEC Error Control on the Edge
In this second part we further analyze the AL-FEC Protection Scheme integrated with MEC presented in [5].
We provide performance evaluation results discussing initially the improvements the proposed scheme could introduce in multicast NGMN but apart from this we reveal the bounds on the performance of this scheme regarding deployment parameters.
Fig. 5 presents the basis of the architecture where the AL-FEC protection is migrated to the edge gateways of the network. While in conventional deployments the AL-FEC is applied on the multicast gateway level, in this work the AL-FEC application is also handled by the edge gateways responsible for a cluster of UEs in cooperation with the multicast gateway.
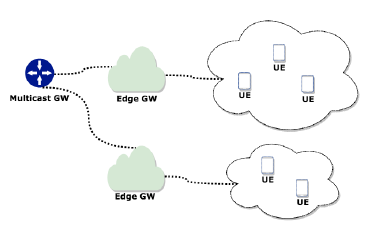 Figure 5: AL-FEC error control on the edge
Figure 5: AL-FEC error control on the edge
The delegation of the decision on the transmission overhead amount to the level of the edge gateways enables a coarse-grained policy on the process computing the most appropriate AL-FEC transmission overhead for a delivery. Hence, this architecture provides enhanced efficiency for AL-FEC since the number of repair packets will be reduced resulting also on network load decrease always with respect to the reception conditions of the UEs cluster. Another important fact that will also provide enhanced scalability and efficiency is that any monitoring functions required for an AL-FEC scheme can also be implemented on the edge gateways.
In more details, the Multicast GW is responsible to select, according to the Multicast GW and Edge GW connection type, if it will introduce AL-FEC redundancy to the content forwarded to the edge layer. On the edge GW layer when the transmitted content arrives the GW should decide if the content will be forwarded as it is to the end users in case of an already encoded content. In case of the arrival of a non AL-FEC protected content, the edge GW will AL-FEC encode it introducing the appropriate overhead based on networking functions implementation on the receptions conditions of the UEs cluster served by the specific Edge GW.
For the sake of clarity, we have to clarify that in the application layer, apart from the AL-FEC protection applied, a file-repair post-session is also utilized [24] where a UE that fails to decode a FEC protected source block is able to determine which source symbols are missing for the source block and achieve the retransmission of them via dedicated unicast bearers.
6.1. Performance Evaluation
In this part we present theoretical performance results on the potential improvements such a scheme has on the transmitted redundancy and in general in the overall network traffic.
AL-FEC Transmission Overhead In the presented results we investigate the improvement on the volume of the data redundancy introduced. The percentage results refer to the comparison of the proposed method with conventional architectures with the protection redundancy computed from the multicast source. In both cases we assume that both examined approaches require the same delivery success rate in the end-users.
In Fig. 6 we investigate the decrease on the average introduced error protection overhead with the increase of the number of UEs per each Edge GW for three different values of average packet loss rate 5%, 10% and 20%.
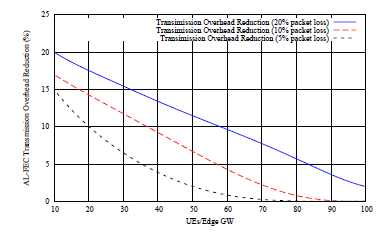 Figure 6: AL-FEC Transmission Overhead vs UEs/Edge GW
Figure 6: AL-FEC Transmission Overhead vs UEs/Edge GW
It is anticipated that as the number of UEs served by an Edge GW increase the gains on the transmission overhead are decreased since the required average transmission overhead is increased. In more details when evaluating 10 UEs per Edge GW with 20% packets lost the transmission overhead is reduced around 20% and for the same number of UEs but for 10% and 5% of average packet loss rate the improvement is about 17% and 15% respectively. For the case of 20% of average packet loss rate and for 50 UEs per Edge GW we notice a decrease of almost 10%. While, for 100 UEs the decrease is shortened to around 5%. This performance is expected since if the number of endusers assigned to an Edge GW increases then the number of UEs with heterogeneous packet losses under the same Edge GW is increased too resulting to the increase of the average transmission overhead amount that should be introduced to the delivery. However, the improvement on the introduced AL-FEC transmission overhead is still noticeable even in the case of the 100 UEs per Edge GW and 20% packet losses. Another interesting remark is that for the cases of evaluated packet losses of 5% and 10% a threshold for the efficiency of the proposed scheme is revealed with respect to the number of UEs served by an Edge GW since for 5% packet losses we have no gains for more than around 50 UEs and for 10% packet losses this threshold is less than 70 UEs.
Network Traffic In this last part we investigate the impacts of the edge error control architecture on the network traffic of the mobile network. We evaluate the total amount of traffic towards the UEs but also on the backwards channels too since a UE is able to request the retransmission of lost symbols from the multicast source via unicast bearers in case of corrupted source content.
Fig. 7 presents simulation results evaluating the impact on the network traffic in terms of packets exchanged on the network with the average packet loss rate increase from 5% up to 20% and the number of UEs served by an Edge GW increased from 10 UEs to 100 UEs.
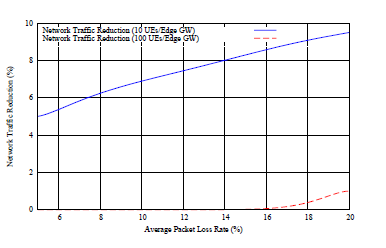 Figure 7: Network Traffic vs Packet Loss Rate
Figure 7: Network Traffic vs Packet Loss Rate
The first remark from the trends of the 10 UEs curve is that the network traffic decrease is enhanced as the packet losses increase. For 10 UEs served by an Edge GW with 5% of packet losses the network traffic decrease is more than 5% and for 20% of losses the decrease overcomes 9%. This is a direct consequence from the results presented in previous section since as the packet losses are increased the decrease achieved from the proposed scheme on the average transmission overhead required is increased too. Hence, less redundant repair symbols are transmitted required in average to achieve a successful decoding. On the other hand, as in the previous results presented in Fig. 6 the increase of the UEs delegated to an Edge GW to 100 UEs reveals again the scalability bound of the proposed scheme since we observe that in this case the decrease on the network case is eliminated for average packet loss rate values till around 18% and only extremely high packet losses of 20% denote a network traffic decrease of around 1%. This is a direct consequence of the fact that as the UEs delegated to an Edge
GW increase the coarse-grained tuning on the required
AL-FEC transmission overhead gets eliminated since the number of UEs with high deviations on reception conditions is constantly increased too.
7. Conclusions and Future Work
The MTO online algorithm is presented in this manuscript on the online AL-FEC policy problem. The baseline of the proposed algorithm is the adaptation of the introduced AL-FEC transmission redundancy based on the feedback received from previous transmissions. We have presented and stated the introduced MTO AL-FEC online algorithm based on the online ALFEC policy and we have provided an analysis of the impacts of this algorithm on the application of AL-FEC error control comparing with feedback-based error recovery and the common approach of introducing a fixed amount of AL-FEC overhead in the transmission and providing simulation results on the achieved performance of the MTO online algorithm. According to the results, the online algorithm achieves close performance to that of the retransmission based approach and sometimes it overcomes it. Another aspect we have investigated is the impacts of the MTO algorithm on network resource utilization. The evaluated results verified that the online approach is the most efficient compared with the other evaluated approaches.
The second part investigates the migration of ALFEC protection on the edge of a MEC-enabled network. Apart from this, performance evaluation results were presented indicating the gains that such a scheme can introduce on the efficiency of the AL-FEC protection application since, such a choice is able to introduce coarse-grained error recovery capabilities on a multicast network. This design choice was analyzed in terms of network traffic reduction but also we have investigated the scalability bounds of the proposed scheme under different reception conditions and deployment parameters. We have verified that, under the condition that the parameters of such an approach are carefully selected, such a design choice id capable to reduce the AL-FEC overhead and hence increase network resources utilization.
Future work of this manuscript could concentrate on the design of more sophisticated and advanced online algorithms on the problem investigated in this work i.e., advanced approaches to apply AL-FEC efficiently on NGMN. Another potential field that could extend the work presented in this manuscript is deviceto-device (D2D) communication over MEC architectures. IoT architectures, apart from the common communication channels providing connectivity between the cloud and IoT devices, defines also connectivity capabilities between the IoT devices. Based on this, the proposed architecture could be enhanced enabling D2D capabilities where, during the AL-FEC source block reconstruction, missing repair symbols could be also received from another device in proximity and not from the Edge GW.
- A. Borodin and R. El-Yaniv, Online computation and competitive analysis. New York, NY, USA: Cambridge University Press, 1998.
- R. Motwani and P. Raghavan, “Algorithms and theory of computation handbook,” M. J. Atallah and M. Blanton, Eds. Chapman & Hall/CRC, 2010, ch. Randomized algorithms. [Online]. Available: http://dl.acm.org/citation.cfm?id= 1882757.1882769
- Y. C. Hu, M. Patel, D. Sabella, N. Sprecher, and V. Young, “Mobile edge computing?a key technology towards 5g.”
- C. Bouras and N. Kanakis, “Evolving al-fec application towards 5g ngmn,” in 2018 9th IFIP International Conference on New Technologies, Mobility and Security (NTMS), Feb 2018, pp. 1–5.
- C. Bouras and N. Kanakis, “Al-fec application on ngmn-edge computing integrated systems,” in 2018 Tenth International Conference on Ubiquitous and Future Networks (ICUFN), July 2018, pp. 364–369.
- L. Lin, N. Shroff, and R. Srikant, “Asymptotically optimal energy-aware routing for multihop wireless networks with renewable energy sources,” Networking, IEEE/ACM Transactions on, vol. 15, no. 5, pp. 1021 –1034, oct. 2007.
- W. Liang and X. Quo, “Online multicasting for network capacity maximization in energy-constrained ad hoc networks,” Mobile Computing, IEEE Transactions on, vol. 5, no. 9, pp. 1215 –1227, sept. 2006.
- J. Janssen, D. Krizanc, L. Narayanan, and S. Shende, “Distributed Online Frequency Assignment in Cellular Networks,” Journal of Algorithms, vol. 36, no. 2, pp. 119 – 151, 2000. [Online]. Available: http://www.sciencedirect.com/science/ article/pii/S0196677499910684
- A. El Gamal, C. Nair, B. Prabhakar, E. Uysal-Biyikoglu, and S. Zahedi, “Energy-efficient scheduling of packet transmissions over wireless networks,” in INFOCOM 2002. Twenty-First Annual Joint Conference of the IEEE Computer and Communications Societies. Proceedings. IEEE, vol. 3, 2002, pp. 1773 – 1782 vol.3.
- Y. Bartal, J. Byers, M. Luby, and D. Raz, “Feedback-free multicast prefix protocols,” in Computers and Communications, 1998. ISCC ’98. Proceedings. Third IEEE Symposium on, jun-2 jul 1998, pp. 135–141.
- C. Bouras, N. Kanakis, V. Kokkinos, and A. Papazois, “Deploying AL-FEC with Online Algorithms,” in Next Generation Mobile Apps, Services and Technologies (NGMAST), 2013 Seventh International Conference on. IEEE, 2013, pp. 175–180.
- C. Bouras and N. Kanakis, “A Competitive AL-FEC Framework over Mobile Multicast Delivery,” in Wireless Communications and Mobile Computing Conference (IWCMC), 2013 9th International, jul. 2013.
- C. Bouras and N. Kanakis, “An Adaptive Weighted Online AL-FEC Algorithm over Mobile Multicast Networks,” in Wireless Communications and Networking Conference (WCNC), 2014 IEEE. IEEE, 2014.
- W. Shi, J. Cao, Q. Zhang, Y. Li, and L. Xu, “Edge computing: Vision and challenges,” IEEE Internet of Things Journal, vol. 3, no. 5, pp. 637–646, Oct 2016.
- L. M. Vaquero and L. Rodero-Merino, “Finding your way in the fog: Towards a comprehensive definition of fog computing,” SIGCOMM Comput. Commun. Rev., vol. 44, no. 5, pp. 27–32, Oct. 2014. [Online]. Available: http://doi.acm.org/ 10.1145/2677046.2677052
- P. Bellavista and A. Zanni, “Feasibility of fog computing deployment based on docker containerization over raspberrypi,” in Proceedings of the 18th International Conference on Distributed Computing and Networking, ser. ICDCN ’17. New York, NY, USA: ACM, 2017, pp. 16:1–16:10. [Online]. Available: http://doi.acm.org/10.1145/3007748.3007777
- 5G Infrastructure Public Private Partnership, “5G Vision: The 5G Infrastructure Public Private Partnership: the next generation of communication networks and services,” 5G Infrastructure Public Private Partnership, https://5g-ppp.eu/wpcontent/ uploads/2015/02/5G-Vision-Brochure-v1.pdf, Tech. Rep., 2015.
- D. J. MacKay, “Fountain codes,” in Communications, IEE Proceedings-, vol. 152, no. 6. IET, 2005, pp. 1062–1068.
- M. Luby, “LT codes,” in Foundations of Computer Science, 2002. Proceedings. The 43rd Annual IEEE Symposium on, 2002, p. 271–280.
- M. Luby, A. Shokrollahi, M. Watson, T. Stockhammer, and L. Minder, “RaptorQ Forward Error Correction Scheme for Object Delivery,” RFC 6330, Internet Engineering Task Force, Aug. 2011. [Online]. Available: http://tools.ietf.org/rfc/ rfc6330.txt
- 3GPP, “Rationale for MBMS AL-FEC Enhancements,” 3rd Generation Partnership Project (3GPP), Tdoc S4-110449, 2011.
- 3GPP, “Simulation results for the performance and complexity of RS codes for MBMS FEC,” 3rd Generation Partnership Project (3GPP), Tdoc S4-050107, 2005.
- C. Bouras, N. Kanakis, V. Kokkinos, and A. Papazois, “Application layer forward error correction for multicast streaming over LTE networks,” International Journal of Communication Systems, 2012. [Online]. Available: http://dx.doi.org/10.1002/dac. 2321
- 3GPP, “Multimedia Broadcast/Multicast Service (MBMS); Protocols and codecs (Release 10),” 3rd Generation Partnership Project (3GPP), TS 26.346, 2011. [Online]. Available: http: //www.3gpp.org/ftp/Specs/html-info/26346.htm
