A Cyber-Vigilance System for Anti-Terrorist Drives Based on an Unmanned Aerial Vehicular Networking Signal Jammer for Specific Territorial Security
A Cyber-Vigilance System for Anti-Terrorist Drives Based on an Unmanned Aerial Vehicular Networking Signal Jammer for Specific Territorial Security
Volume 3, Issue 3, Page No 43-50, 2018
Author’s Name: Dhiman Chowdhury1,a), Mrinmoy Sarkar2, Mohammad Zakaria Haider3
View Affiliations
1Electrical Engineering, University of South Carolina, SC 29208, U.S.A.
2Electrical and Computer Engineering, North Carolina A & T State University, NC- 27411, U.S.A.
3Electrical and Electronic Engineering, Bangladesh University of Engineering and Technology, Dhaka-1000, Bangladesh.
a)Author to whom correspondence should be addressed. E-mail: dhiman@email.sc.edu
Adv. Sci. Technol. Eng. Syst. J. 3(3), 43-50 (2018); ![]() DOI: 10.25046/aj030306
DOI: 10.25046/aj030306
Keywords: Anti-terrorist drive, Band-pass filter, Cyber-vigilance system, Motion control, Networking signal jammer, Territorial security, Unmanned aerial vehicle, Video surveillance
Export Citations
During sudden anti-terrorist drives conducted by the law enforcement agencies, a localized cyber security system happens to be a special tactic to avert the unprecedented massacre and gruesome fatalities against the residents of that area by disconnecting the affected territory from the rest of the world; so that the militants and their outside accomplices cannot communicate with each other and also the terrorists cannot go through the ongoing apprehensive operation via wireless communications. This paper presents a novel framework of an unmanned aerial vehicular networking signal jammer which is oriented to block incoming and outgoing signals of all frequencies transmitted from a specifically marginalized territory scanned and explored by the aerial vehicle. During such a cyber-vigilance operation, the aerial vehicle is equipped with a transmitter and an auto-tuning band-pass filter module with automatic regulation of center frequencies according to the surrounding networking signals, which are considered to be the suppressing noise parameters. In order to restrict the signal blocking operation within the militant hub, the aerial vehicle with the network terminator is controlled to navigate within a particular boundary of a residential area and its navigation is continuously mapped and stored for effective evacuation process directed to save the innocent stranded people. A very low frequency (VLF) metal detector has been designed to trace the explosives and buried landmines inside the exploration arena. An algorithm for 3-D mapping of the metal traces detected by the aerial navigator has been presented in this paper. Signal blocking, metal tracing and stable confined movements have been tested where the testbed is provided with signals of different frequencies along with variation in dimensions of the testing region to evaluate the reliability of the proposed framework.
Received: 11 April 2018, Accepted: 02 May 2018, Published Online: 20 May 2018
1. Introduction
In order to commit crimes with ease and for ensuring household materials are to be damaged. Due to the their maximum safety with encrypted identity from exposure of Internet and wireless communication prothema law enforcement personnel, the militants choose vision, the militants supposedly utilize networking places full of common people where the abodes are sub- signals and Internet facilities to penetrate the compreurbs or localities with a dense population and resident- pensive anti-terrorist operation and they often material housing structures. During certain anti-militant realize communication with their outside accomplices drives, the first and foremost security aspect is to evac- to assist them to flee from the drive. If the terroristsbecome successful to pervade the vigilance system, they can cause unprecedented human fatalities of the stranded local people.
This paper is an extended version of the work reported in [1]. An unmanned aerial vehicle equipped with a networking signal jammer has been implemented for monitoring and controlling an anti-militant mission. The aerial vehicle is manually and semi-autonomously operated to explore within a specified region of interest with an on-board camera providing consistent video feedback and an electronic device subsuming an auto-tuning band-pass filter with a transmitter and a segregated power module. The extensions in this paper are the inclusion of a consistent 3-D mapping of the detected metallic substances, performance evaluation of the signal blocking operation in 4G networks, test-bed analysis for accurate metal tracings and deviations in 3-D navigations of the employed aerial vehicle within certain territorial regions.
The employed prototype and its motion planning algorithms are reported in [2] where to restrict the aerial exploration inside a marginalized trajectory, the path planning algorithm has been modified. The process of the autonomous concatenated map generation of the traversed region is described in [2] and [3]. The auto center frequency reconfigurable bandpass filter to substantiate networking signal jammer is based on a novel design proposed in [4] where an ultra high frequency and high quality factor integrated Gm-C technology based bandpass filter is presented which is fabricated using the modified Nauta’s Transconductor principle. Traditionally, a signal jammer enacts the role of an adaptive source of interfering noise suppressed onto a propagating message signal at the node of eavesdroppers so that the confidentiality of the relevant wireless protocol is maintained by not allowing any outsider to decode the inherent messaging information. In the papers [5]-[8] the degrading security concerns in military operations based on wireless communication, jamming based physical layer security prospects and particular environmental reliability challenges incorporated in sensor networks are reported respectively. The paper presented in [8] documents an innovative anti-deception jamming method for radar sensor networks whereas in [9] a detailed perspective analysis of the secrecy transmission capacity of hostile jammers is articulated. The paper presented in [10] describes a novel outage-based characterization approach for joint relay and jammer selection scheme in case of channel state information feedback delays.
To enhance the strength of the signal of interest in a wireless communication scheme, jamming attacks should be effectively retaliated. In the works reported in [11] and [12] the investigating methodologies related to a MIMO interference cancellation based jamming resilient system, an energy harvesting jammer to minimize secrecy outage for powered communication networks and optimal stopping theory dependent jammer selection process for secured radio networks are documented respectively.
The proposed aerial vehicular signal jamming system incorporates auto tuning band-pass filter module with consistent video surveillance and automatic map generation capabilities. The vehicle is boarded with a very low frequency discriminative metal detector circuit to trace different types of explosive materials. The locomotion of the aerial route is confined to a specified territory with the provision of manual and semiautonomous motion control algorithms. The implemented system with its salient features, applied signal jamming technique, motion control and mapping algorithms along with explosives detection technique and test-bed results are articulated in this paper sectionby-section.
2. Implemented Cyber-Vigilance System and Proposed Salient Features
The tactical security system based on unmanned aerial vehicle facilitated with networking signal jammer is solicited to be deployed in case of anti-militant and anti-terrorist drives conducted by the law enforcement agencies. The investigated methodologies, salient features and entities, control algorithms and constituents of the developed framework are articulated in the following excerpts.
2.1. Unmanned Aerial Vehicle
The detailed specifications of the aerial vehicle are described in [2] and Fig. 1 shows the demonstrated aircraft. Fig. 2 presents the vehicle at an elevation. As mentioned in [2], Q450 V3 is the main quad frame with glass fiber platform with arms constructed of polyamide nylon. There are four 820 kVA BLDC motors and for solemnizing motion and elevation control there are two normal and two pusher propellers. Being exposed to a payload of 0.5-0.55 kg and a single shot flight duration of approximately 14 minutes, the entire aerial structure weighs around 1.4 kg.
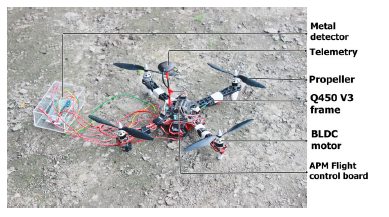 Figure 1: Employed unmanned aerial vehicle [the background is a muddy surface of the test arena]
Figure 1: Employed unmanned aerial vehicle [the background is a muddy surface of the test arena]
 Figure 2: Vehicle in flight mode
Figure 2: Vehicle in flight mode
An open source ground station application for MAV communication, called APM Mission Planner 2.0, is utilized to control the flight modes, longitude and altitude parameters of the vehicle. Mission Planner is interfaced with manual and semi-autonomous motion planning algorithms developed on C language platform with continuous data logging with the GPS waypoints and control events. As presented in [2], there is a simulation interface of the flight control phenomena and the associated tuning parameters.
2.2. Networking Signal Jammer
To block the surrounding networking signals propagating in the terrorized region, a novel band-pass filter module along with a radio transmitter is utilized as the signal jammer. To self-calibrate the jamming process, the radio transmitter is housed with the band-pass filter and the overall jammer set-up is attached to the surface of the vehicle.
According to the design considerations and technology proposed in [4], TSMC 0.18 µm CMOS fabrication process based Gm-C band-pass filter module is used where active transconductor components and six CMOS inverters are incorporated. The quality factor is maintained more than 40 and the adjustable center frequency of the operating bandwidth can be configured within the range of 797.4 MHz to 819.5 MHz. The automatic tuning procedure is enabled following an analog Phase-Locked-Loop (PLL) technique based on an adaptive integrated Voltage-Controlled-Oscillator (VCO). As described in [4], an inherently symmetric improved Nauta’s Transconductor building block is introduced.
The improved Nauti’s Tran conductor configuration, device parameters, equivalent circuit of the fabricated
Gm-C band-pass filter, analog PLL topology for automatic frequency tuning system, architecture of the adaptive VCO and relative performance evaluation are presented in [4]. The signal jammer-cum-adaptive band-pass filter module tunes its center frequencies within an approximate range of 797 MHz to 819 MHz with a unity gain and it blocks other frequency signals as the commensurate suppressing noise parameters.
The data acquisition rate of the Wi-Fi camera is constantly kept at 800 MHz and hence the video surveillance is not interrupted during the entire systematic operation.
Several band-pass filter topologies for communication media and transmission channels with low-loss, costreliability and high selectivity factors have been investigated like the work presented in [13]. This paper documents a microstrip band-pass filter with electronically tunable notch response which keeps the bandwidth within a range of 2.9 GHz to 5.8 GHz. The operating bandwidth range lies in the interest communication signal transmission range and hence this approach is not employed in this proposed vigilance system. A novel design of frequency reconfigurable transmission antennas with the provision of automatic switching features is proposed in [14] where a voltage doubler circuit is utilized to convert a Radio Frequency value to its equivalent DC reference value. In [15], a FPGA based FIR band-pass filter is proposed for satellite communication and in [16], a spectral-parameter approximation based variable digital filter with adjustable center frequencies is described. Another sophisticated technology for developing tunable bandpass filter is presented in [17] where an integrated coupled resonator optical waveguide based band-pass filter is explained for photonic signal processing. The methodologies and implemented band-pass filters in [15],[16] and [17] are not suitable for practical implementation for an aerial project because of the design complexity and very high cost of deployment.
2.3. Motion Control Algorithm of the Aerial Vehicle
Aerial navigation of the explorer is subject to control in order to ensure a reliable and effective surveillance operation. The aerodynamics enact as a key factor to determine the degrees of freedom of the aerial movement of the vehicle. Air friction and vibration of the mechanical structure are two considerable aspects in case of motion control application. The aerial exploration of the quadrotor is consistently monitored and controlled from a base station. Initially the uplifting and elevation of the vehicle are controlled manually and then a modified Point-to-Point (PTP) path planning algorithm, as described in [2], controls the aerial movement semi-autonomously. The PTP algorithm is very much similar to the process introduced in [18] where the monitoring arena is divided into several cells of uniform dimensions.
In [19] and [20], path planning algorithms of unmanned aerial vehicles offering coverage missions and geo-fencing activities are proposed respectively where energy and maneuverability constraints and multiobjective optimization principle based on a multi-gene structure are considered. Genetic algorithm formulates multi-point search space and an improved path control method is proposed in [21] which is a more sophisticated version of the customized PTP algorithm. In [22], a time optimal two-dimensional path planning approach is documented along with obstacle avoidance provision. Several sophisticated motion control techniques for unmanned aerial vehicles have been articulated in [23], [24] and [25].
The basic control algorithm to decide the navigation trajectory of the demonstrated aerial vehicle follows the one presented in [2] with a modification of insertion of three dimensional movement within a bounded arena with limited specifications. The aerial vehicle is subject to scan the maximum coverage area of the region of interest by moving from a point to its nearest point of exploration. The customized algorithm for the aerial motion control is presented in Algorithm 1. Apart form that GPS coordinates and orientation sensors embedded onto the vehicular structure enables automatic mapping of the stored position values of the navigating and continuously moving quadrotor.
Algorithm 1 Algorithm for Motion Control
Array of X-axis coordinates of center of each grid
→ X
Array of Y-axis coordinates of center of each grid
→ Y
Array of Z-axis coordinates of center of each grid
→ Z
Dummy variables → i,j,k
Maximum index of X-array → I
Maximum index of Y-array → J
Maximum index of Z-array → K Coordinates of the present grid → x,y,z INITIALIZE:
i ← 0 j ← 0 k ← 0
START: While (j < J) x ← x[i] y ← Y[j] y ← Z[k] if j%2 = 0 then i ← i +1 k ← k +1
else
i ← i −1 k ← k −1 end if if i = I and k = K then
i ← i −1 k ← k −1 j ← j +1 if i = −1 and k = −1 then
i ← i +1 k ← k +1 j ← j +1
else
Move vehicle to (x,y,z) point end if
end if Goto START
2.4. Explosives Tracing and Detection
Algorithm 2 Algorithm for 3-D Mapping of the GPS Traces of Suspicious Metals
Array of (x,y,z) coordinates → Ac
Array index → Ia
State variable → Sa
Program variable → Cp Sa ← 0 ; no change in the present state
Sa ← 1 ; change in the present state Cp ← 0 ; operation is being executed
Cp ← 1 ; operation is being terminated Present location point → (x,y,z) INITIALIZE:
X←0 ; initial x-axis location
Y←0 ; initial y-axis location
Z←0 ; initial z-axis (or elevated) location
Ia ← 0
START: Read Sa if Sa == 0 then
Ac[Ia][0][0] ← x Ac[Ia][1][0] ← y
Ac[Ia][1][1] ← z
Ia ← Ia +1 end if if Cp == 0 then for m < 0;m < Ia;m ← m+1 do x ← Ac[m][0][0] y ← Ac[m][1][0] z ← Ac[m][1][1]
x ← x +x0 y ← y +y0 z ← z +z0 x0 ← x y0 ← y
z0 ← z
plot (x,y,z) and connect with the previous points
end for
end if
Goto START
The militants can bury improvised explosive devices and landmines in a terrorized area and such malpractice can devastate the entire locality causing huge holistic fatalities of the innocent people and their belongings. To prevent such malicious activities the proposed aerial vehicle based vigilance system is provided with a metal detector circuit module which is attached to a downward inclined portion of the navigator to keep the metal sensing circuitry close to the surface of the landscape. The metal detection technique and implemented sensing system follows the one presented in [2] which contains a submersible monoloop coil and works on the principle of very low frequency electromagnetic induction. The sensing frequency of the detector is about 5.5 kHz which is suitable to detect the emanations from improvised ammos as they contain very less exposed metallic surface. The sensing depth potential of the configuration is approximately 30 to 35 cm being in elevation from the ground surface. The explorer can detect buried metals from a maximum of 35 cm elevation height measured from the ground surface. The tracing and algorithm for simultaneous 2-D mapping of the detected metal points in the explored region are described in [2]. In this paper, algorithm for consistent 3-D mapping of the scanned surfaces and detected metals has been presented. In the flight mode, aerial vehicle sends (x,y,z) location coordinates of the detected metals where the metal detecting circuit senses the presence of any suspicious material within a maximum depth potential of 35 cm above the ground. Therefore, the z-location values do not exceed 35 cm ground clearance where the x and y-location values are confined within the testing territory. Algorithm 2 shows the implemented approach to map GPS traces of the metals.
3. Results and Analysis
The developed cyber-vigilance system is assessed in different test-beds to ensure the sustainability and reliability of the aerial vehicle based networking signal jammer especially in case of accurate signal blocking activities and stable aerial motion within a confined territory.
3.1. Evaluation of the Signal Blocking Phenomenon
The implemented security system is tested in different environments with different frequency signals with co-existence of the communication signals of 2G, 3G and 4G spectra and wide fidelity (Wi-Fi) and radio frequency (RF) signals. With different combinations of co-existing signals in an arena with a dimension of 10m×10m with a flight elevation height of 12m, each time the prototype is tested for 50 times for performance evaluation in terms of accurate blocking (%) and false blocking (%), which are enumerated in Table 1. The evaluated percentages enlisted here are close approximated values.
Table 1: Evaluation of Accurate and False Signal Blocking Phenomena
| Test Signals | BA(%) | BF(%) | ||
| 2G | 96 | 4 | ||
| 2G +3G | 86 | 14 | ||
| 2G +3G +4G | 85 | 15 | ||
|
2G + 3G + Fi(800MHz) |
Wi | − | 82 | 18 |
|
2G + 3G + 4G Fi(800MHz) |
+ Wi | − | 79 | 21 |
|
2G + 3G + Fi(800MHz)+R |
Wi F | − | 78 | 22 |
|
2G + 3G + 4G + Wi Fi(800MHz)+RF |
− | 75 | 25 | |
Here BA and BF are the percent values of accurate and false blocking operations respectively and these are determined as
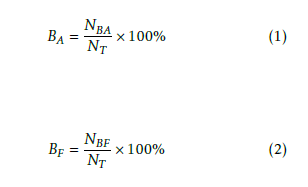 where NBA is the number of accurate blocking operations, NBF is the number of false blocking operations and NT is the total number of testing operations [NT = NBA +NBF].
where NBA is the number of accurate blocking operations, NBF is the number of false blocking operations and NT is the total number of testing operations [NT = NBA +NBF].
The aerial vehicle is solicited to different elevation heights within a certain territorial boundary of 13.5m× 13.5m and the accurate detection phenomenon is tested for 50 consecutive times for each elevation where each time a composition of 2G + 3G + Wi −
Fi(800MHz) signals is present there.
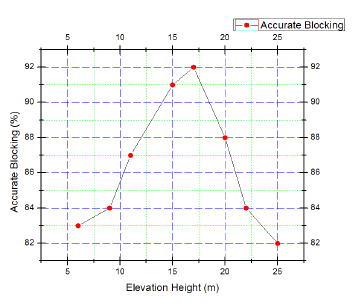 Figure 3: Evaluation of accurate blocking operation in case of different elevation heights
Figure 3: Evaluation of accurate blocking operation in case of different elevation heights
The performance evaluation of accurately blocking signals for different elevation heights is presented in Fig. 3.
Likewise the accurate blocking operation of the signal jammer is tested for different two dimensional territories with a constant elevation height of 12.5m for 50 consecutive times. The performance evaluation of accurately blocking signals for different territorial boundaries for a constant elevation height is presented in Fig. 4.
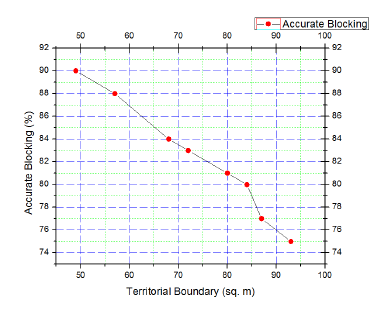 Figure 4: Evaluation of accurate blocking operation in case of different territorial boundaries with a constant elevation height
Figure 4: Evaluation of accurate blocking operation in case of different territorial boundaries with a constant elevation height
3.2. Evaluation of the Accurate Metal Tracing Phenomenon
The aerial vehicle is tested for accurate tracing of (x,y) locations of the metals within the testing boundary. In this case, z-locations of the traces are constant for 50 testing attempts. The vehicle in flight mode is controlled to navigate along a 350cm elevation height from the ground surface which is to be scanned to find metal traces. The metal detector is attached to a platform approximately 20cm underneath the main vehicular body and hence the detector senses the metals from a ground clearance of 30cm. Fig. 5 presents the performance evaluation of accurate metal tracing of (x,y) locations within the testing arena.
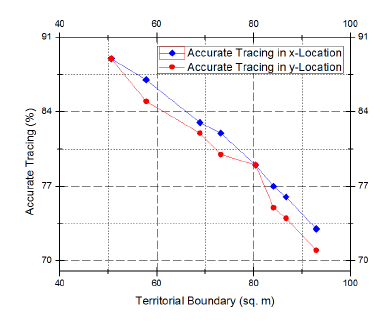 Figure 5: Evaluation of accurate metal tracing for (x,y) locations with a constant z-location value in case of different test arenas
Figure 5: Evaluation of accurate metal tracing for (x,y) locations with a constant z-location value in case of different test arenas
3.3. Evaluation of Deviations in Acceleration
According to [2], the navigation has been controlled in such a manner that the vibration of the aerial structure remains within −3 cms−2 to +3 cms−2 along x and yaxis and −5 cms−2 to −15 cms−2 along z-axis. The linear accelerometer shows some small deviations from the aforementioned standard range when the vehicle is in its flight mode. Fig. 6 presents the (x,y,z) deviations in acceleration of the vehicle. These have been derived for 50 consecutive test runs and the values are approximated from the accelerometer readings.
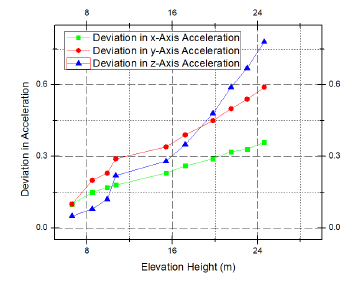 Figure 6: Evaluation of deviations of the vehicle in flight mode from the standard (x,y,z) acceleration values
Figure 6: Evaluation of deviations of the vehicle in flight mode from the standard (x,y,z) acceleration values
3.4. Evaluation of Stable Motion within a Confined Territory
The unmanned aerial vehicle is supposed to navigate within a confined region where the signal jammer blocks the networking signals with the provision of video surveillance, map generation and metal detection. The developed system is tested in terms of percentage of accurate confinement to affirm its stable aerial exploration within a certain bounded area. For each different boundary limit, the vehicle is made to explore for 20 times of assessment and the estimated accuracy of confinement in % is enlisted in Table 2.
Table 2: Evaluation of Accuracy of Confinement
| Testing Arenas (m×m×m) | CA (%) |
| 7×5.5×5 | 93 |
| 8.5×6.3×7.4 | 89 |
| 11×7.5×9.8 | 87 |
| 14×9×10.2 | 82 |
| 16.7×12.5×13 | 79 |
Here
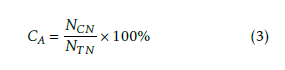 where CA is the accuracy of confinement, NCN is the number of confined navigations and NT N is the number of total navigations.
where CA is the accuracy of confinement, NCN is the number of confined navigations and NT N is the number of total navigations.
4. Conclusion
This paper articulates a novel aerial vehicle based cyber-vigilance framework capable of networking signal jamming retaliation against militants and terrorists to corner them during an anti-terrorist drive. The unconventional signal jammer consists of a auto tunable band-pass filter module to block communication signals present in the examined area. This surveillance system provides an apprehensive security system which is handy for saving innocent lives stranded in a terrorized region. The aerial prototype is equipped with ammo detection module and has a unique feature of automatic path mapping of the covered region. Accurate signal blocking operation, accurate metal detection, 3-D mapping of the metal traces and stable confined motion with sustainable aerodynamic movement are the prominent features of the proposed work. The test results corroborate the efficacy and authenticity of the developed system for application in defense missions and security drills.
- D. Chowdhury, M. Sarkar, M. Z. Haider, S. A. Fattah and C. Shahnaz, “Design and Implementation of a Cyber-Vigilance System for Anti-Terrorist Drives Based on an Unmanned Aerial Vehicular Networking Signal Jammer for Specific Territorial Security” in Humanitarian Technology Conference (R10- HTC), Dhaka Bangladesh, 2017. https://doi.org/10.1109/R10- HTC.2017.8288995
- S.A. Fattah, M. Z. Haider, D. Chowdhury, M. Sarkar, R. I. Chowdhury, M. S. Islam, R. Karim, A. Rahi, and C. Shahnaz, “An aerial landmine detection system with dynamic path and explosion mode identification features” in IEEE Global Humanitarian Technology Conference (GHTC), Seattle WA USA, 2016. https://doi.org/10.1109/GHTC.2016.7857361
- S.A. Fattah, D. Chowdhury, M. Z. Haider, M. Sarkar, M. Refat, G. Rabbi, S. B. Masud, and C. Shahnaz, “Dynamic map generating rescuer offering surveillance robotic system with autonomous path feedback capability” in IEEE Region 10 Humanitarian Technology Conference (R10-HTC), Cebu City Philippines, 2015. https://doi.org/10.1109/R10- HTC.2015.7391872
- G.Zhiqiang, L. Zhiheng, H. Zhengxiong, Z. Yonglai, and Z. Xinyuan, “A uhf cmos gm-c bandpass filter and automatic tuning design” in Academic Symposium on Optoelectronics and Microelectronics Technology and 10th Chinese- Russian Symposium on Laser Physics and Laser TechnologyOptoelectronics Technology (ASOT), Harbin China, 2010. https://doi.org/10.1109/RCSLPLT.2010.5615323
- P.J. Nicholas, J. C. Tkacheff, and C. M. Kuhns, “Measuring the operational impact of military SATCOM degradation” in Winter Simulation Conference (WSC), Washington DC USA, 2016. https://doi.org/10.1109/WSC.2016.7822342
- Y.Zou, J. Zhu, X. Wang, and V. C. M. Leung, “Improving physical-layer security in wireless communications using diversity techniques” IEEE Netw., 29(1), 42–48, 2015. https://doi.org/10.1109/MNET.2015.7018202
- J.Zhu, Y. Zou, and B. Zheng, “Physical-layer security and reliability challenges for industrial wireless sensor networks” IEEE Acce., 5, 5313–5320, 2017. https://doi.org/10.1109/ACCESS.2017.2691003
- M.Nouri, M. Mivehchy, and M. F. Sabahi, “Novel anti-deception jamming method by measuring phase noise of oscillators in lfmcw tracking radar sensor networks” IEEE Acce., 5, 11455–11467, 2017. https://doi.org/10.1109/ACCESS.2017.2655040
- C.Si, H. Sun, M. Sheng, X. Wang, and J. Li, “Physical layer security with hostile jammers and eavesdroppers: Secrecy transmission capacity” in IEEE 27th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC), Valencia Spain, 2016. https://doi.org/10.1109/PIMRC.2016.7794718
- L.Wang, Y. Cai, Y. Zou, W. Yang, and L. Hanzo, “Joint relay and jammer selection improves the physical layer security in the face of csi feedback delays” IEEE Trans. Vehi. Tech., 65(8), 6259–6274, 2016. https://doi.org/10.1109/TVT.2015.2478029
- Q.Yan, H. Zeng, T. Jiang, M. Li, Lou, and Y. T. Hou, “Jamming resilient communication using mimo interference cancellation” IEEE Trans. Info. Fore. and Secu., 11(7), 1486–1499, 2016. https://doi.org/10.1109/TIFS.2016.2535906
- Q.Gao, Y. Huo, L. Ma, X. Xing, X. Cheng, T. Jing, and H. Liu,“Optimal stopping theory based jammer selection for securing cooperative cognitive radio networks” in IEEE Global Communications Conference (GLOBECOM), Washington DC USA, 2016. https://doi.org/10.1109/GLOCOM.2016.7842096
- M.A. Mutalib, Z. Zakaria, N. A. Shairi, and W. Y. Sam, “Design of microstrip bandpass filter with electronically tunable notch response” in 26th International Conference Radioelektronika (RADIOELEKTRONIKA), Kosice Slovakia, 2016. https://doi.org/10.1109/RADIOELEK.2016.7477380
- L.Hinsz and B. D. Braaten, “A frequency reconfigurable transmitter antenna with autonomous switching capabilities” IEEE Trans. Ante. and Prop., 62(7), 3809–3813, 2014. https://doi.org/10.1109/TAP.2014.2316298
- V.Kumar, R. Mehra, and Shallu, “Reconfigurable band pass filter using kaiser window for satellite communication” in 2nd International Conference on Next Generation Computing Technologies (NGCT), Dehradun India, 2016. https://doi.org/10.1109/NGCT.2016.7877451
- S.J. Darak, A. P. Vinod, E. M. K. Lai, J. Palicot, and H. Zhang, “Linear-phase vdf design with unabridged bandwidth control over the nyquist band” IEEE Trans. Circ. and Syst. II: Expr. Brief., 61(6), 428–432, 2014. https://doi.org/10.1109/TCSII.2014.2319992
- C.Taddei, L. Zhuang, M. Hoekman, A. Leinse, R. Oldenbeuving, P. van Dijk, and C. Roeloffzen, “Fully reconfigurable coupled ring resonator-based bandpass filter for microwave signal processing” in International Topical Meeting on Microwave Photonics (MWP) and the 2014 9th Asia-Pacific Microwave Photonics Conference (APMP), Sendai Japan, 2014. https://doi.org/10.1109/MWP.2014.6994485
- I.Khoufi, P. Minet, and N. Achir, “Unmanned aerial vehicles path planning for area monitoring” in International Conference on Performance Evaluation and Modeling in Wired and Wireless Networks (PEMWN), Paris France, 2016. https://doi.org/10.1109/PEMWN.2016.7842902
- G.Gramajo and P. Shankar, “Path-planning for an unmanned aerial vehicle with energy constraint in a search and coverage mission” in IEEE Green Energy and Systems Conference (IGSEC), Long Beach CA USA, 2016. https://doi.org/10.1109/IGESC.2016.7790077
- Y.Liu, R. Lv, X. Guan, and J. Zeng, “Path planning for unmanned aerial vehicle under geo-fencing and minimum safe separation constraints” in 12th World Congress on Intelligent Control and Automation (WCICA), Guilin China, 2016. https://doi.org/10.1109/WCICA.2016.7578482
- J.Tao, C. Zhong, L. Gao, and H. Deng, “A study on path planning of unmanned aerial vehicle based on improved genetic algorithm” in 8th International Conference on Intelligent Human-Machine Systems and Cybernetics (IHMSC), Hangzhou China, 2016. https://doi.org/10.1109/IHMSC.2016.182
- J.W. Yeol and Y. W. Hwang, “Parametrization of nonlinear trajectory for time optimal 2D path planning for unmanned aerial vehicles” in 2nd International Conference on Control, Automation and Robotics (ICCAR), Hong Kong China, 2016. https://doi.org/10.1109/ICCAR.2016.7486751
- F.Lazzari, A. Buffi, P. Nepa, and S. Lazzari, “Numerical Investigation of an UWB Localization Technique for Unmanned Aerial Vehicles in Outdoor Scenarios” IEEE Sens. Journal, 17(9), 2896–2903, 2017. https://doi.org/10.1109/JSEN.2017.2684817
- T.Lee, “Geometric Control of Quadrotor UAVs Transporting a Cable-Suspended Rigid Body” IEEE Trans. Cont. Syst. Tech., 26(1), 255–264, 2018. https://doi.org/10.1109/TCST.2017.2656060
- L.L. Gomes, L. P. Leal, T. R. Oliveira, J. P. V. S. d. Cunha, and T. C. Revoredo, “Unmanned Quadcopter Control Using a Motion Capture System” IEEE Latin America Trans., 14(8), 3606– 3613, 2016. https://doi.org/10.1109/TLA.2016.7786340

