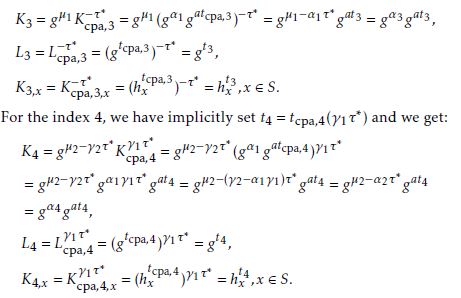Short CCA-Secure Attribute-Based Encryption
Volume 3, Issue 1, Page No 261-273, 2018
Author’s Name: Hiroaki Anada1,a), Seiko Arita2
View Affiliations
1Department of Information Security, University of Nagasaki, 851–2195, Japan
2Graduate School of Information Security, Institute of Information Security, 221–0835, Japan
a)Author to whom correspondence should be addressed. E-mail: anada@sun.ac.jp
Adv. Sci. Technol. Eng. Syst. J. 3(1), 261-273 (2018); ![]() DOI: 10.25046/aj030132
DOI: 10.25046/aj030132
Keywords: Role-based access control, Attribute-based encryption, Direct chosen-ciphertext security, Twin Diffie-Hellman
Export Citations
Chosen-ciphertext attacks (CCA) are typical threat on public-key encryption schemes. We show direct chosen-ciphertext security modification in the case of attribute-based encryption (ABE), where an ABE scheme secure against chosen-plaintext attacks (CPA) is converted into an ABE scheme secure against CCA by individual techniques. Our modification works in the setting that the Diffie-Hellman tuple to be verified in decryption is in the target group of a bilinear map. The employed techniques result in expansion of the secret-key length and the decryption cost by a factor of four, while the public-key and the ciphertext lengths and the encryption cost remain almost the same.
Received: 16 November 2017, Accepted: 16 January 2018, Published Online: 30 January 2018
1 Introduction
Access control is one of the fundamental processes and requirements in cybersecurity. Attribute-based encryption (ABE) invented by Sahai and Waters [1], where attributes mean authorized credentials, enables to realize access control which is functionally close to role-based access control (RBAC), but by encryption. In key-policy ABE (KP-ABE) introduced by the subsequent work of Goyal, Pandey, Sahai and Waters [2], a secret key is associated with an access policy over attributes, while a ciphertext is associated with a set of attributes. In a dual manner, in ciphertext-policy ABE (CP-ABE) [2, 3, 4], a ciphertext is associated with an access policy over attributes, while a secret key is associated with a set of attributes. In a KP-ABE or CP-ABE scheme, a secret key works to decrypt a ciphertext if and only if the associated set of attributes satisfies the associated access policy. The remarkable feature of ABE is attribute privacy; that is, in decryption, no information about the access policy and the identity of the secret key owner in the case of KPABE (or, the attributes and the identity of the secret key owner in the case of CP-ABE) leaks except the fact that the set of attributes satisfies the access policy. Since the proposals, it has been studied to attain certain properties such as indistinguishability against chosen-plaintext attacks (IND-CPA) in the standard model [4] and adaptive security against adversary’s choice of a target access policy [5].
In this paper1, we work through resolving a problem of constructing a shorter ABE scheme that attains indistinguishability against chosen-ciphertext attacks (IND-CCA) in the standard model. Here CCA means that an adversary can collects decryption results of ciphertexts of its choice through adversaries’ attacking. Note that “provable security” of a cryptographic primitive is now a must requirement when we employ the primitive in a system, where it means that an appropriately defined security is polynomially reduced to the hardness of a computational problem. Moreover, the CCA security of an encryption scheme is preferable to attain because the CCA security is one of the theoretically highest securities and hence the scheme can be used widely.
To capture the idea of our approach, let us recall the case of identity-based encryption (IBE). The CHK transformation of Canetti, Halevi and Katz [7] is a generic tool for obtaining IND-CCA secure IBE scheme. It transforms any hierarchical IBE (HIBE) scheme that is selective-ID IND-CPA secure [8] into an IBE scheme that is adaptive-ID IND-CCA secure [8]. A point of the CHK transformation is that it introduces a dummy identity vk that is a verification key of a one-time signature. Then a ciphertext is attached with vk and a signature σ, which is generated each time one executes encryption. In contrast, the direct chosen-ciphertext security technique for IBE of Boyen, Mei and Waters [9] is individual modification for obtaining an IND-CCA secure IBE scheme. It converts a HIBE scheme that is adaptive-ID IND-CPA secure into an IBE scheme that is adaptive-ID INDCCA secure. Though the technique needs to treat each scheme individually, the obtained scheme attains better performance than that obtained by the generic tool (the CHK transformation). Let us transfer into the case of ABE. The transformation in [10] is a generic tool for obtaining IND-CCA secure ABE scheme. It transforms any ABE scheme (with the delegatability or the verifiability [10]) that is IND-CPA secure into an ABE scheme that is IND-CCA secure. A point of their transformation is, similar to the case of IBE, that it introduces a dummy attribute vk that is a verification key of a one-time signature. Then a ciphertext is attached with vk and a signature σ. Notice here that discussing direct chosen-ciphertext security modification for ABE (in the standard model) is a missing piece. One of the reasons seems that there is an obstacle that a Diffie Hellman tuple to be verified is in the target group of a bilinear map. In that situation, the bilinear map looks of no use.
1.1 Our Contribution
A contribution is that we fill in the missing piece; we demonstrate direct chosen-ciphertext security modification in the case of the Waters CP-ABE scheme [4] and the KP-ABE scheme of Ostrovsky, Sahai and Waters [11] To overcome the above obstacle, we employ the technique of the Twin Diffie-Hellman Trapdoor Test of Cash, Kiltz and Shoup [12]. In addition, we also utilize the algebraic trick of Boneh and Boyen [13] and Kiltz [14] to reply for adversary’s decryption queries.
1.2 Related Works
Waters [4] pointed out that IND-CCA security would be attained by the CHK transformation. Gorantla, Boyd and Nieto [15] constructed a IND-CCA secure CP-ABKEM in the random oracle model. In [10] the authors proposed a generic transformation of a INDCPA secure ABE scheme into a IND-CCA secure ABE scheme. Their transformation is considered to be an ABE-version of the CHK transformation, and it is versatile. Especially, it can be applied to non-pairingbased scheme.
The Waters CP-ABE [4] can be captured as a CP-ABKEM: the blinding factor can be considered as a random one-time key. This Waters CP-ABKEM is IND-CPA secure because the Waters CP-ABE is proved to be IND-CPA secure. For theoretical simplicity, we demonstrate an individual conversion of the Waters CP-ABKEM into a CP-ABKEM which is IND-CCA secure. Then we provide a CP-ABE scheme which is IND-CCA secure. As for KP-ABE, we demonstrate an individual conversion of KP-ABKEM of Ostrovsky, Sahai and Waters [11], which is IND-CPA secure, into a KP-ABKEM which is IND-CCA secure. Then we provide a KP-ABE scheme which is IND-CCA secure.
Finally, we note that there is a remarkable work of CP-ABE schemes and KP-ABE schemes with constantsize ciphertexts [16, 17]. Our direct chosen-ciphertext security modification is not constant-size ciphertexts but a different approach for easier implementation in engineering.
1.3 Organization of the Paper
In Section 2, we survey concepts, definitions and techniques needed. In Section 3, we revisit the concept, the algorithm and the security of the twin Diffie Hellman technique. In Section 4, we construct a CCAsecure CP-ABKEM from the Waters CPA-secure CPABKEM [4], and provide a security proof. Also, we describe the encryption version, a CCA-secure CPABE. In Section 5, we construct a CCA-secure KP-ABKEM from the Ostrovsky-Sahai-Waters CPA-secure KP-ABKEM [11], and provide a security proof. Also, we describe the encryption version, a CCA-secure KPABE. In Section 6, we compare efficiency of our CP-ABE and KP-ABE schemes with the original schemes, and also, with the schemes obtained by applying the generic transformation [10] to the original schemes. In Section 7, we conclude our work.
2 Preliminaries
The security parameter is denoted λ. A prime of bit length λ is denoted p. A multiplicative cyclic group of order p is denoted G. The ring of exponent domain of G, which consists of integers from 0 to p − 1 with modulo p operation, is denoted Zp.
2.1 Bilinear Map
We remark first that our description in the subsequent sections is in the setting of a symmetric bilinear map for simplicity, but we can employ an asymmetric bilinear map instead for better efficiency as is noted in Section 6. Let G and GT be two multiplicative cyclic groups of prime order p. Let g be a generator of G and e be a bilinear map, e : G × G → GT . The bilinear map e has the following properties:
- Bilinearity: for all u,v ∈ G and a,b ∈ Zp, we have e(ua,vb) = e(u,v)ab.
- Non-degeneracy: e(g,g) , idGT (: the identity element of the group GT ).
Parameters of a bilinear map are generated by a probabilistic polynomial time (PPT) algorithm Grp on input λ: (p,G,GT ,g,e) ← Grp(λ).
Hereafter we assume that the group operation in G and GT and the bilinear map e : G × G → GT are computable in PT in λ.
2.2 Access Structure
Let U = {χ1,…,χu} be a set of attributes, or simply set U = {1,…,u} by numbering. An access structure, which corresponds to an access policy, is defined as a collection A of non-empty subsets of U; that is, A ⊂ 2U \{φ}. An access structure A is called monotone if for any B ∈ A and B ⊂ C, C ∈ A holds. The sets in A are called authorized sets, and the sets not in A are called unauthorized sets. We will consider in this paper only monotone access structures.
2.3 Linear Secret-Sharing Scheme
We only describe a linear secret-sharing scheme (LSSS) in our context of attribute-based schemes. A secret-sharing scheme Π over the attribute universe U is called linear over Zp if:
- The shares for each attribute form a vector over Zp, 2. There exists a matrix M of size l×n called the share generating matrix for Π and a function ρ which maps each row index i of M to an attribute in U = {1,…,u}: ρ : {1,…,l} → U.
To make shares, we first choose a random vector v~ = (s,y2,…,yn) ∈ Znp: s is a secret to be shared. For i = 1 to l, we calculate each share λi = v~·Mi, where Mi denotes the i-th row vector of M and · denotes the formal inner product. LSSS Π = (M,ρ) defines an access structure A through ρ.
Suppose that an attribute set S satisfies A (S ∈ A) and let IS = ρ−1(S) ⊂ {1,…,l}. Then, let {ωi ∈ Zp;i ∈ IS} be a set of constants (linear reconstruction constants) such that if {λi ∈ Zp;i ∈ IS} are valid shares of a secret s according to M, then Pi∈IS ωiλi = s. It is known that these constants {ωi}i∈IS can be found in time polynomial in l: the row size of the share-generating matrix M. If S does not satisfy A (S <A), then no such constants {ωi}i∈IS exist.
2.4 Attribute-Based Key Encapsulation Mechanism
Ciphertext-policy attribute-based key encapsulation mechanism (CP-ABKEM). A CP-ABKEM consists of four PPT algorithms (Setup, Encap, KeyGen, Decap)[1].
Setup(λ,U). A setup algorithm Setup takes as input the security parameter λ and the attribute universe U = {1,…,u}. It returns a public key PK and a master secret key MSK.
Encap(PK,A). An encapsulation algorithm Encap takes as input the public key PK and an access structure A. It returns a random string κ and its encapsulation ψ. Note that A is contained in ψ. KeyGen(PK,MSK,S). A key generation algorithm KeyGen takes as input the public key PK, the master secret key MSK and an attribute set S. It returns a secret key SKS corresponding to S. Note that S is contained in SKS.
Decap(PK,SKS,ψ). A decapsulation algorithm Decap takes as input the public key PK, an encapsulation (we also call it a ciphertext according to context) ψ and a secret key SKS. It first checks whether S ∈ A, where S and A are contained in SKS and ψ, respectively. If the check result is False, it puts κˆ =⊥. It returns a decapsulation result κˆ.
Chosen-Ciphertext Attack on CP-ABKEM. According to previous works (for example, see [15]), the chosen-ciphertext attack on a CP-ABKEM is formally defined as the indistinguishability game (IND-CCA game). In this paper, we consider the selective game on a target access structure (IND-sel-CCA game); that is, the adversary A declares a target access structure∗
A before A receives a public key PK, which is defined as the following experiment.
Experimentind-sel-ccaA,CP-ABKEM(λ,U)∗
A ← A(λ,U),(PK,MSK) ← Setup(λ,U)
← AKeyGen(PK,MSK,·),Decap(PK,SK·,·)(PK)
(κ∗,ψ∗) ← Encap(PK,A∗),κ ← KeySp(λ),b ← {0,1} If b = 1 then κ˜ = κ∗ else κ˜ = κ
b0 ← AKeyGen(PK,MSK,·),Decap(PK,SK·,·)(κ,ψ˜ ∗)
If b0 = b then return Win else return Lose.
In the above experiment, two kinds of queries are issued by A. One is key-extraction queries. Indicating an attribute set Si, A queries its key-extraction oracle KeyGen(PK,MSK,·) for the secret key SKSi . Here we do not require any input attribute sets Si1 and Si2 to be distinct. Another is decapsulation queries. Indicating a pair (Sj,ψj) of an attribute set and an encapsulation, A queries its decapsulation oracle Decap(PK, SK·,·) for the decapsulation result κˆj. Here an access structure Aj, which is used to generate an encapsulation ψj, is implicitly included in ψj. In the case that S <A, κˆj =⊥ is replied to A. Both kinds of queries are at most qk and qd times in total, respectively, which are polynomial in λ.
The access structure A∗ declared by A is called a target access structure. Two restrictions are imposed on A concerning A∗. In key-extraction queries, each attribute set Si must satisfy Si <A∗. In decapsulation queries, each pair (Sj,ψj) must satisfy Sj <A∗ ∨ ψj , ψ∗.
The advantage of the adversary A over CP-ABKEM in the IND-CCA game is defined as the following probability:
Advind-sel-ccaA,CP-ABKEM(λ,U) def= Pr[Experimentind-sel-ccaA,CP-ABKEM(λ,U) returns Win].
CP-ABKEM is called selectively secure against chosenciphertext attacks if, for any PPT adversary A and for any attribute universe U, Advind-sel-ccaA,CP-ABKEM(λ,U) is negligible in λ. Here we must distinguish the two cases; the case that U is small (i.e. |U| = u is bounded by a polynomial of λ) and the case that U is large (i.e. u is not necessarily bounded by a polynomial of λ). We assume the small case in this paper.
In the indistinguishability game against chosenplaintext attack (IND-CPA game), the adversary A issues no decapsulation query (that is, qd = 0).
Ciphertext-Policy Attribute-Based Encryption Scheme (CP-ABE). In the case of the encryption version (i.e. CP-ABE), Encap(PK,A) and Decap(PK,SKS,ψ) are replaced by PPT algorithms Encrypt(PK,A,m) and Decrypt(PK,SKS,CT), respectively, where m and CT mean a message and a ciphertext, respectively.
The IND-CCA game for CP-ABE is defined in the same way as for CP-ABKEM above, except the following difference. In Challenge phase, the adversary A submits two equal length messages (plaintexts) m0 and m1. Then the challenger flips a coin b ∈ {0,1} and gives an encryption result CT of mb to A. In Guess phase, the adversary A returns b0 ∈ {0,1}. If b0 = b, then A wins in the IND-CCA game. Otherwise, A loses.
Key-Policy Attribute-Based Key Encapsulation
Mechanism (KP-ABKEM) and Encryption Scheme (KP-ABE). The key-policy case is analogously defined as the case of the ciphertext-policy case. We state only the syntax and the security experiment of the key-policy ABKEM.
Setup(λ,U). A setup algorithm Setup takes as input the security parameter λ and the attribute universe U = {1,…,u}. It returns a public key PK and a master secret key MSK.
Encap(PK,S). An encapsulation algorithm Encap takes as input the public key PK and an attribute set S. It returns a random string κ and its encapsulation ψ. Note that S is contained in ψ.
KeyGen(PK,MSK,A). A key generation algorithm KeyGen takes as input the public key PK, the master secret key MSK and an access structure A. It returns a secret key SKA corresponding to S. Note that A is contained in SKA.
Decap(PK,SKA,ψ). A decapsulation algorithm Decap takes as input the public key PK, an encapsulation (we also call it a ciphertext according to context) ψ and a secret key SKA. It first checks whether S ∈ A. If the check result is False, it puts κˆ =⊥. It returns a decapsulation result κˆ.
Chosen-Ciphertext Attack on KP-ABKEM. The selective game on a target attribute set (IND-sel-CCA game) is defined by the following experiment.
Experimentind-sel-ccaA,KP-ABKEM(λ,U)
S∗ ← A(λ,U),(PK,MSK) ← Setup(λ,U)
← AKeyGen(PK,MSK,·),Decap(PK,SK·,·)(PK)
(κ∗,ψ∗) ← Encap(PK,S∗),κ ← KeySp(λ),b ← {0,1} If b = 1 then κ˜ = κ∗ else κ˜ = κ
b0 ← AKeyGen(PK,MSK,·),Decap(PK,SK·,·)(κ,ψ˜ ∗)
If b0 = b then return Win else return Lose.
2.5 Target Collision Resistant Hash Functions
Target collision resistant (TCR) hash functions [18] are treated as a family. Let us denote a function family as Hfam(λ) = {Hµ}µ∈HKey(λ). Here HKey(λ) is a hash key space, µ ∈ HKey(λ) is a hash key and Hµ is a function from {0,1}∗ to {0,1}λ. We may assume that Hµ is from {0,1}∗ to Zp, where p is a prime of length λ.
Given a PPT algorithm CF , a collision finder, we consider the following experiment (the target collision resistance game).
ExperimenttcrCF ,Hfam(λ)
m∗ ← CF (λ),µ ← HKey(λ),m ← CF (µ)
If m∗ , m ∧ Hµ(m∗) = Hµ(m) then return Win else return Lose.
Then we define CF ’s advantage over Hfam in the game of target collision resistance as follows.
AdvtcrCF ,Hfam(λ)
def= Pr[ExperimenttcrCF ,Hfam(λ) returns Win].
We say that Hfam is a TCR function family if, for any
PPT algorithm CF , AdvtcrCF ,Hfam(λ) is negligible in λ.
TCR hash function families can be constructed based on the existence of a one-way function [18].
3 The Twin Diffie-Hellman Technique Revisited
A 6-tuple (g,X1,X2,Y,Z1,Z2) ∈ G6 is called a twin Diffie-Hellman tuple if the tuple is written as (g,gx1,gx2,gy,gx1y,gx2y) for some elements x1,x2,y in
Zp. In other words, a 6-tuple (g,X1,X2,Y,Z1,Z2) is a twin Diffie-Hellman tuple (twin DH tuple, for short) if Y = gy and Z1 = X1y and Z2 = X2y.
The following lemma of Cash, Kiltz and Shoup will be used in the security proof to decide whether a tuple is a twin DH tuple or not.
Lemma 1 (“Trapdoor Test”[12]) Let X1,r,s be mutually independent random variables, where X1 takes values in G, and each of r,s is uniformly distributed over Zp. Define the random variable X2 = X1−rgs. Suppose that Y,ˆ Zˆ1,Zˆ2 are random variables taking values in G, each of which is defined independently of r. Then the probability that the truth value of Zˆ1rZˆ2 = Yˆ s does not agree with the truth value of (g,X1,X2,Y,ˆ Zˆ1,Zˆ2) being a twin DH tuple is at most 1/p. Moreover, if (g,X1,X2,Y,ˆ Zˆ1,Zˆ2) is a twin DH tuple, then Zˆ1rZˆ2 = Yˆ s certainly holds.
Note that Lemma 1 is a statistical property. Especially, Lemma 1 holds without any number theoretic assumption. To be precise, we consider the following experiment of an algorithm Cheat with unbounded computational power (not limited to PPT), where Cheat, given a triple (g,X1,X2), tries to complete a 6-tuple (g,X1,X2,Y,ˆ Zˆ1,Zˆ2) which passes the “Trapdoor Test” but which is not a twin DH tuple.
ExperimenttwinDH-testCheat,G (λ)
(g,X1) ← G2,(r,s) ← Zrgs
G3 3 (Y,ˆ Zˆ1,Zˆ2) ← Cheat(g,X1,X2)
If Zˆ1rZˆ2 = Yˆ s ∧ (g,X1,X2,Y,ˆ Zˆ1,Zˆ2) is NOT a twin DH tuple,
then return Win else return Lose
Let us define the advantage of Cheat over G as follows.
AdvtwinDH-testCheat,G (λ)
def= Pr[ExperimenttwinDH-testCheat,G (λ) returns Win].
Now we are ready to complement Lemma 1.
Lemma 2 (Complement for “Trapdoor Test” [12]) For any algorithm Cheat with unbounded computational power, AdvtwinDH-testCheat,G (λ) is at most 1/p.
For a proof of Lemma 2, see Appendix A.
4 Securing the Waters CP-ABKEM against Chosen-Ciphertext Attacks
In this section, we describe our direct chosenciphertext security technique by applying it to the Waters CP-ABE [4].
Overview of Our Modification The Waters CP-ABE is proved to be secure in the IND-sel-CPA game [4]. We convert it into a scheme that is secure in the INDsel-CCA game by employing the Twin Diffie-Hellman technique of Cash, Kiltz and Shoup [12] and the algebraic trick of Boneh and Boyen [13] and Kiltz [14].
In encryption, a ciphertext becomes to contain additional two elements (d1,d2), which function in decryption as a “check sum” to verify that a tuple is certainly a twin DH tuple.
In security proof, the Twin Diffie-Hellman Trapdoor Test does the function instead. It is noteworthy that we are unable to use the bilinear map instead because the tuple to be verified is in the target group. In addition, the algebraic trick enables to answer for adversary’s decryption queries. Note also that the both technique become compatible by introducing random variables.
Key Encapsulation and Encryption. The Waters CP-ABE can be captured as a CP-ABKEM: the blinding factor of the form e(g,g)αs in the Waters CP-ABE can be considered as a random one-time key. So we call it the Waters CP-ABKEM hereafter and denote it as CP-ABKEMcpa. Likewise, we distinguish parameters and algorithms of CP-ABKEMcpa by the index cpa. For theoretical simplicity, we first develop a KEM CP-ABKEM.
4.1 Our Construction
Our CP-ABKEM consists of the following four PPT algorithms (Setup, Encap, KeyGen, Decap). Roughly speaking, the Waters original scheme CP-ABKEMcpa (the first scheme in [4]) corresponds to the case k = 1 below excluding the “check sum” (d1,d2).
Setup(λ,U). Setup takes as input the security parameter λ and the attribute universe U = {1,…,u}. It runs Grp(λ) to get (p,G,GT ,g,e), where G and GT are cyclic groups of order p, e : G × G → GT is a bilinear map and g is a generator of G. These become public parameters. Then Setup chooses u random group elements h1,…,hu ∈ G that are associated with the u attributes. In addition, it chooses random exponents αk ∈ Zp,k = 1,…,4,a ∈ Zp and a hash key η ∈ HKey(λ). The public key is published as PK = (g,ga,h1,…,hu,e(g,g)α1,…,e(g,g)α4,η). The authority sets MSK = (gα1,…,gα4) as the master secret key.
Encap(PK,A). The encapsulation algorithm Encap takes as input the public key PK and an LSSS access structure A = (M,ρ), where M is an l × n matrix and ρ is the function which maps each row index i of M to an attribute in U = {1,…,u}. Encap first chooses a random value s ∈ Zp that is the encryption randomness, and chooses random values y2,…,yn ∈ Zp. Then Encap forms a vector v~ = (s,y2,…,yn). For i = 1 to l, it calculates λi = v~ · Mi, where Mi denotes the i-th row vector of M. In addition, Encap chooses random values r1,…,rl ∈ Zp. Then, a pair of a random onetime key and its encapsulation (κ,ψ) is computed as follows.
Put C0 = gs;For i = 1 to l : Ci = gaλi hρ−(rii),Di = gri ; ψcpa = (A,C0,((Ci,Di);i = 1,…,l)),τ ← Hη(ψcpa); For k = 1 to 4 : κk = e(g,g)αks;d1 = κ1τκ3,d2 = κ2τκ4; (κ,ψ) = (κ1,(ψcpa,d1,d2)).
KeyGen(MSK,PK,S). The key generation algorithm KeyGen takes as input the master secret key MSK, the public key PK and a set S of attributes. KeyGen first chooses a random tk ∈ Zp,k = 1,…,4. It generates the secret key SKS as follows.
For k = 1 to 4 : Kk = gαk gatk ,Lk = gtk
For x ∈ S : Kk,x = htxk ;
SKS = ((Kk,Lk,(Kk,x;x ∈ S));k = 1,…,4).
Decap(PK,ψ,SKS). The decapsulation algorithm Decap takes as input the public key PK, an encapsulation ψ for an access structure A = (M,ρ) and a private key SKS for an attribute set S. It first checks whether S ∈ A. If the result is False, put κˆ =⊥. Otherwise, let IS = ρ−1(S) ⊂ {1,…,l} and let {ωi ∈ Zp;i ∈ IS} be a set of linear reconstruction constants. Then, the decapsulation κˆ is computed as follows.
Parse ψ into (ψcpa = (A,C0,((Ci,Di);i = 1,…,l)),d1,d2); τ ← Hη(ψcpa);
For k = 1 to 4 : κˆk = e(C0,Kk)/ Y(e(Lk,Ci)e(Di ωi = e(g,g)αks,Kk,ρ(i)))
i∈IS
If κˆ1τκˆ3 , d1 ∨ κˆ2τκˆ4 , d2, then put κˆ =⊥,else put κˆ = κˆ1.
4.2 Security and Proof
Theorem 1 If the Waters CP-ABKEMcpa [4] is selectively secure against chosen-plaintext attacks and an employed hash function family Hfam has target collision resistance, then our CP-ABKEM is selectively secure against chosenciphertext attacks. More precisely, for any given PPT adversary A that attacks CP-ABKEM in the IND-sel-CCA game where decapsulation queries are at most qd times, and for any small attribute universe U, there exist a PPT adversary B that attacks CP-ABKEMcpa in the IND-selCPA game and a PPT target collision finder CF on Hfam that satisfy the following tight reduction.
Advind-sel-ccaA,CP-ABKEM(λ,U)
ind-sel-cpa tcr (λ)+ qd .
≤AdvB,CP-ABKEMcpa(λ,U)+AdvCF ,Hfam p
Proof. Given any adversary A that attacks our scheme CP-ABKEM in the IND-sel-CCA game, we construct an adversary B that attacks the Waters scheme
CP-ABKEMcpa in the IND-sel-CPA game as follows. Commit to a Target Access Structure. B is given (λ,U) as inputs, where λ is the security parameter and U = {1,…,u} is the attribute universe. B invokes A on input (λ,U) and gets a target access structure
A = (M ,ρ ) from A, where M is of size l × n . B uses A∗ as the target access structure of itself and outputs A∗.
Setup. In return to outputting A∗, B receives the public key PKcpa for CP-ABKEMcpa, which consists of the following components.
PKcpa = (g,ga,h1,…,hu,e(g,g)α).
To set up a public key PK for CP-ABKEM, B herein needs a challenge instance: B queries its challenger and gets a challenge instance (κ,ψ˜ ). It consists of the following components.
κ˜ = e(g,g)αs∗ OR a random one-time key κ ∈ KeySp(λ),
gs∗,((Ci∗,Di∗);i = 1,…,l∗)).
Then B makes the rest of parameters of PK as follows.
Choose η ← HKey(λ) and take τ∗ ← H);
Put e(g,g)α1 = e(g,g)α;
Choose γ1,γ2 ← Zp, put e(g,g)α2 = e(g,g)γ2/e(g,g)α1γ1;
Choose µ1,µ2 ← Zp, put e(g,g)α3 = e(g,g)µ1/e(g,g)α1τ∗,
e(g,g)α4 = e(g,g)µ2/e(g,g)α2τ∗.
Note we have implicitly set relations in the exponent domain:
α2 = γ2 − α1γ1, α3 = µ1 − α1τ∗, α4 = µ2 − α2τ∗ = µ2 − (γ2 − α1γ1)τ∗. (1) A public key PK for CP-ABKEM become:
PK = (PKcpa,e(g,g)α2,e(g,g)α3,e(g,g)α4,η).
Then B inputs PK into A. Note that PK determines the corresponding MSK uniquely.
Phase 1. B answers for two types of A’s queries as follows.
(1) Key-Extraction Queries. In the case that A issues a key-extraction query for an attribute set S ⊂ U, B has to simulate A’s challenger. To do so, B issues keyextraction queries to B’s challenger for S repeatedly up to four times. As replies, B gets four secret keys of the Waters CP-ABKEMcpa for a single attribute set S:
SKcpa,S,k = (Kcpa,k,Lcpa,k,(Kcpa,k,x;x ∈ S)),k = 1,…,4.
We remark that, according to the randomness in the key-generation algorithm of the Waters CP-ABKEMcpa, all four secret keys SKcpa,S,1,…,SKcpa,S,4 are random and mutually independent. To reply a secret key SKS of our CP-ABKEM to A, B converts the four secret keys as follows.
K1 = Kcpa,1, L1 = Lcpa,1, K1,x = Kcpa,1,x,x ∈ S; K2 = gγ2Kcpa−γ1,2, L Kcpa−γ,x, x ∈ S;
K, L Kcpaτ∗ ,3,x, x ∈ S;
K Kcpaγ1τ,∗4,x, x ∈ S.
Then B replies SKS = ((Kk,Lk,(Kk,x;x ∈ S));k = 1,…,4) to A.
(2) Decapsulation Queries. In the case that A issues a decapsulation query for (S,ψ), where S ⊂ U is an attribute set and ψ = (ψcpa,d1,d2) is an encapsulation concerning A, B has to simulate A’s challenger. To do so, B computes the decapsulation result κˆ as follows.
If S <A then put κˆ =⊥,
else
τ ← Hη(ψcpa);
Yˆ = e(C0,g)τ−τ∗,Zˆ1 = d1/e(C0,g)µ1,Zˆ2 = d2/e(C0,g)µ2;
If Zˆ1γ1Zˆ2 , Yˆ γ2 (: call this checking TwinDH-Test) then put κˆ = κˆ1 =⊥
else
If τ = τ∗ then abort (: call this case Abort) else κˆ = κˆ1 = Zˆ11/(τ−τ∗).
Challenge. In the case that A queries its challenger for a challenge instance, B makes a challenge instance as follows.
Put d;
Put ψ ψ ,d .
Then B feeds (κ,ψ˜ ∗) to A as a challenge instance.
Phase 2. The same as in Phase 1.
Guess. In the case that A returns A’s guess b˜, B returns b˜ itself as B’s guess.
In the above construction of B, B can perfectly simulate the real view of A until the case Abort happens, except for a negligible case, and hence the algorithm A works as designed. To see the perfect simulation with a negligible exceptional case, we are enough to prove the following seven claims.
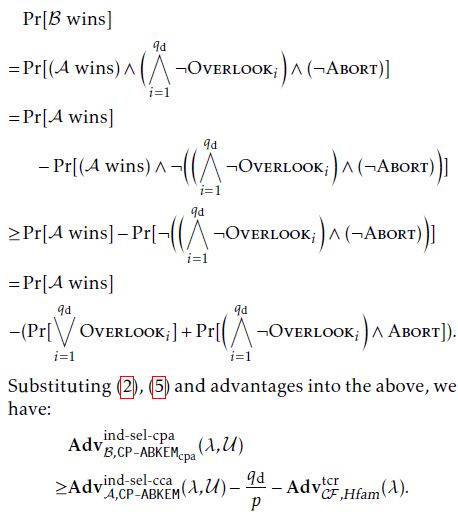
Claim 1 The reply SKS = ((Kk,Lk,(Kk,x;x ∈ S));k = 1,…,4) for a key-extraction query of A is a perfect simulation.
Proof. We must consider the implicit relations (1). For the index 2, we have implicitly set the randomness t2 = tcpa,2(−γ1) and we get:
K2 = gγ2Kgatcpa,2)−γ1
= gγ2(gα1gat2/(−γ1))−γ1 = gγ2−α1γ1gat2 = gα2gat2,
Lgtcpa,2)−γ1 = gt2,
−γ1 tcpa,2
K2,x = Kcpa,2,x = (hx )S.
For the index 3 and 4, see Appendix B.
Claim 2 (e(g,g), e(g,g)α1, e(g,g)α2, Y,ˆ Zˆ1, Zˆ2) is a twin Diffie-Hellman tuple if and only if (e(g,g), e(g,g)α1τe(g,g)α3, e(g,g)α2τe(g,g)α4, e(C0,g), d1, d2) is a twin Diffie-Hellman tuple.
Proof. This claim can be proved by a short calculation.
See Appendix C.
Claim 3 If (e(g,g),e(g,g)α1,e(g,g)α2,Y,ˆ Zˆ1,Zˆ2) is a twin
Diffie-Hellman tuple, then (Y,ˆ Zˆ1,Zˆ2) certainly passes the TwinDH-Test: Zˆ1γ1Zˆ2 = Yˆ γ2.
Proof. This claim is a direct consequence of Lemma 1.
Claim 4 Consider the following event which we name as Overlooki:
In the i-th TwinDH-Test, the following condition holds:
|
|
Zˆ1γ1Zˆ2 = Yˆ γ2 holds and
(e(g,g),e(g,g)α1,e(g,g)α2,Y,ˆ Zˆ1,Zˆ2) is NOT a twin DH tuple. |
Then, for at most qd times decapsulation queries of A, the probability that at least one Overlooki occurs is negligible in λ. More precisely, the following inequality holds:
qd
_
Pr[ Overlooki] ≤ qd/p. (2) i=1
Proof. To apply Lemma 2, we construct an algorithm Cheatλ,U with unbounded computational power, which takes as input (e(g,g),e(g,g)α1,e(g,g)α2) and returns (Y,ˆ Zˆ1,Zˆ2) employing the adversary A as a subroutine. Fig. 1 shows the construction.
First, note that the view of A in Cheatλ,U is the same as the real view of A and hence the algorithm A works as designed.
Second, note that the return (Y,ˆ Zˆ1,Zˆ2) of Cheatλ,U is randomized in TABLE. Hence:
qd qd X 1 1 X
Pr[Overlooki] = Pr[Overlooki] i=1 qd qd i=1
=AdvtwinDH-testCheatλ,U ,G (λ). (3)
Third, applying Lemma 2 to Cheatλ,U , we get:
AdvtwinDH-testCheatλ,U ,G (λ) ≤ 1/p. (4)
Combining (3) and (4), we have:
qd qd
_ X
Pr[ Overlooki] ≤ Pr[Overlooki] i=1 i=1
≤qdAdvtwinDH-testCheatλ,U ,G (λ) ≤ qpd .
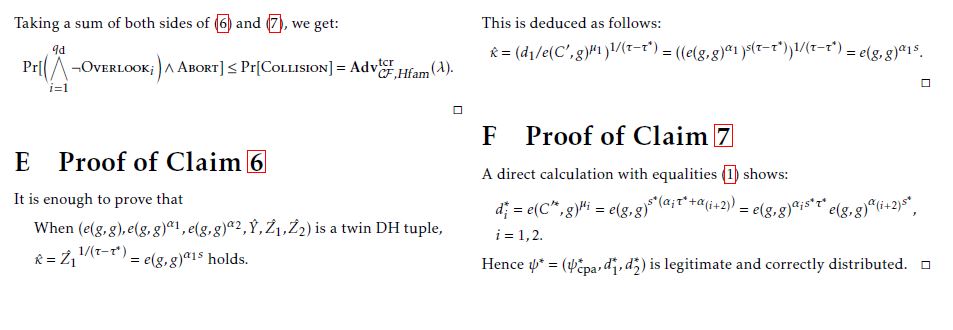
Claim 5 The probability that Overlooki never occurs in TwinDH-Test for every i and Abort occurs is negligible in λ. More precisely, the following inequality holds:
qd
Pr[^¬Overlooki ∧ Abort] ≤ AdvtcrCF ,Hfam(λ). (5) i=1
Proof. This claim is proved by constructing a collision finder CF on Hfam. See Appendix D.
Claim 6 The reply κˆ to A as an answer for a decapsulation query is correct.
Claim 7 The challenge instance is correctly distributed.
Proof. These two claims are proved by a direct calculation. See Appendices E and F, respectively.
Evaluation of the Advantage of B. Now we are ready to evaluate the advantage of B in the IND-sel-CPA game. That A wins in the IND-sel-CCA game means that (κ,ψ˜ ∗ )) is correctly guessed. This is equivalent to that (κ,ψ˜ cpa∗ ) is correctly guessed because determines the consistent blinding factor κ∗ = e(g,g)αs∗ uniquely. This means that B wins in the IND-sel-CPA game.
 Figure 1: An Algorithm Cheatλ,U with Unbounded Computational Power for a Proof of Claim 4.
Figure 1: An Algorithm Cheatλ,U with Unbounded Computational Power for a Proof of Claim 4.
Therefore, the probability that B wins is equal to the probability that A wins, Overlooki never holds in TwinDH-Testfor each i and Abort never occurs. So we have:
This is what we should prove in Theorem 1.
4.3 Encryption Scheme from KEM
It is straightforward to construct our encryption scheme CP-ABE from CP-ABKEM. The IND-sel-CCA security of CP-ABE is proved based on IND-sel-CPA security of the Waters KEM CP-ABKEMcpa. Setup(λ,U). The same as Setup of CP-ABKEM.
Encrypt(PK,A,m). The same as Encap of CP-ABKEM except that Encrypt multiplies m by the blinding factor κ in the group GT . Encrypt returns CT = (C = mκ,ψ = (ψcpa,d1,d2)).
KeyGen(MSK,PK,S). The same as KeyGen of
CP-ABKEM.
Decrypt(PK,CT,SKS). The same as Decap of CP-ABKEM except that Decrypt divides out C by the decapsulated blinding factor κˆ. Decrypt returns the result mˆ.
4.4 Security and Proof
Theorem 2 If the Waters CP-ABKEMcpa [4] is selectively secure against chosen-plaintext attacks and an employed hash function family Hfam has target collision resistance, then our CP-ABE is selectively secure against chosenciphertext attacks. More precisely, for any given PPT adversary A that attacks CP-ABE in the IND-sel-CCA game where decryption queries are at most qd times, and for any small attribute universe U, there exist a PPT adversary B that attacks CP-ABKEMcpa in the IND-sel-CPA game and a PPT target collision finder CF on Hfam that satisfy the following inequality.
Advind-sel-ccaA,CP-ABE (λ,U)
≤2AdvBind-sel-cpa,CP-ABKEMcpa(λ,U)+AdvtcrCF ,Hfam(λ)+ qpd .
Proof. Given any adversary A that attacks our scheme CP-ABE in the IND-sel-CCA game, we construct an adversary B that attacks the Waters KEM CP-ABKEMcpa in the IND-sel-CPA game as follows. Commit to a Target Access Structure. The same as that of CP-ABKEM.
Setup. In return to outputting A∗, B receives the public key PKcpa for CP-ABKEMcpa. To set up a public key PK for CP-ABE, B herein needs a challenge instance:
B queries its challenger and gets a challenge instance
). The rest of procedure is the same as that of
CP-ABKEM, and B inputs PK into A. Phase 1. The same as that of CP-ABKEM except that B replies a decrypted message mˆ to A for a decryption query.
Challenge. In the case that A submits two plaintexts
) of equal length, B makes a challenge ciphertext CT as follows and feeds CT∗ to A.
Choose b0 ← {0,1}, put C˜∗ = m∗b0 κ˜;
Put d(C0∗,g)µ1,d2∗ = e(C0∗,g)µ2;
Put CT.
Phase 2. The same as in Phase 1.
Guess. In the case that A returns A’s guess b˜, B returns b˜ as B’s guess.
Evaluation of the Advantage of B. A standard argument deduces a loss of tightness by a factor of 1/2. That is;
ind-sel-cpa
AdvB,CP-ABKEMcpa(λ,U)
≥12Advind-sel-ccaA,CP-ABE (λ,U) − qpd − AdvtcrCF ,Hfam(λ).
5 Securing the Ostrovsky-SahaiWaters KP-ABKEM against Chosen-Ciphertext Attacks
In this section, we describe our direct chosenciphertext security modification by applying it to the Ostrovsky-Sahai-Waters KP-ABE [11]. Overview of Our Modification The Ostrovsky-Sahai-Waters KP-ABE is proved to be secure in the IND-selCPA game [11]. We convert it into a scheme that is secure in the IND-sel-CCA game by employing the Twin Diffie-Hellman technique of Cash, Kiltz and Shoup [12] and the algebraic trick of Boneh and Boyen [13] and Kiltz [14].
In encryption, a ciphertext becomes to contain additional two elements (d1,d2), which function in decryption as a “check sum” to verify that a tuple is certainly a twin DH tuple.
In security proof, the Twin Diffie-Hellman Trapdoor Test does the function instead. It is noteworthy that we are unable to use the bilinear map instead because the tuple to be verified is in the target group. In addition, the algebraic trick enables to answer for adversary’s decryption queries. Note also that the both technique become compatible by introducing random variables.
Key Encapsulation and Encryption. The Ostrovsky-Sahai-Waters KP-ABE can be captured as a KP-ABKEM: the blinding factor of the form e(g,g)aαs in the Ostrovsky-Sahai-Waters KP-ABE can be considered as a random one-time key. So we call it the Ostrovsky-Sahai-Waters KP-ABKEM hereafter and denote it as KP-ABKEMcpa. Likewise, we distinguish parameters and algorithms of KP-ABKEMcpa by the index cpa. For theoretical simplicity, we first develop a KEM KP-ABKEM.
5.1 Our Construction
Our KP-ABKEM consists of the following four PPT algorithms (Setup, Encap, KeyGen, Decap). Roughly speaking, the Ostrovsky-Sahai-Waters original scheme KP-ABKEMcpa (the first scheme in [11]) corresponds to the case k = 1 below excluding the “check sum” (d1,d2).
Setup(λ,U). Setup takes as input the security parameter λ and the attribute universe U = {1,…,u}. It runs Grp(λ) to get (p,G,GT ,g,e), where G and GT are cyclic groups of order p, e : G → GT is a bilinear map and g is a generator of G. These become public parameters. Then Setup chooses u random group elements h1,…,hu ∈ G that are associated with the u attributes. In addition, it chooses random exponents αk ∈ Zp,k = 1,…,4,a ∈ Zp and a hash key η ∈ HKey(λ). The public key is published as PK = (g,ga,h1,…,hu,e(g,g)aα1,…,e(g,g)aα4,η). The authority sets MSK = (α1,…,α4) as the master secret key. Encap(PK,S). The encapsulation algorithm Encap takes as input the public key PK and a set S of attributes. Encap first chooses a random value s ∈ Zp that is the encryption randomness. Then, a pair of a random one-time key and its encapsulation (κ,ψ) is computed as follows.
Put C0 = gs;For x ∈ S : Cx = hsx ψcpa = (S,C0,(Cx;x ∈ S)),τ ← Hη(ψcpa); For k = 1 to 4 : κk = e(g,g)aαks;d1 = κ1τκ3,d2 = κ2τκ4; (κ,ψ) = (κ1,(ψcpa,d1,d2)).
KeyGen(MSK,PK,A). The key generation algorithm KeyGen takes as input the master secret key MSK, the public key PK and an LSSS access structure A = (M,ρ), where M is an l ×n matrix and ρ is the function which maps each row index i of M to an attribute in U = {1,…,u}. For k = 1 to 4, KeyGen first chooses random values yk,2,…,yk,n ∈ Zp and forms a vector v~k = (αk,yk,2,…,yk,n). Then, for i = 1 to l, it calculates λk,i = v~k · Mi, where Mi denotes the i-th row vector of M, and it chooses random values rk,i ∈ Zp. KeyGen generates the secret key SKA as follows.
For k = 1 to 4 : For l = 1 to l :
Kk,i = gaλk,i hrρk,i(i),Lk,i = grk,i
SKA = (((Kk,i,Lk,i);i = 1,…,l)k = 1,…,4).
Decap(PK,ψ,SKA). The decapsulation algorithm Decap takes as input the public key PK, an encapsulation ψ for an attribute set S and a private key SKA for an access structure A = (M,ρ). It first checks whether S ∈ A. If the result is False, put κˆ =⊥. Otherwise, let IS = ρ−1(S) ⊂ {1,…,l} and let {ωi ∈ Zp;i ∈ IS} be a set of linear reconstruction constants. Then, the decapsulation κˆ is computed as follows.
Parse ψ into (ψcpa = (S,C0,(Cx;x ∈ S)),d1,d2); τ ← Hη(ψcpa);
For k = 1 to 4 :
Y 0 ωi
κˆk = (e(C ,Kk,i)/e(Lk,i,Cρ(i))) = e(g,g)aαks
i∈IS
If κˆ1τκˆ3 , d1 ∨ κˆ2τκˆ4 , d2, then put κˆ =⊥,else put κˆ = κˆ1.
5.2 Security and Proof
Theorem 3 If the Ostrovsky-Sahai-Waters KP-ABKEMcpa [11] is selectively secure against chosen-plaintext attacks and an employed hash function family Hfam has target collision resistance, then our KP-ABKEM is selectively secure against chosen-ciphertext attacks. More precisely, for any given PPT adversary A that attacks KP-ABKEM in the IND-sel-CCA game where decapsulation queries are at most qd times, and for any small attribute universe U, there exist a PPT adversary B that attacks KP-ABKEMcpa in the IND-sel-CPA game and a PPT target collision finder CF on Hfam that satisfy the following tight reduction.
Advind-sel-ccaA,KP-ABKEM(λ,U)
≤AdvBind-sel-cpa,KP-ABKEMcpa(λ,U)+AdvtcrCF ,Hfam(λ)+ qpd .
Proof. We will omit the description of the proof because the proof goes analogously to the case of CP-
ABKEM in Section 4.2.
5.3 Encryption Scheme from KEM
It is straightforward to construct our encryption scheme KP-ABE from KP-ABKEM. The IND-sel-CCA security of KP-ABE is proved based on IND-sel-CPA security of the Waters KEM KP-ABKEMcpa. Setup(λ,U). The same as Setup of KP-ABKEM. Encrypt(PK,A,m). The same as Encap of KP-ABKEM except that Encrypt multiplies m by the blinding factor κ in the group GT . Encrypt returns CT = (C = mκ,ψ = (ψcpa,d1,d2)).
KeyGen(MSK,PK,S). The same as KeyGen of
KP-ABKEM.
Decrypt(PK,CT,SKS). The same as Decap of KP-ABKEM except that Decrypt divides out C by the decapsulated blinding factor κˆ. Decrypt returns the result mˆ.
5.4 Security and Proof
Theorem 4 If the Ostrovsky-Sahai-Waters KP-ABKEMcpa [11] is selectively secure against chosen-plaintext attacks and an employed hash function family Hfam has target collision resistance, then our KP-ABE is selectively secure against chosen-ciphertext attacks. More precisely, for any given PPT adversary A that attacks KP-ABE in the INDsel-CCA game where decryption queries are at most qd times, and for any small attribute universe U, there exist a PPT adversary B that attacks KP-ABKEMcpa in the IND-sel-CPA game and a PPT target collision finder CF on Hfam that satisfy the following inequality.
Advind-sel-ccaA,KP-ABE (λ,U)
≤2AdvBind-sel-cpa,KP-ABKEMcpa(λ,U)+AdvtcrCF ,Hfam(λ)+ qpd .
Proof. We will omit the description of the proof because the proof goes in the same way as the case of
CP-ABE in Section 4.4.
6 Efficiency Discussion
First of all, we remark that our individual modification to attain CCA security is applicable when a DiffieHellman tuple to be verified is in the target group of a bilinear map e : G × G → GT . Especially, it is applicable even when an original CPA secure scheme is based on asymmetric pairing [19], e : G1 × G2 → GT . For example, the Type 3 version [19] of the Waters CP-ABE scheme [4] can be found in [20]. Detailed discussions and results on real implementations are found for the case of CPA-secure ABE schemes [21, 20]. We note here that the efficiency comparison below enables to guess the implementation results of CCA-secure ABE schemes via our modification.
We compare the efficiency of our CP-ABE with the original Waters CP-ABEcpa, and our KP-ABE with the original Ostrovsky-Sahai-Waters KP-ABEcpa. We also compare the efficiency of our schemes with the CCAsecure CP-ABE and KP-ABE schemes obtained by the generic transformation in [10]. Here the generic transformation [10] is considered in the case of a small attribute universe, the delegation type [10] and the Lamport one-time signature [22]. Table 1 shows these comparison. Note that a hash function is applied to generate a message digest of bit-length λ before signing by a secret key of the one-time signature. Note also, for simplicity, we evaluate the lengths and the amounts of computation below in the case that an access structure A is “all-AND” and an attribute map ρ is injective (i.e “single-use” that is opposed to “multiuse”).
Table 1: Efficiency comparison of IND-sel-CCA secure ABEs ([10] and ours) with the original IND-sel-CPA secure ABEs [4, 11].
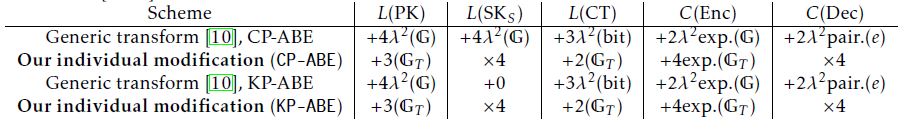
Our individual modification results in expansion of the length of a secret-key and the amount of decryption computation by a factor of four, while the length of a public-key, the length of a ciphertext and the amount of encryption computation are almost the same as those of the original CPA-secure schemes. In the case that the size of an attribute set is up to ( of) the square of the security parameter λ, the amount of decryption computation of our CP-ABE and KP-ABE are smaller than those of the CP-ABE and KP-ABE obtained by the generic transformation [10], respectively.tion by the map e, respectively.
7 Conclusion
We demonstrated direct chosen-ciphertext security modification for ABE in the standard model in the case of the Waters scheme (CP-ABKEMcpa, CP-ABEcpa) and the Ostrovsky-Sahai-Waters scheme(KP-ABKEMcpa, KP-ABEcpa). We utilized the Twin DiffieHellman Trapdoor Test of Cash, Kiltz and Shoup and the algebraic trick of Boneh and Boyen [13] and Kiltz [14]. Our modification worked for the setting that the Diffie-Hellman tuple to be verified in decryption was in the target group of the bilinear map. We compared the efficiency of our CCA-secure ABE schemes with the original CPA-secure ABE schemes and with the CCA-secure ABE schemes obtained by the versatile generic transformation.
Acknowledgment
This work was supported by JSPS KAKENHI Grant Number JP15K00029.
Appendix
A Proof of Lemma 2
The only one point to be complemented to the original proof (in [12]) is that even for any algorithm A with unbounded computational power, the statement holds. This is because, conditioning on the input fixed values (g,X1,X2), A only reduces the twodimensional freedom (r,s) ∈Z2p into the one-dimensional freedom r ∈Zp even if A correctly guesses the relation s = rx1 +x2.
B Proof of Claim 1
For the index 3, we have implicitly set t3 = tcpa,3(−τ∗) and we get:
C Proof of Claim 2
Suppose that we are given a twin DH tuple (e(g,g),e(g,g)α1,e(g,g)α2, Y,ˆ Zˆ1,Zˆ2). Then, di/e(C0,g)µi = (e(g,g)αi )s(τ−τ∗),i = 1,2. So, using the implicit relations (1), we have:
∗ ∗ di = e(g,g)αis(τ−τ )e(gs,g)µi = (e(g,g)αi(τ−τ )e(g,g)µi )s
=(e(g,g)αi(τ−τ∗)e(g,g)αiτ∗+α(i+2))s = (e(g,g)αiτe(g,g)α(i+2))s,i = 1,2.
This means that (e(g,g), e(g,g)α1τe(g,g)α3, e(g,g)α2τe(g,g)α4, e(C0,g), d1, d2) is a twin Diffie-Hellman tuple.
The converse is also verified by the reverse calculation.
D Proof of Claim 5
To reduce to the target collision resistance of an employed hash function family Hfam, we construct a PPT target collision finder CF that attacks Hfam using A as a subroutine. The construction is shown in Fig.2. (Note that the case Collision is defined in Fig.2.)
Note that the view of A in CF is the same as the real view of A until the case Collision occurs and hence the algorithm A works as designed.
To evaluate the probability in Claim 5, we consider the following two cases.
Case 1: the case that Abort (τ = τ∗) occurs in B in Phase 1. In this case, the target τ∗ has not been given to A. So A needs to guess τ∗ to cause a collision τ = τ∗. Hence:
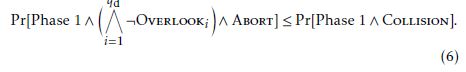 Case 2: the case that Abort (τ = τ∗) occurs in B in Phase 2. In this case, if, in addition to τ = τ∗, it occurred that (and hence C0 = C0∗), then it would occur that ψ = ψ∗. This is because the following two tuples are equal twin DH tuples by the fact that Overlooki never occurs:
Case 2: the case that Abort (τ = τ∗) occurs in B in Phase 2. In this case, if, in addition to τ = τ∗, it occurred that (and hence C0 = C0∗), then it would occur that ψ = ψ∗. This is because the following two tuples are equal twin DH tuples by the fact that Overlooki never occurs:
(e(g,g),e(g,g)α1τe(g,g)α3,e(g,g)α2τe(g,g)α4,e(C0,g),d1,d2),
Hence both S ∈A and ψ = ψ∗ would occur. This is ruled out in decapsulation query; a contradiction. So we have ψcpa , ψcpa∗ ; that is, a collision: ψcpa ,.
Therefore, if Overlooki never occurs for each i, then only decapsulation queries for which (e(g,g), e(g,g)α1, e(g,g)α2, Y,ˆ Zˆ1, Zˆ2) are certainly twin DH tuples have the chance to cause a collision τ = τ∗, as is the case in CF . Hence we have:
^qd Pr[Phase 2∧ ¬Overlooki ∧Abort] ≤ Pr[Phase 2∧Collision].
i=1 (7)
 Figure 2: A PPT Collision Finder CF that attacks Hfam for the proof of Claim 5.
Figure 2: A PPT Collision Finder CF that attacks Hfam for the proof of Claim 5.
- Amit Sahai and Brent Waters. Fuzzy identity-based encryption. In Advances in Cryptology – EUROCRYPT 2005, 24th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Aarhus, Denmark, May 22-26, 2005, Proceedings, pages 457–473, 2005.
- Vipul Goyal, Omkant Pandey, Amit Sahai, and Brent Waters. Attribute-based encryption for fine-grained access control of encrypted data. In Proceedings of the 13th ACM Conference on Computer and Communications Security, CCS 2006, Alexandria, VA, USA, Ioctober 30 – November 3, 2006, pages 89–98, 2006.
- John Bethencourt, Amit Sahai, and Brent Waters. Ciphertextpolicy attribute-based encryption. In 2007 IEEE Symposium on Security and Privacy (S&P 2007), 20-23 May 2007, Oakland, California, USA, pages 321–334, 2007.
- Brent Waters. Ciphertext-policy attribute-based encryption: An expressive, efficient, and provably secure realization. In Public Key Cryptography – PKC 2011 – 14th International Conference on Practice and Theory in Public Key Cryptography, Taormina, Italy, March 6-9, 2011. Proceedings, pages 53–70, 2011.
- Allison B. Lewko, Tatsuaki Okamoto, Amit Sahai, Katsuyuki Takashima, and Brent Waters. Fully secure functional encryption: Attribute-based encryption and (hierarchical) inner product encryption. In Advances in Cryptology – EUROCRYPT 2010, 29th Annual International Conference on the Theory and Applications of Cryptographic Techniques, French Riviera, May 30 – June 3, 2010. Proceedings, pages 62–91, 2010.
- Hiroaki Anada and Seiko Arita. Short cca-secure ciphertextpolicy attribute-based encryption. In 2017 IEEE International Conference on Smart Computing, SMARTCOMP 2017, Hong Kong, China, May 29-31, 2017, pages 1–6, 2017.
- Ran Canetti, Shai Halevi, and Jonathan Katz. Chosenciphertext security from identity-based encryption. In Advances in Cryptology – EUROCRYPT 2004, International Conference on the Theory and Applications of Cryptographic Techniques, Interlaken, Switzerland, May 2-6, 2004, Proceedings, pages 207– 222, 2004.
- Dan Boneh and Xavier Boyen. Efficient selective-id secure identity-based encryption without random oracles. In Advances in Cryptology – EUROCRYPT 2004, International Conference on the Theory and Applications of Cryptographic Techniques, Interlaken, Switzerland, May 2-6, 2004, Proceedings, pages 223–238, 2004.
- Xavier Boyen, Qixiang Mei, and Brent Waters. Direct chosen ciphertext security from identity-based techniques. In Proceedings of the 12th ACM Conference on Computer and Communications Security, CCS 2005, Alexandria, VA, USA, November 7-11, 2005, pages 320–329, 2005.
- Shota Yamada, Nuttapong Attrapadung, Goichiro Hanaoka, and Noboru Kunihiro. Generic constructions for chosenciphertext secure attribute based encryption. In Public Key Cryptography – PKC 2011 – 14th International Conference on Practice and Theory in Public Key Cryptography, Taormina, Italy, March 6-9, 2011. Proceedings, pages 71–89, 2011.
- Rafail Ostrovsky, Amit Sahai, and Brent Waters. Attributebased encryption with non-monotonic access structures. In Proceedings of the 2007 ACM Conference on Computer and Communications Security, CCS 2007, Alexandria, Virginia, USA, October 28-31, 2007, pages 195–203, 2007.
- David Cash, Eike Kiltz, and Victor Shoup. The twin diffiehellman problem and applications. In Advances in Cryptology – EUROCRYPT 2008, 27th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Istanbul, Turkey, April 13-17, 2008. Proceedings, pages 127–145, 2008.
- Dan Boneh and Xavier Boyen. Efficient selective-id secure identity-based encryption without random oracles. In Advances in Cryptology – EUROCRYPT 2004, International Conference on the Theory and Applications of Cryptographic Techniques, Interlaken, Switzerland, May 2-6, 2004, Proceedings, pages 223–238, 2004.
- Eike Kiltz. Chosen-ciphertext security from tag-based encryption. In Theory of Cryptography, Third Theory of Cryptography Conference, TCC 2006, New York, NY, USA, March 4-7, 2006, Proceedings, pages 581–600, 2006.
- Choudary Gorantla, Colin Boyd, and Juan Manuel Gonz´alez Nieto. Attribute-based authenticated key exchange. In Information Security and Privacy – 15th Australasian Conference, ACISP 2010, Sydney, Australia, July 5-7, 2010. Proceedings, pages 300–317, 2010.
- Nuttapong Attrapadung, Benoˆit Libert, and Elie de Panafieu. Expressive key-policy attribute-based encryption with constant-size ciphertexts. In Public Key Cryptography – PKC 2011 – 14th International Conference on Practice and Theory in Public Key Cryptography, Taormina, Italy, March 6-9, 2011. Proceedings, pages 90–108, 2011.
- Nuttapong Attrapadung. Dual system encryption via doubly selective security: Framework, fully secure functional encryption for regular languages, and more. In Advances in Cryptology – EUROCRYPT 2014 – 33rd Annual International Conference on the Theory and Applications of Cryptographic Techniques, Copenhagen, Denmark, May 11-15, 2014. Proceedings, pages 557–577, 2014.
- Moni Naor and Moti Yung. Universal one-way hash functions and their cryptographic applications. In Proceedings of the 21st Annual ACM Symposium on Theory of Computing, May 14-17, 1989, Seattle, Washigton, USA, pages 33–43, 1989.
- Steven D. Galbraith, Kenneth G. Paterson, and Nigel P. Smart. Pairings for cryptographers. Discrete Applied Mathematics, 156(16):3113–3121, 2008.
- Eric Zavattoni, Luis J. Dominguez Perez, Shigeo Mitsunari, Ana H. S´anchez-Ram´irez, Tadanori Teruya, and Francisco Rodr´iguez-Henr´iquez. Software implementation of an attribute-based encryption scheme. IEEE Trans. Computers, 64(5):1429–1441, 2015.
- Ana Helena S´anchez and Francisco Rodr´iguez-Henr´iquez. NEON implementation of an attribute-based encryption scheme. In Applied Cryptography and Network Security – 11th International Conference, ACNS 2013, Banff, AB, Canada, June 25-28, 2013. Proceedings, pages 322–338, 2013.
- Lamport. Constructing digital signatures from a one-way function. Technical report, October 1979.
Citations by Dimensions
Citations by PlumX
Google Scholar
Scopus
Crossref Citations
No. of Downloads Per Month
No. of Downloads Per Country