Collaborative Encryption Algorithm Between Vigenere Cipher, Rotation of Matrix (ROM), and One Time Pad (OTP) Algoritma
Collaborative Encryption Algorithm Between Vigenere Cipher, Rotation of Matrix (ROM), and One Time Pad (OTP) Algoritma
Volume 2, Issue 5, Page No 13-21, 2017
Author’s Name: Elwinus H. A. Mendrofa1,a), Elwin Yunith Purba1, Boy Yako Siahaan1, Rahmad W Sembiring2
View Affiliations
1Department of Informatics Engineering, University of North Sumatera, Medan, 20155, Indonesia
2Politeknik Negeri Medan, Medan-Indonesia
a)Author to whom correspondence should be addressed. E-mail: elwin.zeva@gmail.com
Adv. Sci. Technol. Eng. Syst. J. 2(5), 13-21 (2017); ![]() DOI: 10.25046/aj020503
DOI: 10.25046/aj020503
Keywords: Cryptography, Vigenere Cipher, Rotation of Matrixs
Export Citations
Cryptography is still developing today. Classical cryptography is still in great demand for research and development. Some of them are Vigenere Cipher and One Time Pad (OTP) Algorithm. Vigenere Cipher is known as the alphabet table used to encrypt messages. While OTP is often used because it is still difficult to solve. Currently there are many ways to solve the Vigenere Cipher algorithm. OTP itself has constraints with the distribution of keys that are too long. The key length in the OTP algorithm is the same as the plaintext length. Key random creation also increases the intensity of key distribution. This requires a secure network at a high cost. The key repeater also lowers the message security level. EM2B Key algorithm is able to overcome key problem in OTP. EM2B and Increment of Key (Lk) collaborations produce key lengths equal to plaintext. The Rotation of Matrix (ROM) algorithm contributes to manipulating the length of plaintext characters. ROM works with Square Matrix tables that also scramble the contents of plaintext. The addition of Vigenere Cipher further enhances plaintext security. The algorithm was developed with the EnC1 function, Subrange (Si), and Length of Plaintext (Lp). This research produces a very strong ciphertext. Because plaintext undergoes four stages of encryption to become cipherteks. Then the length of the plaintext changes with the number of cells in the matrix. The value of Si and Lp is added to the plaintext to be a flag for the decryption process.
Received: 14 March 2017, Accepted: 20 April 2017, Published Online: 13 June 2017
1. Introduction
In this increasingly sophisticated era almost all the good circles of government, industry, business to personal companies do the work using computer. The capabilities possessed by computer devices is no doubt, this is proved by the level of accuracy to a high speed in completing a job. Besides the bias advantage obtained from the use of computer, the most important thing to be considered is part of its security which if the information/data stored in the computer suffered damage or loss then it could lead to huge losses. The condition of a computer that is not secured properly, will be a great opportunity to the hackers to enter the computer access and steal all the data he wants. Some examples of hacking cases in 2016, among others “Ransomware emerges as a top cyber threat to business, UK second only to US in DDoS attacks, 412 million user accounts exposed in Friend Finder Networks hack, Financial Conduct Authority concerned about cyber security of banks, and other cases caused by the weakness of the security system. For that we need a computer security system. Security of data in a computer is very important to protect the data from other parties that do not have the authority to determine the content of the data [1]. Security concerns relate to risk areas such as external data storage, dependency on the public internet, lack of control, multi-tenancy and integration with internal security [2].
2. Literature Review
The NIST Computer Security Handbook [NIST95] defines the term computer security as follows: The protection afforded to an automated information system in order to attain the applicable objectives of preserving the integrity, availability, and confidentiality of information system resources (includes hardware, software, firmware, information/data, and telecommunications) [3]. Cryptography is one of the areas of science that studies about information security / data to avoid adverse effects due to misuse of information by irresponsible parties. Cryptography has an important role in maintaining the confidentiality of information both in the computer and at the time of transaction data.
So a more hardheaded goal of cryptography is to make it too work intensive for attacker [11]. The basic terms used in cryptography are discussed bellow:
Plaintext
In crytography, plaintext is a simple readable text before being encrypted into ciphertext [12]. The data can be read and understood without any special measure is called plaintext [13].
Ciphertext
In Cryptography, the transformation of original message into non-readable message before the transmission is known as cipher text [16]. It is amessage obtained by some kind of encryption operation on plain text.
Encryption
Encryption is a process of converting plain text into cipher text. Encryption process requires encryption algorithm and key to convert the plain text into cipher [17]. In cryptography encryption performed at sender end.
Decryption
Decryption is the reverse process of encryption. It converts the cipher text into plain text. In cryptography decryption performed at receiver end [11].
Key
The key is the numeric or alphanumeric text used for the encryption of plain text and decryption of cipher text [16]
Currently the scientists in the field of cryptography has been a lot of research about the science of cryptography by creating a variety of new algorithms developed from previous algorithms. The level of security offered varies, there is a security priority by applying the stages of a very complex algorithm, and by offering the speed of the execution process of the algorithm they created.
Vigenere Cipher is one of the classic cryptographic algorithms that until now is still widely developed by researchers. In the cryptography, it contains different methods among them the cryptography with the Vigenère matrix. Cipher was proposed by BLAISEDE VIGENÈRE in 1583 and has reigned about 03centuries.
Another classic cryptographic algorithm is Vernam Cipher, known as the One Time Pad algorithm. In its development One Time Pad algorithm is still much in demand by researchers, because the key length generated randomly equal to the length of the message. But the length of the key to be distributed becomes an interesting thing to develop, because when sending a key must require a secure network where the secure network is expensive. The key looping is also a weak point in the algorithm, which means that if the message is encrypted and decrypted then to encrypt the same message must use a new key, it means that network security is a top priority due to frequent distribution of keys.
The key looping is also a weak point in the algorithm, which means that if the message is encrypted and decrypted then to encrypt the same message must use a new key, it means that network security is a top priority due to frequent distribution of keys. This is the case with Vigenere ciphers though considered safe for centuries but then its weaknesses have been identified. Friedrich Kasiki invented a method to identify the period and therefore the key and plaintext [11]
This research provides a solution to the length of keys to be distributed that have lengths to be equal to the message. Doubts over repetition of key biases that result in cryptanalysis can easily know the contents of the message can be overcome by the collaboration with the algorithm Vigenere Cipher and Rotation of Matrix (ROM). These three algorithms support each other to ensure the security level of the message and make it difficult for the irresponsible party to guess the contents of the original message.
The message will be sent encryption process four stages where each stage will produce 1st ciphertext, 2nd ciphertext, 3rd ciphertext, and final ciphertext [10]. The first stage, the message is encrypted using the Vigenere Cipher algorithm by first determining the index of each message character and key. Both indexes are summed and modulated to the specified character length of the index table. The result of this stage is called 1st ciphertext. . The next step is to determine the value of subrange and Length of plaintext. The subrange value is derived from the sum of each message index and the Length of Plaintext is determined by the number of characters of the message itself. After the subrange and length of plaintext values are obtained then the index value for each key character multiplied by the subrange value and modulated by length of plaintext, this result is called Encryption 1st ciphertext (EnC1). 2nd ciphertext is obtained from multiplication between 1st ciphertext and EnC1 value. The third stage is using the Rotation of Matrix (ROM) algorithm where in this stage the message that has been converted into 2nd ciphertext is inserted into a matrix table. This algorithm aims to scramble messages that have been entered into the matrix table using the rotation method and manipulate the number of characters from the message.
The workings of this algorithm is very easy but requires precision because the rotation value obtained from a key algorithm called E2mbs Key Algorithm and the length of the key characters will determine the number of matrix tables to rotate. After all the process at this stage is done then obtained 3rd ciphertext, and the final stage is using One Time Pad algorithm, where as we know this algorithm is run by converting all characters of the message and key into binary numbers which then operated by exclusive or (XOR) method. The One Time Pad algorithm in this research has been modified in the key generation section. Previous research has always used a random machine to generate a key. The need for modifications to the key generation process aims to avoid making such long keys when restoring the original message from ciperthext. The key used to encrypt messages on the One Time Pad algorithm is the primary key that has been altered using the E2mbs Key algorithm, then to increase the length of the key so that it is the same as the message display, the increment key method is used. The encryption results in this final stage produce Final Ciphertext which will be sent to the recipient of the message along with the main key where the length of the character does not have to be the same length of the message. In this classic algorithm has been found a way to find out the contents of the original message without having to know the key, This research is explained that the decryption process will be faster if the recipient of the message to obtain the main key and follow the correct procedure. However, if decrypted by guessing the key then kriptanalis must go through a long route and the weight of the possibility to find out the original message content.
3. Materials and Methods
According to (William, 2010) Cryptography is a technique applied for encryption and decryption. In the field of cryptography there are several techniques available for encryption/decryption. These techniques can be generally classified into two major groups, i.e. Conventional and public key Cryptography [4].
To understand the workings of cryptographic algorithms in this research, the following will be presented a block diagram explaining the flow of the encryption process.
 Figure 1. Block Diagram of Cryptography Algorithm Encryption and Decryption.
Figure 1. Block Diagram of Cryptography Algorithm Encryption and Decryption.
From the picture above can be known in general the process of encryption of a plaintext into ciphertext and the decryption of ciphertext to plaintext.
In this cryptographic algorithm used two tables as parameter to determine character index among others, Plaintext Index Table (0, 1, 2, …, 36) of 37 characters to identify characters (A, B, …, Z, spaces, 0, 1 , …, 9) and ASCII tables as character parameters changed into ASCII characters.
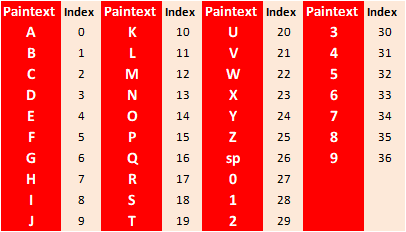 Figure 2. Plaintext Index Table
Figure 2. Plaintext Index Table
 Figure 3. Three-Pass Protocol Process Scheme based on ASCII table
Figure 3. Three-Pass Protocol Process Scheme based on ASCII table
Source: http://www.asciitable.com
The Vigenere cipher is a method of encrypting alphabetic text by using a series of different Caesar ciphers based on the letters of a keyword. It is a simple form of polyalphabetic substitution in which each alphabet can replace with several cipher alphabets [5]. The encoding by the Vigenère matrix is the type by substitution. It consists to employ a key composed by a word or by an expression. It utilizes a square composed by the alphabet 25 times in such way it signifies a square matrix where each cell contains a letter of the alphabet (it exists several variants of the matrix) [6]. Message is divided in blocks. Length’s block is equal length’s key K. Maximal Length of key is 208 bits (26*8=208). Key length then could be 128,192,256… for one matrix. To perform the encryption using Vigenere Cipher algorithm development required the following functions:
This function is then developed by multiplying each index to the value of 1st ciphertext (Ci1) with Encryption 1st ciphertext. Encryption 1st ciphertext (EnC1) is the sum of subrange with length of plaintext.
3.1. Cryptography
The word Cryptography is derived from the Greek, namely from word Cryptos meaning of the word hidden and graphein means writing. Cryptography can be interpreted as an art or a science which researched how the data is converted into a certain shape that is difficult to understand [1]. Cryptography aims to maintain the confidentiality of information or data that can not be known by unauthorized parties (unauthorized person)
Cryptography components
Basically, the cryptographic component consists of several components, such as:
- Encryption: is very important in cryptography, is a way of securing the transmitted data that are kept confidential. The original message is called plaintext, which is converted into code that is not understood. Encryption can be interpreted with a cypher or code. Similarly, do not understand a word then we will see it in a dictionary or glossary. Unlike the case with encryption, to convert plain text into text-code we use algorithms to encode the data that we want.
- Decryption: is the opposite of encryption. The encrypted message is returned to the original form (original text), called the message encryption algorithm used for encryption is different from the algorithm used for encryption.
- Keywords: that means here is the key used for encryption and description.
Security of cryptographic algorithms depending on how the algorithm works, therefore this kind of algorithm is called finite algorithm. Limited algorithm is an algorithm used a group of people to keep the messages they send.
3.2. Vigenere Chiper
The Vigenère cipher is a method of encrypting alphabetic text by using a series of different Caesar ciphers based on the letters of a keyword. It is a simple form of polyalphabetic substitution. [2]. The characters used in the Cipher Vigenere that is A, B, C, …, Z and united with the numbers 0, 1, 2, …, 25. The encryption process is done by writing the key repeatedly. Writing the key repeatedly performed until each character in messages have a couple of key characters. Furthermore, the characters in the message is encrypted using the Caesar Cipher key values that have been paired with numbers. The Confederacy’s messages were far from secret and the Union regularly cracked their messages. Throughout the war, the Confederate leadership primarily relied upon three key phrases, “Manchester Bluff”, “Complete Victory” and, as the war came to a close, “Come Retribution”.[3] The table below show the example of encription using Vigenere Chiper consist of Plaintext, Key and Chipertextin Figure 4.
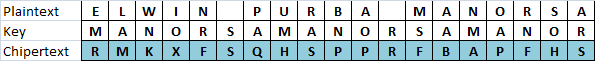 Figure 4. Examples Using Encryption Vigenere Cipher (Bruen, 2005)
Figure 4. Examples Using Encryption Vigenere Cipher (Bruen, 2005)
Examples of encryption in Figure 1, the message character “E” is encrypted with a key “M” and generate cipher text “R“. The results obtained from the code encrypting the message “E” is worth 5 and a key character “M” which is worth 13. Each character value added 5 + 13 = 18. Because 18 is less than the 26 which is the number of characters used, then 18 divided by 26. The rest of the division is 18 which is a character “R“. The encryption process can be calculated by the following equation (Stalling, 2011):
??=(??+??) ??? 26 (2.0)
where ??, ?? and ?? an encrypted character, the character of the message and the character key. While the decryption process can use the following equation:
??=(??−??) ??? 26 (2.1)
with ?? is the result of the decryption code, ?? is character cipher text or cipher, ?? is a key character. While other methods to perform the encryption process with Vigenere Cipher method that uses tabula recta (also called Vigenere square; Figure 5).
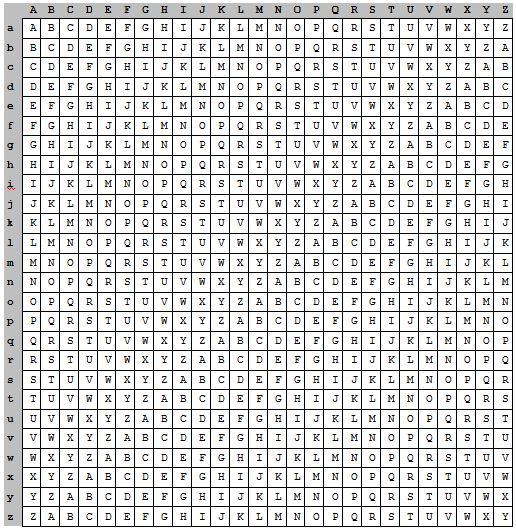 Figure 5. Tabula recta Vigenere algorithm.
Figure 5. Tabula recta Vigenere algorithm.
The leftmost column of squares states key letters, while the top line states plaintext letters. Each line in the rectangle states the letters ciphertext obtained by Caesar Cipher, in which the number of shifts letter plaintext specified numerical values of letters that key (ie, a = 0, b = 1, c = 2, …, z = 25) , Vigenère square is used to obtain the ciphertext by using a key that has been determined. If the key length is shorter than the length of the plaintext, then the key are repeated it’s use (the periodic system). When the key length is m, then the period is said to be m.
3.3. Vernam Chiper
Cryptography for most people is something that is very difficult and we as beginners tend to be lazy to learn it. However there is a cryptographic method that is rather easy to learn and the experts have stated that this method is a cryptographic method that is safe enough to use. The method is commonly known by the name of One Time Pad (OTP) or better known as the Vernam Cipher [4]. Vernam Cipher invented by Major J. Maugborne and G. Vernam in 1917. Algorithms One Time Pad (OTP) is a diversified symetric key algorithm, which means that the key used to encrypt and decrypt the same key. In the process of encryption, algorithm it uses the stream cipher derived from the XOR between bits of plaintext and key bits. In this method, the plain text is converted into ASCII code and then subjected to an XOR operation on the key that has been converted into ASCII code.
3.4. One Time Pad
One-time pad (OTP) is a stream cipher to encrypt and decrypt one character each time [5]. This algorithm was found in 1917 by Major Joseph Mauborgne as improvement of Vernam Cipher to produce a perfect security. Mauborgne proposes the use of One-Time Pad containing a row of characters randomly generated key. One pad is used only once (one-time) only to encrypt a message, after the pad has been used demolished so as not be reused for other encrypting messages. Encryption can be expressed as the sum modulo 26 of the plaintext character with one key character one-time pad [6]. This is the equation of one-time pad encryption 26 characters shown in Equation 2.2 below:
Ci= (Pi+Ki) mod 26 (2.2)
If the character that is used is a member of the set of 256 characters (such as characters with ASCII encoding), then the encryption equation shown in equation 2.3 below.
Pi= (Ci–Ki) mod 26 (2.3)
After the sender encrypts the message with the key, he destroyed the key. Recipient of the message using the same pad to decrypt the ciphertext characters into characters plaintext with equation 2.4 below.
Pi= (Ci–Ki) mod 26 (2.4)
for the 26-letter alphabet, or for the 256-character alphabet with equation 2.5 below.
Pi= (Ci–Ki) mod 256 (2.5)
The ways of working one time pad method:
C = P XOR K (2.6)
P = C XOR K (2.7)
Note that the key length should be equal to the length of the plaintext, so there is no need to repeat the use of the key during the encryption process (as in vernam cipher).
3.5. Rotation Matrix
Rotation matrix is shifting ciphertext character that has been incorporated into the matrix column clockwise, along the defined distance of the key. How to determine the length of shifts and the number of shifts can be seen in the following Table 1 below:
Table 1. Calculation of Long Shifts in Matrix
| Ki | M | A | N | O | R | S | A | |
| A = Dec(Ki) | 77 | 65 | 78 | 79 | 82 | 83 | 65 | (2.8) |
| B = A+Cn-1 | 76 | 90 | 91 | 79 | 83 | 87 | 70 | (2.9) |
| C = A mod 26 | 25 | 13 | 0 | 1 | 4 | 5 | 13 | (2.10) |
| D = B+C mod 26 | 23 | 25 | 13 | 2 | 9 | 14 | 5 | (2.11) |
| Char | W | Y | M | B | I | N | E | |
| G = Dec(Char) | 87 | 89 | 77 | 66 | 73 | 78 | 69 | (2.12) |
| Rg = G mod 26 | 9 | 11 | 25 | 14 | 21 | 0 | 17 | (2.13) |
Explanation:
Ki : Key
A : Decimal ASCII value of the key characters
B : Results Summation with a decimal value key with the previous result (C).
C : The decimal value of a key character mod 26
D : Number of B + C mod 26
Char : The result of the shift in the index table alphabetic characters as much as the value of D
G : Decimal ASCII value of the key characters
Rg : Long shifts in the character matrix table
Whereas for the amount of shift is determined by the character key.
Forms of research conducted by the authors in this paper is a review of literature. The literature review is a framework, concepts, or orientation to perform the analysis and classification of facts collected in a study. Referral sources from books and journals, which are referred to in this paper are directly related to the object under researched, that is the plaintext encryption. The method of research that used in this paper is a flowchart. This method includes determining a model of encryption, the completion of the encryption algorithm, encryption simulation manufacture and analysis of simulation results encryption. Flowchart design simulations on complete this research can be seen in Figure 6.
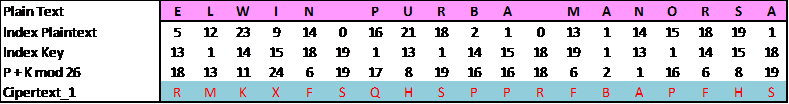 Figure 6. Table Testing of Encryption Vigenere Cipher
Figure 6. Table Testing of Encryption Vigenere Cipher
Rotation Key Algorithm
Rotation key generation algorithm aims to improve the security of the plaintext by changing the keys into a new character. Furthermore, the new character is converted to decimal and then look for the value of the modulation to determine the length of a shift towards the characters in the matrix table. Consider the following Figure 7.
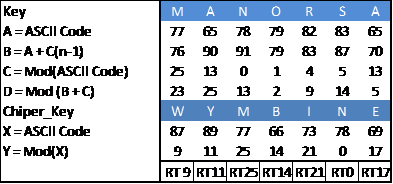 Figure 7. Process Key Algorithm determining Long Shifts on Matrix rotation
Figure 7. Process Key Algorithm determining Long Shifts on Matrix rotation
Rotation algorithm
In this process, all the characters ciphertext that has been generated on Vigenere Cipher algorithm written into the matrix table where condition matrix which must consist of a matrix of squares, where the number of rows equals the number of columns (Figure 8). To run this algorithm, first consider the following steps.
- Write down all of the ciphertext into the matrix
- The matrix will be formed must consist of the same number of rows and columns.
- To define a matrix of rows and columns calculate the amount of n ciphertext; n = length of ciphertext.
- If 0 < n <= 9, it will form a 3 x 3 matrix.
If 9 < n <= 16, it will form a matrix of 4 x 4
If 16 < n <= 25, it will form a matrix of 5 x 5, etc.
- If the matrix column empty, fill it with the alphabet from A until the empty column full of character.
- Copy the first column then make a new ending column
- After that copy the first line and then make a new ending line.
- Make the first shift in which the shift length is determined by the rotation of key algorithms. Rotation matrix will end after reaching n MAX of keys.
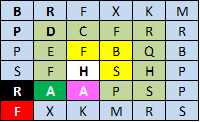
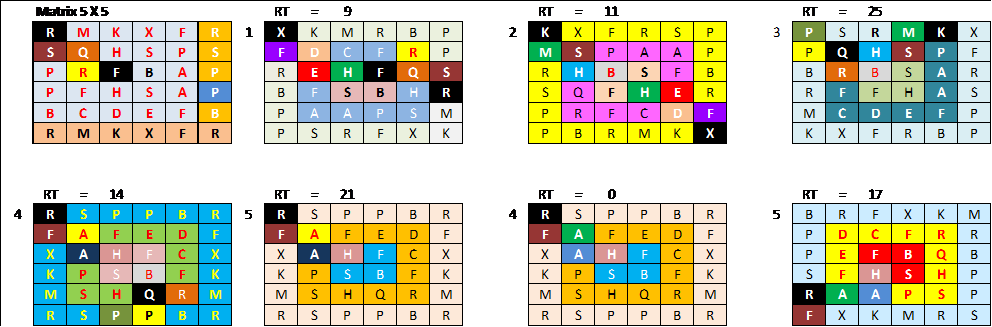 Figure 8. Process of Rotation Matrix
Figure 8. Process of Rotation Matrix
Retrieved end Cipertext: BRFXKMPDCFRRPEFBQBSFHSHPRAAPSPFXKMS
Vernam Cipher
Encryption can be expressed as the result of the Exclusive OR (XOR) of the plaintext character with an OTP key characters. This algorithm acts to encrypt the plaintext where the key is generated randomly. This key is valid only disposable where if you want to decrypt the same message then the generated key will be changed.
One Time Pad
In this method, there are two things that need to be encrypted is the key and the ciphertext obtained from vigenere chipper. This method works in advance is change the main key with One Time Pad methode to produce the Ciphertext of the key then this key will be the second key or a new key (Figure 9).
Ei : Pi XOR Ki
The main key : MANORSA
Random key :
Key Ciphertext : “€ +« “n%
| Plaintext | Binary Bit | Random Bit | XOR | Key |
| M | 01001101 | 11100101 | 10101000 | “ |
| A | 01000001 | 11000001 | 10000000 | € |
| N | 01001110 | 01100101 | 00101011 | + |
| O | 01001111 | 11100100 | 10101011 | « |
| R | 01010010 | 11111010 | 10101000 | “ |
| S | 01010011 | 00111101 | 01101110 | n |
| A | 01000001 | 01100100 | 00100101 | % |
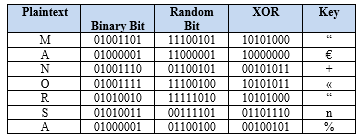 Figure 9. Encryption Results of Main Key
Figure 9. Encryption Results of Main Key
The next new key that has been generated is used to encrypt the ciphertext that has been obtained from vigenere cipher.
From the results of the main key encryption in the previous process we obtain a new key and then the key is repeated until the key length equal to the length of the plaintext. The result of the encryption of the plaintext and the key will be the end of the process to produce a strong ciphertext.
Plaintext : BRFXKMPDCFRRPEFBQBSFHSHPRAAPSPFXKMRS
Key
: “€+«“n%“€+«“n%“€+«“n%“€+«“n%“€+«“n%“
Ciphertext : ÛÊm¾Ò#uý├m¨·>`¯┬zÚ¹(m¹╚{¨Ú/u¹ðm¾Ò#w¹
The encryption process is represented in binary form :
Pi : 01000010 01010010 01000110 01011000 01001011 01001101
Ki : 10101000 10000000 00101011 10101011 10101000 01101110
Ci : 11101010 11010010 01101101 11110011 11100011 00100011
Pi : 01010000 01000100 01000011 01000110 01010010 01010010
Ki : 00100101 10101000 10000000 00101011 10101011 10101000
Ci : 01110101 11101100 11000011 01101101 11111001 11111010
Pi : 01010000 01000101 01000110 01000010 01010001 01000010
Ki : 01101110 00100101 10101000 10000000 00101011 10101011
Ci : 00111110 01100000 11101110 11000010 01111010 11101001
Pi : 01010011 01000110 01001000 01010011 01001000 01010000
Ki : 10101000 01101110 00100101 10101000 10000000 00101011
Ci : 11111011 00101000 01101101 11111011 11001000 01111011
Pi : 01010010 01000001 01000001 01010000 01010011 01010000
Ki : 10101011 10101000 01101110 00100101 10101000 10000000
Ci : 11111001 11101001 00101111 01110101 11111011 11010000
Pi : 01000110 01011000 01001011 01001101 01010010 01010011
Ki : 00101011 10101011 10101000 01101110 00100101 10101000
Ci : 01101101 11110011 11100011 00100011 01110111 11111011
Fig. 8 The encryption process with the one-time pad method
4. Results and Discussions
The results of encryption on this method obtain ciphertext to be sent to the recipient where there are two keys that are sent, among others, the key to decrypt the plaintext and the key to decrypt the key.
4.1. Description
One Time Pad
To know the plaintext from the ciphertext received by the rightful recipient of the message, that is by first using the one-time pad method. The message recipients require a new key as a reference to recover the plaintext.
Ciphertext : ÛÊm¾Ò#uý├m¨·>`¯┬zÚ¹(m¹╚{¨Ú/u¹ðm¾Ò#w¹
New Key : “€+«“n%
Ciphertext and the key then is XOR ed using the formula:
Di : Ci XOR Ki
The process of the message recipient to get a new message that is still in the form of Ciphertext are:
BRFXKMPDCFRRPEFBQBSFHSHPRAAPSPFXKMRS.
After successful decryption of the message recipient to decrypt back to find out the main key is still the one-time pad method.
Ciperteks key : “€+«“n%
Key : åÁeäú=d
Main Key = Ci XOR Ki
“ : 10101000 XOR å : 11100101 = 01001101 : M
€ : 10000000 XOR Á : 11000001 =01000001 : A
+ : 00101011 XOR e : 01100101 =01001110 : N
« : 10101011 XOR ä : 11100100 =01001111 : O
“ : 10101000 XOR ú : 11111010 =01010010 : R
N : 01101110 XOR = : 00111101 =01010011 : S
% : 00100101 XOR d : 01100100 =01000001 : A
Main Key : MANORSA
Rotation algorithm
The next decryption algorithm is an algorithm in which the rotation that has been encrypted ciphertext of the previous methods to be put into a matrix table. See the Figure 10 below.
Ciphertext: BRFXKMPDCFRRPEFBQBSFHSHPRAAPSPFXKMRS
In the previous encryption process, ciphertext character that is in the column of the matrix are moved forward along key value, but on the decryption algorithm ciphertext character that is in the matrix table is sliding backwards or revers along key value and repeated as much as the key length. The key value is obtained from the following process in the Figure 11 and Figure 12.
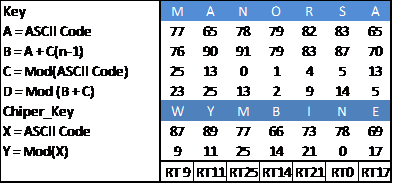 Figure 11. The process of determining the value of the key.
Figure 11. The process of determining the value of the key.
After a successful key value is determined next process is to do a rotation matrix algorithm.
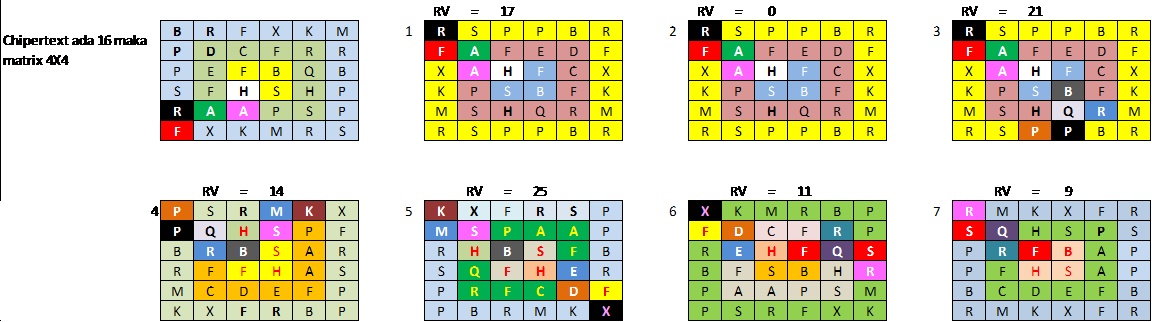 Figure 12. Process Description ciphertext with Matrix Ciphertext Algorithm
Figure 12. Process Description ciphertext with Matrix Ciphertext Algorithm
The results of the first rotation indicated at number one in the previous figure 10 wherein R is on the line five-column one. If we look at previous matrix characters that are in row one column one is B, then calculated spin clockwise as key values obtained from the previous process. The key value is taken values that are at the end of the index is 17, the next process is the value at the previous index up until the beginning of the index, this is certainly the opposite of encryption algorithms. Having calculated the characters are on the order of 17 is R then R is placed on row one column one on the following matrix and is followed by the next character, then repeated continuously until the last process (Figure 13). In the process of this algorithm obtained the final matrix below:
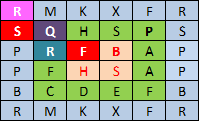 Figure 13. The Results of Algorithm Rotation Matrix
Figure 13. The Results of Algorithm Rotation Matrix
The next stage removes the last row and the last column of the matrix.
The Ciphertext become:
Algoritma Vigenere
Last decryption algorithm using the algorithm vigenere cipher by using the key with formula:
Di = (Ci – Ki) mod 26
So the result we can see below:
Ciphertext : RMKXFSQHSPPRFBAPFHS
Key : MANORSAMANORSAMANOR
Plaintext : ELWIN PURBA MANORSA
5. Conclusions
The encryption mechanism used in the present research is still modest or simple, but is expected to be useful as a first step to enter into the world of cryptography, particularly in the implementation of message security algorithms using other combinations. To the future, this research is expected to be developed, used and applied in the areas of life that is more complex.
- Zaeniah, Bambang Eka Purnama, “An Analysis of Encryption and Decryption Application by using One Time Pad Algorithm”, (IJACSA) International Journal of Advanced Computer Science and Applications, 6(9), 2015.
- K Hashizume , “An analysis of security issues for cloud computing”, Journal of Internet Services and Applications, a Springer open Journal: 1-13, 2013.
- Michael Nieles, Kelley Dempsey, Victoria Yan Pillitteri, “An Introduction to Information Security”, National Institute of Standards and Technology Special Publication 800-12 Revision 1, 2017.
- William Stallings, “Cryptography and Network Security: Principles & Practices”, Fifth edition, Prentice Hall, ISBN-13: 978-0136097044, 2010.
- C. Bhardwaj, “Modification of Vigenère Cipher by Random Numbers, Punctuations & Mathematical Symbols,” Journal of Computer Engineering (IOSRJCE) ISSN No: 2278-0661, 2012.
- Anuja Priyam, “Extended Vigenère using double Transposition Cipher with One Time Pad Cipher”, Intl J Engg Sci Adv Research; 1(2):62-65, ISSN No: 2395-0730, 2015.
- Sundram Prabhadevi, Rahul De, Pratik Shah, “Cost Effective Poly Vernam Cipher With Cache Optimization”, Journal of Theoretical and Applied Information Technology, ISSN: 1992-8645, 2013.
- Shukla, R. and Prakash, H.O., “Sampurna Suraksha: Unconditionally Secure and Authenticated One Time Pad Cryptosystem”, IEEE Conference: International Conference on Machine Intelligence and Research Advancement 174-178, DOI: 10.1109/ICMIRA.2013.40, 2013.
- Borowski, M., Lesniewicz, M.,“Modern usage of old one-time pad”, IEEE Conference :Communications and Information Systems: 1-5, ISBN:978-1-4673-1422-0, 2012
- Elwinus Mendrofa, Elwin Yunith Purba, Boy Yako Siahaan, Rahmad W Sembiring, “Manipulation Vigenere Cipher Algorithm With Vernam Cipher Trough Matrix Table Rotation”, 2nd International Conference of Computer, Environment, Social Science, Health Science, Agriculture & Technology (ICEST), ISBN: 979-458-964-0, 2017.
- Aized Amin Soofi, Irfan Riaz, Umair Rasheed, “An Enhanced Vigenere Cipher For Data Security”, International Journal Of Scientific & Technology Research 5(03), March 2016, ISSN:22778616.
- M. Rouse. (2007, Plain text. Available: http://searchsecurity.techtarget.com/definition/plaintext, 2017.
- T. Gunasundari and K. Elangovan, “A Comparative Survey on Symmetric Key Encryption Algorithms,” International Journal of Computer Science and Mobile Applications, ISSN no.2321-8363, 2014.
- Digital Economy Promotion Agency, under the Administrative Supervision of the Minister of Digital Economy and Society, 2016.
- Avialable at: ?http://www.sipa.or.th”, 2017.
- M. Agrawal and P. Mishra, “A comparative survey on symmetric key encryption techniques,” International Journal on Computer Science and Engineering (IJCSE), vol. 4, pp. 877-882, 2012.
- V. Beal. (2009, Encryption. Available: http://www.webopedia.com/TERM/E/encryption.html, 2017.