Volume 2, Issue 5 (Conferences)
Download Complete Issue
Current Issue features key papers related to multidisciplinary domains involving complex system stemming from numerous disciplines; this is exactly how this journal differs from other interdisciplinary and multidisciplinary engineering journals. This issue contains 26 accepted papers in Mathematics domain.
Editorial
Front Cover
Adv. Sci. Technol. Eng. Syst. J. 2(5), (2017);
Editorial Board
Adv. Sci. Technol. Eng. Syst. J. 2(5), (2017);
Editorial
Adv. Sci. Technol. Eng. Syst. J. 2(5), (2017);
Table of Contents
Adv. Sci. Technol. Eng. Syst. J. 2(5), (2017);
Articles
Three-Pass Protocol Implementation in Vigenere Cipher Classic Cryptography Algorithm with Keystream Generator Modification
Amin Subandi, Rini Meiyanti, Cut Lika Mestika Sandy, Rahmat Widia Sembiring
Adv. Sci. Technol. Eng. Syst. J. 2(5), 1-5 (2017);
View Description
Vigenere Cipher is one of the classic cryptographic algorithms and included into symmetric key cryptography algorithm, where to encryption and decryption process use the same key. Vigenere Cipher has the disadvantage that if key length is not equal to the length of the plaintext, then the key will be repeated until equal to the plaintext length, it course allows cryptanalysts to make the process of cryptanalysis. And weaknesses of the symmetric key cryptographic algorithm is the safety of key distribution factor, if the key is known by others, then the function of cryptography itself become useless. Based on two such weaknesses, in this study, we modify the key on Vigenere Cipher, so when the key length smaller than the length of plaintext entered, the key will be generated by a process, so the next key character will be different from the previous key character. In This study also applied the technique of Three-pass protocol, a technique which message sender does not need to send the key, because each using its own key for the message encryption and decryption process, so the security of a message would be more difficult to solved.
Modification of Symmetric Cryptography with Combining Affine Chiper and Caesar Chiper which Dynamic Nature in Matrix of Chiper Transposition by Applying Flow Pattern in the Planting Rice
Dewi Sartika Ginting, Kristin Sitompul, Jasael Simanulang, Rahmat Widia Sembiring, Muhammad Zarlis
Adv. Sci. Technol. Eng. Syst. J. 2(5), 6-12 (2017);
View Description
Classical cryptography is a way of disguising the news done by the people when there was no computer. The goal is to protect information by way of encoding. This paper describes a modification of classical algorithms to make cryptanalis difficult to steal undisclosed messages. There are three types of classical algorithms that are combined affine chiper, Caesar chiper and chiper transposition. Where for chiperteks affine chiper and Caesar chiper can be looped as much as the initial key, because the result can be varied as much as key value, then affine chiper and Caesar chiper in this case is dynamic. Then the results of the affine and Caesar will be combined in the transposition chiper matrix by applying the pattern of rice cultivation path and for chipertext retrieval by finally applying the pattern of rice planting path. And the final digit of the digit shown in the form of binary digits so that 5 characters can be changed to 80 digit bits are scrambled. Thus the cryptanalyst will be more difficult and takes a very long time to hack information that has been kept secret.
Collaborative Encryption Algorithm Between Vigenere Cipher, Rotation of Matrix (ROM), and One Time Pad (OTP) Algoritma
Elwinus H. A. Mendrofa, Elwin Yunith Purba, Boy Yako Siahaan, Rahmad W Sembiring
Adv. Sci. Technol. Eng. Syst. J. 2(5), 13-21 (2017);
View Description
Cryptography is still developing today. Classical cryptography is still in great demand for research and development. Some of them are Vigenere Cipher and One Time Pad (OTP) Algorithm. Vigenere Cipher is known as the alphabet table used to encrypt messages. While OTP is often used because it is still difficult to solve. Currently there are many ways to solve the Vigenere Cipher algorithm. OTP itself has constraints with the distribution of keys that are too long. The key length in the OTP algorithm is the same as the plaintext length. Key random creation also increases the intensity of key distribution. This requires a secure network at a high cost. The key repeater also lowers the message security level. EM2B Key algorithm is able to overcome key problem in OTP. EM2B and Increment of Key (Lk) collaborations produce key lengths equal to plaintext. The Rotation of Matrix (ROM) algorithm contributes to manipulating the length of plaintext characters. ROM works with Square Matrix tables that also scramble the contents of plaintext. The addition of Vigenere Cipher further enhances plaintext security. The algorithm was developed with the EnC1 function, Subrange (Si), and Length of Plaintext (Lp). This research produces a very strong ciphertext. Because plaintext undergoes four stages of encryption to become cipherteks. Then the length of the plaintext changes with the number of cells in the matrix. The value of Si and Lp is added to the plaintext to be a flag for the decryption process.
Combination of Caesar Cipher Modification with Transposition Cipher
Fahrul Ikhsan Lubis, Hasanal Fachri Satia Simbolon, Toras Pangidoan Batubara, Rahmat Widia Sembiring
Adv. Sci. Technol. Eng. Syst. J. 2(5), 22-25 (2017);
View Description
The caesar cipher modification will be combine with the transposition cipher, it would be three times encryption on this experiment that is caesar modification at first then the generated ciphertext will be encrypted with transposition, and last, the result from transposition will be encrypted again with the second caesar modification, similarly at the decryption but the process is reversed. In the modification of caesar cipher, what would be done is the shift of letters are not based on the alphabet but based on ASCII table, plaintext will get the addition of characters before encryption and then the new plaintext with the addition of characters will be divided into two, they are plaintext to be encrypted and plaintext are left constantly (no encryption), The third modification is the key that is used dynamically follows the ASCII plaintext value.
Analysis of Learning Development With Sugeno Fuzzy Logic And Clustering
Maulana Erwin Saputra, Safrizal
Adv. Sci. Technol. Eng. Syst. J. 2(5), 26-30 (2017);
View Description
In the first journal, I made this attempt to analyze things that affect the achievement of students in each school of course vary. Because students are one of the goals of achieving the goals of successful educational organizations. The mental influence of students’ emotions and behaviors themselves in relation to learning performance. Fuzzy logic can be used in various fields as well as Clustering for grouping, as in Learning Development analyzes. The process will be performed on students based on the symptoms that exist. In this research will use fuzzy logic and clustering. Fuzzy is an uncertain logic but its excess is capable in the process of language reasoning so that in its design is not required complicated mathematical equations. However Clustering method is K-Means method is method where data analysis is broken down by group k (k = 1,2,3, .. k). To know the optimal number of Performance group. The results of the research is with a questionnaire entered into matlab will produce a value that means in generating the graph. And simplify the school in seeing Student performance in the learning process by using certain criteria. So from the system that obtained the results for a decision-making required by the school.
A Theoretical and Experimental Comparison of One Time Pad Cryptography using Key and Plaintext Insertion and Transposition (KPIT) and Key Coloumnar Transposition (KCT) Method
Pryo Utomo, Nadia Widari Nasution, Arisman, Rahmat Widia Sembiring
Adv. Sci. Technol. Eng. Syst. J. 2(5), 31-34 (2017);
View Description
One Time Pad (OTP) is a cryptographic algorithm that is quite easy to be implemented. This algorithm works by converting plaintext and key into decimal then converting into binary number and calculating Exclusive-OR logic. In this paper, the authors try to make the comparison of OTP cryptography using KPI and KCT so that the ciphertext will be generated more difficult to be known. In the Key and Plaintext Insertion (KPI) Method, we modify the OTP algorithm by adding the key insertion in the plaintext that has been splitted. Meanwhile in the Key Coloumnar Transposition (KCT) Method, we modify the OTP algorithm by dividing the key into some parts in matrix of rows and coloumns. Implementation of the algorithms using PHP programming language.
System Control Device Electronics Smart Home Using Neural Networks
Safarul Ilham, Abdul Muin, Dedi Candro
Adv. Sci. Technol. Eng. Syst. J. 2(5), 35-37 (2017);
View Description
The use of information technology is very useful for today’s life and the next, where the human facilitated in doing a variety of activities in the life day to day. By the development of the existing allows people no longer do a job with difficulty. For that, it takes a system safety home using system technology Web-based and complete video streaming CCTV (video streaming) a person can see the condition of his home whenever and wherever by using handphone, laptops and other tools are connected to the Internet network. This tool can facilitate someone in the monitor at home and control equipment the House as open and close and the lock the gate, turning on and off the lights so homeowners are no longer have to visit their home and fear the state of the House because fully security and control in the House was handled by the system. based on the above problems Writer try to design work system a tool that can control the simulation tools home using two Microcontroller is Attiny 2313 and Atmega16.
Comparison of K-Means and Fuzzy C-Means Algorithms on Simplification of 3D Point Cloud Based on Entropy Estimation
Abdelaaziz Mahdaoui, Aziz Bouazi, Abdallah Marhraoui Hsaini, El Hassan Sbai
Adv. Sci. Technol. Eng. Syst. J. 2(5), 38-44 (2017);
View Description
In this article we will present a method simplifying 3D point clouds. This method is based on the Shannon entropy. This technique of simplification is a hybrid technique where we use the notion of clustering and iterative computation. In this paper, our main objective is to apply our method on different clouds of 3D points. In the clustering phase we will use two different algorithms; K-means and Fuzzy C-means. Then we will make a comparison between the results obtained.
Degenerate 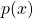 -elliptic equation with second membre in
-elliptic equation with second membre in 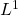
Adil Abbassi, Elhoussine Azroul, Abdelkrim Barbara
Adv. Sci. Technol. Eng. Syst. J. 2(5), 45-54 (2017);
View Description
In this paper, we prove the existence of a solution of the strongly nonlinear degenerate ![]() -elliptic equation of type:
-elliptic equation of type:
![]()
where ![]() is a bounded open subset of
is a bounded open subset of ![]() is a Caratheodory function from
is a Caratheodory function from ![]() into
into ![]() , who satisfies assumptions of growth, ellipticity and strict monotonicity. The nonlinear term
, who satisfies assumptions of growth, ellipticity and strict monotonicity. The nonlinear term ![]() checks assumptions of growth, sign condition and coercivity condition, while the right hand side
checks assumptions of growth, sign condition and coercivity condition, while the right hand side ![]() belongs to
belongs to ![]() .
.
Steel heat treating: mathematical modelling and numerical simulation of a problem arising in the automotive industry
Jose Manuel Diaz Moreno, Concepcion Garcia Vazquez, Maria Teresa Gonzalez Montesinos, Francisco Ortegon Gallego, Giuseppe Viglialoro
Adv. Sci. Technol. Eng. Syst. J. 2(5), 55-62 (2017);
View Description
We describe a mathematical model for the industrial heating and cooling processes of a steel workpiece representing the steering rack of an automobile. The goal of steel heat treating is to provide a hardened surface on critical parts of the workpiece while keeping the rest soft and ductile in order to reduce fatigue. The high hardness is due to the phase transformation of steel accompanying the rapid cooling. This work takes into account both heating-cooling stage and viscoplastic model. Once the general mathematical formulation is derived, we can perform some numerical simulations.
Petrov-Galerkin formulation for compressible Euler and Navier-Stokes equations
Nacer E. El Kadri E, Abdelhakim Chillali
Adv. Sci. Technol. Eng. Syst. J. 2(5), 63-69 (2017);
View Description
The resolution of the Navier-Stokes and Euler equations by the finite element method is the focus of this paper. These equations are solved in conservative form using, as unknown variables, the so-called conservative variables (density, momentum per unit volume and total energy per unit volume). The variational formulation developed is a variant of the Petrov-Galerkin method. The nonlinear system is solved by the iterative GMRES algorithm with diagonal pre-conditioning. Several simulations were carried out, in order to validate the proposed methods and the software developed.
Simulation of flows in heterogeneous porous media of variable saturation
Nacer E. El Kadri E, Abdelhakim Chillali
Adv. Sci. Technol. Eng. Syst. J. 2(5), 70-77 (2017);
View Description
We develop a resolution of the Richards equation for the porous media of variable saturation by a finite element method. A formulation of interstitial pressure head and volumetric water content is used. A good conservation of the global and local mass is obtained. Some applications in the case of heterogeneous media are presented. These are examples which make it possible to demonstrate the capillary barrier effect.
Models accounting for the thermal degradation of combustible materials under controlled temperature ramps
Alain Brillard, Patrick Gilot, Jean-Francois Brilhac
Adv. Sci. Technol. Eng. Syst. J. 2(5), 78-87 (2017);
View Description
The purpose of this conference is to present and analyze di_erent models accounting for the thermal degradation of combustible materials (biomass, coals, mixtures…), when submitted to a controlled temperature ramp and under non-oxidative or oxidative atmospheres. Because of the possible rarefaction of fossil fuels, the analysis of di_erent combustible materials which could be used as (renewable) energy sources is important. In industrial conditions, the use of such materials in energy production is performed under very high temperature ramps (up to 105 K/min in industrial pulverized boilers). But the analysis of the thermal degradation of these materials usually _rst starts under much lower temperature ramps (less than 100 K/min), in order to avoid di_usional limitations which modify the thermal degradation.
Threshold Multi Split-Row algorithm for decoding irregular LDPC codes
Chakir Aqil, Rachid El Alami, Ismail Akharraz, Abdelaziz Ahaitouf
Adv. Sci. Technol. Eng. Syst. J. 2(5), 88-93 (2017);
View Description
In this work, we propose a new threshold multi split-row algorithm in order to improve the multi split-row algorithm for LDPC irregular codes decoding. We give a complete description of our algorithm as well as its advantages for the LDPC codes. The simulation results over an additive white gaussian channel show that an improvement in code error performance between 0.4 dB and 0.6 dB compared to the multi split-row algorithm.
A new color image encryption algorithm based on iterative mixing of color channels and chaos
Mohamed Essaid, Ismail Akharraz, Abderrahim Saaidi and Ali Mouhib
Adv. Sci. Technol. Eng. Syst. J. 2(5), 94-99 (2017);
View Description
In this paper, we present a novel secure cryptosystem for direct encryption of color images, based on an iterative mixing spread over three rounds of the R, G and B color channels and three enhanced chaotic maps. Each round includes an affine transformation that uses three invertible matrices of order 2 _ 2; whose parameters are chosen randomly from a chaotic map. The proposed algorithm has a large secret key space and strong secret key sensitivity, which protects our approach from a brutal attack. The simulation results show that our algorithm is better for color images in terms of Peak Signal to Noise Ratio (PSNR), entropy, Unified Average Changing Intensity (UACI) and Number of Pixels Change Rate (NPCR).
Cyclical contractive conditions in probabilistic metric spaces
Abderrahim Mbarki, Rachid Oubrahim
Adv. Sci. Technol. Eng. Syst. J. 2(5), 100-103 (2017);
View Description
The purpose of this paper is to prove a fixed point theorem for a probabilistic k-contraction restricted to two nonempty closed sets of a probabilistic metric spaces, then we prove that these results can be extended to a collection of finite closed sets.
Group law and the Security of elliptic curves on ![Rendered by QuickLaTeX.com F_p[e_1,...,e_n]](https://www.astesj.com/wp-content/ql-cache/quicklatex.com-ae9f261183a36e0724c456834bbd7341_l3.png)
Abdelalim Seddik, Chaichaa Abdelhak, Souhail Mohamed
Adv. Sci. Technol. Eng. Syst. J. 2(5), 104-108 (2017);
View Description
In this paper, we study the elliptic curve ![]() , with
, with ![]() the localization of the ring
the localization of the ring ![]() where
where ![]() and
and ![]() if
if ![]() , in the maximal ideal
, in the maximal ideal ![]() . Finally we show that
. Finally we show that ![]() and the execution time to solve the problem of discrete logarithm in
and the execution time to solve the problem of discrete logarithm in ![]() is
is ![]() , such that the execution time to solve the problem of discrete logarithm in
, such that the execution time to solve the problem of discrete logarithm in ![]() is
is ![]() . The motivation for this work came from search for new groups with intractable (DLP) discrete logarithm problem is there great importance.
. The motivation for this work came from search for new groups with intractable (DLP) discrete logarithm problem is there great importance.
Nonlinear parabolic problem with lower order terms in Musielak-Orlicz spaces
Mhamed Elmassoudi, Ahmed Aberqi, Jaouad Bennouna
Adv. Sci. Technol. Eng. Syst. J. 2(5), 109-123 (2017);
View Description
We prove an existence result of entropy solutions for the nonlinear parabolic problems: ![]() and
and ![]() is a Leary-Lions operator defined on the inhomogeneous Musielak-Orlicz space, the term
is a Leary-Lions operator defined on the inhomogeneous Musielak-Orlicz space, the term ![]() is a Cratheodory function assumed to be continuous on u and satisfy only the growth condition
is a Cratheodory function assumed to be continuous on u and satisfy only the growth condition ![]() , prescribed by Musielak-Orlicz functions
, prescribed by Musielak-Orlicz functions ![]() and
and ![]() which inhomogeneous and not satisfy
which inhomogeneous and not satisfy ![]() -condition,
-condition, ![]() is a Cratheodory function not satisfies neither the sign condition or coercivity and
is a Cratheodory function not satisfies neither the sign condition or coercivity and ![]() .
.
S-asymptotically w-periodic solutions in the p-th mean for a Stochastic Evolution Equation driven by Q-Brownian motion
Solym Mawaki Manou-Abi, William Dimbour
Adv. Sci. Technol. Eng. Syst. J. 2(5), 124-133 (2017);
View Description
In this paper, we study the existence (uniqueness) and asymptotic stability of the p-th mean S-asymptotically !-periodic solutions for some nonautonomous Stochastic Evolution Equations driven by a Q-Brownian motion. This is done using the Banach fixed point Theorem and a Gronwall inequality.
On the Spectrum of problems involving both p(x)-Laplacian and P(x)-Biharmonic
Abdelouahed El Khalil, My Driss Morchid Alaoui, Abdelfattah Touzani
Adv. Sci. Technol. Eng. Syst. J. 2(5), 134-140 (2017);
View Description
We prove the existence of at least one non-decreasing sequence of positive eigenvalues for the problem,
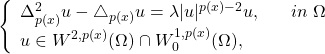
Our analysis mainly relies on variational arguments involving Ljusternik-Schnirelmann theory.
Existence and Boundedness of Solutions for Elliptic Equations in General Domains
Elhoussine Azroul, Moussa Khouakhi, Chihab Yazough
Adv. Sci. Technol. Eng. Syst. J. 2(5), 141-151 (2017);
View Description
This article is devoted to study the existence of solutions for the strongly nonlinear ![]() -elliptic problem:
-elliptic problem:
![]()
![]()
Where ![]() is an open set of
is an open set of ![]() , possibly of infinite measure, also we will give some regularity results for these solutions.
, possibly of infinite measure, also we will give some regularity results for these solutions.
Nonresonance between the first two Eigencurves of Laplacian for a Nonautonomous Neumann Problem
Ahmed Sanhaji, Ahmed Dakkak
Adv. Sci. Technol. Eng. Syst. J. 2(5), 152-159 (2017);
View Description
We consider the following Neumann elliptic problem
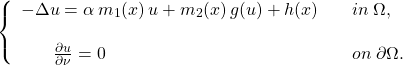
By means of Leray-Schauder degree and under some assumptions on the asymptotic behavior of the potential of the nonlinearity g, we prove an existence result for our equation for every given ![]() .
.
Existence Results for Nonlinear Anisotropic Elliptic Equation
Youssef Akdim, Mostafa El moumni, Abdelhafid Salmani
Adv. Sci. Technol. Eng. Syst. J. 2(5), 160-166 (2017);
View Description
In this work, we shall be concerned with the existence of weak solutions of anisotropic elliptic operators ![]() where the right hand side
where the right hand side ![]() belongs to
belongs to ![]() and
and ![]() belongs to
belongs to ![]() for
for ![]() and
and ![]() is a Leray-Lions operator. The critical growth condition on
is a Leray-Lions operator. The critical growth condition on ![]() is the respect to
is the respect to ![]() and no growth condition with respect to u, while the function
and no growth condition with respect to u, while the function ![]() grows as
grows as ![]() .
.
Boundary gradient exact enlarged controllability of semilinear parabolic problems
Touria Karite, Ali Boutoulout
Adv. Sci. Technol. Eng. Syst. J. 2(5), 167-172 (2017);
View Description
The aim of this paper is to study the boundary enlarged gradient controllability problem governed by parabolic evolution equations. The purpose is to find and compute the control ![]() which steers the gradient state from an initial gradient one
which steers the gradient state from an initial gradient one ![]() to a gradient vector supposed to be unknown between two defined bounds
to a gradient vector supposed to be unknown between two defined bounds ![]() and
and ![]() , only on a subregion
, only on a subregion ![]() of the boundary
of the boundary ![]() of the system evolution domain
of the system evolution domain ![]() . The obtained results have been proved via two approaches, The sub-differential and Lagrangian multiplier approach.
. The obtained results have been proved via two approaches, The sub-differential and Lagrangian multiplier approach.
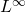 -Estimates for Nonlinear Degenerate Elliptic Problems with p-growth in the Gradient
-Estimates for Nonlinear Degenerate Elliptic Problems with p-growth in the Gradient
Youssef Akdim, Mohammed Belayachi
Adv. Sci. Technol. Eng. Syst. J. 2(5), 173-179 (2017);
View Description
In this work, we will prove the existence of bounded solutions for the nonlinear elliptic equations
![]()
in the setting of the weighted Sobolev space ![]() where
where ![]() ,
, ![]() are Caratheodory functions which satisfy some conditions and
are Caratheodory functions which satisfy some conditions and ![]() satisfies suitable summability assumption.
satisfies suitable summability assumption.
Doubly Nonlinear Parabolic Systems In Inhomogeneous Musielak- Orlicz-Sobolev Spcaes
Ahmed Aberqi, Mhamed Elmassoudi, Jaouad Bennouna, Mohamed Hammoumi
Adv. Sci. Technol. Eng. Syst. J. 2(5), 180-192 (2017);
View Description
In this paper, we discuss the solvability of the nonlinear parabolic systems associated to the nonlinear parabolic equation: ![]() where the function
where the function ![]() verifies some regularity conditions, the term
verifies some regularity conditions, the term ![]() is a generalized Leray-Lions operator and
is a generalized Leray-Lions operator and ![]() is a Caratheodory function assumed to be Continuous on
is a Caratheodory function assumed to be Continuous on ![]() and satisfy only a growth condition. The source term
and satisfy only a growth condition. The source term ![]() belongs to
belongs to ![]() .
.

